Wed 10 January 2024
TL;DR
This article shares empirical data and tools for detecting critical and high-severity, remotely, and actively exploitable vulnerabilities. These vulnerabilities have been collected from sources like CISA KEV, Google’s Tsunami, and our new addition Ostorlab’s Asteroid Project. In this article, we are Open-sourcing new tools to detect at scale a large proportion of these vulnerabilities.
Introduction
Not all vulnerabilities are “born” the same, they carry different impacts and require different conditions to be exploited. Remotely non-authenticated critical and high-impact vulnerabilities are among the most dangerous, be it remote code execution, account takeover, or default and weak credentials, as all can lead to a devastating impact.
This article focuses on identifying these critical vulnerabilities, setting them apart, and introducing a suite of new open-source tools (agents) to detect them within any system.
Furthermore, the results of employing these tools at a Bug Bounty scale will be shared and analyzed.
The Vulnerabilities
Vulnerability severity varies based on various factors, including the attack vectors (whether they're local or remote), the level of required privileges, and the need for user interaction. Another important criterion that can be added to evaluate these vulnerabilities is whether they have been exploited in the wild. These criteria help in pinpointing and prioritizing vulnerabilities that represent the most critical threats, demanding immediate attention and remediation.
This prioritization process becomes more feasible with the aid of several sources like CISA KEV and Google’s Tsunami. CISA KEV, a vulnerability catalog that tracks actively exploited CVEs, and Tsunami which specializes in critical and high-severity vulnerabilities prioritized by the Security Automated Team at Google.
CISA KEV :
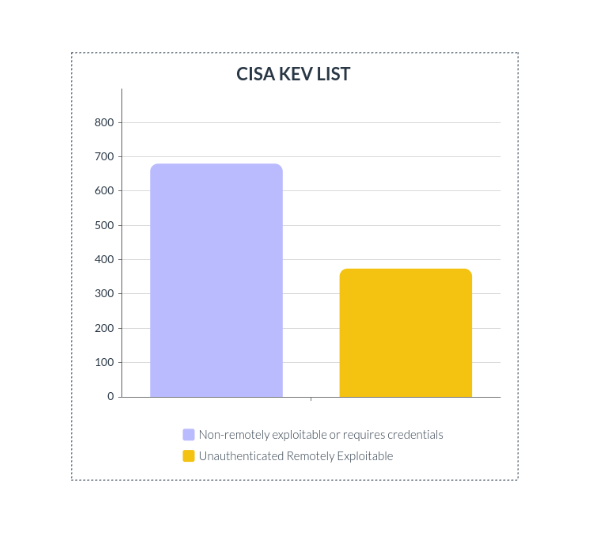
The CISA KEV list contained 1054 CVEs in total:
-
680 are non-remotely exploitable or require user interactions or authentication.
-
374 vulnerabilities are exploited remotely without user interaction or any privileges.
Out of the 374 vulnerabilities analyzed, 264 had confirmed public exploits available. For the remaining vulnerabilities, some had corresponding write-ups providing insights, while others lacked any associated information.
Out of the investigated Proof of Concepts, not all were authentic, either partial, erroneous, malicious, or mere pranks.
Another example is CVE-2022-28958 which is not a real vulnerability. Attackers did use false payload in their attacks, which indicates that the public exploit was used without verification.
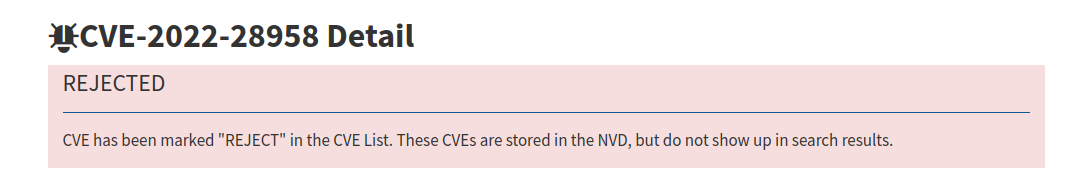
The description for the vulnerability is: “DIR816L_FW206b01 shareport.php has an issue that attackers can use to execute commands via value parameter”.
However after investigation, the researcher's proof of concept ended up being non-functional, and further testing conducted on the firmware done by VulnCheck, failed to uncover any evidence supporting the existence of the vulnerability.
