Tue 23 September 2025
📊 Mobile Benchmarking for PentestAI
Android Benchmark Suite
Developed 72 Android applications containing a diverse set of real-world vulnerabilities.to benchmark Mobile PentestAI’s Android scanning capabilities, focusing on common and critical weaknesses seen in the Android mobile application.
Key vulnerability categories include:
- Intent-Based Vulnerabilities – Implicit intent leaks, intent redirection, task hijacking, untrusted intent scheme usage in WebViews, and intent-based XSS/HTML injection.
- WebView Exploits – Malicious URL loading, session token leakage, JavaScript interface abuse, and insecure URL handling.
- Authentication & Session Management – OAuth misconfigurations, session not invalidated after password change, 2FA and biometric bypass, and account takeover via adb backup.
- Data Exposure & Privacy Leaks – Sensitive data in logs, cleartext storage, Firebase misconfig, IP/location exposure, and Google indexing of private content.
- Code Execution & Injection – JavaScript execution via
openURL, SQL injection in content providers, unsafe deserialization, and shell command injection. - Component Exposure – Unprotected services, broadcast receivers, and activities; insecure pending intents; sensitive broadcast leaks.
- Cryptographic Weaknesses – Insecure PRNG usage, hardcoded secrets, weak key generation, and missing encryption of sensitive files.
- File & IPC Vulnerabilities – Path traversal via ZIP processing, internal file overwrite, escalation via
grantUriPermission, and unsafe access from external storage. - Other Critical Issues – Notification injection, mismatched parceling, OAuth account takeover, passcode bypass, and misuse of Android platform features.
iOS Benchmark Suite
Built 21 iOS applications simulating high-impact security issues to benchmark Mobile PentestAI’s iOS scanning capabilities, focusing on common and critical weaknesses seen in the IOS mobile application.
Key vulnerability categories include:
