Tue 19 March 2024
Insights
- Evolving Landscape: 30% of banking apps were launched post-2021, indicating rapid evolution, yet many remain outdated.
- Update Frequency: Two-thirds of apps have been updated within the past 3 months, reflecting a commitment to security and innovation.
- Technical Diversity: Dominance of C++ with Kotlin and Objective-C leading on their respective platforms. Cordova is favored in cross-platform development, contrasting with the broader trend where Flutter is the preferred choice for newer applications.
- Supply Chain and Native Library Vulnerabilities: A reliance on vulnerable native libraries presents major security challenges, Over 85% of apps include vulnerable components, emphasizing the need for secure supply chain management.
- Widespread Vulnerabilities: 98% of apps contain vulnerabilities, with 55% having critical or high-severity issues.
- Critical Backend Issues: The presence of critical vulnerabilities, like Remote Code Execution, Dependency Confusion, and XSS highlights the importance of secure coding and dependency vetting.
- Biometric Authentication Gaps: Outdated biometric authentication APIs necessitate updates to secure authentication methods.
- OAuth Security Weaknesses: Insecure OAuth mechanisms in about 10% of apps underline the need for stronger authentication protocols to prevent account takeovers.
- Encryption and Communication Risks: The mixed use of encrypted and clear text communications in 20% of apps points to a critical area for security enhancement.
Introduction
The widespread adoption of Mobile Banking Applications highlights their significance in the contemporary banking landscape.
A study by Fiserv underscores this point, revealing a direct correlation between the quality and availability of Mobile Banking Applications and key customer metrics such as satisfaction and attrition rates. This connection highlights how digital banking solutions are no longer just a convenience but a critical component of a bank's value proposition.
Furthermore, research conducted by Delta Risk elucidates the profound impact of bank security breaches and the overall security posture on customer loyalty and preferences for banking institutions. This relationship underscores the pivotal role of cybersecurity in maintaining customer trust and confidence in digital banking platforms.
Amidst these considerations, mobile banking apps emerge as prime targets for Mobile Malware attacks, driven by the lucrative potential for financial exploitation. This reality elevates the importance of developing secure and privacy-preserving mobile applications to protect customers' financial well-being and safeguard banking institutions' reputational integrity and trustworthiness.
This article presents a comprehensive empirical analysis of the Security of Bank Mobile Applications across North America, encompassing both the United States and Canada. Key insights are derived from an extensive mapping of the capabilities offered by these applications, including an assessment of their attack surface and potential vulnerabilities and the underlying technological stacks that power them.
This analysis aims to shed light on the pressing need for robust security measures and privacy safeguards in mobile banking applications.
Applications Overview
The analysis covered over 400 applications on both Android and iOS. Despite the maturity of banking mobile applications, recent data reveals that nearly 30% were launched after 2021, while 20% trace their origins back to 2010 or earlier.
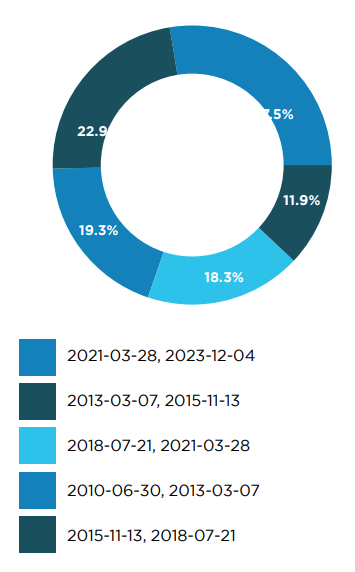
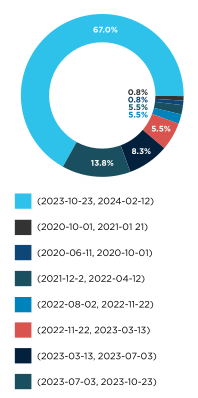
Significantly, more than two-thirds (67%) of these applications have seen updates within the past three months, highlighting a trend towards frequent releases. However, about 10% have not been updated in over two year, indicating a subset of applications may be becoming outdated.
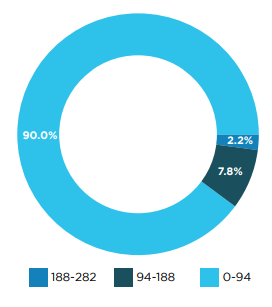
On the iOS platform, app sizes are increasing, with 4% exceeding 340MB, reaching up to 500MB, and 15% larger than 150MB. In contrast, Android applications are generally smaller, with only 3% ranging between 100MB and 130MB.
