Mon 21 March 2022
yevhsec1@ wrote an informative comparison of iOS application security scanners at his blog
at ios-apps-security-scanners-practical-comparison
yevhsec1@ blog focused on the detection aspect and went over the scan results on multiple known vulnerable iOS
applications.
While the article recommended Ostorlab, it only touched slightly on the actual differences between the platforms, their coverage, and their true capabilities.
In this article, we hope to provide a more comprehensive view while at the same time highlighting what truly differentiates Ostorlab from existing platforms - in addition to its improved detection capabilities.
| Ostorlab | Nowsecure | MobSF | ImmuniWeb | Appknox | Quixxi | Oversecured | |
|---|---|---|---|---|---|---|---|
| Framework Support | Native and Multiplatform (Crodova, React Native, Flutter, Xamarin ...) | Native | Native | Native | Native | Native | Native |
| Static Taint Analysis: | Yes |
Unknown | No | No | Unknown | Unknown | Yes |
| Binary Analysis | Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Android only |
| Source Code Analysis | No | No | No | No | Unknown | No | iOS only |
| Outdated Dependencies | Yes |
Unknown | No | No | No | No | No |
| Supply Chain | Yes |
Unknown | No | No | No | No | No |
| Secrets | Yes |
No | No | No | No | No | No |
| 3rd Party Analysis | Yes |
Yes |
Yes |
Yes |
Yes |
No | No |
| Privacy Checks | Yes |
Yes |
Yes |
No | Unknown | No | No |
| Dynamic Analysis | Yes |
Yes |
Yes |
Yes |
Yes |
No | No |
| Manual Device Interaction | No | No | Yes |
No | Yes |
No | No |
| Automated Device Interaction | Yes |
Yes |
No | No | No | No | No |
| SSL Pinning Support | Yes |
Unknown | No | No | Unknown | No | No |
| Authenticated Test | Yes |
No | No | No | Unknown | No | No |
| OTP Support | Yes |
No | No | No | Unknown | No | No |
| Backend Scanning | Yes |
Yes |
Yes |
Yes |
Yes |
No | No |
| Monitoring | Yes |
Yes |
No | Unknown | Unknown | No | No |
