Wed 28 January 2026
Ostorlab 2025 Year in Review
2025 was a year of putting "many" ideas into practice at Ostorlab. AI moved from experiments and prototypes into engines that run real tests, drive real automation, and surface real issues in production-grade systems.
At the same time, our focus continued to evolve from building isolated features to working on how they play together. We invested in three areas in parallel.
Key components include the AI Pentest Engine, AI Monkey Tester, and Ticket Aggregation for workflow integration. The analysis encompasses mobile banking risk, attack surface discovery, privacy behavior, and case studies like the Signal Android chain. The infrastructure comprises OXO and OXO Titan for orchestration, along with an open agent and benchmark ecosystem.
The sections that follow are a snapshot of how these threads came together over the years.
AI Pentest Engine
AI is changing industries, whether we like it or not; it is reshaping decade-old processes, tools, and platforms. Security Testing is no exception. The advent of LLMs, the evolution of Agentic AI, and Tool Calling are opening doors that were previously impossible or required incredible human resources.
Both vulnerability scanning and manual, human-driven penetration testing are, and will be, radically reshaped in the coming years.
It is with this belief that AI Pentest Engine started and shipped its first version in December of 2025. It has already demonstrated exceptional capabilities, but also shown enormous future possibilities. 2026 is when Ostorlab homes in on what should be the most advanced mobile security testing platform on the planet. Period.
Ticket Aggregation and Automation
Ticket Aggregation v2 is the result of customer feedback. It is a ticketing system designed for vulnerability management and is customizable for both small and exceptionally large organisations.
We spent a lot of time listening to and discussing with teams, and looking at how they manage vulnerabilities within their organisations. Some grouped by app, others by asset, others by root cause or environment. Ticket Aggregation v2: whenever a user explains to us that their flow groups vulnerabilities by platform, but they have both dev, prod, and testing, we should only consider it fixed once it is in prod, so we have to do it by hand. Imagine their faces when we say that flow is fully automated, nothing to do there, we can detect fixed bugs in prod and track from dev.

AI Monkey Tester
The Monkey Tester journey began early on at Ostorlab. Its goal is to automate application interaction for every use case for every framework.
With time came the need to make it customizable, while we started with an Appium script, they were brittle, slow, and stopped working with every minor change of the UI, plus impossible to even implement in a complex UI.
AI Monkey Tester solved all of these; it reasoned about complex UI and made advanced automation happen, truly, everywhere, from your CI/CD working with testing prompts.

The year the team grew up
2025 felt different inside Ostorlab. We didn't just add more names; we introduced a diverse range of new personalities, backgrounds, and opinions to the room. The team grew across engineering, research, product, and marketing, and that changed the day-to-day atmosphere as much as anything else.
Growing teams do, however, come with their new challenges, some that we are still navigating. It did, however, reinforce our strong belief that a company's first customers are its members. Making sure we onboard smart, talented, and committed people continues to be our biggest priority as we continue to truly strive to serve all of our customers with unreasonable excellence.
Mobile Banking Security Report 2025
In 2025, we used our engines to assess real-world risk. One of the main outcomes was the "Banking Report 2025: Security at the Core of Mobile Finance", a detailed look at how mobile banking apps behave under automated testing.
For this study, we analyzed more than 500 of the top mobile banking apps worldwide. We examined both client-side and server-side exposure, the age and health of codebases and dependencies, and how much backend infrastructure is shared, centralized, or reused across institutions.
Recurring vulnerabilities were discovered in components that handle financial transactions and sensitive data, as well as the presence of obsolete code and dependencies in regularly used banking apps.
The report brought together several capabilities from the platform. Mobile static and dynamic analysis, including Monkey Tester-driven flows, uncovers client-side flaws and interaction paths. Backend reconnaissance, fingerprinting, and CVE matching from Attack Surface and Threat Center map vulnerable services and outdated components on the server side.
Download the full report here: Banking Report 2025 PDF
AI-automated attack surface and threat-driven discovery
We concentrated on switching from point-in-time graphs and static tables to AI-assisted discovery and threat-driven discovery for attack surface management in 2025. Reducing manual asset curation and improving discovery coverage were the goals.
The AI-Automated Attack Surface feature allows seeding discovery using prompts, such as requesting to "find all Microsoft and its acquisitions." The system then generates a candidate set that includes domains, subdomains, cloud resources, mobile apps, and SaaS surfaces.
In parallel, the Threat Center continued to develop. The initial release introduced a UI to map high-risk CVEs to your own assets. In 2025, we added the ability to filter down to CVEs that affect your environment and kept enriching the system with newly exploited vulnerabilities and updated fingerprints. These cover issues in products such as Ivanti, CrushFTP, Craft CMS, Cisco ISE, Fortinet, Next.js, and others.
Together, Ostorlab’s AI-Automated Attack Surface and Threat Center provide an inventory that is informed by current exploitation activity. Discovery, enrichment, and scan routing are linked to what attackers are using in practice.