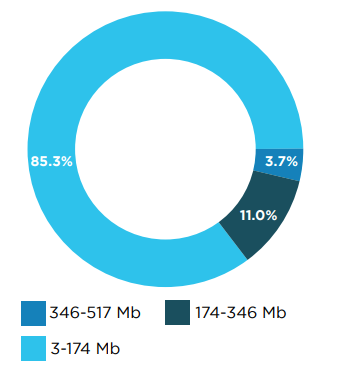
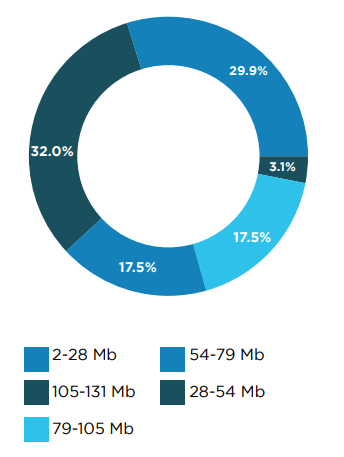
This analysis suggests that while the banking app ecosystem is characterized by a consistent update cycle and substantial app sizes, a noteworthy proportion remains outdated, lacking updates for over two years.
Technical Architecture
Tech Stacks
This section examines the technical compositions of mobile applications, focusing on programming languages, frameworks, and their association with application vulnerabilities.
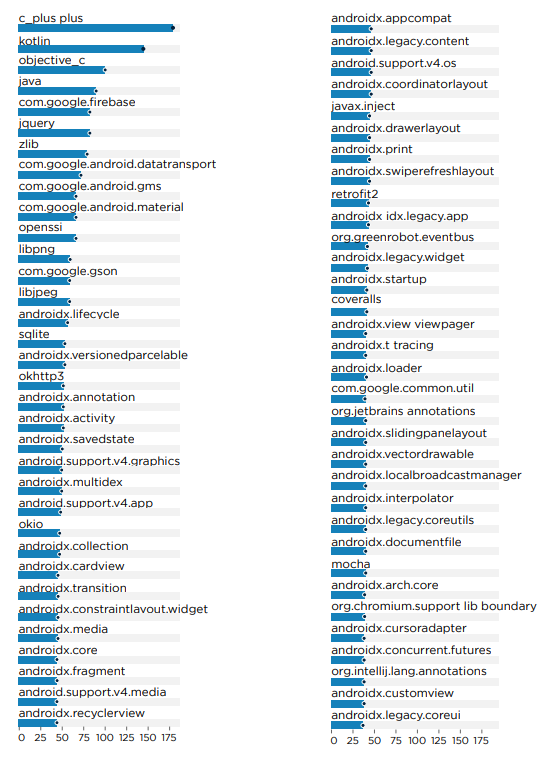
C++ emerged as the predominant programming language in mobile applications, attributed to its extensive use in native libraries that enhance functionalities like image optimization and file compression.
On Android platforms, Kotlin ranks second, while Objective-C maintains its popularity among iOS developers. For cross-platform development, Cordova leads as the most utilized framework, contrasting with the broader trend where Flutter is the preferred choice for newer applications.
Features and Capabilities
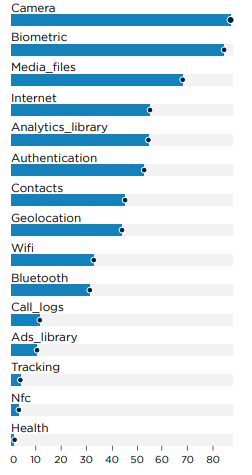
Regarding features and capabilities, the vast majority of Android mobile applications include camera access and biometric authentication, underscoring the broad adoption of biometric security in banking apps.
Additionally, 30% of these applications require WiFi and Bluetooth permissions, indicating a significant number that leverage these connections for enhanced functionality.
Conversely, only 15% of applications incorporate advertisement libraries, and a mere 5% possess user-tracking capabilities. This suggests that most applications prioritize user privacy, avoiding invasive tracking practices.
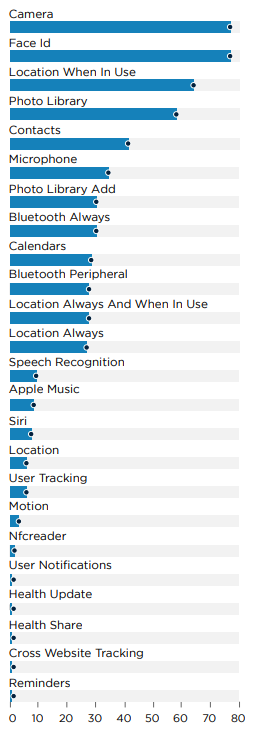
On iOS, the status quo persists, with all applications requiring camera access and Face ID for authentication, reinforcing the trend towards biometric security in banking apps. The prevalence of user tracking on iOS aligns with Android, maintaining the same percentage, indicating a consistent approach to user privacy across platforms.