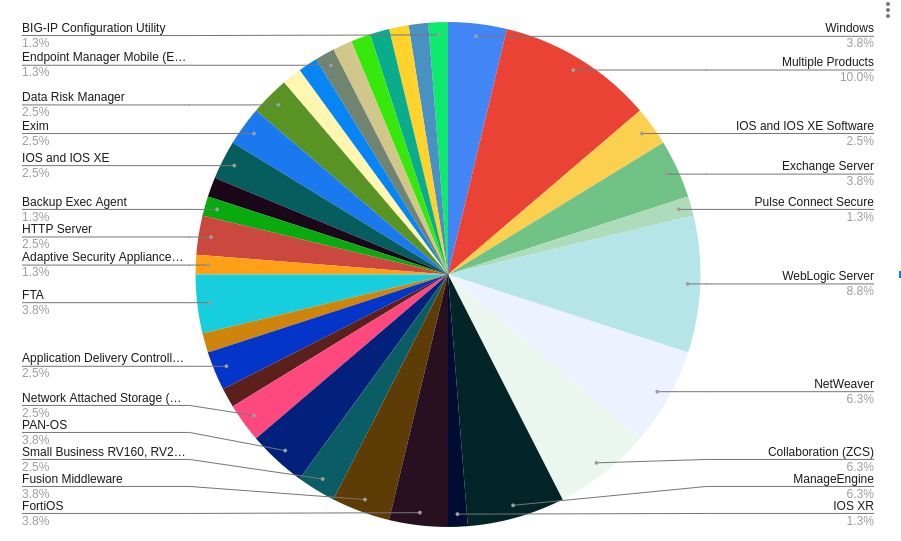
The analysis also revealed a diversity among the vendors and products listed.
Below is a distribution of (Remotely Exploitable vs Not Remotely Exploitable) CVEs by Vendors
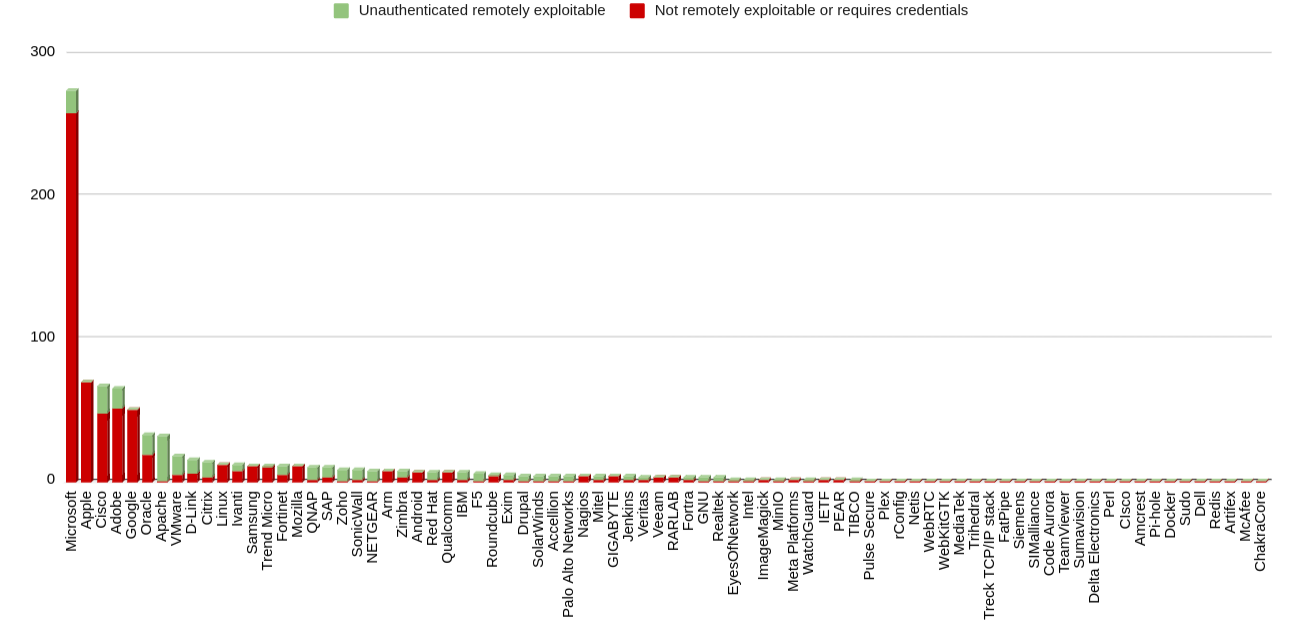
Notable points to mention:
Microsoft: Leads the way with 275 CVEs but only 16 that are unauthenticated remotely exploitable.Apache: Ranks first in terms of unauthenticated remotely exploitable CVEs with 31 vulnerabilities.