Privacy as a first-class testing profile
With regulations tightening worldwide, 2025 was the year privacy became a primary scan type in Ostorlab. Privacy moved from an occasional check to a profile that teams can include in regular assessments.
We developed a privacy profile system that evaluates both stated policies and actual behaviors. It processes privacy policies in HTML or PDF formats against regulations like GDPR, CCPA, CPRA, HIPAA, and LGPD. Additionally, it monitors app requests and transmissions—permissions, embedded SDKs, data collection APIs, network traffic, and third-party data recipients—to pinpoint privacy risks by comparing these two perspectives.
Later versions enhanced Privacy Compliance Testing to encompass a wider range of asset types and introduced an extensive model of data categories, including over twenty types of personal and sensitive data such as biometrics, financial data, location history, media usage, and browsing patterns. The findings are supported by detailed evidence from both policy and application traces, with reports aligning directly to standards like CCPA, CNIL, and MASVS.
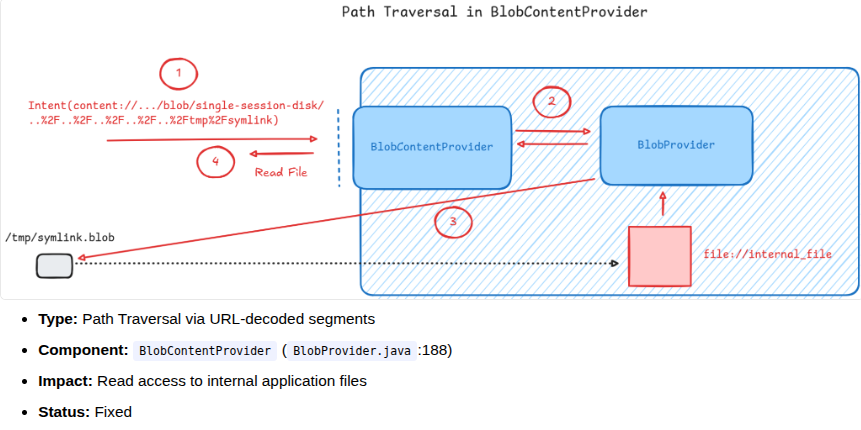
Arbitrary file read vulnerability chain in Signal Android
Alongside building new features, we continued investigating widely used apps to validate our tooling on complex, security-sensitive targets. One of the key 2025 case studies was a multi-step attack chain against Signal for Android that combined several issues into an arbitrary file read.
Using an automated analysis platform, several weaknesses were identified, including a path traversal bug in BlobContentProvider, allowing crafted URIs to access locations in Signal's private storage. Additionally, a file-read issue in ShareActivity permitted ACTION_SEND_MULTIPLE intents with file:// URIs to bypass validation, exposing internal files to Signal's blob storage. The Android SDK's handling of file:// URIs and MIME-type resolution also enabled these internal files to evade both platform checks and Signal's type filters.
The case study highlights how path traversal, MIME confusion, and validation gaps can lead to significant exploits, stressing the importance of multi-layer defense mechanisms. Signal's use of multi-layer encryption and Android Keystore helped prevent account takeovers and facilitated quick post-disclosure responses. It also identified design flaws in the Android SDK concerning file URIs and descriptor behavior, which affect other applications and enhance strategies for file and URI management.
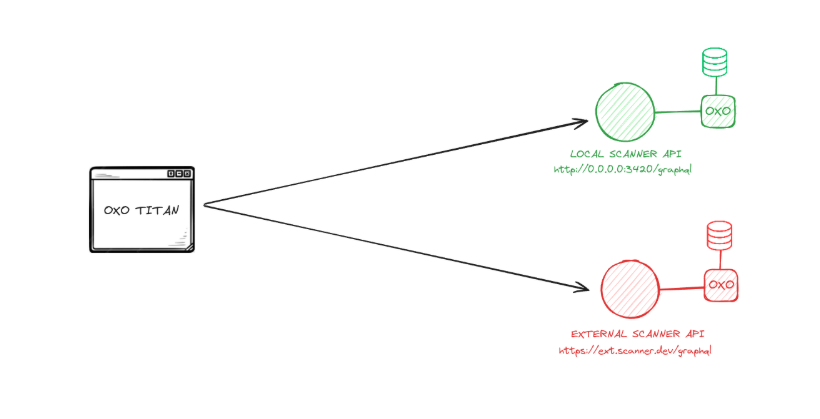
OXO ecosystem: OXO v1, OXO Titan, and the open agent store
In 2025, the OXO orchestration layer was enhanced, serving as a connector for scans, agents, and AI workflows. The release of OXO v1.0 significantly optimized scan operations, reducing startup time to approximately 16.5 seconds, and supporting standalone binaries for major operating systems with ARM64 compatibility.
It enables orchestration of multiple assets via YAML and provides a public agent store, improving command-line usability. Alongside the open-source engine, OXO Titan offers a graphical interface for local execution of various flows, catering to compliance and scalability needs.
The ecosystem expanded with agents like Nebula and others to enhance vulnerability detection across different domains. Ostorlab provides a versatile platform to incorporate AI Pentest into CI pipelines, facilitating on-prem execution while maintaining orchestration and AI logic.
Conclusion
Taken together, these pieces show a platform that is broader and more connected than it was a year ago.
AI now influences asset discovery, threat prioritization, and actionable findings in pentesting. Research on practical applications enhances tools' reasoning regarding vulnerabilities, while privacy gains a new specialized profile.
The work is ongoing. Growing the team in 2025 changed how we build and review these capabilities, and it raised the bar for how we want to test and ship them.
The direction, however, is clear:
- more automation where it helps,
- more context around every finding,
- and more ways for teams to plug Ostorlab into their own environments.
The goal for the next year is to keep tightening those loops so that it stays aligned with how modern security teams operate.
Tags:
OstorlabTable of Contents
- Ostorlab 2025 Year in Review
- AI Pentest Engine
- Ticket Aggregation and Automation
- AI Monkey Tester
- The year the team grew up
- Mobile Banking Security Report 2025
- AI-automated attack surface and threat-driven discovery
- Privacy as a first-class testing profile
- Arbitrary file read vulnerability chain in Signal Android
- OXO ecosystem: OXO v1, OXO Titan, and the open agent store
- Conclusion