Native Dependencies
Analysis reveals a significant reliance on native libraries such as Zlib, libpng, libjpeg, sqlite, curl and opencv across mobile applications. These libraries are known to contain various vulnerabilities.
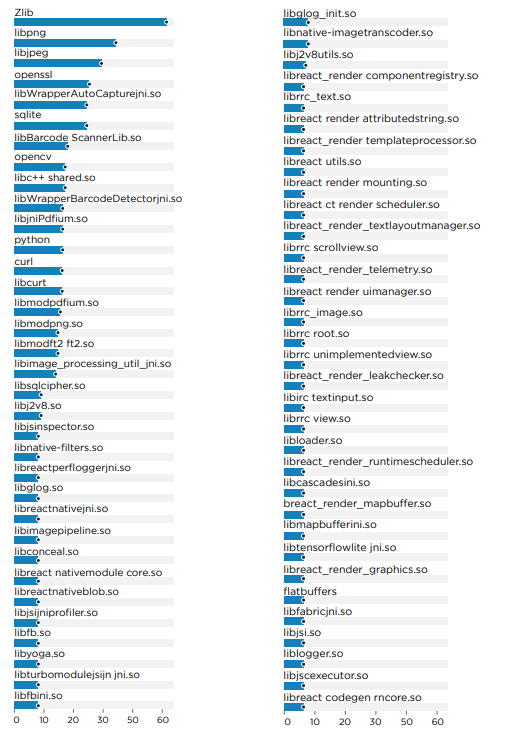
For instance, curl version 7.49.0, identified in some applications, is vulnerable to multiple CVEs, including but not limited to CVE-2022-35252, CVE-2022-32221, and CVE-2022-27782, with impacts ranging from denial of service to buffer overflow.
The security implications of these dependencies are thoroughly examined in the Security Challenge and Vulnerabilities section.
Backends
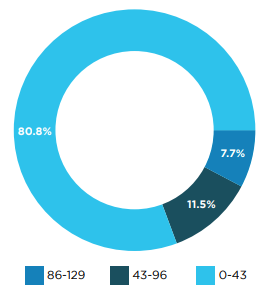
Our analysis indicates that, on average, 80% of applications interact with fewer than 40 backends, ranging from CDN analytics to various API systems. Notably, about 20% of these applications are connected to up to 120 different backends.

Android applications, in particular, display a higher diversity in backend connections, with 10% utilizing between 100 to 300 backend services.
Geographically, the majority of these backends are located in the United States, followed by significant numbers in Europe, specifically in the Netherlands, France, Spain, Ireland, and the UK. China ranks third in terms of backend location, which is noteworthy given the scrutiny often applied to sensitive US applications that communicate with Chinese servers. This interaction, however, is predominantly associated with banks owned by Chinese entities.

Banking Apps Attack Surface
Permissions
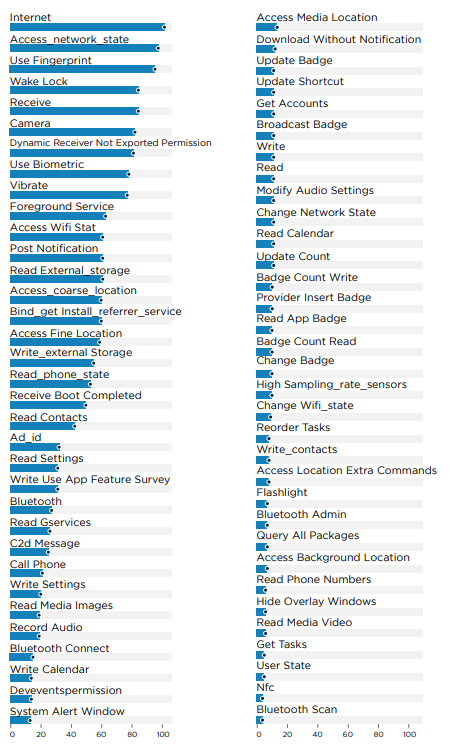
The analysis reveals that applications demand a broad spectrum of permissions, from basic internet access to modifying WiFi settings and using the flashlight.
iOS's permission system is simpler, potentially mitigating risks associated with extensive permissions.
Data indicates that 20% of applications on iOS request access to contacts and the microphone. Furthermore, 30% seek location access, and 5% require continuous location tracking.
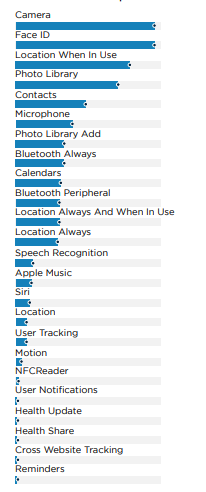
In summary, while applications generally need various permissions for functionality, a subset requests more intrusive permissions, such as continuous location tracking and access to personal data.
