Thu 16 June 2022
In this 2nd part of the article, we will not go into how to run attack surface collection but share insights we are seeing from the data we have been reviewing on organizations' external attack surface.
Attack Surface Leaks Data about Organisations, Customers, Growth ...
The first key insight we built is that the attack surface of an organization can give a critical grasp of the competitive edge of an organization, be it how large it is, how distributed it is, how advanced is its infrastructure and how often it is evolving.
Take an organization like Anduril, for instance. Anduril is a defense-focused startup created by the founder of Oculus.
Anduril has a relatively small infrastructure, and the fact it owns several domains like fluxmesh.us and fmesh.us might
indicate a product and technology in that space.
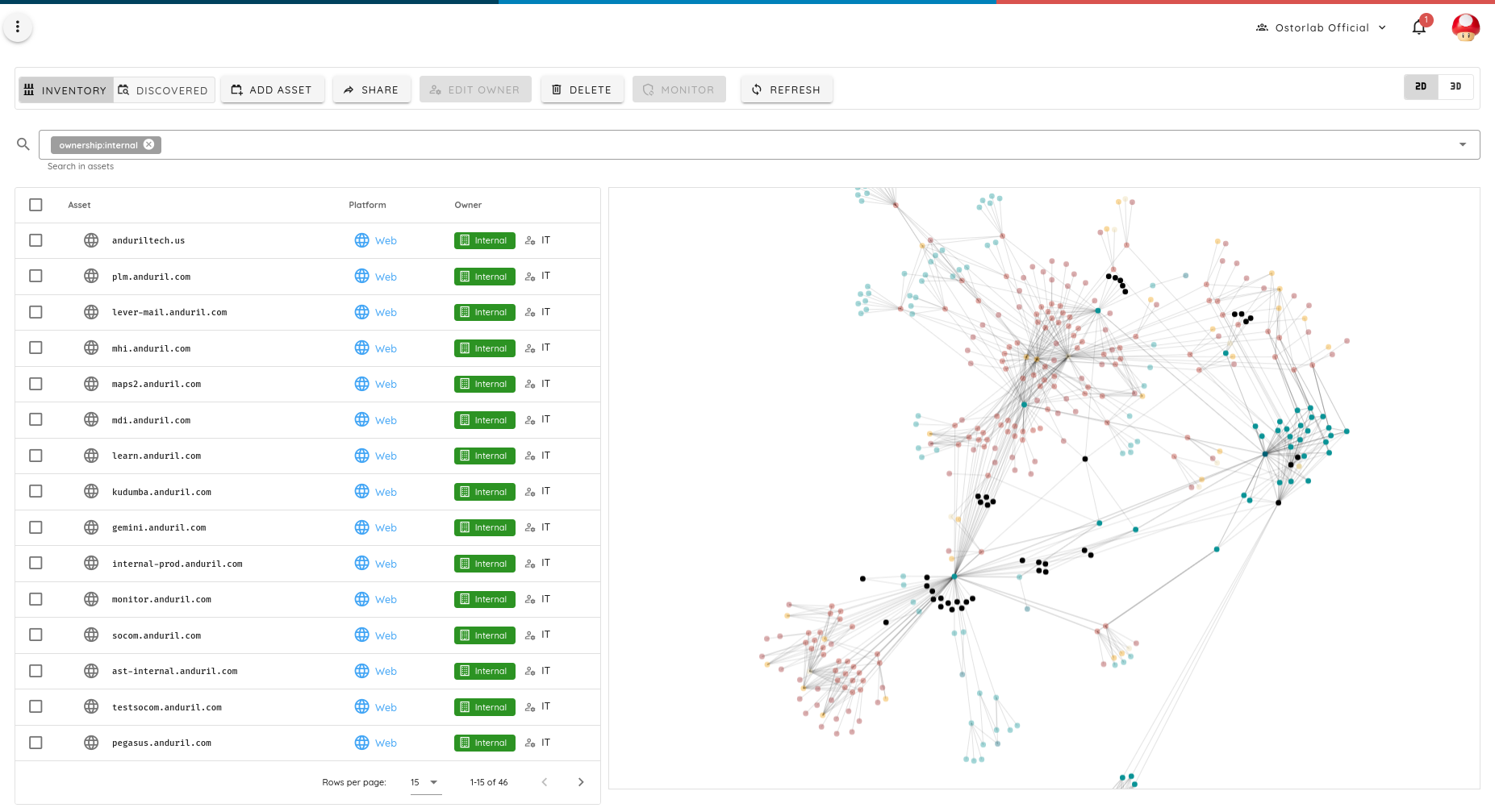
Anduril uses AWS, Markmonitor for its DNS, and Microsoft government cloud for parts of its infrastructure. It has also been running PoC with companies like Palo Alto. Many of its exposed attack surface leaks project with the US military with what seems like internal product code names.
