Mon 27 November 2023
Since the last OWASP Mobile Top 10 was released, we've seen new types of security problems like Dependency Confusion, Task Hijacking, and App Impersonation.
The OWASP Top 10 for 2023 is a big update. It brings new ways to protect mobile applications and deals with these new security issues. Key developments have emerged in mobile security, profoundly influencing the latest Top 10. Android and iOS platforms have gone through significant changes, enhancing their security features while at the same time introducing new attack surfaces with new potential vulnerabilities.
Noteworthy advancements include the introduction of instant apps, the integration of biometric authentication, and the expansion of iOS extensions.
Parallel to these platform changes, mobile applications have grown in complexity and size. Emerging frameworks like Flutter and React Native are redefining application development, presenting opportunities and security challenges.
Most importantly, the role of mobile apps has expanded beyond traditional boundaries. Their integration into critical sectors such as industrial systems, IoT, military, and automotive industries underscores the growing importance and impact of mobile security on a larger scale.
Behind The Scenes
Given the rapidly evolving landscape of mobile security, the need for an update to the OWASP Top 10 for 2023 was clear.
This new edition results from a significant commitment from various contributors and corporations. Special recognition is due to Milan Singh Thakur, Kunwar Atul, Mohammed Junaid Tariq, and Stefen Lortz for their notable contributions.
Additionally, Google provided valuable data, and Japan CERT offered insightful feedback and shared their top 10 findings.
Ostorlab played a crucial role, with Alaeddine Mesbahi and Mohamed Benchikh being key contributors. We summarized a vast database of over 20 million vulnerability entries collected over the years, greatly enriching the research.
The development of the Top 10 spanned several months and involved weekly public meetings. These sessions, lasting between 30 to 60 minutes, were instrumental in discussing progress, actions, tasks, and opinions.
The initial focus was establishing a methodology for drafting the new Top 10, emphasizing a data-driven approach. This required extensive data collection from various stakeholders to minimize bias from any single data source, a challenging and time-consuming task.
Once the data was collected, it underwent a process of cleaning, normalization, and analysis. After consulting a list of stakeholders, a draft of the Top 10 was prepared.
A key consideration was how to balance the list, factoring in aspects like prevalence, impact, and ease of use. Each aspect was carefully scored, and the final rankings were determined based on these scores.
This method resulted in a list that reflects what is perceived as the industry's priorities, offering a balanced view of prevalence, impact, and ease of detection.
The New Release
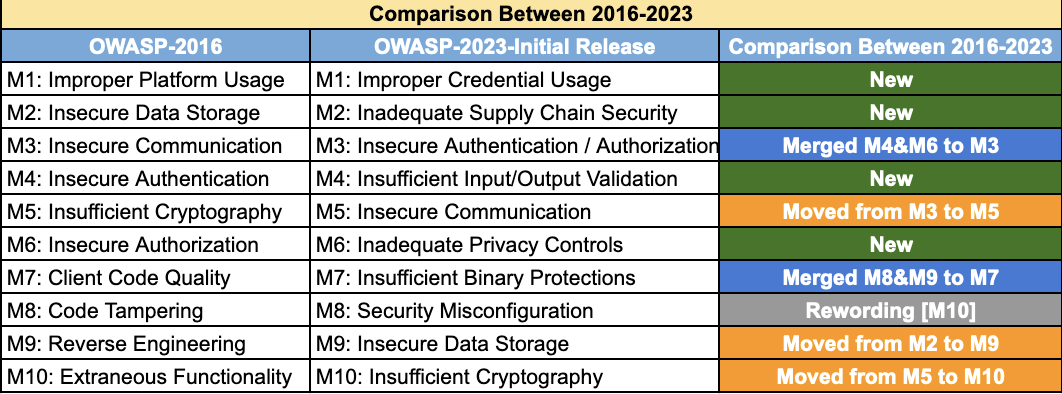
The latest OWASP Top 10 for 2023 presents some notable changes and introduces new challenges.
New entries have emerged at the top of the list. These include Improper Credential Usage and Inadequate Supply Chain Security. This shift reflects a worrying trend where the mishandling of secrets, such as API keys and hardcoded credentials, has become alarmingly commonplace.
Moreover, supply chain issues, particularly those involving outdated and vulnerable dependencies often sourced from open-source, have risen in prevalence.
Another critical area is the fusion of previous issues related to authentication and authorization, which are now more prominent due to efforts to simplify these processes in mobile applications. This includes integrating OAuth, biometric authentication, and support for offline modes, all introducing various vulnerabilities.
The fourth issue is surprisingly new as it sits among the most common issues in other categories like Web Top 10.
This is because mobile applications are getting more complex, accepting input from other applications through IPC or can be interacted with from a browser using custom URLs and custom schemes or Webview javascript interfaces.
The issue of insecure communication, though downgraded from its previous third position, remains a significant concern. Despite efforts by operating systems to implement features like network security configurations, clear text traffic, and other insecure practices persist.
Privacy issues have risen to the sixth position, fueled by growing awareness and concern for privacy-respecting apps. However, challenges remain, especially with third-party ad SDKs that collect excessive data. Common privacy breaches include collecting SSID endpoints to track user locations and movements and identify relations between users.
Binary protection is another critical issue, encompassing the leakage of source code, debug symbols, and lack of obfuscation.