Exposure
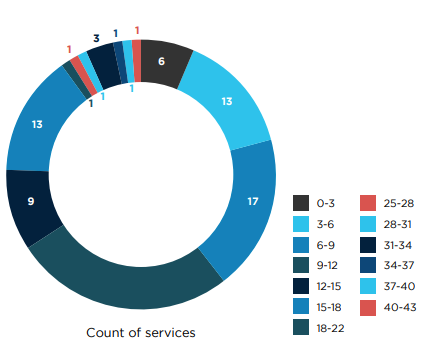
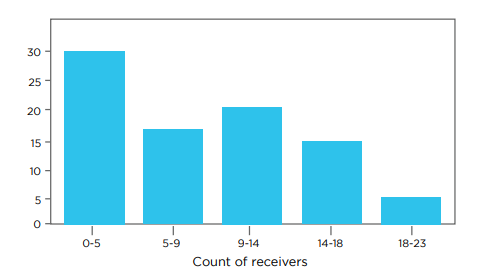
The analysis highlights a significant attack surface within applications. On Android, there's a notable implementation of multiple services, content providers, and activities, expanding potential vulnerability points.
For iOS, applications extensively use URL scheme handlers for various purposes, including authentication callbacks, payments, and deep linking, which similarly increases exposure to potential security risks.
Security Challenges and Vulnerabilities
About the Analysis
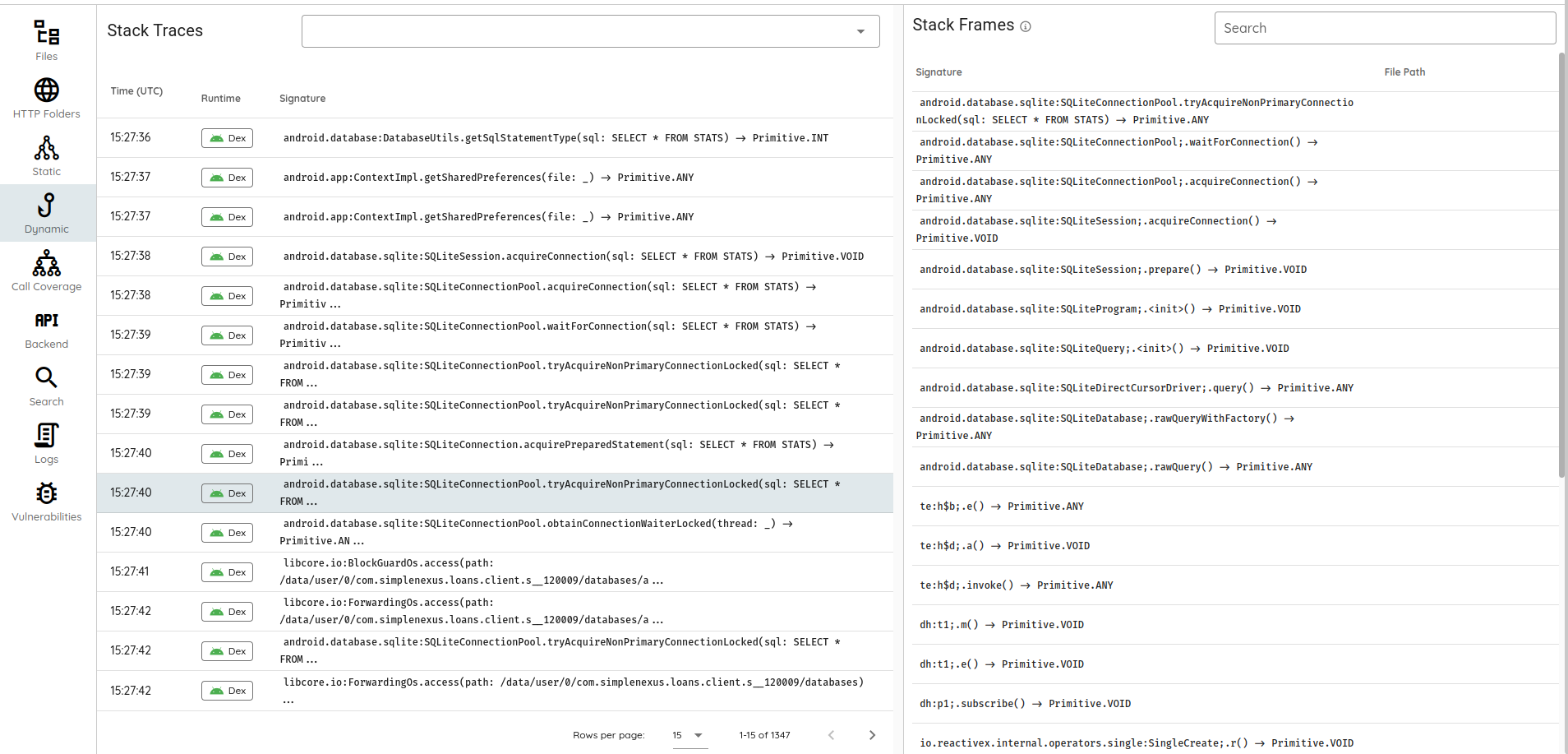
The mobile applications underwent comprehensive vulnerability scans, leveraging automated static and dynamic analysis techniques without user authentication.
