Mon 24 October 2022
CVE-2022-42889 is a vulnerability in the Apache Commons Text Library caused by string interpolation abusing powerful
handlers that allows for remote code execution.
The vulnerability is dubbed Text4Shell and has been pending a fix for seven months until the release of version 1.10
.
For mobile applications, the Apache Commons Text library is a relatively popular library present in popular
applications like
Mi Musicwith over a billion downloads.Amazon shoppingwith over a half billion downloads.Flo Ovulation,LG ThinQ,Fitbit,UMANG,Mi Home,Webnovel,Grammarly Keyboard,Udemyall with tens of millions of downloads.
The vulnerability is technically due to the use of interpolation handlers offering the ability to execute a script, resolve DNS queries, read a file, parse and access XML, read Java constants or make URL requests.
Below are examples of how to exploit the script handler:
String poc1 = “${script:javascript:java.lang.Runtime.getRuntime().exec(\”touch /tmp/tarlogic\”);}”;
String rce1 = StringSubstitutor.createInterpolator().replace(poc1);
String poc2 = “script:javascript:java.lang.Runtime.getRuntime().exec(\”touch /tmp/tarlogic\”)”;
String rce2 = StringLookupFactory.INSTANCE.interpolatorStringLookup().lookup(poc2);
The vulnerability can be traced to two classes with support for interpolation, StringSubstitutor,
and StringLookupFactory.
The fix introduced in version 1.10 removed the handlers for scripts, URLs, and DNS from the defaults.
* Fix https://github.com/apache/commons-text/commit/b9b40b903e2d1f9935039803c9852439576780ea
But it left others like file content, environment variables, and XML path that can still be abused to access sensitive information like secrets, passwords, or source code.
Analysis of the mobile applications using the vulnerable library has shown a low probability of being vulnerable as the affected APIs are rarely used.
For instance, in applications where the dependency is present, searching for the class StringLookupFactory returned little findings. The methods' call stacks didn't indicate the exposure to dangerous inputs for the ones matching.
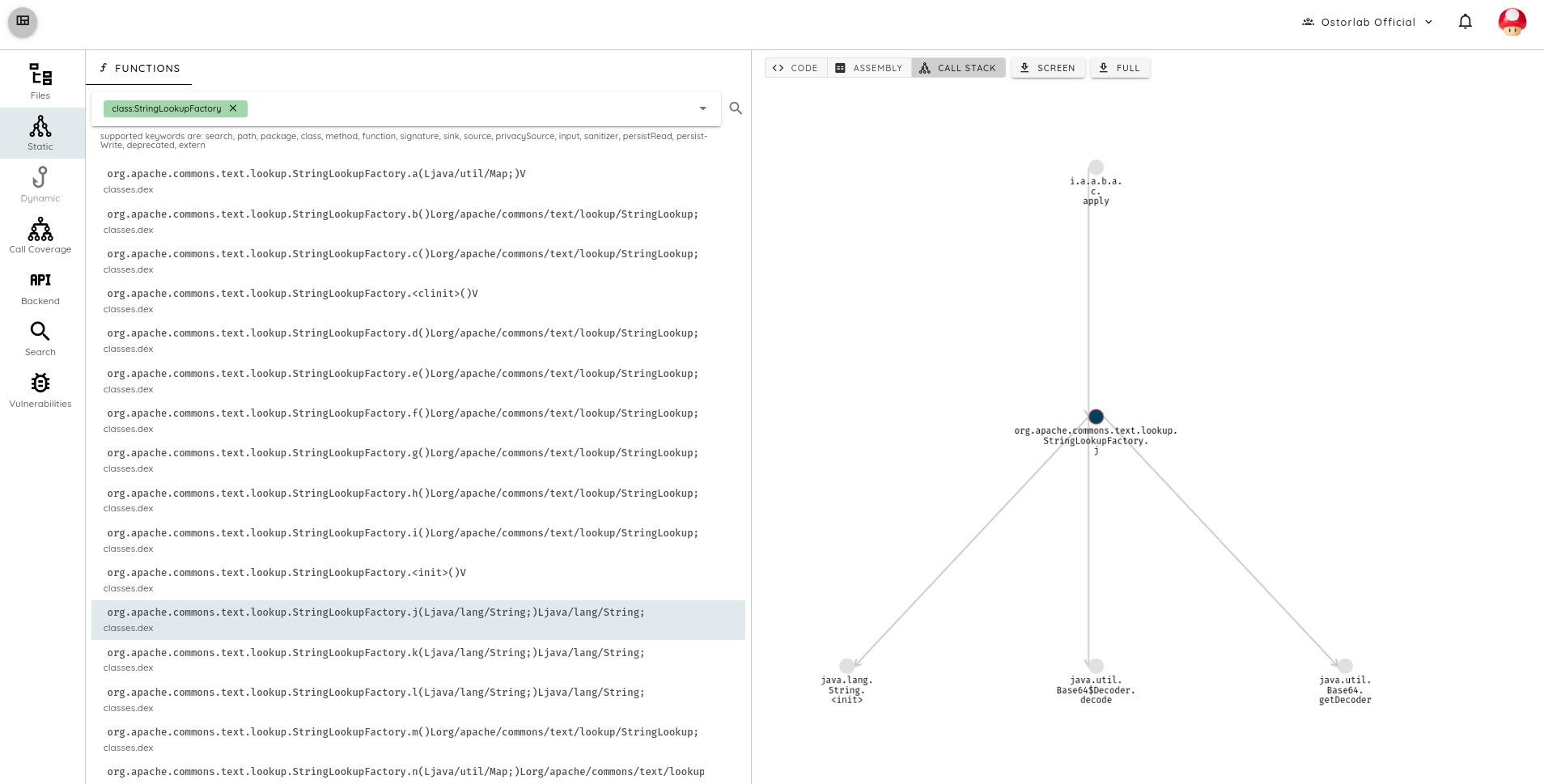
Out of over 50 applications reviewed with Apache Commons Text present, we identified one using the StringLookupFactory
,
and all the rest are using non-vulnerable APIs from the library.
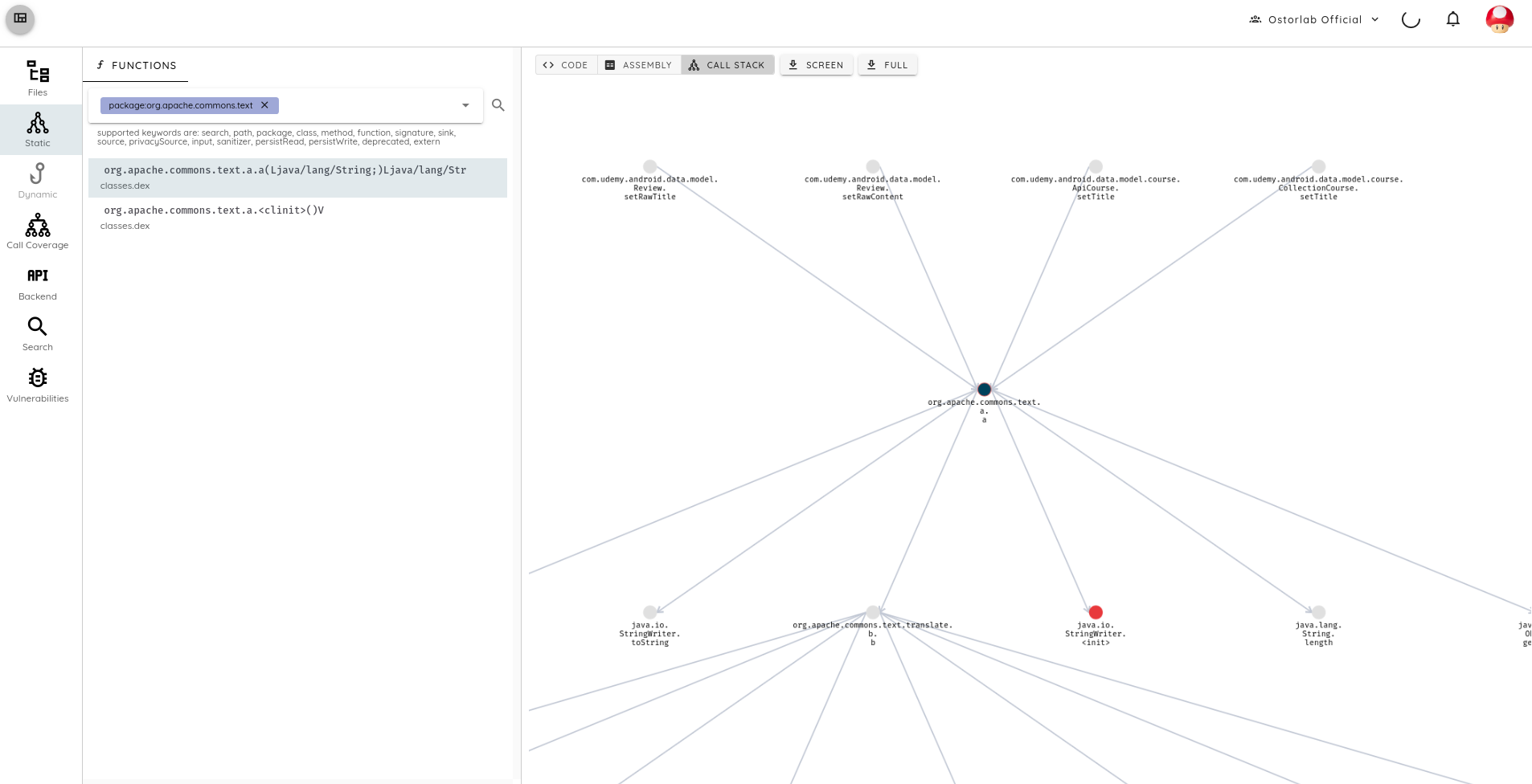
Searching the library by name is, however, insufficient, as in several cases the library is obfuscated, and the initial class names are removed. See the case below for an example from the Udemy application.
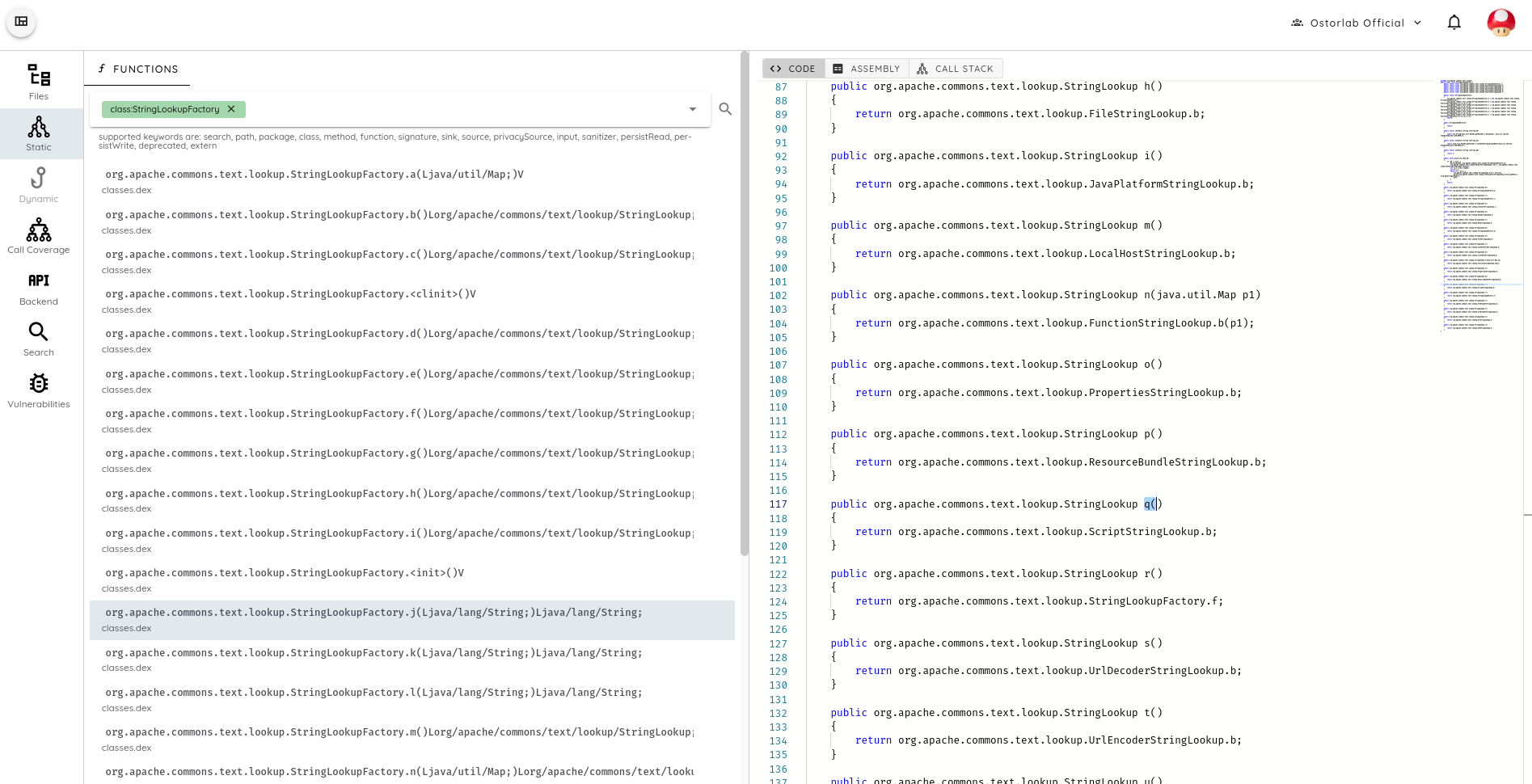
Overall, our analysis indicates a low probability of being vulnerable. If you have a mobile application:
- You can verify if the library is present in your application by checking the fingerprint section in the scan report.
- Check the usage of the vulnerable classes using the analysis environment, but don’t forget to check if obfuscation is present.
- The currently implemented fix only removes the risk of remote code execution. It is still possible to read file content and access environment variables or read java constants. Hence it is recommended to remove them from the list of enabled handlers.