Thu 20 December 2018
This article is about how to manage AWS access keys when using AWS services in your mobile application.
One of the main reasons that make clients reluctant about the cloud is the data control and the security of the full chain. To tackle this concern, AWS defined in the Shared Responsibility Model boundaries between AWS and the customer when dealing with security controls, it described the security best practices to follow when using AWS services at each level.
AWS Shared Responsibility Model
In a nutshell, AWS is responsible for the security of the cloud (represented as the orange part) , while the customer is responsible for the security in the cloud (represented as the green part). So as a customer, you are responsible for managing the users and how they access to the services.
When you access AWS programmatically, you use an access key to verify your identity and the identity of your applications. Anyone who has your access key has the same level of access to your AWS resources that you do. This is why, you should not in any case make your access key public. Uber will not forget this lesson : https://awsinsider.net/articles/2017/11/21/uber-aws-data-breach.aspx
If you are uploading your code to a git repository, you can use git-secrets which checks and prevents you from committing access keys into git repositories.
If you are accessing AWS services via your mobile application, hardcoding the access keys is a high risk vulnerability since your secrets can be compromised by someone examining your code.
To check if your keys are hardcoded in your application, you can use Ostorlab security scanner which detects hardcoded access keys in your mobile application ( Android and iOS).
In the example, I will be using an Android application to upload pictures to AWS S3.
The first example is using the hardcoded keys directly in the upload function:
// KEY and SECRET are gotten when we create an IAM user above
String KEY = "AKIAIUG2TRZ99XFZONBA";
String SECRET = "31eJbrNp5OJgrbvxTyzz38MUZ/MBMNVkG0irtd/2";
BasicAWSCredentials credentials = new BasicAWSCredentials(KEY, SECRET);
AmazonS3Client s3Client =new AmazonS3Client(credentials);
TransferUtility transferUtility =
TransferUtility.builder()
.context(getApplicationContext())
.awsConfiguration(AWSMobileClient.getInstance().getConfiguration())
.s3Client(s3Client)
.build();
The second example is using the keys in a resources config file:
<?xml version="1.0" encoding="utf-8"?>
<keys>
<key name="aws_access_key_id">AIDAJILINIFRJA2HBEEQ </key>
<key name="aws_secret_access_key"> 5syV8k5gCDJXtSCW4BKOjcpCLJHAhgbe/YfSPoJE </key>
</keys>
Ostorlab is able to detect the presence of both keys:
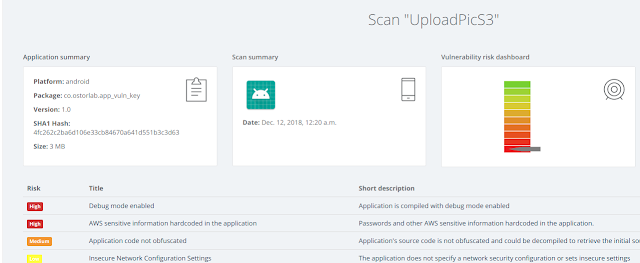
By clicking on AWS sensitive information hardcoded in the application, we can find the keys in the technical details section:
So if you are developing a mobile application and are using AWS services: - Check if you are hardcoding access keys - Obfuscate your code to avoid trivial retrieve of the access keys (You can check Proguard) - Store your keys in a different component and retrieve them only when needed, using AWS Secret Manager for instance.