Static Analysis covered:
- Configuration flaws, such as debug mode in the Facebook SDK, which could leak session information.
- Supply chain vulnerabilities, including outdated dependencies and dependency confusion.
- Taint analysis is used to detect programming errors like SQL injection or file path traversal.
- Hardcoded secrets and weak encryption practices.
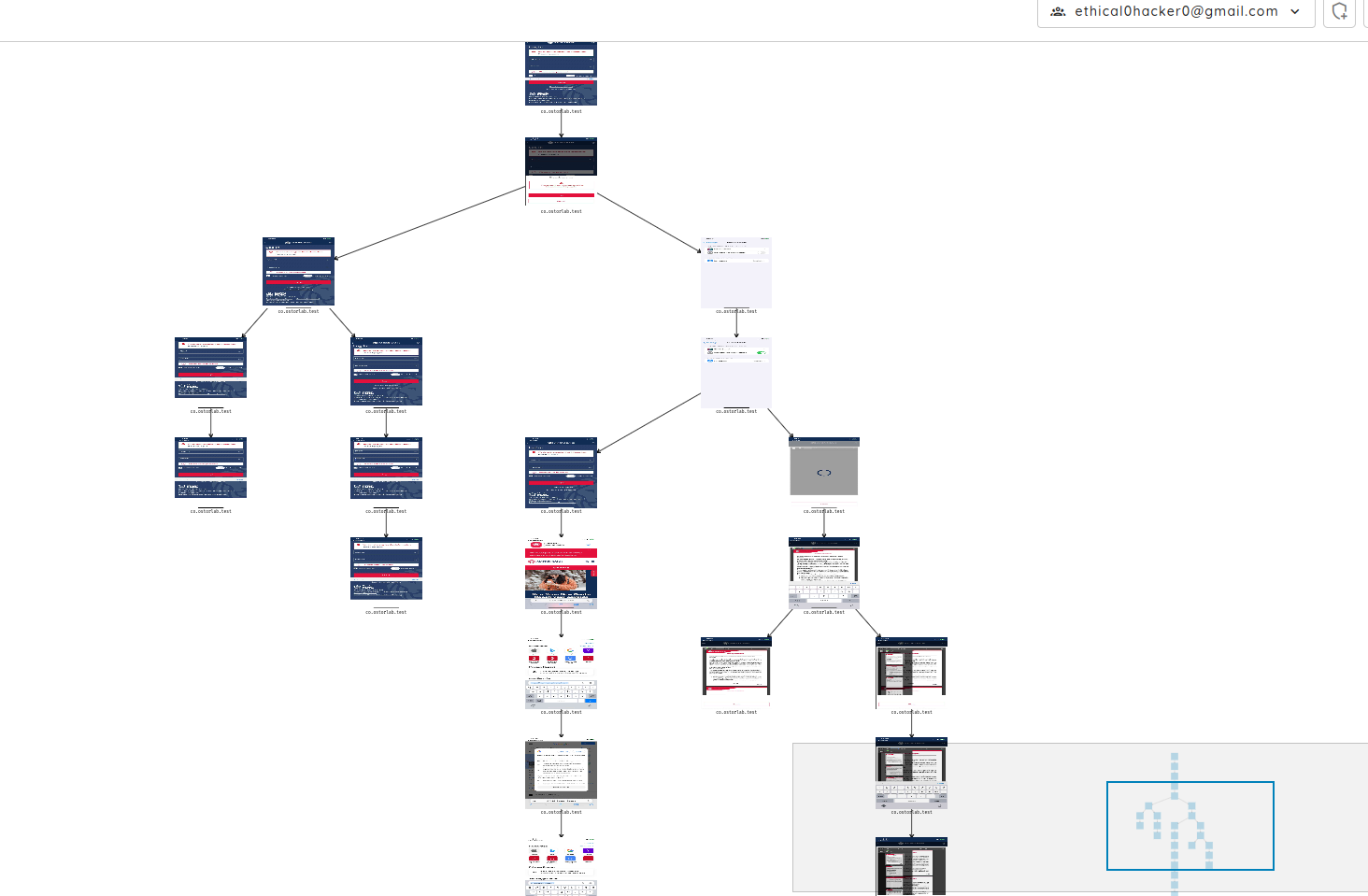
Dynamic Analysis covered:
- API hooking and automated interactions to enhance coverage.