| Direct from the store scanning | Yes |
Yes |
No | Yes |
Unknown | No | No |
| Penetration Testing Services | No | Yes |
No | Yes |
Yes |
No | No |
| Manual Analysis | Yes |
No | Yes |
No | Yes |
No | No |
| Extensibility | Yes |
No | Yes |
No | No | No | No |
| Remediation / Vulnerability Aggregation | Yes |
No | No | No | No | No | No |
| Dashboard | Yes |
Yes |
No | Yes |
Yes |
No | No |
| CI/CD Integrations | Yes |
Yes |
Yes |
No | Unknown | No | Yes |
| Ticketing Integrations | Yes |
No | No | No | Unknown | No | No |
| IDE Integrations | No | Unknown | No | No | Unknown | No | No |
| OTP | Yes |
No | No | Unknown | No | No | No |
| SAML | Yes |
Unknown | No | Unknown | Unknown | No | No |
| Team Support | Yes |
No | No | Unknown | Unknown | No | No |
| Open Source | Ostorlab Scanner and Agents | Frida and Radare2 | Yes |
No | No | No | No |
Detection Capabilities
Detecting vulnerabilities is at the core of what vulnerability scanners are expected to do. To evaluate mobile application vulnerability scanners, there are several critical attributes to look at.
First is Framework Support Coverage. Mobile applications have a rich ecosystem with diverse technological stacks and a diverse range of attack surfaces. From native Java on Android, Swift, and Objective C on iOS, to multiplatform like React Native, Flutter, Cordova, or Xamarin.
Multi-platform frameworks have gained popularity in recent years, especially Flutter, and ensuring the platform understands the framework and its internal is critical to detection.
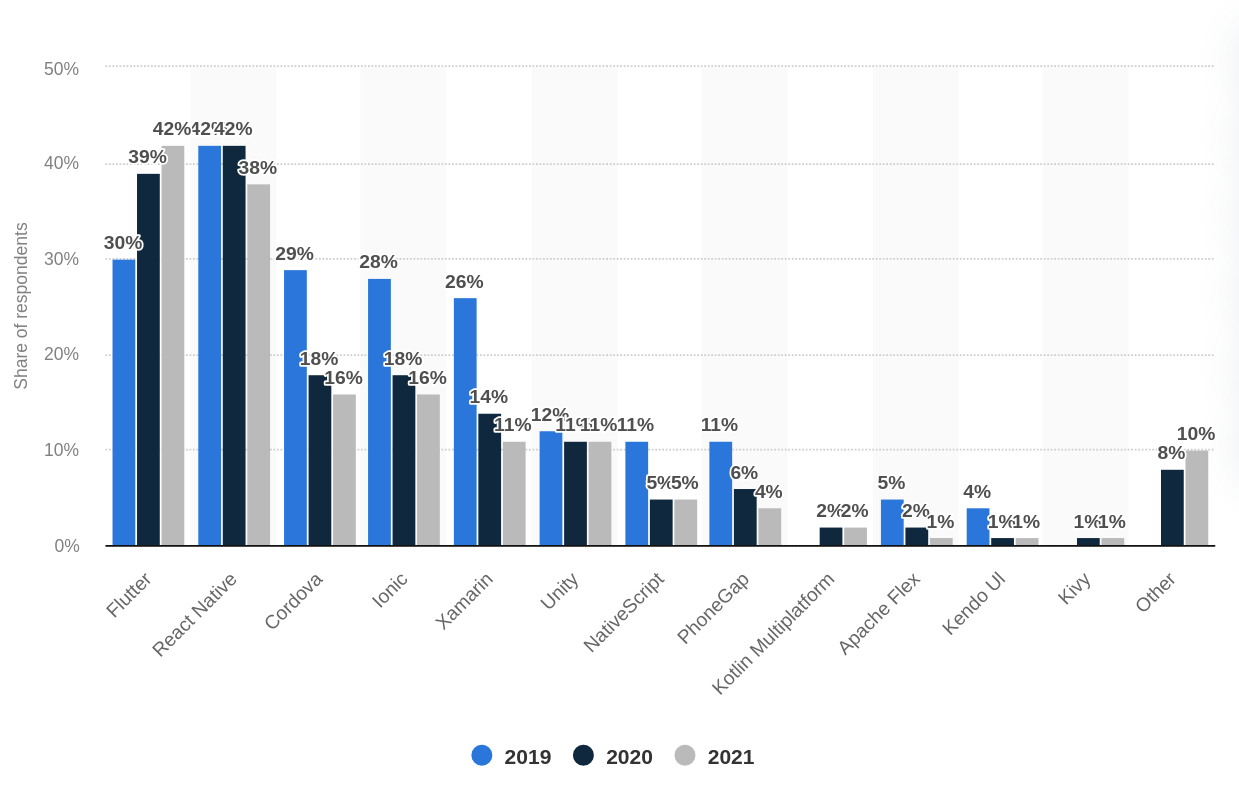
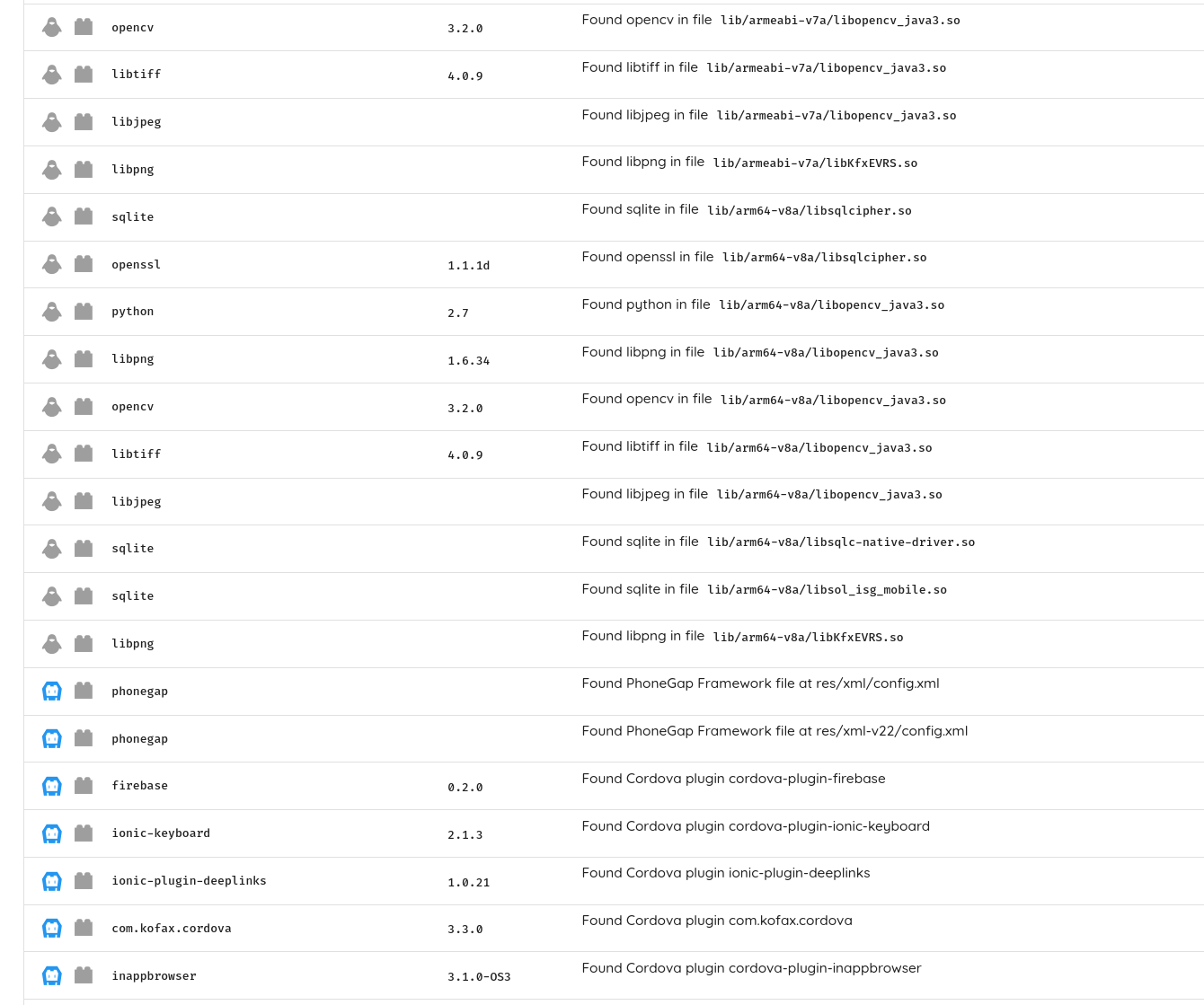
A second attribute is Static Taint Analysis Capabilities and Accuracy. Taint analysis is a core feature that enables finding complex vulnerabilities spanning long code paths. Taint analysis is powerful and resource-intensive and requires understanding the nuances of the different platforms to enable accurate detection.
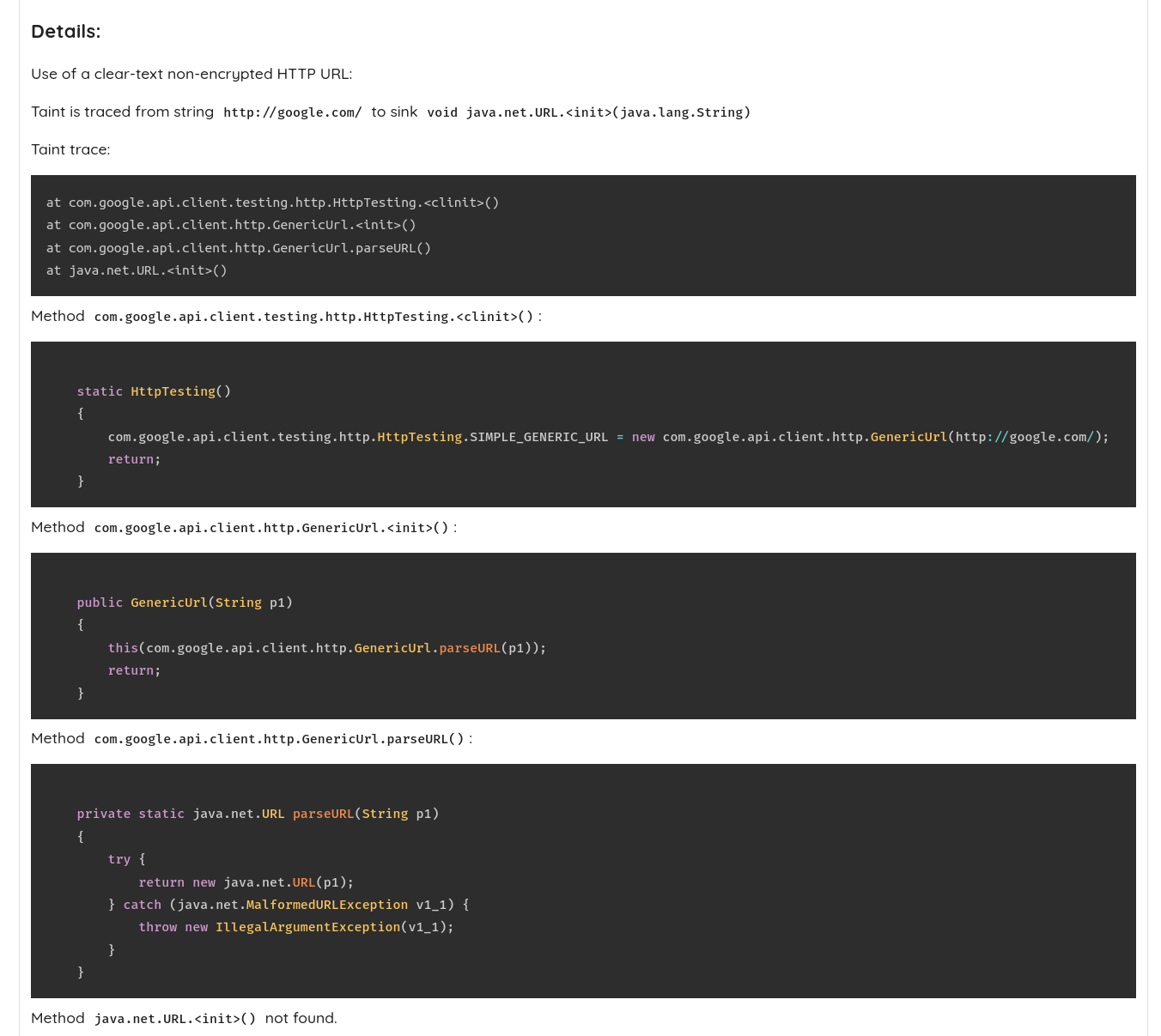
Other attributes include Outdated Vulnerable Dependencies detection, including statically compiled ones, covering both known and unknown (missing CVE) issues.
Detection of Supply Chain vulnerabilities is also critical, like dependency confusion. This vulnerability class is typical in Javascript-based applications and has become a favorite target for attackers.
Secrets and Hardcoded Keys, 3rd Party analysis, and Privacy Checks are also critical checks to look at.
Finally, Dynamic Analysis to detect complex issues that can be hidden or difficult to find because of obfuscation, code reflection, or remote code loading is a must.
Powerful dynamic analysis requires TLS and SSL Pinning Support, Authenticated Testing, including OTP Support, and backend scanning.
In all of these areas, Ostorlab checks each box, offering advanced taint analysis capabilities, detecting outdated depending, including statically compiled ones, detecting secrets and validating them, and enabling rich, dynamic analysis capabilities with authenticated testing, OTP support, traffic interception, and supply chain checks.