Security misconfiguration ranks eighth, leading to severe vulnerabilities like enabling debug modes in SDKs or Webview instances, which can result in session leaks or remote exploitation.
Insecure data storage, once a top concern, has decreased its ranking. This change is attributed to operating system improvements, such as Android's more secure file provider and new storage access modes, reducing the impact of these vulnerabilities.
Lastly, insecure cryptography, though still a concern, has also seen a decline in prevalence, thanks to the introduction of secure libraries that simplify and strengthen cryptographic implementations. This is also due to the complexity of exploiting these vulnerability classes.
Leveraging the new OWASP Top 10
The OWASP Top 10 for 2023 is a crucial tool for prioritizing security checks within mobile applications. To utilize this effectively, consider the following approach:
-
API Usage Review: Catalog all API usage within your application. Ensure that API keys and secrets are not embedded in the app. Assess the use of API key pinning and verify the appropriate permissions for these keys.
-
Dependency Verification: Employ lock files and Software Bill of Materials (SBOM) to list all dependencies. This includes thoroughly checking native dependencies to confirm they are current and secure.
-
Authentication Mechanism Audit: Compile a list of all authentication methods used, such as password-based, SSO, 2FA, SAML, and OAuth. Rigorously review the security of these implementations.
-
API Access Control: Evaluate the access controls for all APIs in the application.
-
Interface Security Analysis: Identify all exposed interfaces of your application, including activities, URL schemes, and deep links. Ensure they securely process data.
-
Backend and Network Security: Ensure all backend links in your application use encrypted traffic. Check that TLS settings are robust and network security policies are properly configured.
-
Privacy Compliance: Review all data collection practices. Confirm that no third-party SDK is gathering user data without consent and that all practices comply with privacy regulations.
-
Binary Protection: In the built APK or IPA, confirm that no symbols or source code are exposed. Apply obfuscation where necessary.
-
Configuration and Data Storage Security: Examine configuration settings in the manifest and info.plist, along with settings in various frameworks. Verify that local storage is secure and sensitive data is encrypted with standard, secure methodologies.
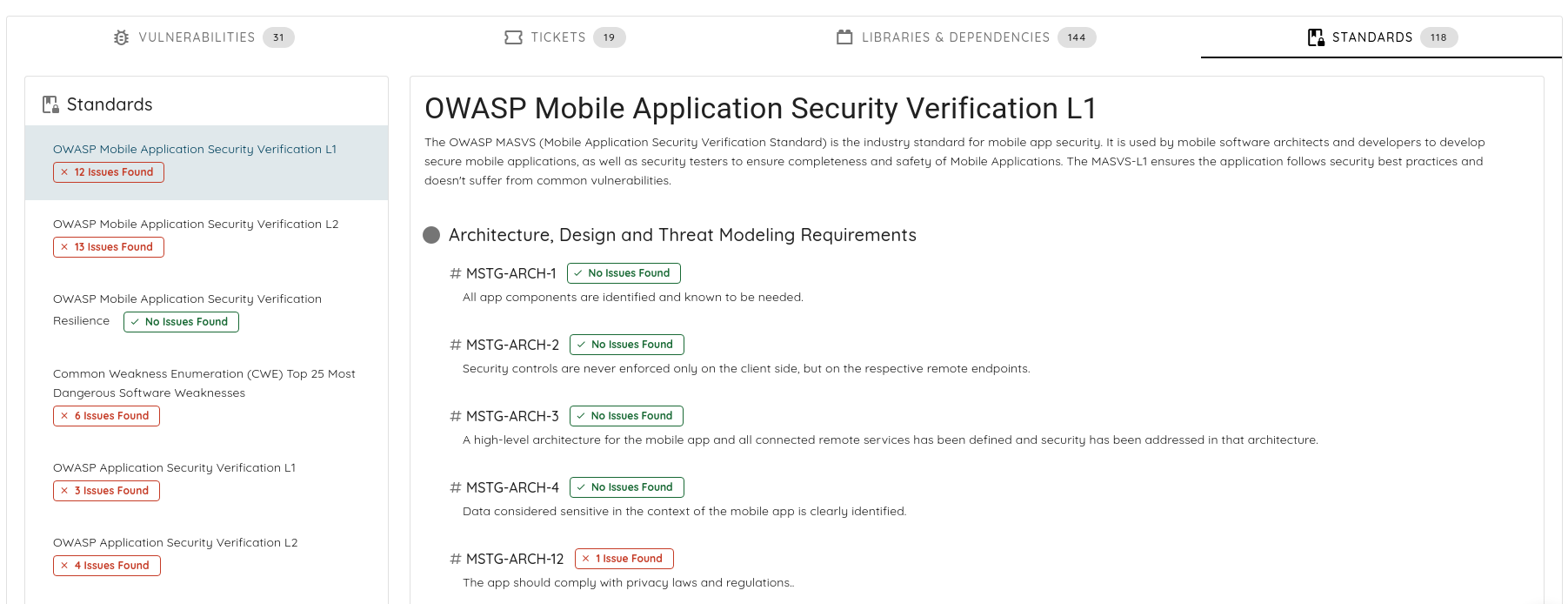
Additionally, the Ostorlab platform can be a valuable resource to automate these checks. It offers comprehensive analysis capabilities covering secrets, dependencies, insecure coding practices, communication, and backend APIs. Ostorlab's extensive capabilities, developed over many years, support a wide range of frameworks and provide a thorough security overview for your mobile applications.