- Backend interception to identify known vulnerabilities and fuzz-testing for potential unknown issues like SQL injection (SQLi) and XML External Entity (XXE) attacks.
The results were concerning, with 98% of applications harboring at least one vulnerability, and 55% containing critical or high-severity vulnerabilities. These ranged from client-side issues like remote data leaks and insecure cryptography to server-side issues, including remote code execution.
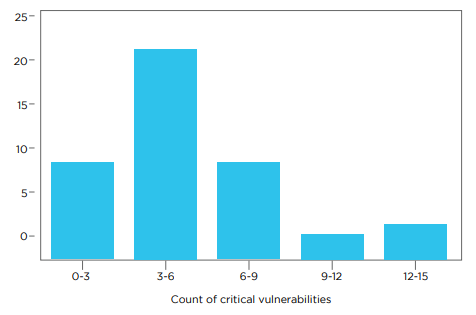
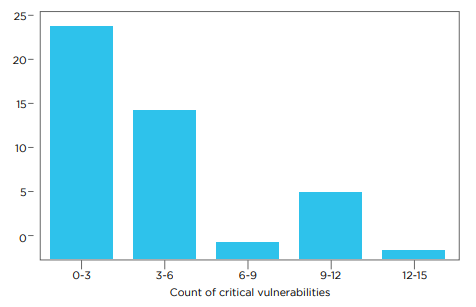
Conversely, a mere 0.4% of applications demonstrated robust security measures, showcasing updated dependencies, secure cryptographic practices, safe communication protocols, and a variety of hardening strategies, such as network security policies and disabling legacy storage options.
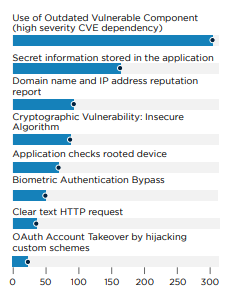
Backend Vulnerabilities
Critical vulnerabilities identified in the backend systems, notably without the need for authentication, include:
- Sitecore Local File Inclusion (LFI): This vulnerability was uncovered when intercepting backend communications with mobile applications, allowing attackers to read files on the server.
- Dependency Confusion: Identified through source map code leaks, this vulnerability arises when an application mistakenly downloads a malicious package masquerading as a legitimate dependency, due to namespace confusion.
- Cross-Site Scripting (XSS) and Open Redirects: Found in third-party software components used by mobile applications, these vulnerabilities can lead to unauthorized script execution in the context of a user's session or redirect users to malicious sites.
Supply Chain
Supply Chain vulnerabilities pose a significant security risk in banking mobile applications, with over 85% containing at least one vulnerable component, and more than half harboring high or critical supply chain vulnerabilities. These issues span across various types, including native memory corruption CVEs and serialization vulnerabilities. Examples include:
- zlib@1.2.8 is affected by multiple CVEs (CVE-2022-37434, CVE-2018-25032, CVE-2016-9843, CVE-2016-9842, CVE-2016-9841, CVE-2016-9840), indicating issues ranging from data leaks to potential remote code execution.
- com.fasterxml.jackson libraries, known for data-binding functionality, have serialization vulnerabilities dating back to 2016, yet they continue to be found in several applications. This widespread presence of vulnerable components underscores the critical need for thorough security audits and updates within the software supply chain, especially in the sensitive domain of banking applications.
Authentication
Authentication is a crucial aspect of banking mobile applications, yet the scan results reveal multiple vulnerabilities, particularly in the implementation of biometric authentication. Key findings include:
- Biometric Authentication Bypass: Some applications rely on outdated and insecure APIs for biometric authentication, which fail to securely link biometric data with session information, rendering the authentication process vulnerable to bypass methods.
- OAuth Account Takeover: Approximately 10% of the applications utilize insecure OAuth authentication mechanisms, which are susceptible to account takeover vulnerabilities. This flaw can be exploited by malware, potentially allowing unauthorized access to user accounts.
These vulnerabilities highlight the importance of using up-to-date, secure authentication methods and the need for continuous monitoring and upgrading of security protocols to protect against evolving threats.
Traffic and Encryption
The security of banking applications critically depends on the use of secure communication channels. Encrypted connections, supplemented by hardening mechanisms such as Network Security Policies, represent standard practices, with 100% of the applications employing encryption for communication. However, it's concerning that 20% of these applications still initiate clear text requests for parts of their communication. This mixed approach undermines the overall security posture by exposing potentially sensitive data to interception and compromise.