- Deeplink & URL Handling Flaws – Deeplink CSRF, deeplink auto-triggering sensitive actions, spoofed URL display, and deeplink information disclosure.
- Injection & Execution Issues – HTML injection, Stored XSS, and WebKit access to internal files from untrusted HTML.
- Authentication & Session Management – Login brute force, PIN code bypass, and unencrypted session storage with arbitrary file access.
- Cryptographic & Data Security Flaws – Hardcoded secrets, weak hashing for security logic, persistent tracking, and improper TLS certificate validation.
- File & Privacy Violations – Path traversal attacks and information leakage to third parties.
🔐 SAML Authentication Support
- SAML-Based Single Sign-On (SSO) – Introduced support for SAML authentication, enabling organizations to integrate with their existing Identity Providers (IdPs) for secure, centralized user management.
- Optional Password Authentication – Organizations can now disable password-based sign-in, enforcing exclusive authentication via their SAML IdP for stricter access control.
- Automated Account Provisioning – Added support for automatic account creation upon first SAML login. Admins can choose to disable this and require explicit invitations for new users.
🛡️ Threat Center
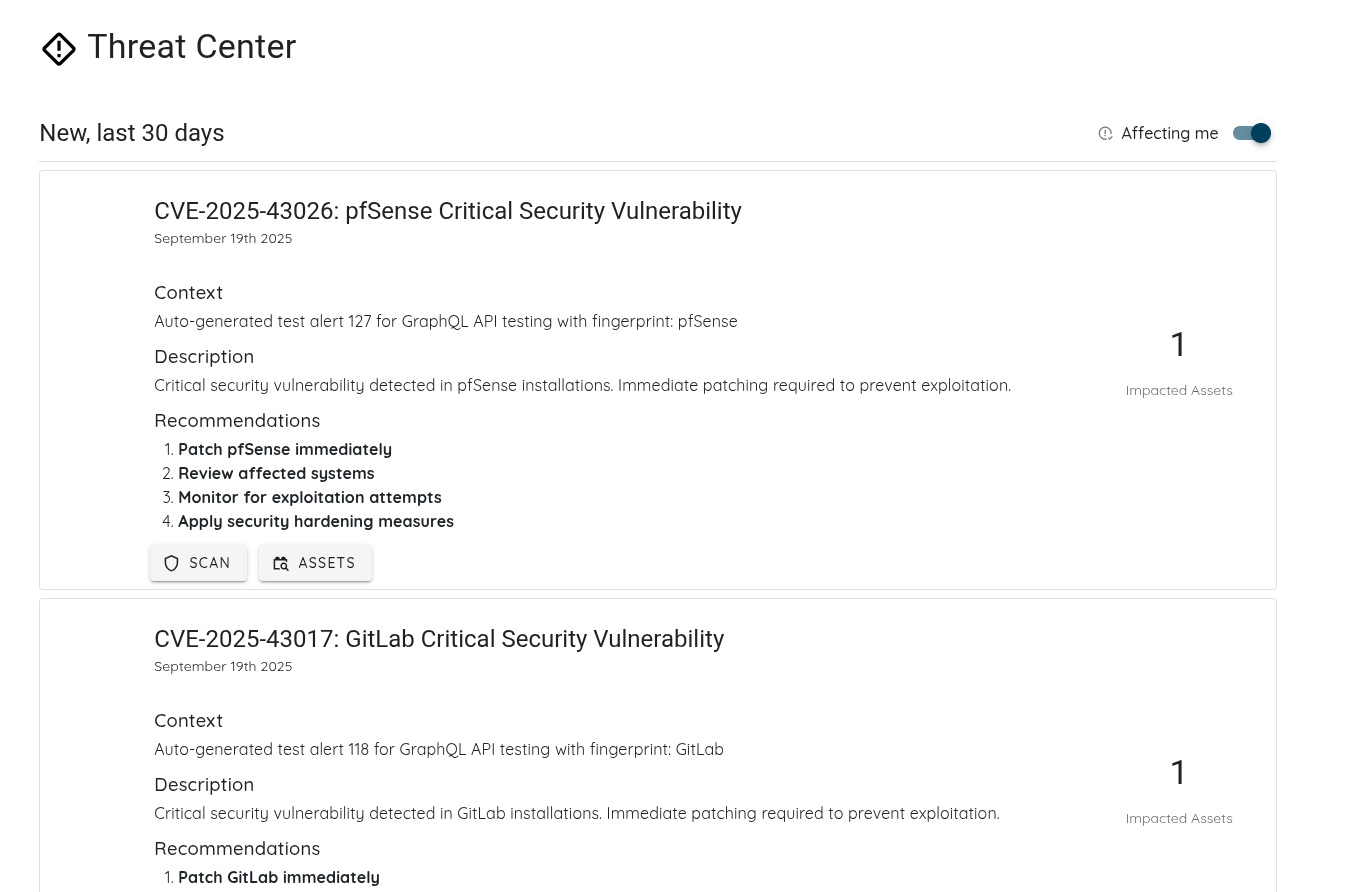
- Filter CVEs by Affected Assets – We've added a new toggle in the Threat Center that lets you view only the CVEs affecting your own assets. When enabled, this filter helps you focus on the vulnerabilities that matter most to your environment.
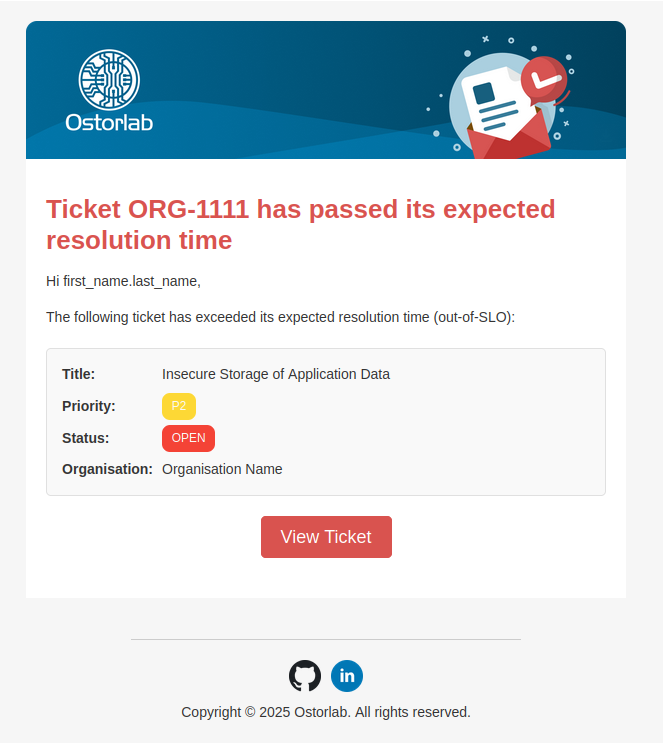
🔔 Notification: Out-of-SLO Tickets
We've added a new notification feature for Out-of-SLO tickets to help you stay on top of urgent issues.
How it works:
- Platform Notification: You'll receive an in-app notification whenever a ticket exceeds its SLO.
- Email Notification: If you've opted in to receive emails, you'll also get a notification in your inbox.
- Recipients: Notifications will be sent to the assigned users and admins.