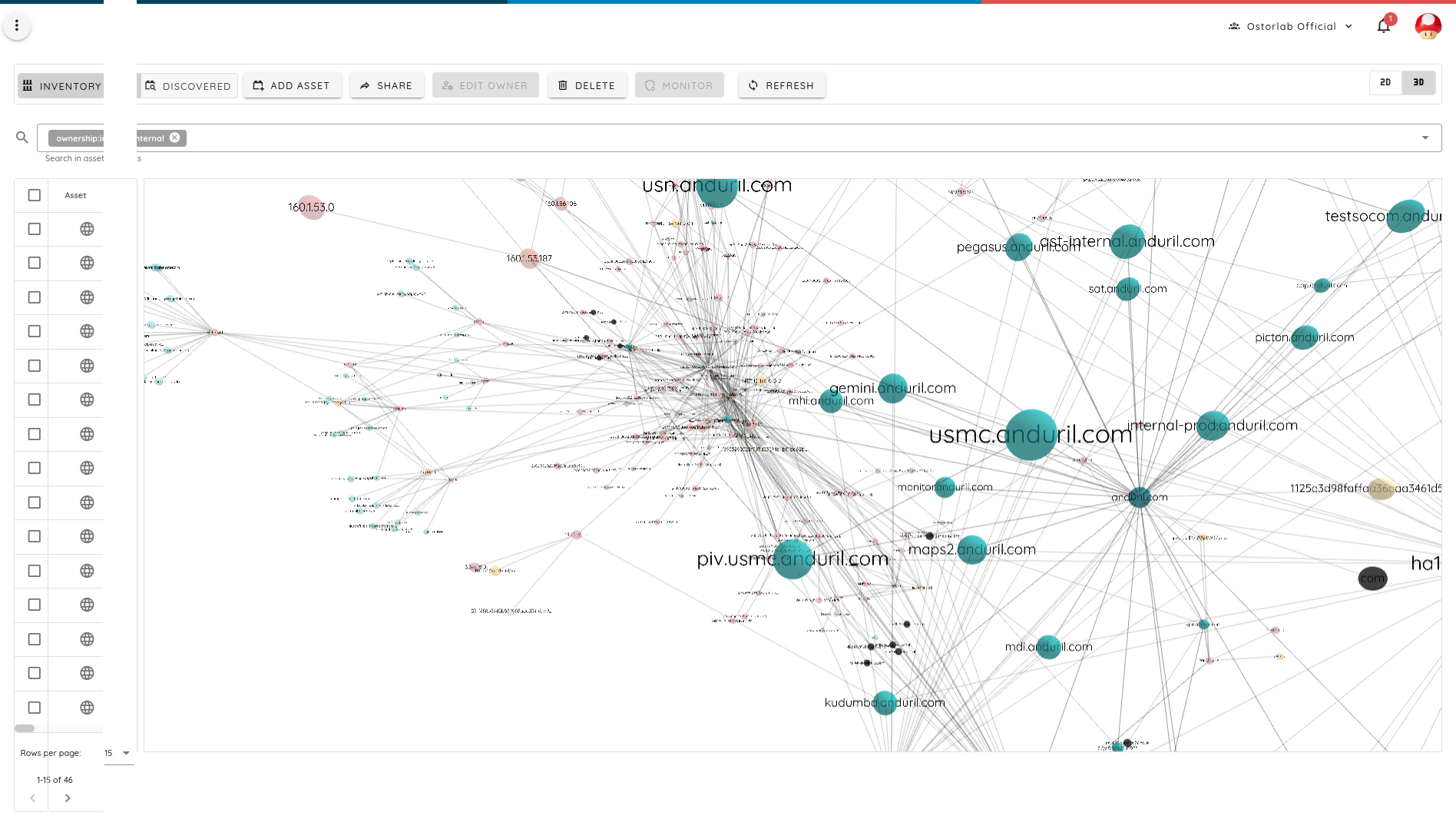
Anduril is also using smaller SaaS providers to host things like training at LessonOnly, for instance. An attacker or competitor can leverage this information to run a phishing attack, estimate growth, gain a competitive edge over competing PoC, etc.