Real-world Security Incidents: Case Studies
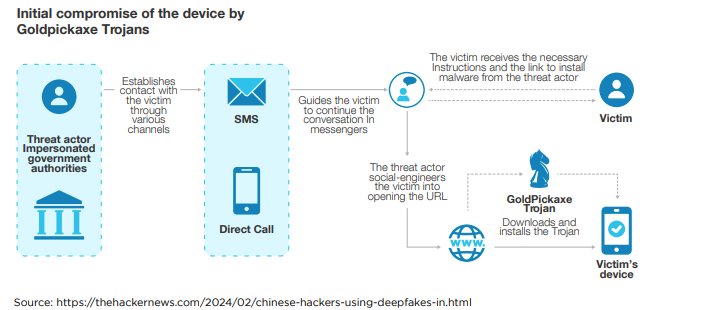
Android and iOS banking malware operated by Chinese-speaking Group
Source: https://thehackernews.com/2024/02/chinese-hackers-using-deepfakes-in.html
GoldFactory, a Chinese-speaking cybercrime group, has gained notoriety for developing sophisticated banking trojans, including GoldPickaxe, which targets iOS users to steal identity documents, facial recognition data, and SMS. Active since mid-2023, this group is also linked to Gigabud and focuses its malicious activities on the Asia-Pacific region, particularly Thailand and Vietnam. They deployed a variety of malware variants such as GoldDigger and GoldDiggerPlus for Android, and GoldKefu, which is embedded within GoldDiggerPlus, utilizing social engineering tactics, including smishing and phishing, to mimic local banks and government entities. These malicious applications are distributed through fake websites and, for iOS, via TestFlight and malicious Mobile Device Management profiles, with the Thailand Banking Sector CERT exposing iOS distribution schemes in November 2023.
The malware suite from GoldFactory is designed to bypass security measures and facilitate unauthorized bank transactions by collecting sensitive information and intercepting communications. GoldPickaxe, for instance, can create deepfake videos for fraud by exploiting the facial recognition systems used in Thailand for large transactions. The Android variants, GoldDigger and GoldDiggerPlus, target Vietnamese financial apps to exfiltrate banking credentials, indicating code-level similarities across the malware families. With advanced capabilities like the Agora SDK in GoldKefu for impersonating bank customer services, GoldFactory showcases a high level of operational sophistication. Their activities underline the growing challenge of mobile banking malware and the importance of cybersecurity vigilance, including skepticism towards suspicious links, cautious app installation, and regular review of app permissions.
Android Banking Trojans targeted 985 bank apps in 2023
Source: https://www.bleepingcomputer.com/news/security/ten-new-android-banking-trojans-targeted-985-bank-apps-in-2023/
In 2023, the cybersecurity landscape witnessed the emergence of ten new Android banking malware families, marking a significant increase in threats targeting the financial sector. These new entrants, alongside updates to 19 existing malware families from the previous year, have expanded their reach to 985 bank and fintech/trading apps across 61 countries. These malware variants are designed with advanced functionalities to steal online banking credentials, bypass two-factor authentication protections, and in some cases, execute unauthorized transactions directly. Enhancements in these trojans include capabilities for automated transfer systems, capturing multifactor authentication tokens, and employing social engineering tactics. Zimperium's comprehensive analysis of all 29 malware families revealed trends such as subscription-based distribution models, priced between $3,000 and $7,000 per month, and the incorporation of features like keylogging, phishing overlays, and the theft of SMS messages.
The threat landscape has also broadened beyond traditional banking targets to include social media, messaging apps, and personal data, indicating a diversification in cybercriminal objectives. Among the ten new trojans identified in 2023, with over 2,100 variants, were notable names like Nexus, Godfather, and Pixpirate, showcasing a wide array of attack methods, from live screen-sharing to automated transaction systems. Despite ongoing efforts by cybersecurity professionals, malware families such as Teabot, Exobot, and Mysterybot continue to pose significant threats, particularly in countries like the United States, the United Kingdom, and Italy. To combat these evolving threats, users are urged to adhere to safety recommendations, including downloading apps exclusively from the Google Play Store, carefully examining app reviews and developer credentials, scrutinizing requested permissions, and avoiding updates from external sources or engaging with links from unsolicited messages.