Distribution of CVEs Requiring Credentials or Not Remotely Exploitable Across Products :
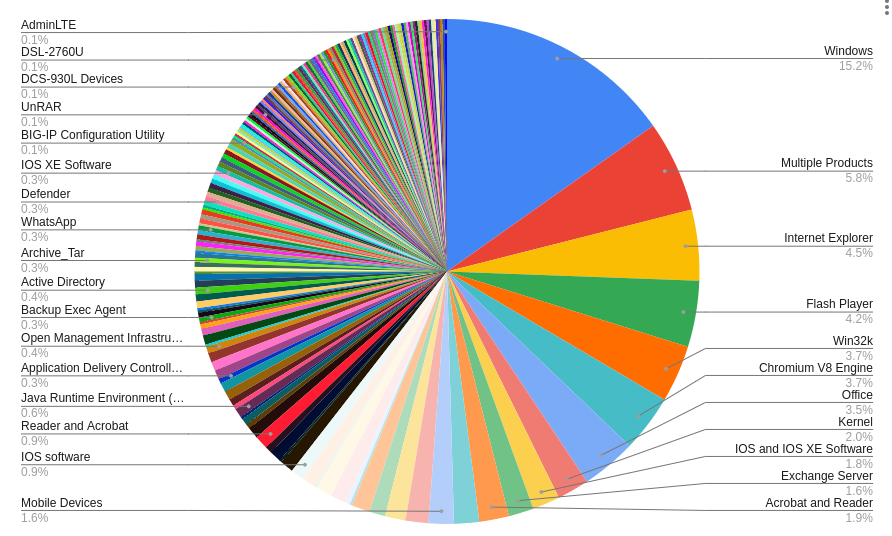
Distribution of Unauthenticated Remotely Exploitable CVEs Across Products:
The complete list is available in the following repository and is constantly being updated: KEV Ostorlab repository.
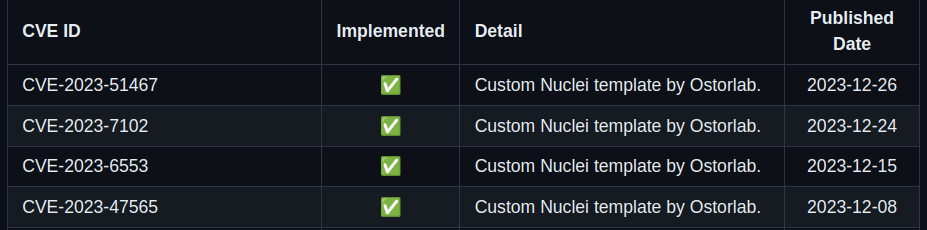
New Open-Source Tools
Ostorlab's open-source security scanning framework played a pivotal role in establishing a centralized scanning solution. It allowed for the simultaneous execution of multiple agents with diverse capabilities to test these vulnerabilities at scale.
For instance, testing the presence of these vulnerabilities against IP ranges yielded poor results. Several of these vulnerabilities are accessible only using valid domain names.
The agents built and utilized to detect these vulnerabilities are:
Nuclei agent: an open-source agent that wraps the Nuclei scanner, allowing scanning against any target and using any specified template.
For more information please check: https://github.com/Ostorlab/agent_nuclei.
Tsunami agent: an open-source agent that wraps the Tsunami scanner, giving the ability to run all the plugins provided by the scanner.
For more information please check: https://github.com/Ostorlab/agent_tsunami.
Metasploit agent: an open-source agent designed to utilize Metasploit modules against any target to check for vulnerability presence.
For more information on how to use it, please refer to: https://github.com/Ostorlab/agent_metasploit.
Agent Asteroid: New agent that enables the execution of complex checks that require custom protocols or complex logic, like cryptography key breaking that would be harder to implement using a Nuclei template. The agent is available at https://github.com/Ostorlab/agent_asteroid.
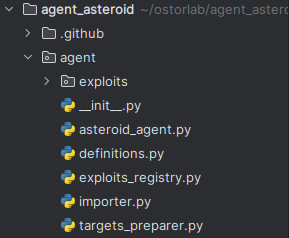
The 'exploits' folder contains the various implemented proofs of concept, which we'll continue to add.
As of this report's publication, our toolkit encompasses 18 distinct checks for various CVEs. In addition to these, we've developed specific custom checks, such as the one targeting the exposure of the Android Debug Bridge (ADB).
Nmap agent: open-source agent to run port discovery. The Nmap agent is what can discover what ports should be targeted by the detection agent, ensuring that these are scanned only once and tested by all.
Amass agent: open-source agent to enumerate subdomains. This agent has been used during large-scale testing to cover all publicly available targets of a specified domain.
Subfinder agent: another open-source agent to enumerate subdomains. This agent is an addition to amass for improved domain enumeration.
Putting it all together
To execute all these agents simultaneously, Ostorlab provides the functionality to define an agent group and specify the desired agents.
To get a full view of the agent group definition you can check known exploitable vulnerabilities.
To run this agent group:
oxo scan run --install -g agent_group.yaml domain-name example.com
Agents are packaged as docker images and the –-install flag will ensure to download the latest version.
