Wed 28 August 2024
🛡️ Open-Source OXO
- We are happy to announce the release of OXO Titan, an intuitive User Interface (UI) to transform user interaction with OXO, a vulnerability scanning orchestrator that automatically binds tools together allowing for rapid scale. This OnPrem UI encapsulates OXO's capabilities within an accessible interface, democratizing advanced security scanning techniques. By bridging the gap between the myriad of complex tools and a simple UI, OXO Titan streamlines operations and enhances the user experience.
- The OXO scan process now exits automatically once completed, streamlining your workflow.
To learn more about OXO Titan, read the full article.
📊 PDF Reports
- Track Vulnerability Trends: Easily monitor your asset's vulnerability trends over the last 6 months with our new
graph that breaks down vulnerabilities by risk rating.
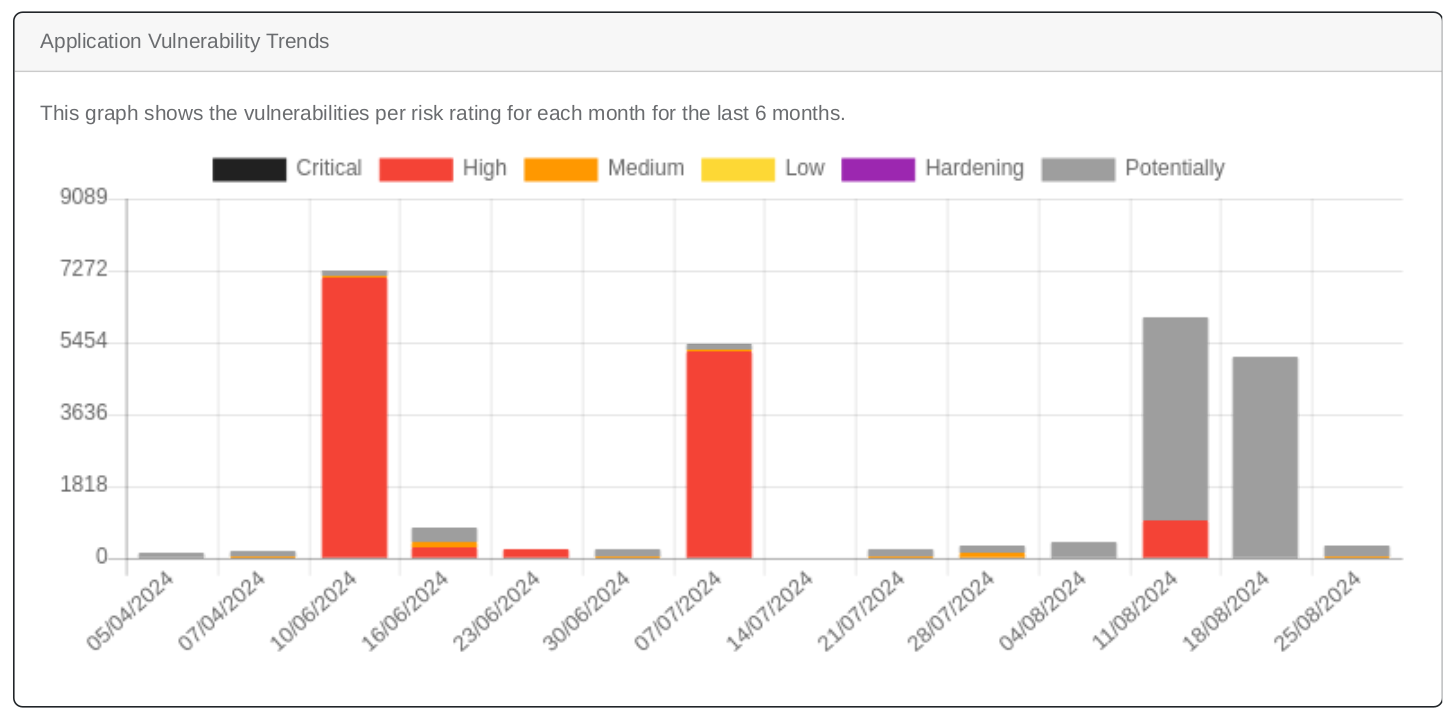
This graph shows the vulnerabilities per risk rating for each month for the last 6 months - See Open vs. Closed Vulnerabilities: Quickly understand the state of your vulnerabilities with a new graph
summarizing open and closed issues.