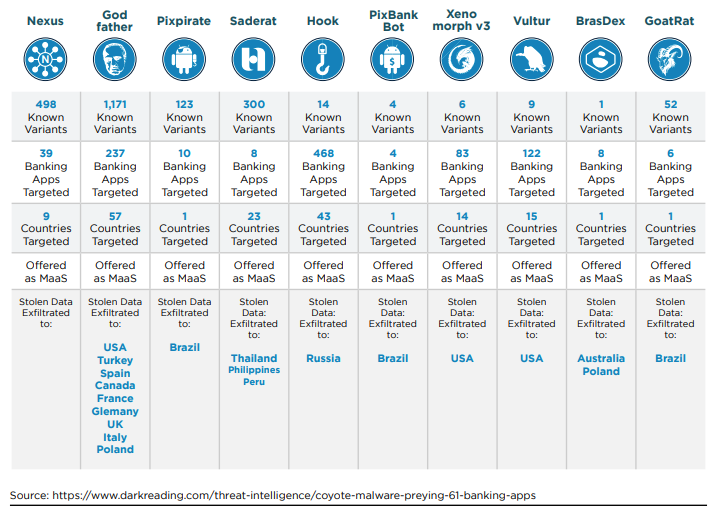
2024 Coyote Banking Malware and Evasion Techniques
Source: https://www.darkreading.com/threat-intelligence/coyote-malware-preying-61-banking-apps
The cybersecurity community has recently uncovered "Coyote," a novel banking Trojan that specifically targets 61 online banking applications, with a primary focus on Brazil. This discovery is noteworthy not only because of the Trojan's immediate threat within Brazil but also due to its potential for international impact, drawing parallels with past Brazilian malware campaigns that have extended their reach globally. Coyote's composition is particularly sophisticated, integrating various technologies such as Squirrel —a relatively obscure programming language—alongside more than a dozen malicious functionalities. This represents a significant evolution in the landscape of financial malware, showcasing the continuous innovation by Brazilian malware developers who have been active and evolving since 2000.
Coyote's capabilities extend beyond typical banking Trojan activities, including executing commands for taking screenshots, logging keystrokes, terminating processes, and deploying a deceptive "Working on updates…" overlay to immobilize victim machines. Such functionalities suggest Coyote's potential development into more dangerous forms of malware, such as initial access Trojans and backdoors. Furthermore, Coyote employs unique evasion techniques to skirt detection, utilizing Squirrel to masquerade as a legitimate software update packager and opting for Nim for its final stage loader to further lower its detection footprint. This strategic departure from more commonly used programming languages like Delphi for malware development underscores a shift towards more sophisticated and harder-to-detect methods, signaling a growing challenge for cybersecurity defenses worldwide.
Future of Mobile Banking Security
- Integration of Banking Services with Non-Financial Platforms: This trend carries significant risk due to potential data privacy and security concerns. Integrating financial services into platforms not primarily focused on financial transactions could increase the attack surface for cyber threats and make user data more vulnerable.
- Expansion of Open Banking and Financial Ecosystems: While open banking promises innovation and personalization, it also poses risks related to data security and customer privacy. The sharing of financial data across institutions and third-party providers requires robust data protection measures to prevent breaches and misuse.
- Rise of Neobanks and Digital-Only Financial Institutions: Neobanks challenge traditional banking models and regulatory frameworks. Their entirely digital presence may pose risks in terms of regulatory compliance, financial stability, and customer trust, especially in the event of tech failures or security breaches.
- Increased Use of Artificial Intelligence and Machine Learning: AI and machine learning bring the risk of opaque decision-making processes, potential biases in algorithms affecting customer services, and the challenge of ensuring the security of AI systems against manipulation or exploitation.
- Enhanced Security Measures with Biometrics and Blockchain: While these technologies are aimed at improving security, they also introduce risks. Biometric data, if compromised, cannot be changed like a password, and blockchain technology, though secure, is not entirely immune to vulnerabilities, especially in its integration and application in banking systems.
Conclusion
The landscape of mobile banking applications is rapidly evolving, driven by technological advancements, changing consumer expectations, and the emergence of new financial players. Our comprehensive analysis across North American banking institutions has highlighted not only the current state of mobile banking security but also the challenges and opportunities that lie ahead.
Key findings:
- Security and Privacy Concerns: Despite the widespread adoption of mobile banking applications, significant security and privacy concerns persist. The presence of vulnerabilities in nearly 98% of the applications, including critical and high-severity ones, underscores the urgent need for enhanced security measures.
- Supply Chain Vulnerabilities: The prevalence of supply chain vulnerabilities in over 85% of the banking applications examined points to the critical need for robust supply chain management and security practices. These vulnerabilities expose financial institutions to potential breaches and data leaks.
- Emerging Trends and Risks: The integration of banking services with non-financial platforms, expansion of open banking, rise of neobanks, increased use of AI and machine learning, and the adoption of biometrics and blockchain technologies present both opportunities and challenges. Each of these trends carries inherent risks, from data privacy concerns to regulatory compliance issues and potential security vulnerabilities.
Table of Contents
- Insights
- Introduction
- Applications Overview
- Technical Architecture
- Banking Apps Attack Surface
- Security Challenges and Vulnerabilities
- Authentication
- Traffic and Encryption
- Real-world Security Incidents: Case Studies
- 2024 Coyote Banking Malware and Evasion Techniques
- Future of Mobile Banking Security
- Conclusion