Are you storing data in approved locations? How about your SaaS providers?
Many organisations must comply with regulations on where users' and customers' data is stored. The military sector is a particular one with strict requirements.
While the organisation itself might comply, most organisations nowadays use a wealth of SaaS providers with access to what could be important data but can, in the worst case, be leveraged for rebound attacks.
Analysis of the data yielded, in some cases, European / American military providers with connections with IPs owned by Chinese Cloud Providers. This is most likely just a coincidence, but it seems at least worth investigating or avoiding.
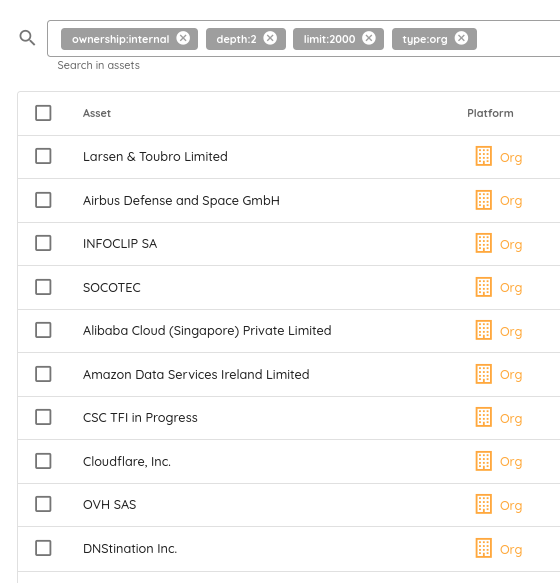
Russian organisations have a large Internet presence
Another insight is how Russian organizations and enterprises have a surprisingly wide internet presence with some earning the top spots in infrastructure size and IP address usage.
For instance, the single IP address with the most subdomains pointing to it is owned not by AWS, not by Google, not by Meta, but Yandex.
That IP is 213.180.204.242 and hosts nearly 300k subdomains.
IPv6 is still lagging
The inspection of the data has also shown that IPv6 adoption remains low, accounting for only 3% of exposed services. Scanning IPv6 space is not only hard, but it also has little benefit to attackers.
The extension of the life of IPv4 addresses has been greatly impacted by Cloud adoption, which offered an improved efficiency in using the IPv4 addresses. However, it also paradoxically reduced the value of scanning IP addresses directly.
In most cases now, IPv4 addresses, if scanned directly, will yield nothing as most services are served over some HTTP-esque protocol that requires sending a valid domain name.
In other words, direct IP scanning in the modern infrastructure world is inefficient; it must be coupled with subdomain enumeration and brute-forcing.
Organisations love nested domains
A common question when evaluating an organisation's attack surface is how deep the enumeration should go. The expectation is that most domains will only use the first levels at best.
Analysis of the data has shown quite the opposite with several organisations using as a far as nine levels of nested subdomains to index their infrastructure.