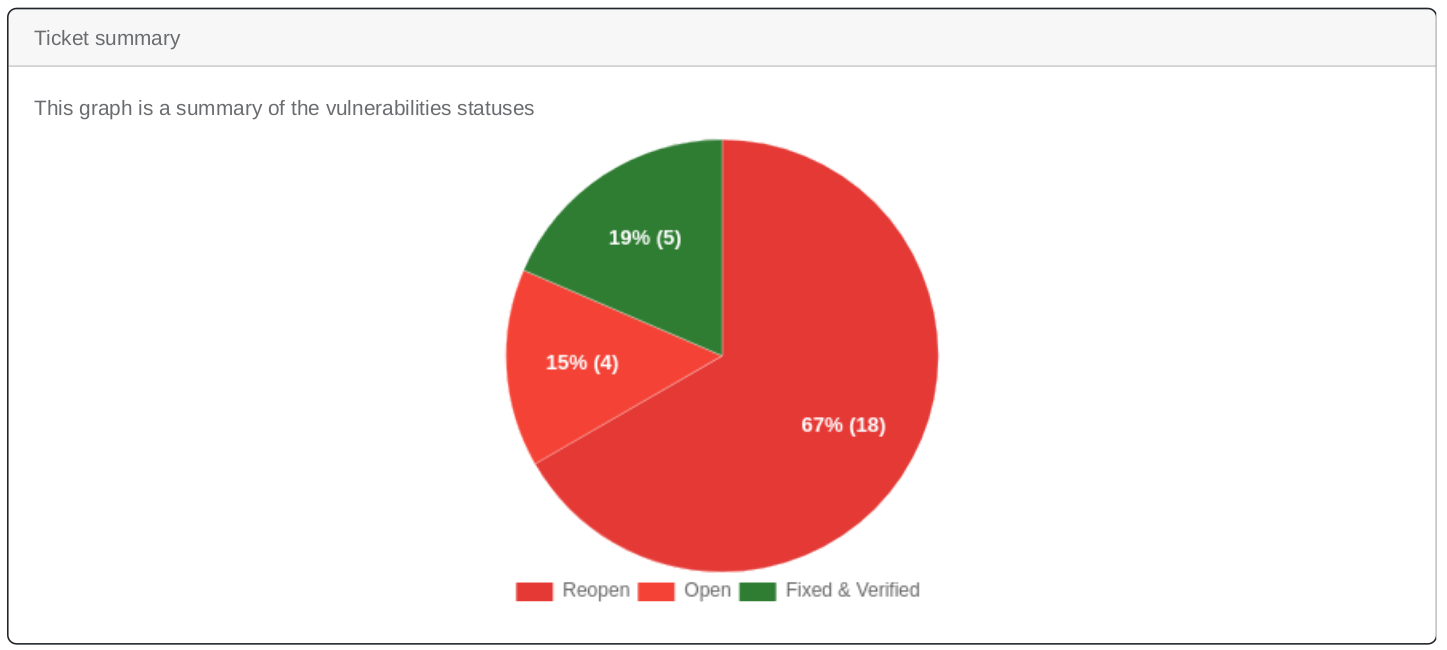
This graph is a summary of the vulnerabilities statuses - Identify Critical Issues Faster: A new graph now highlights the top 10 most severe vulnerabilities, helping you
prioritize critical issues.
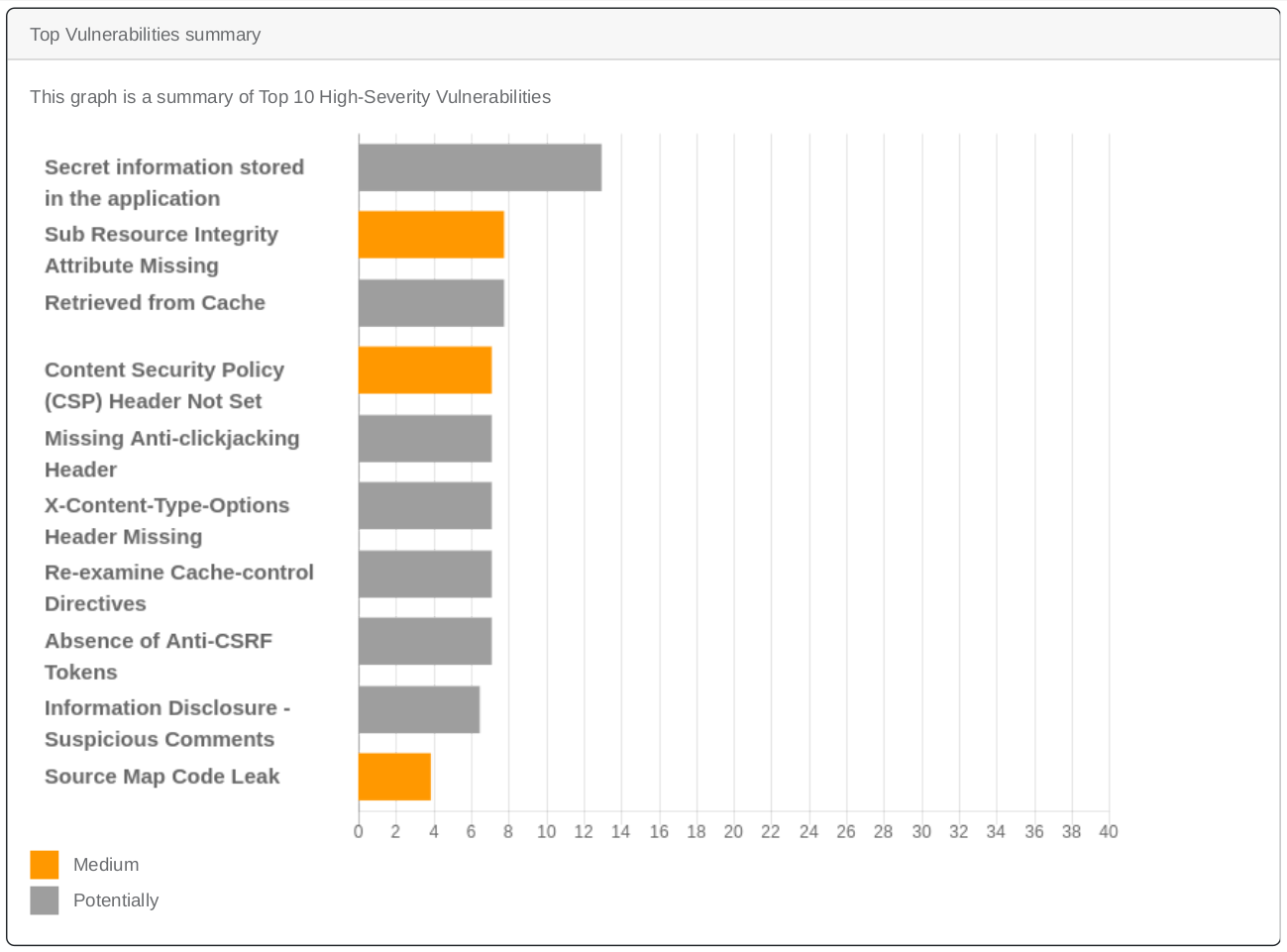
This graph is a summary of Top 10 High-Severity Vulnerabilities
⚡📡 Attack Surface
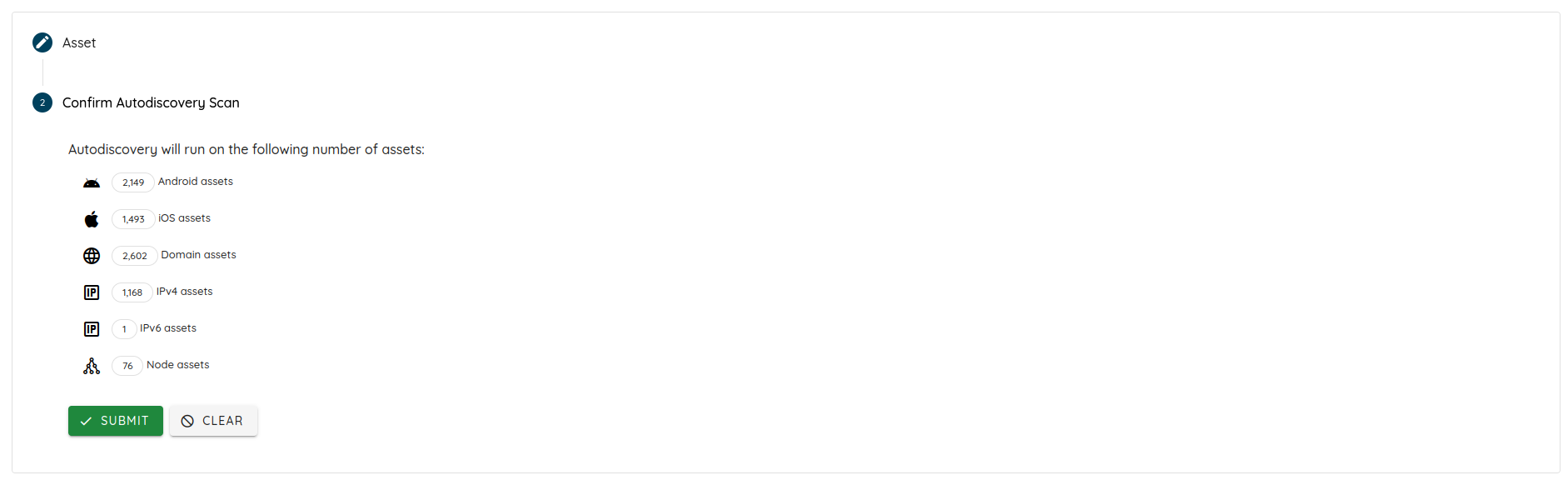
- Added support for running an autodiscovery scan. Autodiscovery enables continuous monitoring of an organization's
infrastructure to detect missing and rogue assets. This helps with finding blind spots like forgotten or missing
acquisition infrastructure, unaccounted-for dev and production machines, or lost assets during internal restructuring
and staff change. To run an autodiscovery scan, go to the new scan page and
select Attack Surface.
- Improved Asset Filtering: Filter assets more effectively by certificate details, including serial number, subject, issuer, and validity dates.
- Enhanced Search Functionality: Search more accurately with the fixed exclusion search feature, ensuring you find exactly what you need.
🔍 Detection
- Enhanced vulnerability assessment with support for the Common Vulnerability Scoring System Version 4.0 (CVSSv4). This
can be accessed on the details page of a vulnerability.
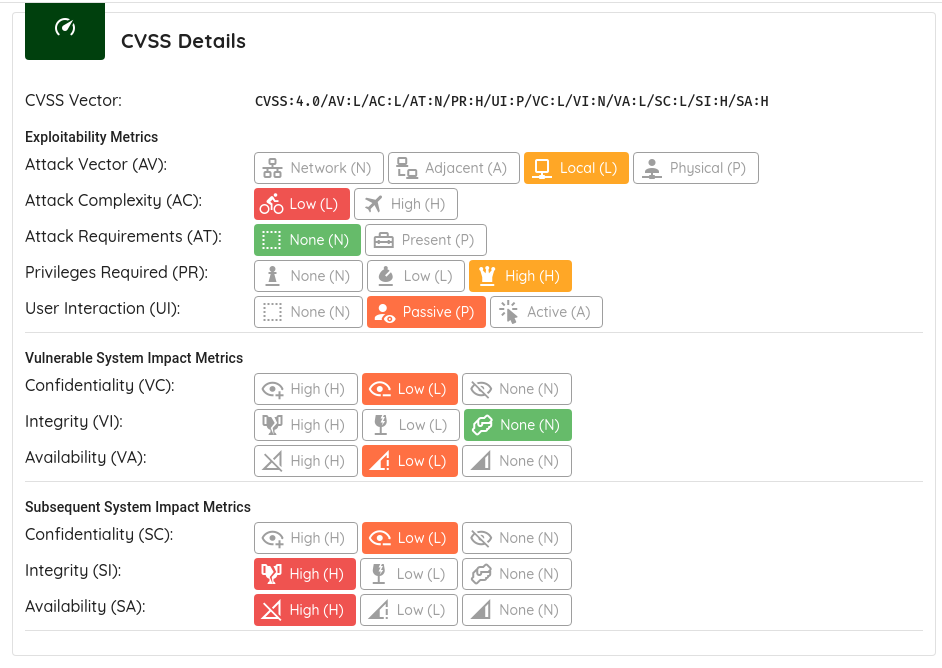
Vulnerability CVSS4 details - Known Exploitable Vulnerabilities: Enhanced security tracking by adding new CVEs -
CVE-2024-38077,CVE-2021-33044,CVE-2024-5932,CVE-2024-28986, andCVE-2022-31814. - Added support for patched versions, minimizing false positives and ensuring your vulnerabilities are accurately reported.
- Fixed an OpenSSH False Positive, ensuring only relevant vulnerabilities are reported.
- Fixed a bug where invalid targets were scanned due to incomplete URL configuration (missing port, scheme, or host). This fix ensures that no inaccurate results are reported.
- Added support for exposing the OS from scans, helping you gain more precise fingerprinting details.
- Fixed a bug where Microsoft authentication was not working, improving the call coverage of web scans.
⚠️ Threat Center
Support for Dahua network IP cameras, pfSense open-source firewall and router software, and Traccar GPS tracking. The addition of these targets will help flag assets that are affected by high-severity threats with active exploitation.
📘 Knowledge Base
- More Accurate Vulnerability Scores: We've fixed the CVSSv3 Vector for the Django Debug Mode to provide more precise information.
- Improved Technical Details: The Insecure Register Receiver Flag Technical details have been fixed so that they're correctly rendering, giving you better clarity on a vulnerability's details.