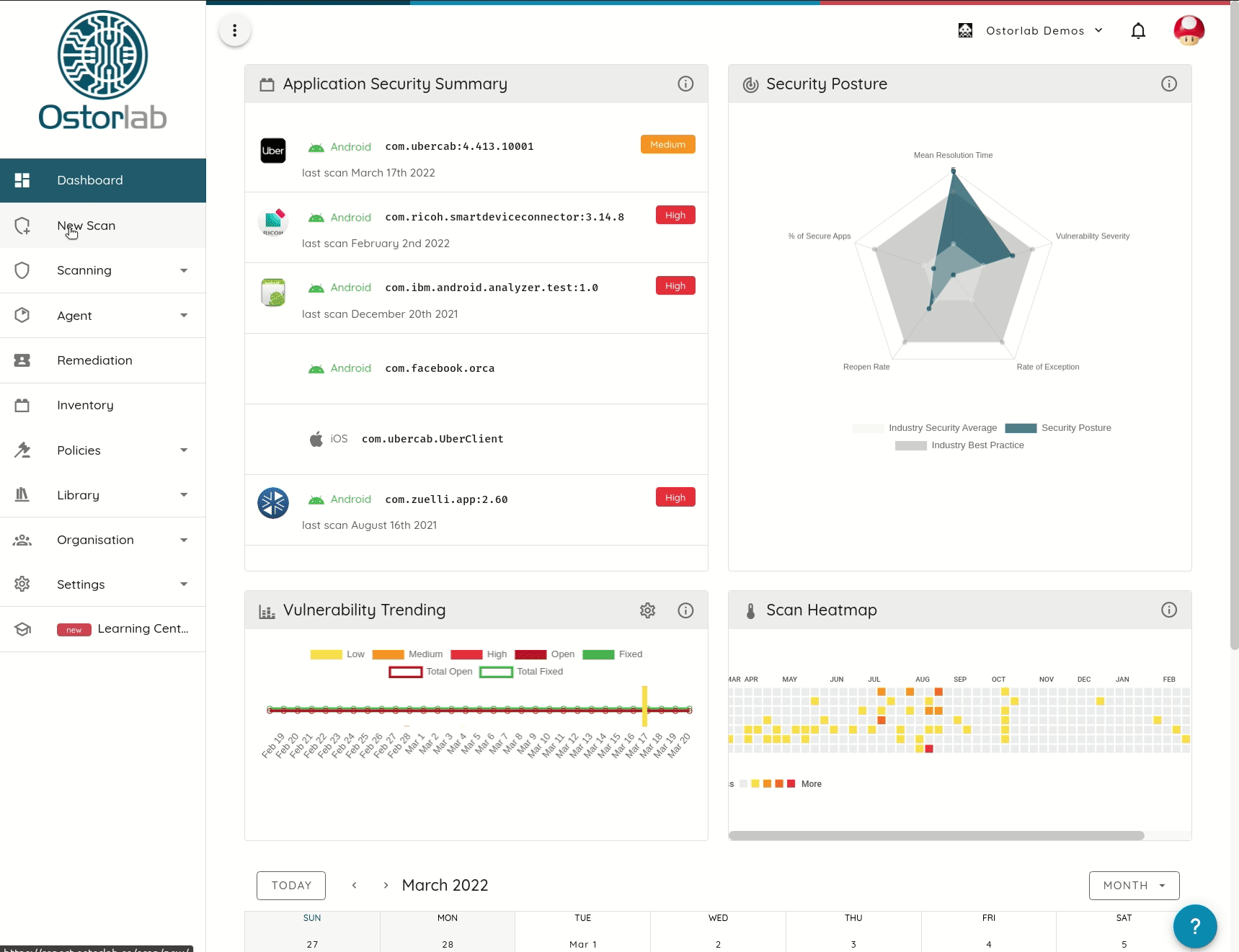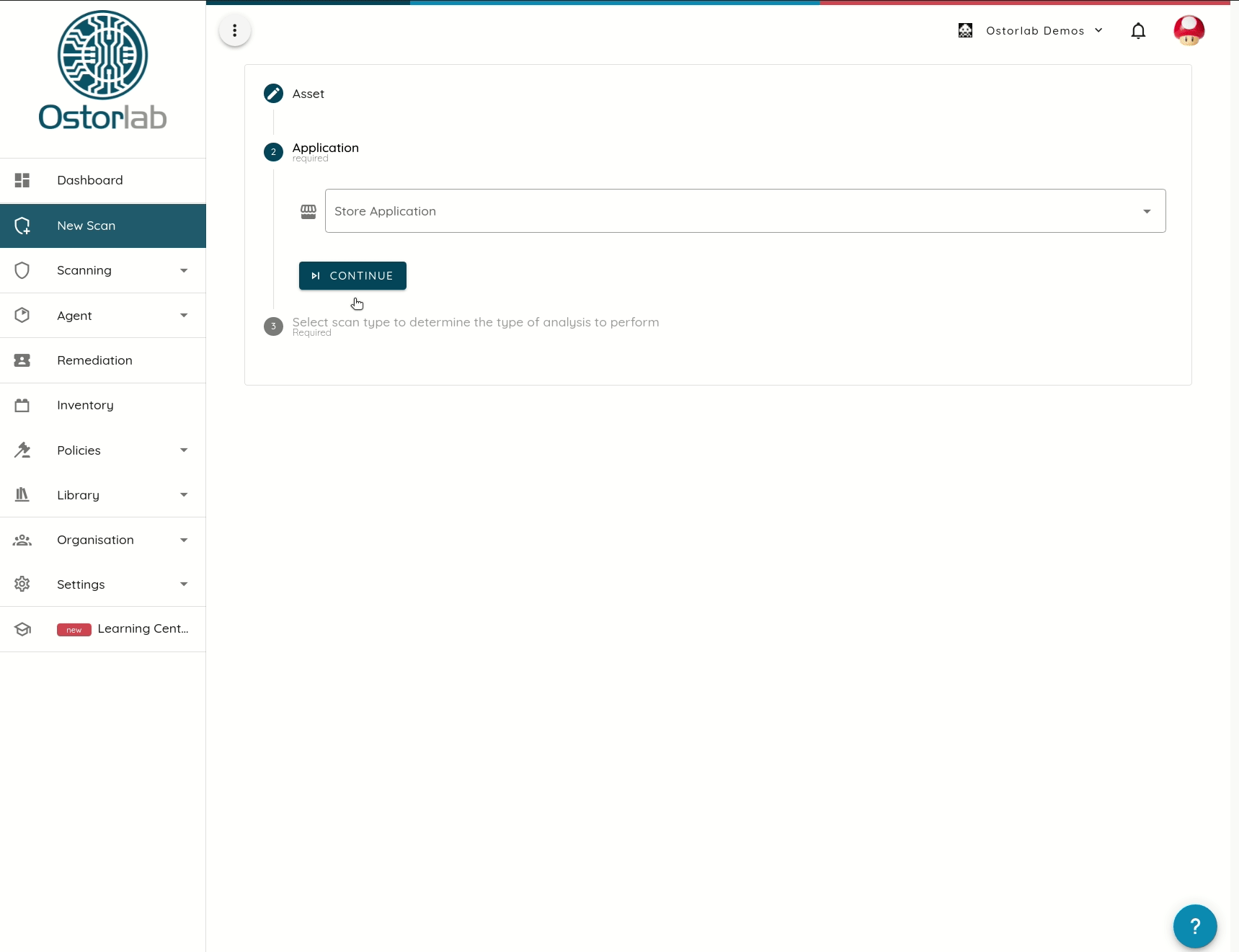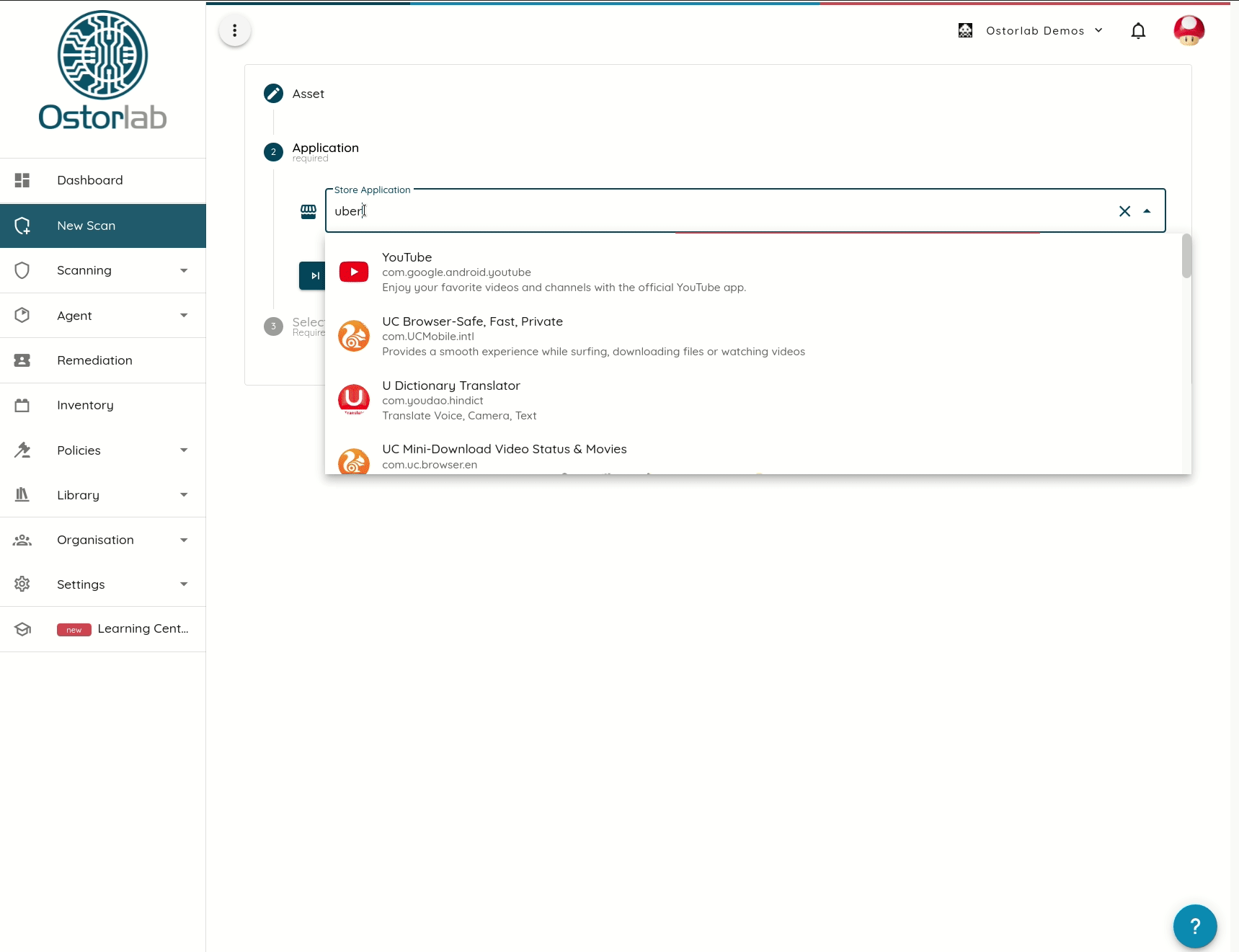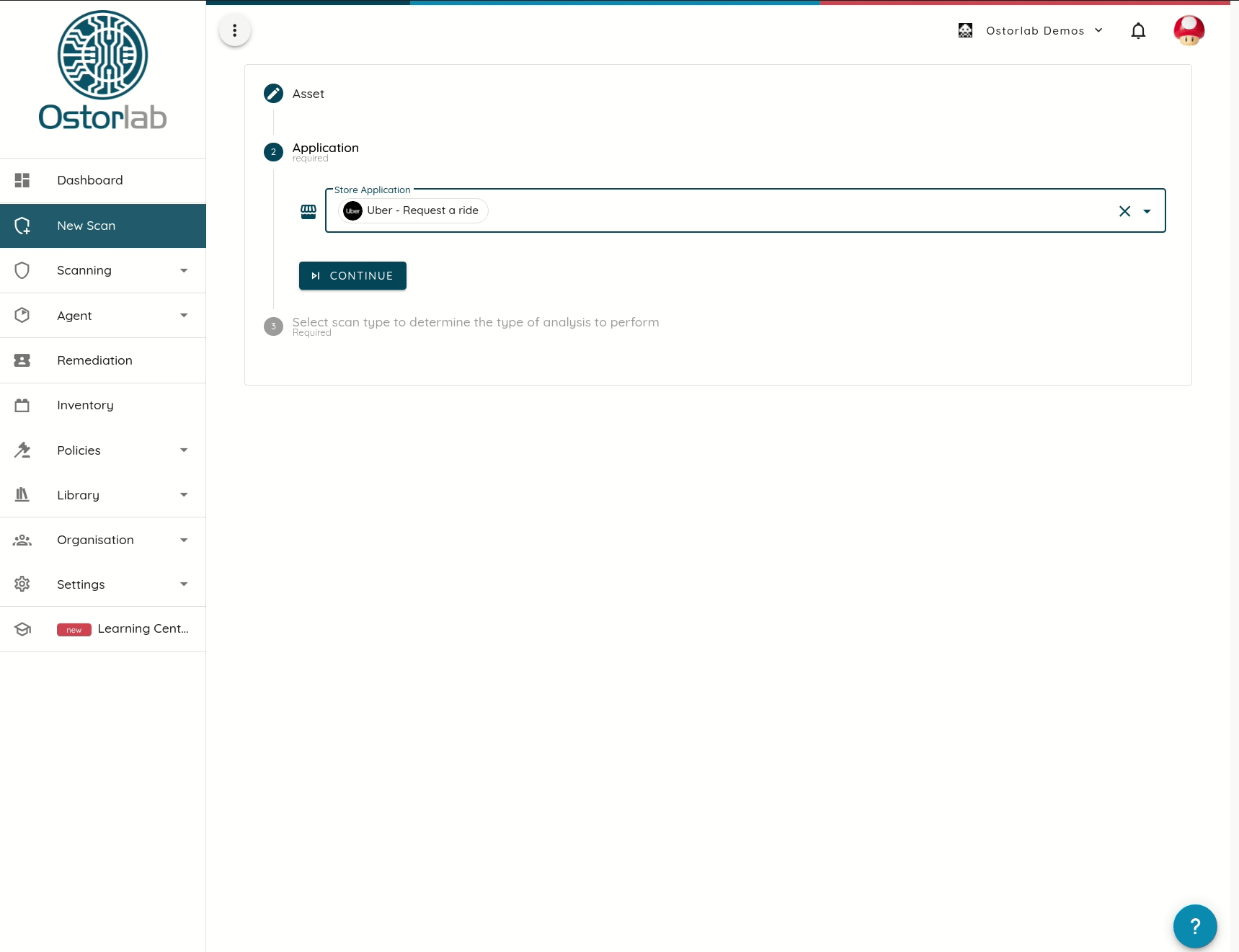
Monitoring
A critical feature of mobile application vulnerability scanners is their ability to save time to focus on complex tasks. One key aspect is enabling continuous monitoring of an application, be it from the store or integrating with CI/CD platforms like Jenkins or Github Actions.
NowSecure and Ostorlab are the only scanners to support continuous application monitoring on both platforms (Android and iOS).
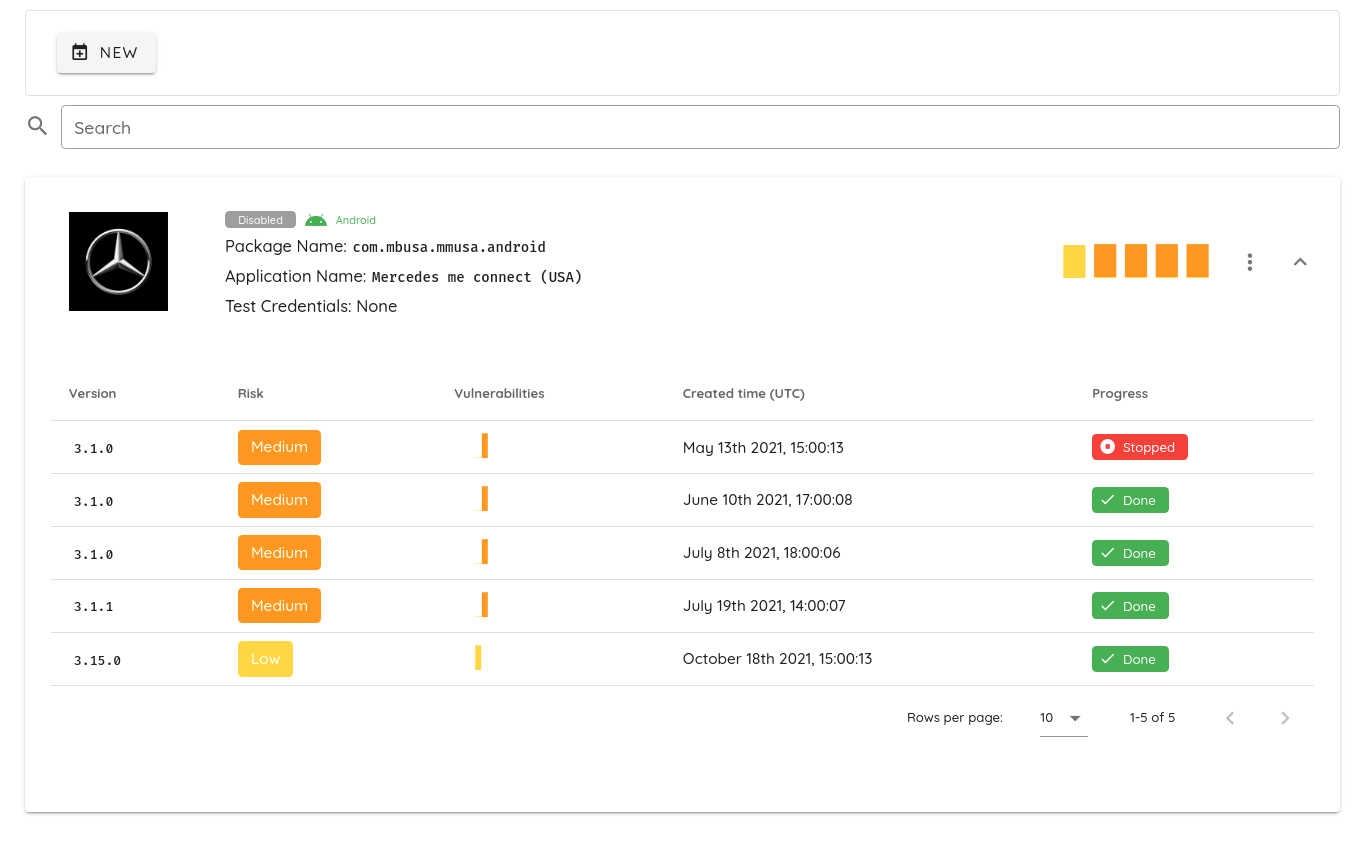
Store Access
In addition to monitoring, Store access offers a friendly experience to users and helps save time by ensuring scanning of the actual production artifacts.