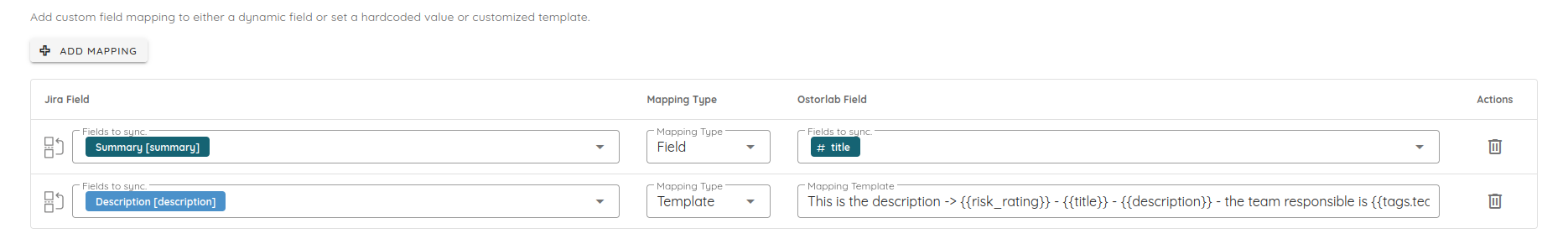
🔧 Jira Integration: Template Mapping
We've added support for template-based field mappings in the Jira integration.
- Dynamic templates: Use expressions like
{{title}} - {{risk_rating}} Riskor{{title}} [{{tags.team}}] - {{tags.platform}}to customize how data is sent to Jira. - How to use: In your Jira integration settings, select "Template" as the mapping type when configuring a field.
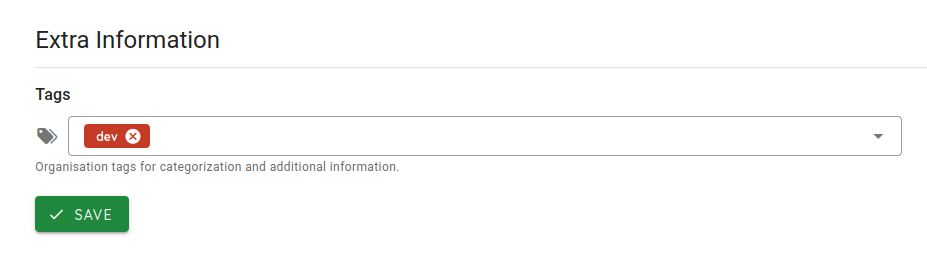
🏷️ Organization Tagging
- Custom Tags for Organizations – You can now assign tags to organizations to improve categorization, filtering, and searchability throughout the platform.
This helps teams better manage tenants based on region, priority, use case, or any internal taxonomy.
🕷️ Crawler Improvement
- In depth Web Crawling – Enhanced the crawler to explore web target more thoroughly, increasing coverage of deeply nested routes and dynamic content.
- Faster Crawling Performance – Optimized crawling speed for quicker scan execution without compromising accuracy.
🪲 Bug Fixes & Enhancements
- Automation Rule Execution Fixes – Resolved bugs affecting the execution of automation rule actions, ensuring correct behavior based on defined filters.
- Ticket SLO Calculation Fix – Fixed an issue where SLO times for tickets were incorrectly computed, improving accuracy in tracking remediation timelines.
- Markdown Rendering Enhancements – Improved Markdown rendering for better readability and formatting consistency across the platform.
- UI Fixes & Enhancements – Implemented minor UI bug fixes and usability improvements across various sections of the platform.
📂 IDE Improvements
- Improved file persistence for Android scans to ensure all decoded files are reliably saved.
🐒 Monkey Tester
-
Prompt-Based Input Fixes – Resolved bugs in the Monkey Tester when executing prompt-based input during dynamic scans, improving reliability and coverage.
-
CI/CD Support for Prompt-Based Input – Added the ability to define and pass custom prompts via OXO CI/CD workflows. This enables streamlining testing for flows that require complex user interaction or authentication steps.
⬇️ Multi-Country Android App Download Support
- Expanded Availability – Added support for downloading Android applications in Qatar 🇶🇦, Indonesia 🇮🇩 and Malaysia 🇲🇾
📚 Documentation Improvements
UI Prompts
Add documentation to describe how to use UI prompts feature, including:
-
Creation and configuration of a UI Prompt with step-by-step instructions.
-
Selecting and applying UI Prompts when running a scan.
-
Viewing and analyzing scan results with UI Prompts to enhance test coverage.
Mobile Scan Prerequisites
Add documentation to explain how mobile app protections can impact scanning and analysis.
- Overview of protection mechanisms and their impact on testing.
- Recommended multi-phase testing strategy to ensure full coverage.
AI Pentest Scan
Add tutorials for creating AI Pentest scans on mobile and web targets, with step-by-step guidance for selecting targets, configuring prompts, setting credentials, and customizing scan options for deeper, focused testing.
Mobile AI Pentest Scan →
Web AI Pentest Scan →
Use IDE: AI Pentest
Add documentation to show how to access and analyze AI Pentest results from the IDE, with a step-by-step walkthrough of the dashboard, threat intel, risks, and detailed task analysis.