Wed 03 July 2024
Summary of the Situation
E.V.A Information Security researchers recently discovered significant vulnerabilities in the CocoaPods dependency manager. These flaws allowed malicious actors to claim ownership of unclaimed pods and inject malicious code into numerous popular iOS and MacOS applications. While these vulnerabilities have been patched, the potential impact was severe, as such an attack could have compromised nearly every Apple device.
One Key Vulnerability is CVE-2024-38368. This vulnerability allowed attackers to claim unclaimed CocoaPods packages and insert malicious code. The potential for widespread damage was immense, affecting both individual developers and large organizations relying on CocoaPods for dependency management.
Root Causes
The root cause of these vulnerabilities lies in the lack of strict ownership and verification mechanisms for unclaimed pods in the CocoaPods repository. This oversight made it possible for attackers to assume control of unclaimed packages and manipulate them to spread malicious code.
Remediation Actions Taken
In response to the discovery, the maintainers of CocoaPods have implemented several key remediation actions:
- Patched Vulnerabilities: All identified vulnerabilities have been patched to prevent further exploitation.
- Improved Governance: Measures have been introduced to improve governance and oversight of the CocoaPods repository.
- Ownership Verification: Enhanced verification processes for claiming packages have been established to ensure that only legitimate developers can claim ownership of pods.
Ostorlab's Analysis
Ostorlab's scanning and analysis have revealed the following:
- Over 290,000 CocoaPods references have been identified in various scans.
- These references correspond to approximately 9,500 unique CocoaPods packages, including transitive dependencies.
- The unclaimed packages have been found in several high profile applications like several
Amazonapps,Tinderand many others. - Only 67 of 9502 of these packages were unclaimed and used in the application (0.07%), namely:
JJPluralForm
ObjectiveGumbo
MosaicUI
GCPlaceholderTextView
iOS-QR-Code-Encoder
JSONKit-NoWarning
GCNetworkReachability
UIImageEffects
MHPrettyDate
NHAlignmentFlowLayout
DBChooser
QR-Code-Encoder-for-Objective-C
GRKInputStreamAggregate
ASCScreenBrightnessDetector
FMMoveTableView
nv-ios-http-status
DYRateView
RegexKitLite
SDNetworkActivityIndicator
MASAttributes
MRCircularProgressView
PPTopMostController
NTMonthYearPicker
UIActionSheet-Blocks
MoPubSDK
NoticeView
HPGrowingTextView
ImageCache
MDSpreadView
Courier
MessagePack
PDKeychainBindingsController
CRGradientNavigationBar
Base64nl
ASIHTTPRequest
JAGPropertyConverter
SHXMLParser
UIAlertView-Blocks
MulticastDelegate
AsyncImageDownloader
DBKit
FPPopover
MagicKit
OAuthCore
XYPieChart
KeychainItemWrapper
MDHTMLLabel
SOCKit
TSCurrencyTextField
CRMotionView
DebugKit
MKMapView-ZoomLevel
ALActionBlocks
StyledPageControl
TouchXML
PinYin4Objc
PopoverView
LogEntries
Promise
WMGaugeView
MGImageUtilities
CSV
MAObjCRuntime
KLSwitch
DejalActivityView
XMLReader
MJPopupViewController
The immediate threat addressed by the CocoaPods maintainers has partly controlled the risk. However, developers and organizations must take proactive steps to mitigate potential risks further.
What You Should Do Next
To ensure the security of your applications, follow these steps:
- Scan your application: Ostorlab reports packages with unclaimed owners. This includes transitive dependencies.
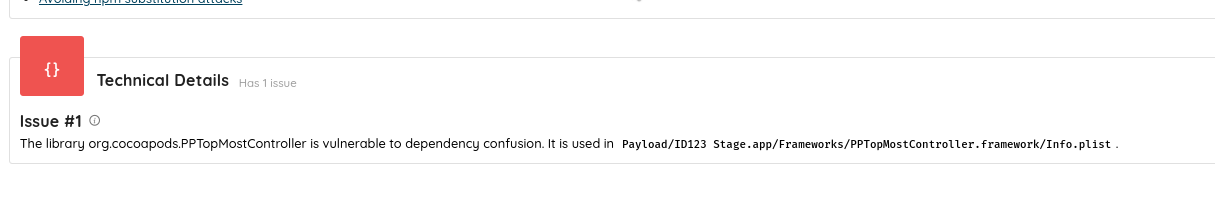
- Remove Unclaimed Packages: To prevent potential exploitation, eliminate any unclaimed packages from your build.