SaaS adoption and Growth
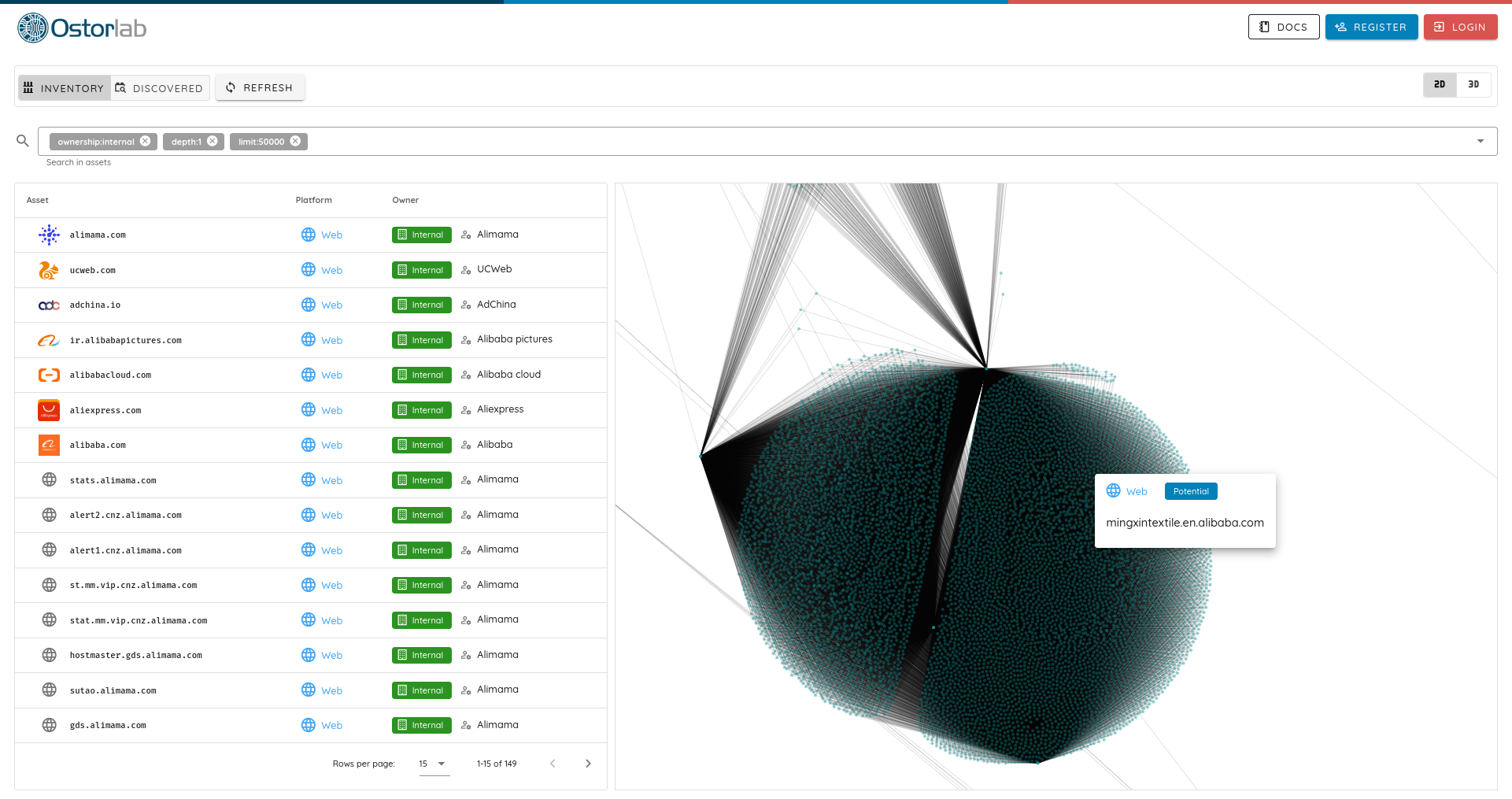
Another key insight is tracking SaaS providers adoption. Some of unexpected ones with a truly massive customer and infrastructure adoption are Alibaba and Alibaba Cloud. They are among the largest internet-facing infrastructure with not only their Cloud Service but also massive products like Tao Bao, Tmall, 1688.com or aliyuncs.com.
Some Car manufacturers have surprisingly big infrastructure
Another unexpected discovery is how some car manufacturers topped the list of large infrastructure like Arrival a british electric vehicle manufacturer or Bentley, a luxury car manufacturer.
The data seems to correlate with IoT equipment and industrial systems. These often have a bad track record of patching and security posture.
How to defend
For defenders, here are some key lessons on managing your attack surface:
- It is a good measure to separate production from a customer-facing system and avoid links between them. This is not bullet-proof but makes the work harder for the attacker to map your external presence.
- External surface is not just about exposed ports and services; its values or impact can be far-reaching. Avoid if possible leaking customer data and internal project names.
- Treat your DNS as public data; it will eventually leak, be it through brute force, certificate transparency, or passive DNS.
- Use IPv6 addresses to your advantage to reduce your visibility and make it hard to find. Beware, however, of ensuring the rest of your security measures are present on IPv6.
Table of Contents
- Attack Surface Leaks Data about Organisations, Customers, Growth ...
- Are you storing data in approved locations? How about your SaaS providers?
- Russian organisations have a large Internet presence
- IPv6 is still lagging
- Organisations love nested domains
- SaaS adoption and Growth
- Some Car manufacturers have surprisingly big infrastructure
- How to defend