Tue 26 March 2024
Discovering & Monitoring Mobile Applications Attack Surface with Ostorlab
Managing the security of a diverse portfolio of mobile applications can be overwhelming, even for organizations with large resources. The traditional method of manually checking each application, ensuring its latest version in the store is scanned, and regularly checking for updates or vulnerabilities can quickly get tedious.
Ostorlab Attack Surface Discovery simplifies this process by automating the identification and scanning of mobile applications, significantly reducing the burden on security teams and making it a pleasant and painless experience overall.
Prepare my inventory:
- You can add mobile applications using the Discovery menu on the attack surface.
- You can either follow the steps from the UI to add the different assets or upload a CSV file with the defined fields of your mobile applications.
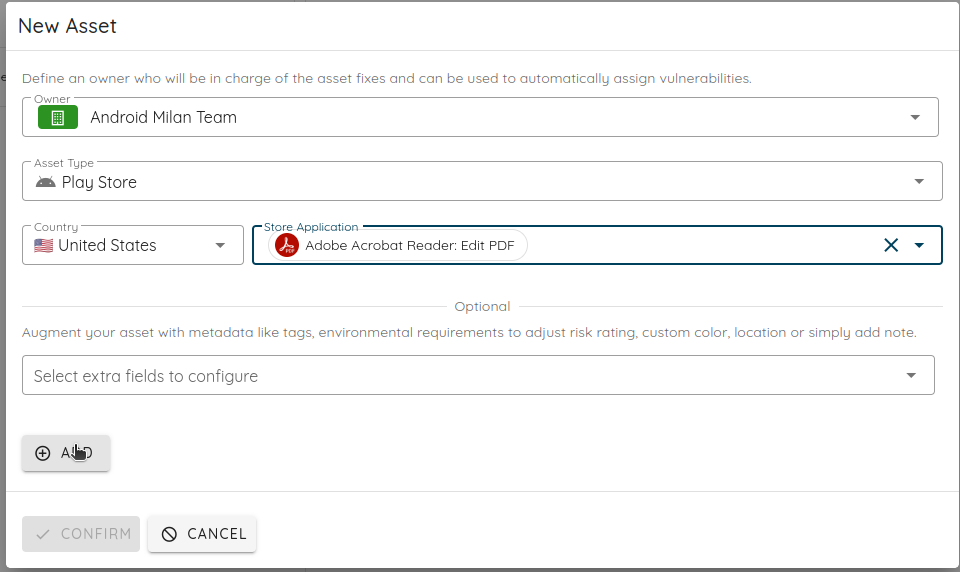
To do it from the UI, you need to define the asset's owner. It is useful to have a point of contact to report vulnerabilities and define permissions and metrics per owner.
The example below will add the Adobe Acrobat Reader application for Android and iOS.
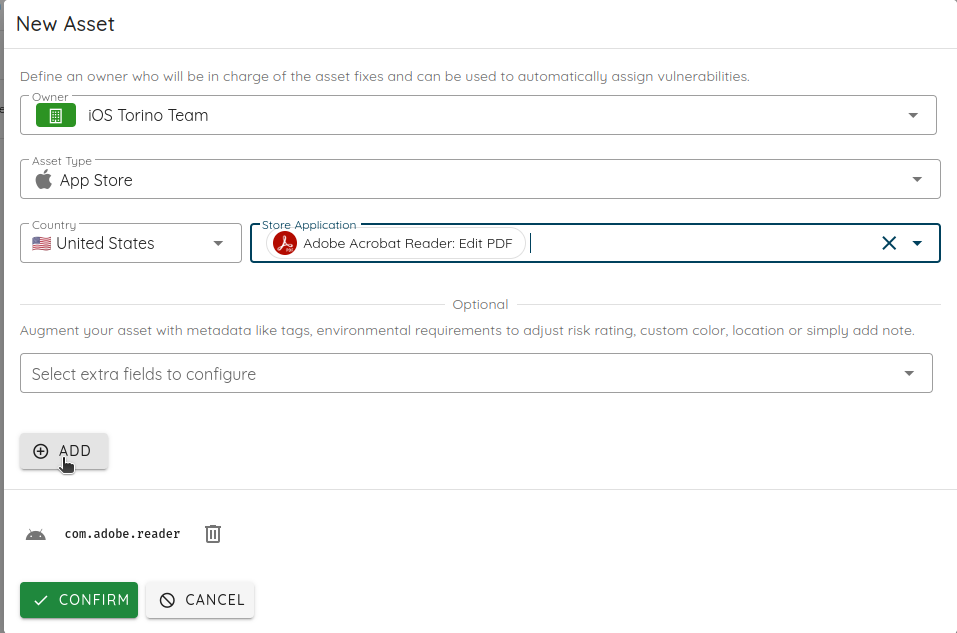
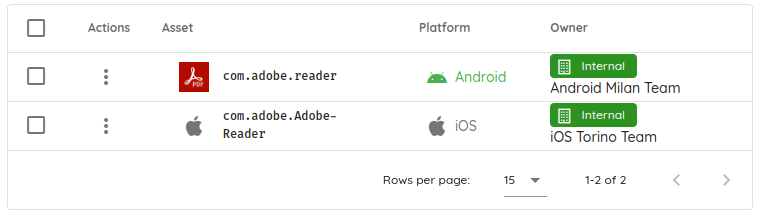
The inventory now has the two mobile applications.
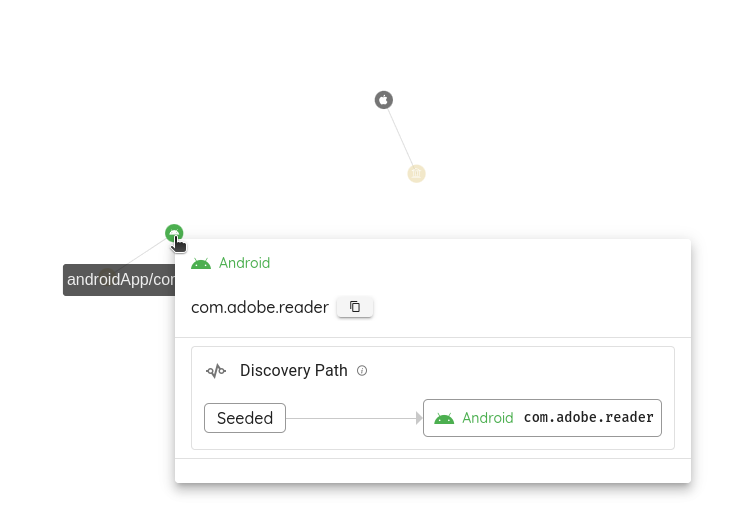
In the graph, you can see the links to the applications. In the background, the platform starts discovering all the potential assets that might belong to the same owner of the added mobile applications.
You will get the first direct potential asset by clicking on the Discover button. In our case, we can see the organizations that own the mobile applications in the Play and App stores.
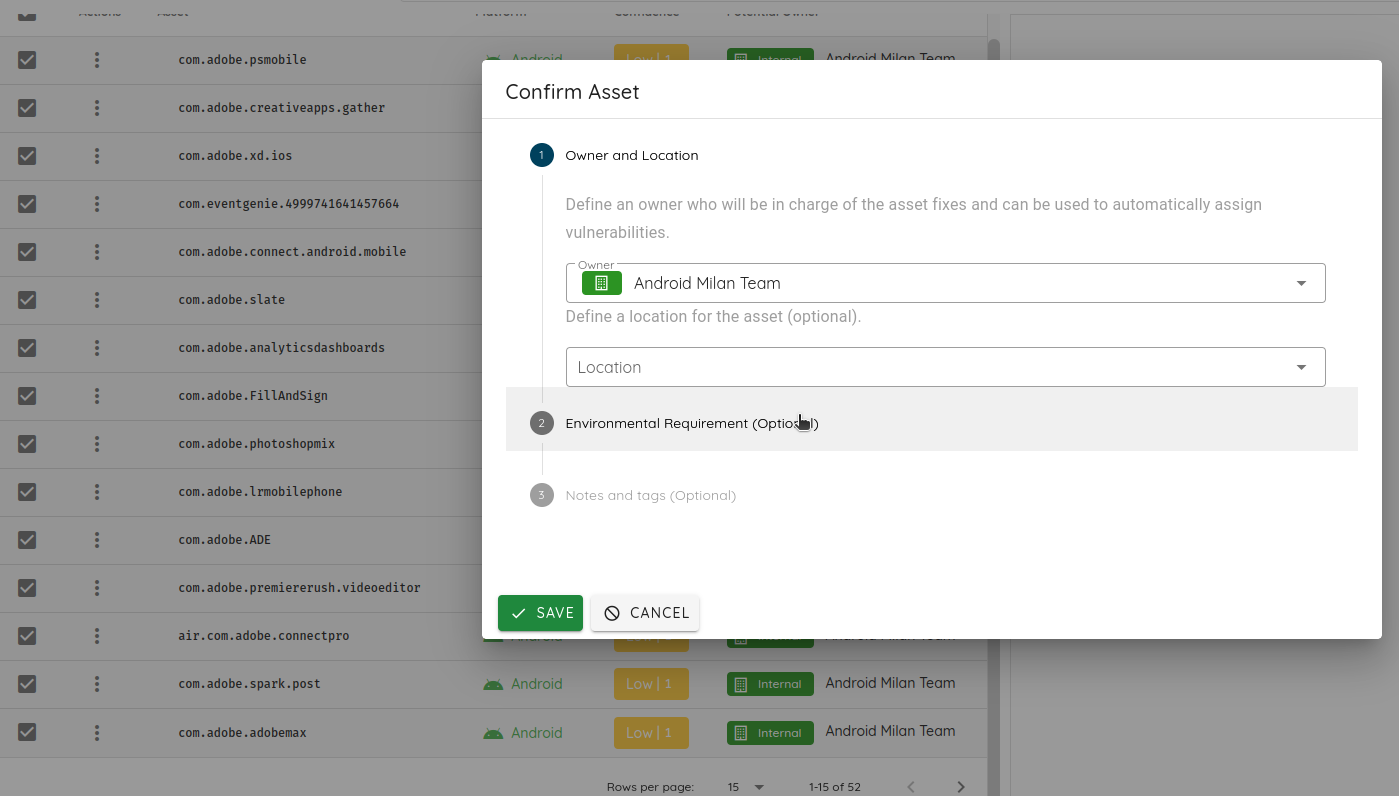
I can confirm them by clicking on the Confirm button.
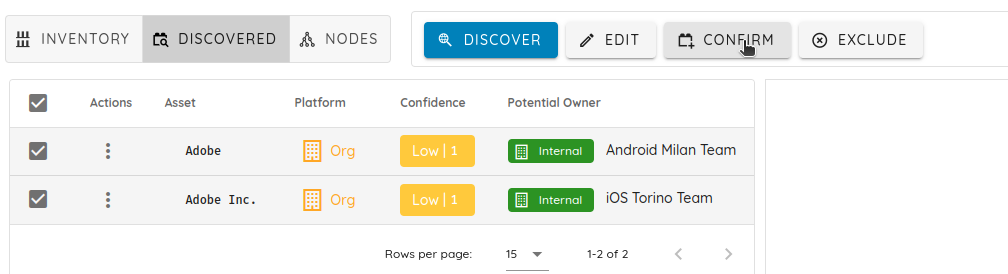
The moment you confirm those organizations, all the mobile applications belonging to those two applications will appear in the graph, and the Discovered assets will appear after you click on Discover.
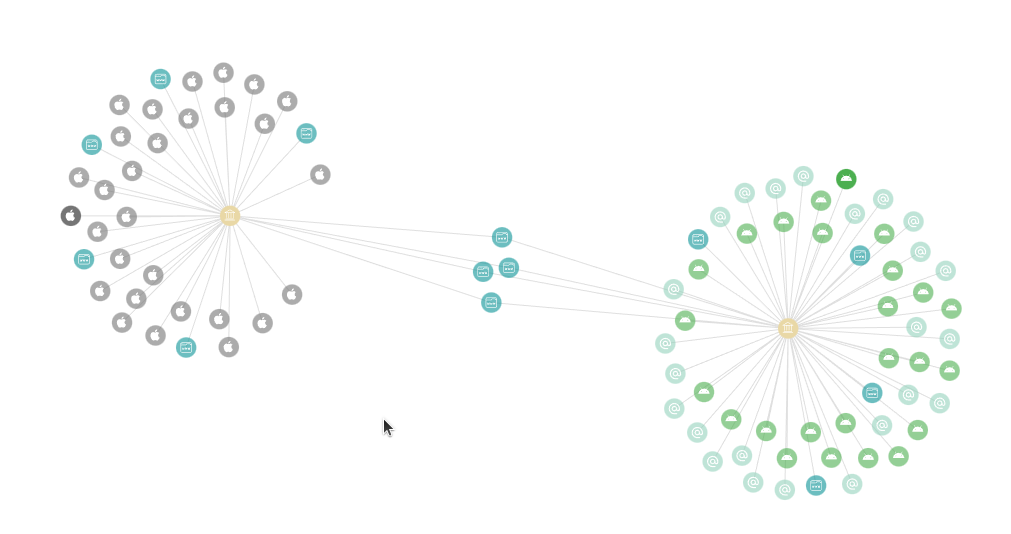
We can see that the platform also discovered other domains, emails, IP addresses, etc., but we will focus on mobile applications in this tutorial.
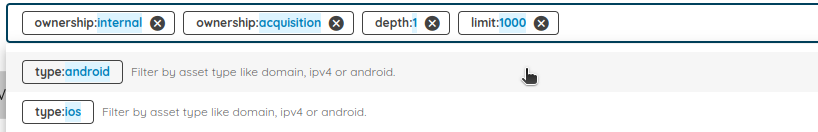
I will use the search bar to filter only on mobile applications.
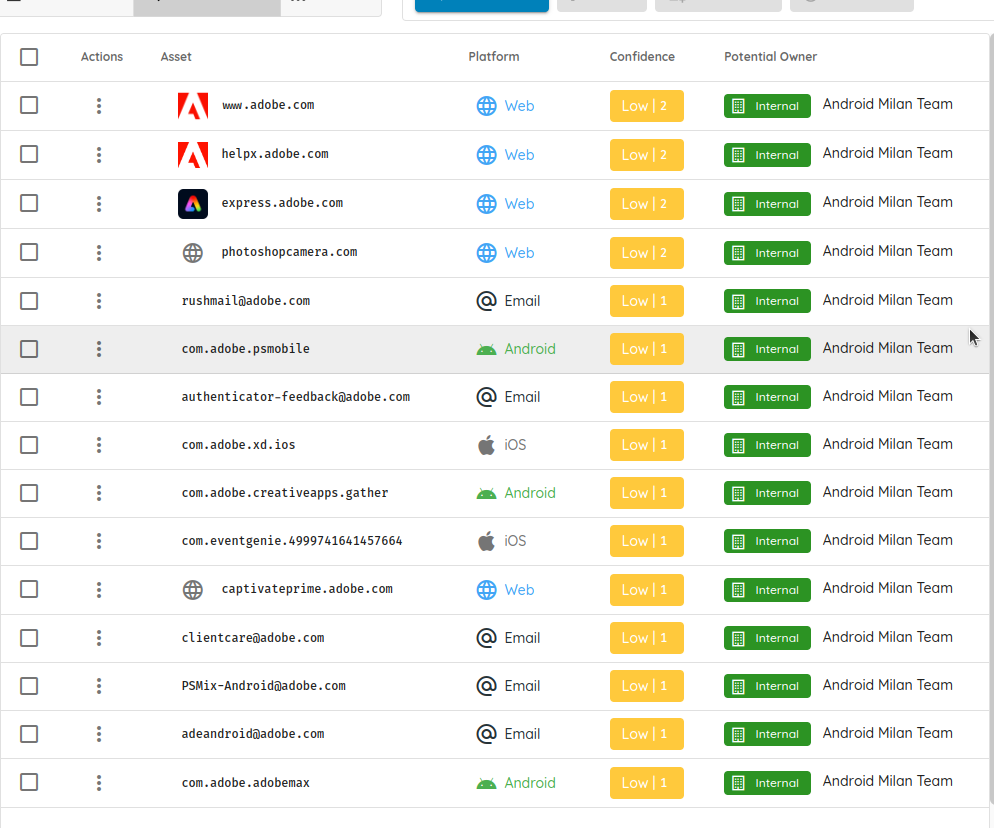
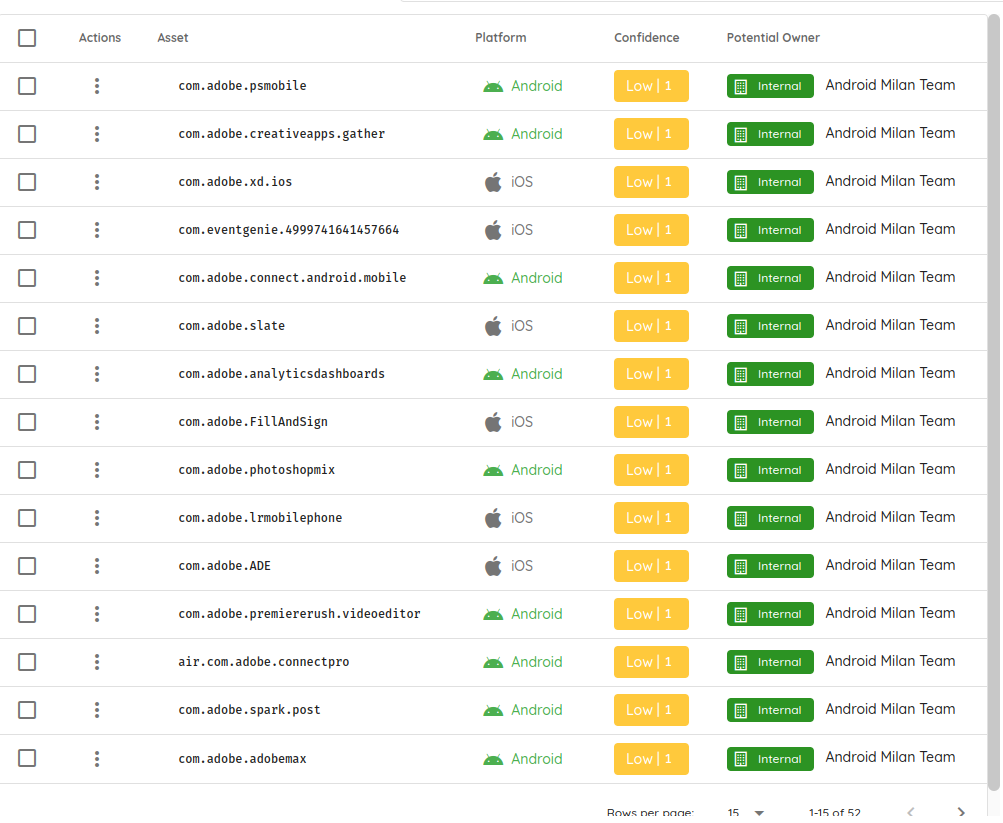
This is how Ostorlab can help list and add all the mobile applications to the inventory. You check and confirm all the ones you want to add.
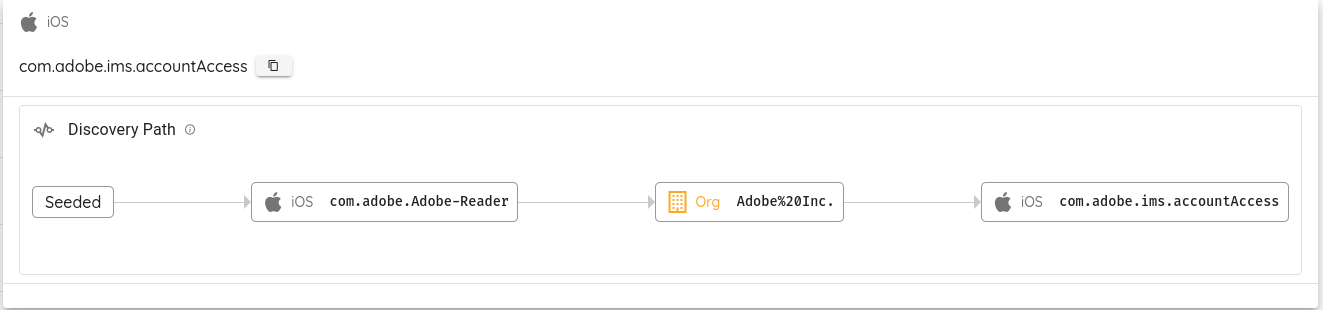
If we want to identify how a specific application was discovered, we click on it in the graph, and it will show the discovery path.
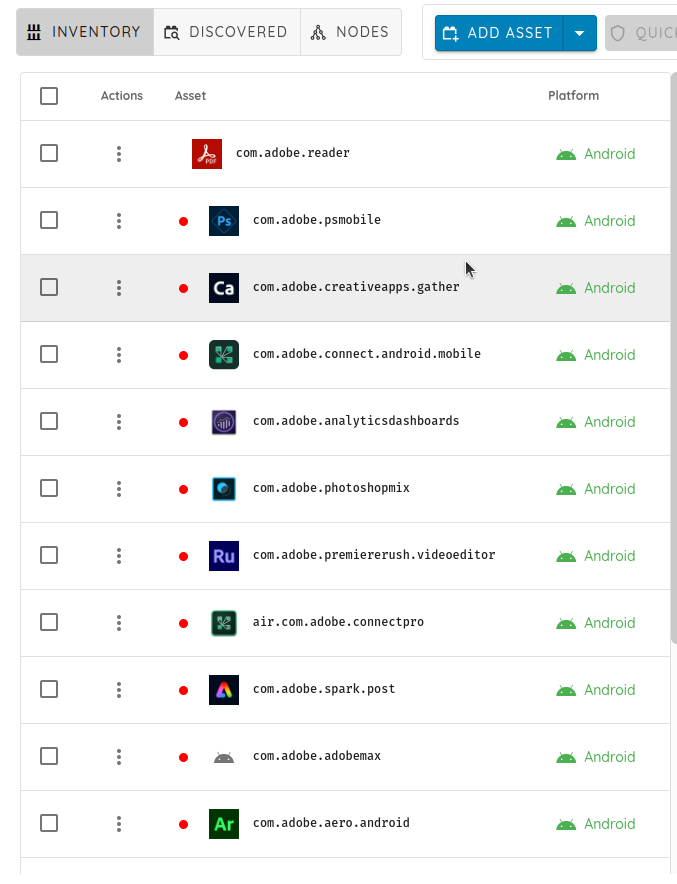
Once all the applications are confirmed, you can review and edit them in the Inventory section.
You can also customize an application and add tags that you can use as search criteria in the vulnerabilities or the components sections.
Monitor my assets:
Once the inventory is complete, I can either trigger a one-time scan or configure continuous monitoring to trigger a scan for specific criteria.
Click the Monitor button to configure your monitoring rule for the defined assets. You can create continuous monitoring or CRON rule.
Continuous monitoring tracks changes to target assets in the store and schedules a scan when a change is detected. This includes a new mobile application release on the store or a new outdated vulnerability in its libraries.
CRON monitoring schedules scans to run periodically at fixed times, dates, or intervals.
Then, you can choose the scan profile to run static or full analysis with the static, dynamic, and backend analysis.
The scans will be created automatically, and notifications will be sent at the end of the scan.
The default notifications are emails, and platform notifications are sent by email to the organization’s members. You can also configure the Slack notification to publish to a channel with customized content.
Conclusion
In conclusion, managing a diverse portfolio of mobile applications can be daunting, particularly for organizations with limited resources.
Fortunately, Ostorlab Attack Surface Discovery offers a solution that automates the identification and scanning of mobile applications. By leveraging its intuitive interface, users can easily add applications to their inventory, track ownership, and initiate scans with just a few clicks. The platform's continuous monitoring feature further simplifies the process by automatically scheduling scans whenever changes are detected in the store to identify new vulnerabilities in the codebase or the 3rd party libraries.