Ostorlab provides the ability to scan applications directly from the store and works around devices and geo-restrictions.
A handful of other providers support store access. Some suffer from restrictions like device and location support.
Interactive Analysis Capabilities
Vulnerability detection does not stop at running a scan and looking at the results. The hard work only comes after to ensure issues get fixed.
An essential part of that is chasing variants, which might exist in 3rd party components where source code is not even accessible.
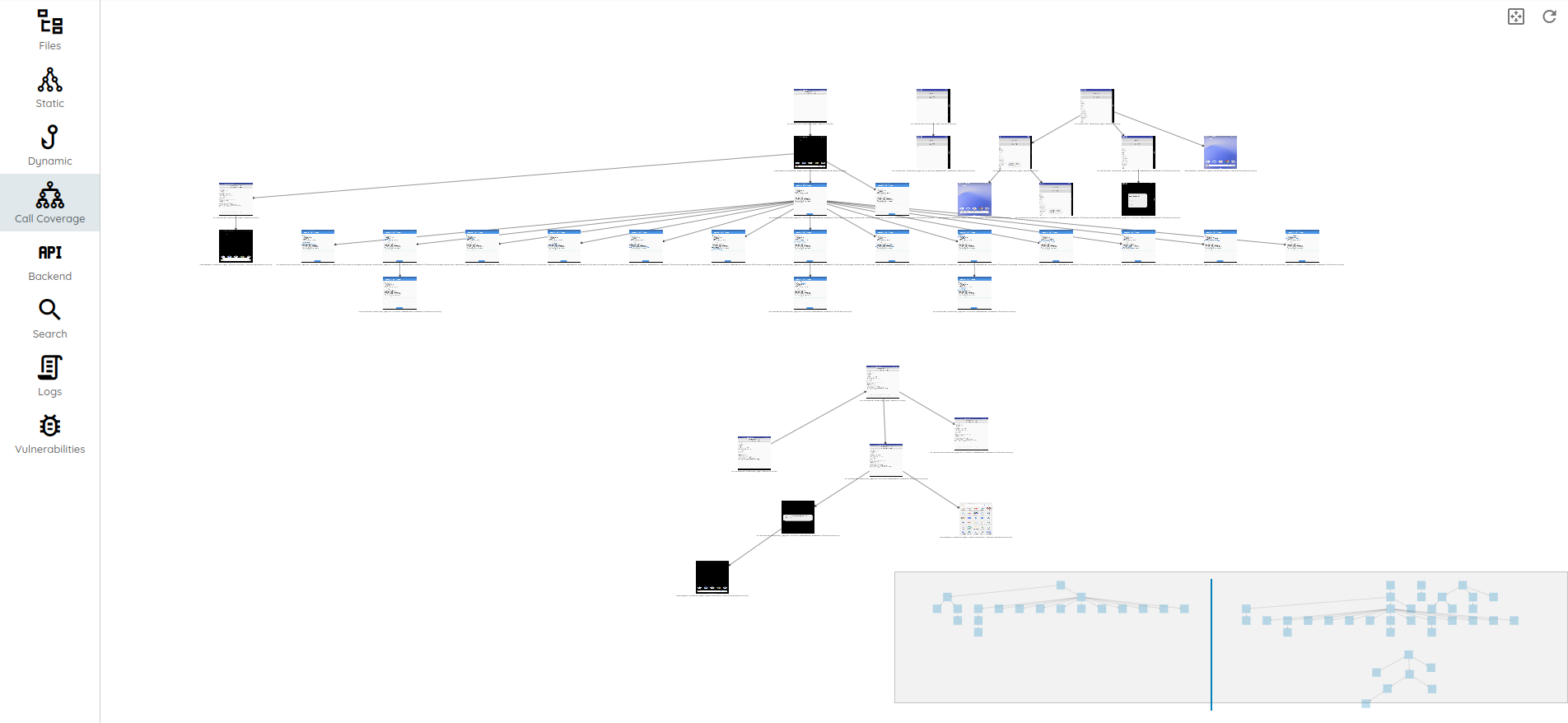
The use of an interactive analysis environment comes in handy to enable the team to understand issues and chase new ones.
Ostorlab ships with an analysis environment that enables seeing what attackers can see, which includes:
- the application decompiled source code, including native code
- call traces,
- extracted dependencies (real bill of materials),
- intercepted traffic
- UI interaction generation
- method risk profile analysis
- content indexing for fast searching
- And many many many more.
Remediation Capabilities
Fixing vulnerabilities is hard, time-consuming, and frankly not a fun experience. It doesn't make your product better or more attractive, but it has the potential of crippling an organization.
Security teams need to balance time and effort to focus on the essential, considering the probability of being targeted, ease in finding, and impact.
While it is great to fix all issues, it is practically impossible due to the sheer volume of findings security teams need to handle.
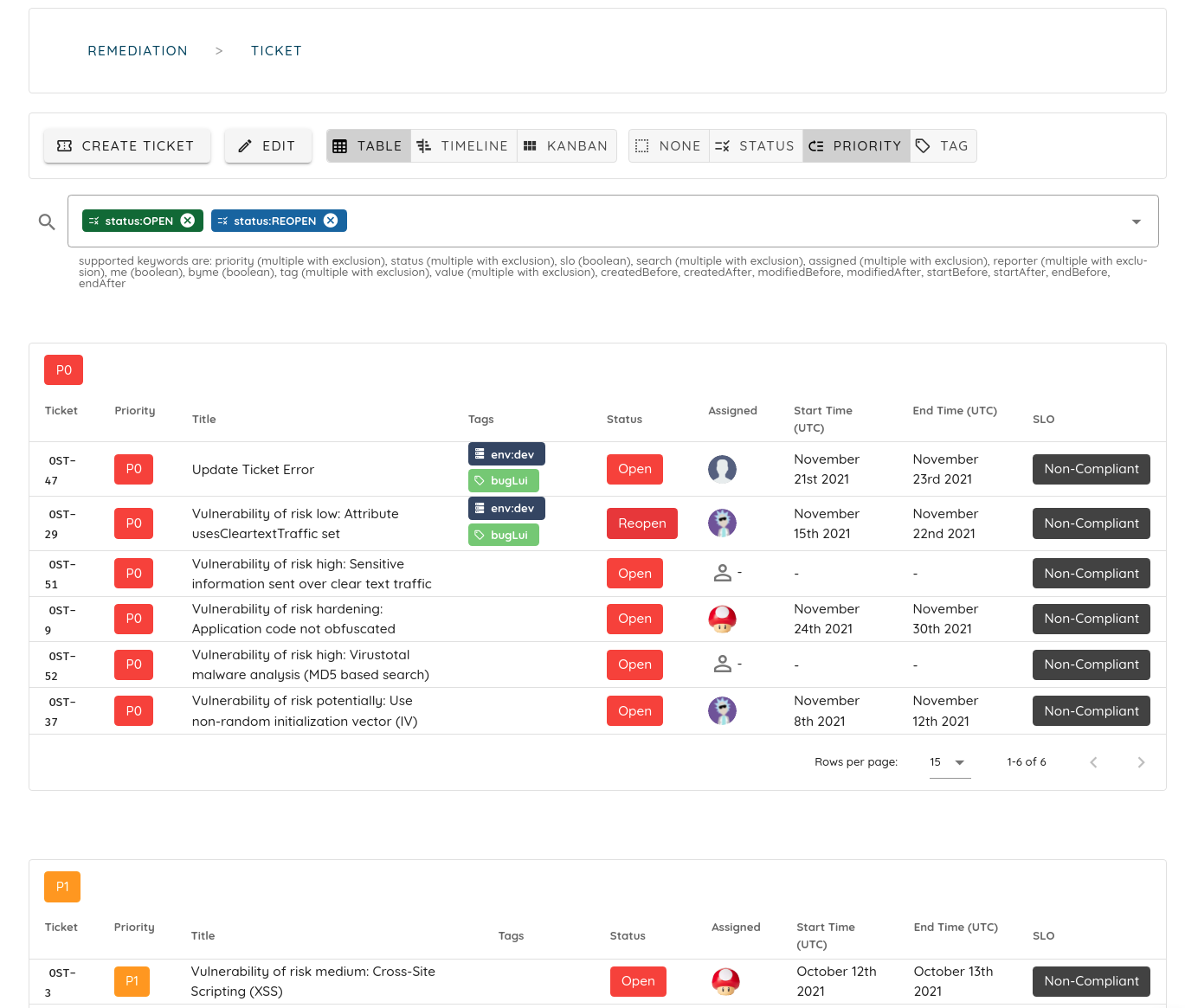
Ostorlab uniquely ships with capabilities to address vulnerability detection's acute pains and challenges. These capabilities include vulnerability aggregation into a single ticket to avoid spamming and vulnerability fatigue. It provides policy settings to ensure nothing is dropped on the floor and maintains a history of issues. It can also detect fixes and mark issues as exceptions or false positives and avoid future redundant reports.
Integrations
Platform integrations are another critical feature that helps the security and development teams save time and effort, thus eventually providing a better and more secure application.
The action of copying scan results into an internal ticketing system or manually triggering a scan with every new release can quickly become tedious and, at some point, simply decide to skip it.
Providing integrations that align with the team's tooling lowers the overhead and improves the tool's adoption within an organization.
Ostorlab provides the most extensive support with integrations like Jira, Jenkins, Github Action, and Gitlab.
Account Security
Due to the nature of data a vulnerability scanner handles, it is critical to ensure secure access to the platform.

Features like brute force detection OTP with secure implementations like TOPT or HOTP prevent authentication attacks.
Multi-organization/team support facilitates data segregation and allows external parties to access only need-to-know data.
Large organizations with internal authentication providers benefit from centralized user management and auditing with SSO support using standardized protocols like SAML or OAuth2.0.
Ostorlab is the only platform among all listed to provide secure OTP access, SAML integration, and multi-team capabilities.
Extensibility and going beyond Fixed Detection
Providing the security team with the power to reuse existing vulnerability scanning infrastructure to detect new or variant vulnerabilities is a time-saver.
However, building on top of proprietary technology is often off-putting as the work done is lost when the team decides to choose a different solution.
Ostorlab enables extensible integrations that are 100% open-source. It offers the flexibility to continue using other platforms if they choose to without losing their work and effort.
MobSF and Ostorlab are the only platforms providing these kinds of extension capabilities thanks to their open-source engines.
Open-Source and Community Support
Committing to open-source is not just about sharing source code. It is about supporting a community to address a common problem.
Ostorlab, since its inception, has been a community-driven platform that offers unlimited free scanning.
We have open-sourced the platform with a mission to provide complete and unrestricted access to all detection capabilities.
In contrast, our paid platform focuses on the enterprise features needed by large organizations to save time and effort, like powerful integration and remediation capabilities.
Thankfully Ostorlab is not the only platform supporting open-source; MobSF and NowSecure, with their notable support for Frida and Radare2, are other great examples.
Roadmap
Ostorlab already provides advanced detection, analysis environments, robust integrations, and intelligent remediation capabilities. However, we are still hard at work excited about all the new capabilities we would like to add.
This year's goal is to significantly improve our vulnerability detection capabilities through our open-source project. We have completed the first stage of creating the building blocks that the team and the open-source community can start using.
Our focus will also aim at fully automating the first stages of building a vulnerability management program to enable a better and more accurate view of an organization's infrastructure.
Work will also include improving the analysis environment by adding live auditing functionality and a powerful search and querying language.
If you want to know more about these as we announce them, you can follow us on Twitter or join our newsletter.
Tags:
autonomous