To visualize how these agents seamlessly collaborate, you can visualize them using the tool at: https://report.ostorlab.co/library/agent/group.
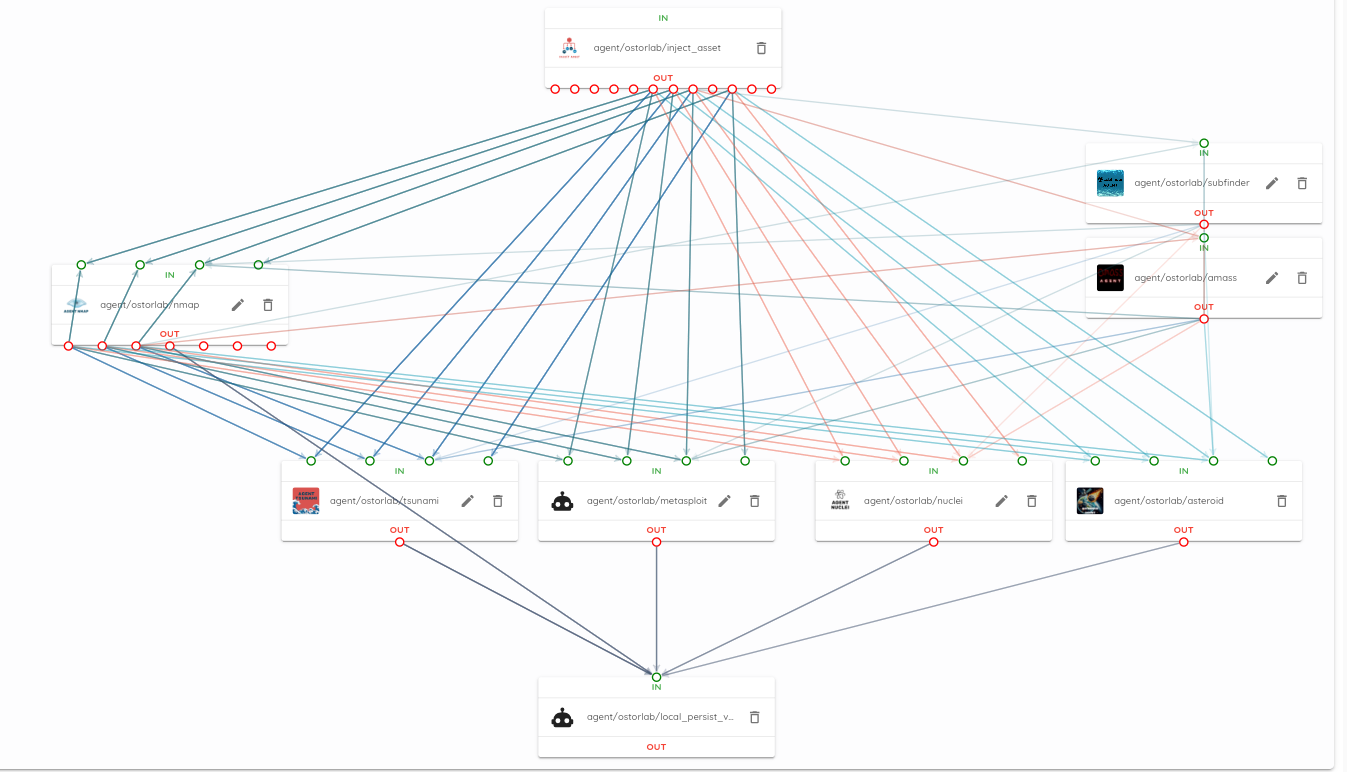
It provides a drag-and-drop functionality that allows the generation of a YAML file for the agent group. Additionally, it enables the visualization of the communication between agents, their inputs and outputs, and their position in the workflow.
Testing At Scale
Running the developed tools on various bug bounty targets provided empirical results on the presence of these vulnerabilities, against targets with a mature security posture.
Out of the 1500 targets, the following results were collected, Twenty-five (25) of the targets contained critical vulnerabilities that led to remote code execution.
For example:
Jboss Application Server - Remote Code Execution vulnerability, With a CVSS score of 9.8.
Eleven of the targets (11) contained high-severity vulnerabilities, ranging from pre-auth RCE, and weak credentials in services like FTP, and IMAP, to Access Control Bypass.
This means that out of these targets with what is expected to be a mature security posture, 2.5% still suffered from publicly exploitable vulnerabilities.
Closing Remarks
Vulnerabilities present an ongoing challenge, and their prioritization remains complex, to say the least. A centralized open-source tool to detect known threats offers an advantage (and first step) in securing environments.
Feel free to contribute to this open-source project. You can create a pull request with your proof of concept at: