Mon 07 April 2025
📈 Reporting & Export Enhancements
- Added support for exporting scan vulnerabilities in Static Analysis Results Interchange Format (SARIF) format for
easy integration with security tools that support SARIF. To export using SARIF format, go to the scan page, choose
export, and then SARIF.
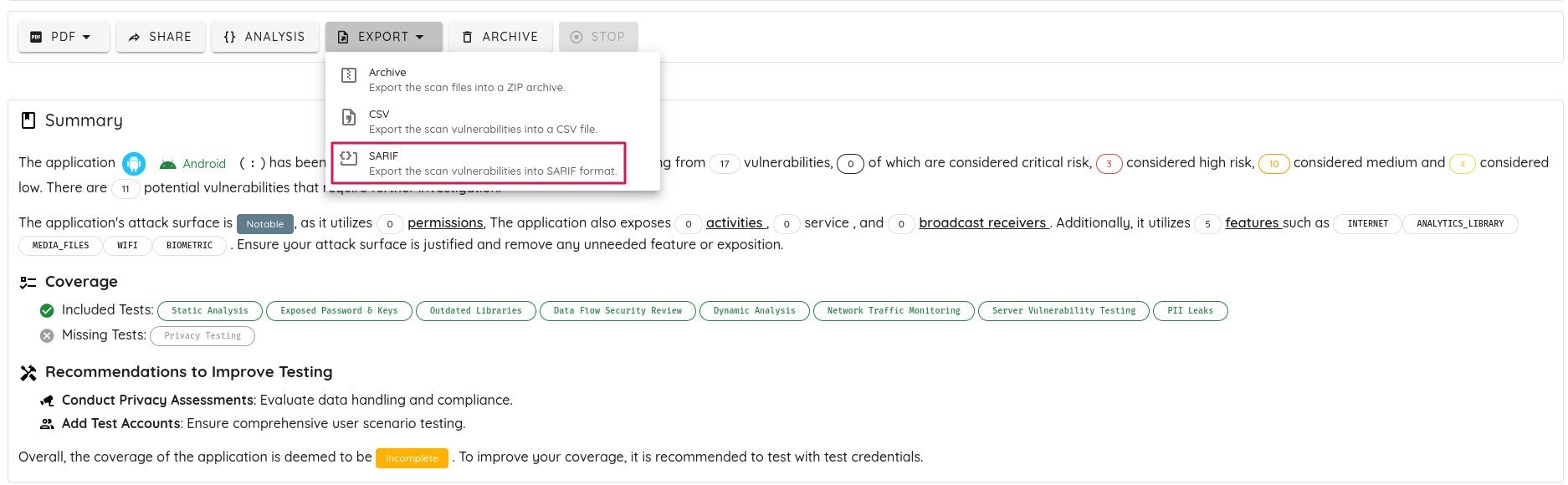
- Added the Commission Nationale de l’Informatique et des Libertés (CNIL) standard, which can be found in the
Standards section of the scan page.
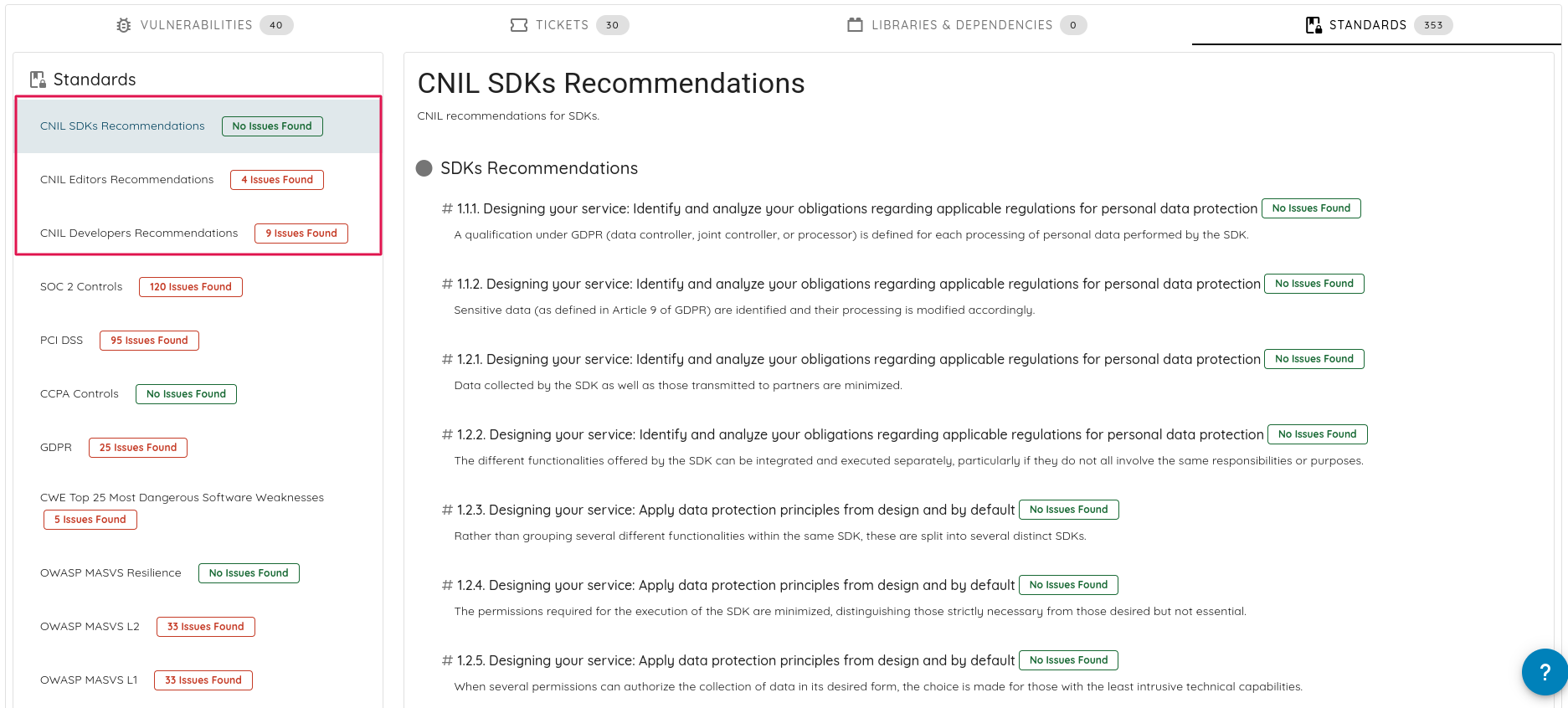
- Enhanced vulnerability DNA. DNA is used to uniquely identify vulnerabilities. This enhancement improves accuracy
in identifying and classifying vulnerabilities, reducing false positives and improving remediation prioritization.
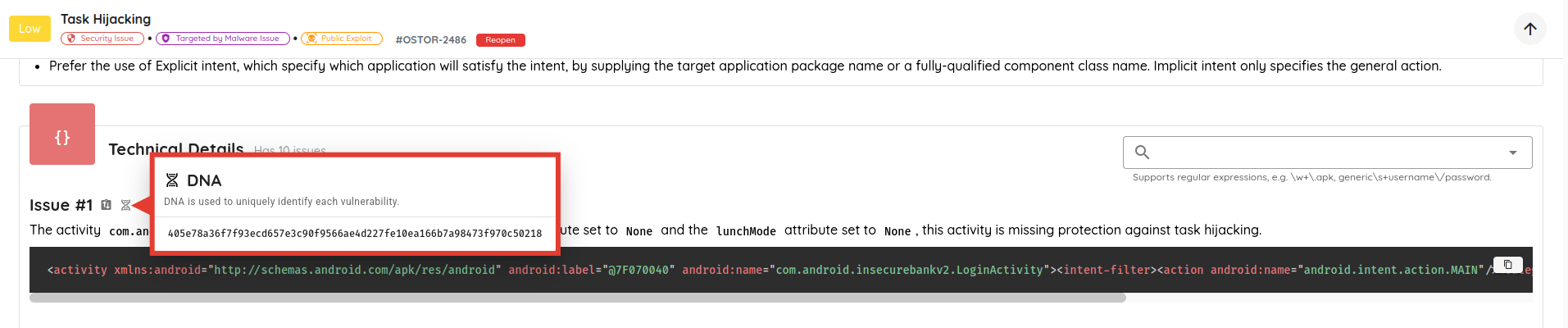
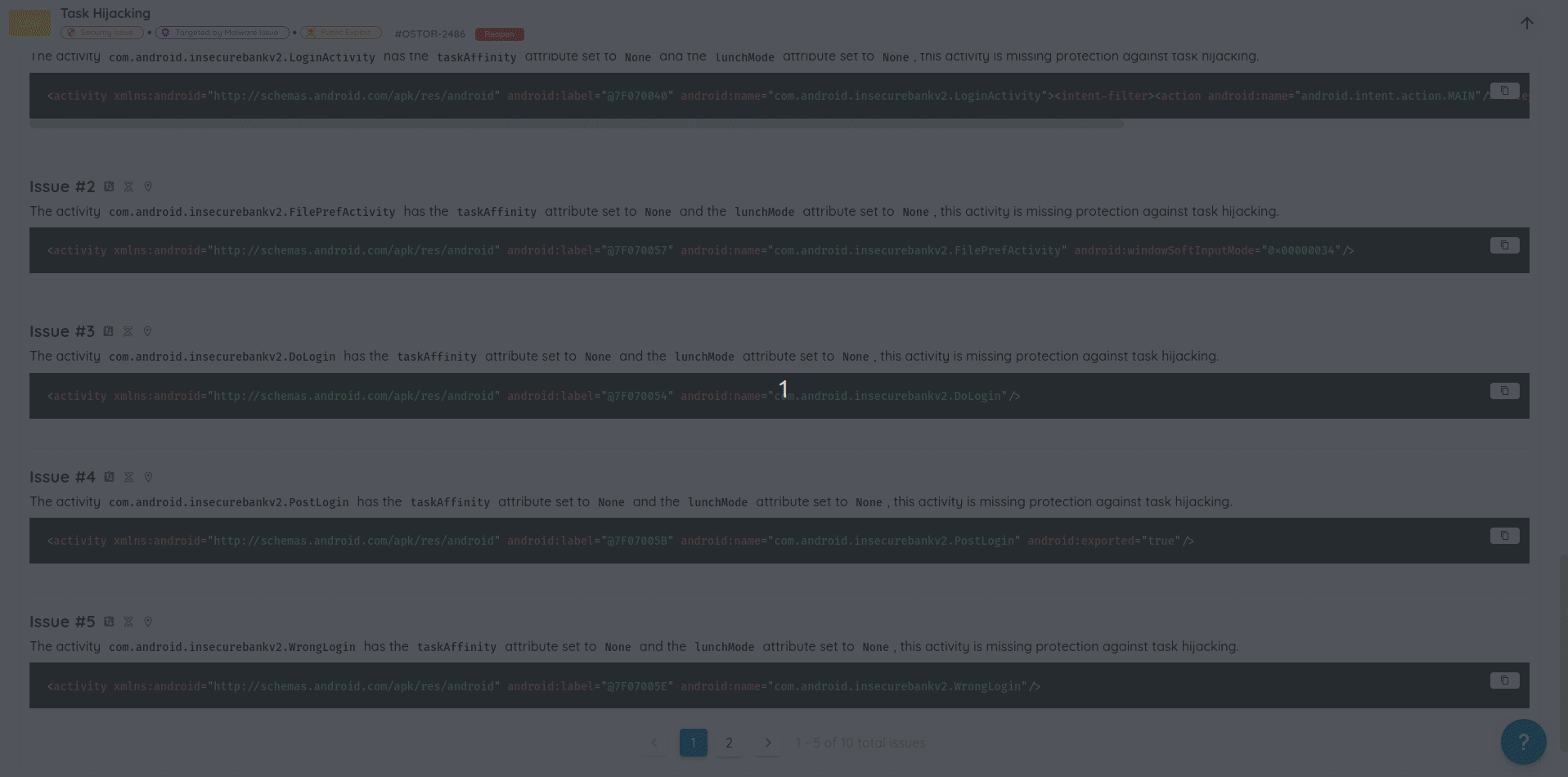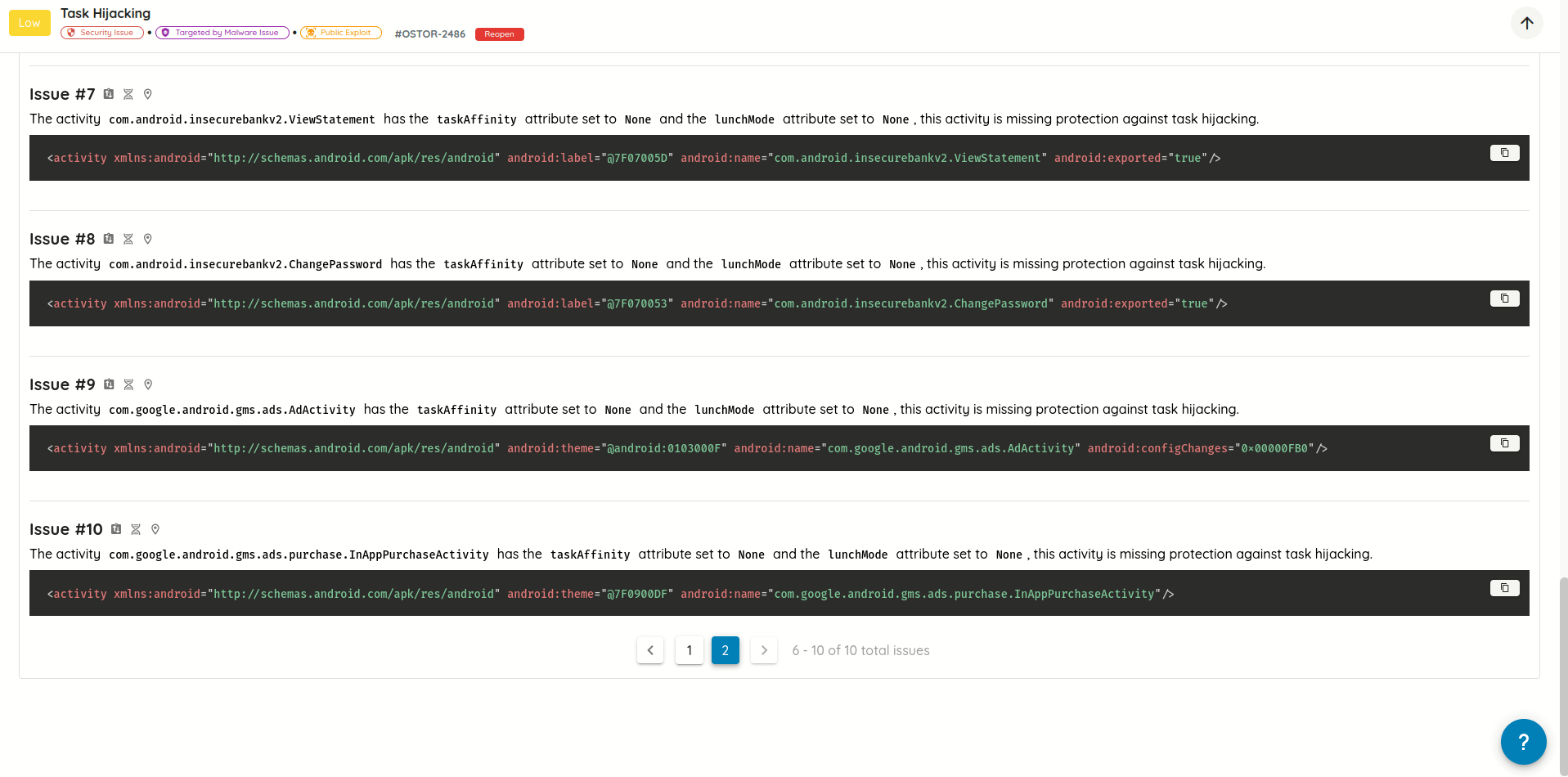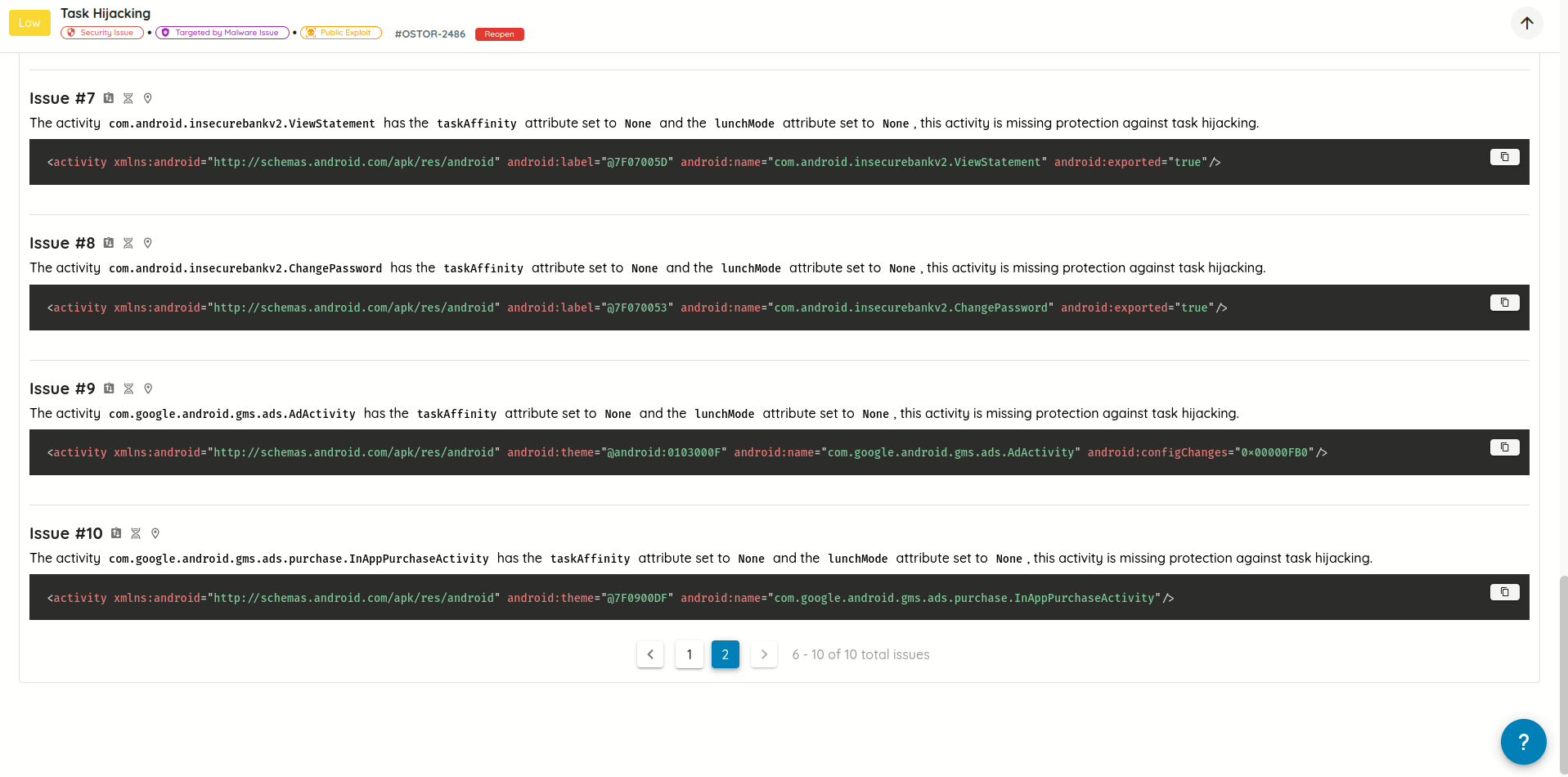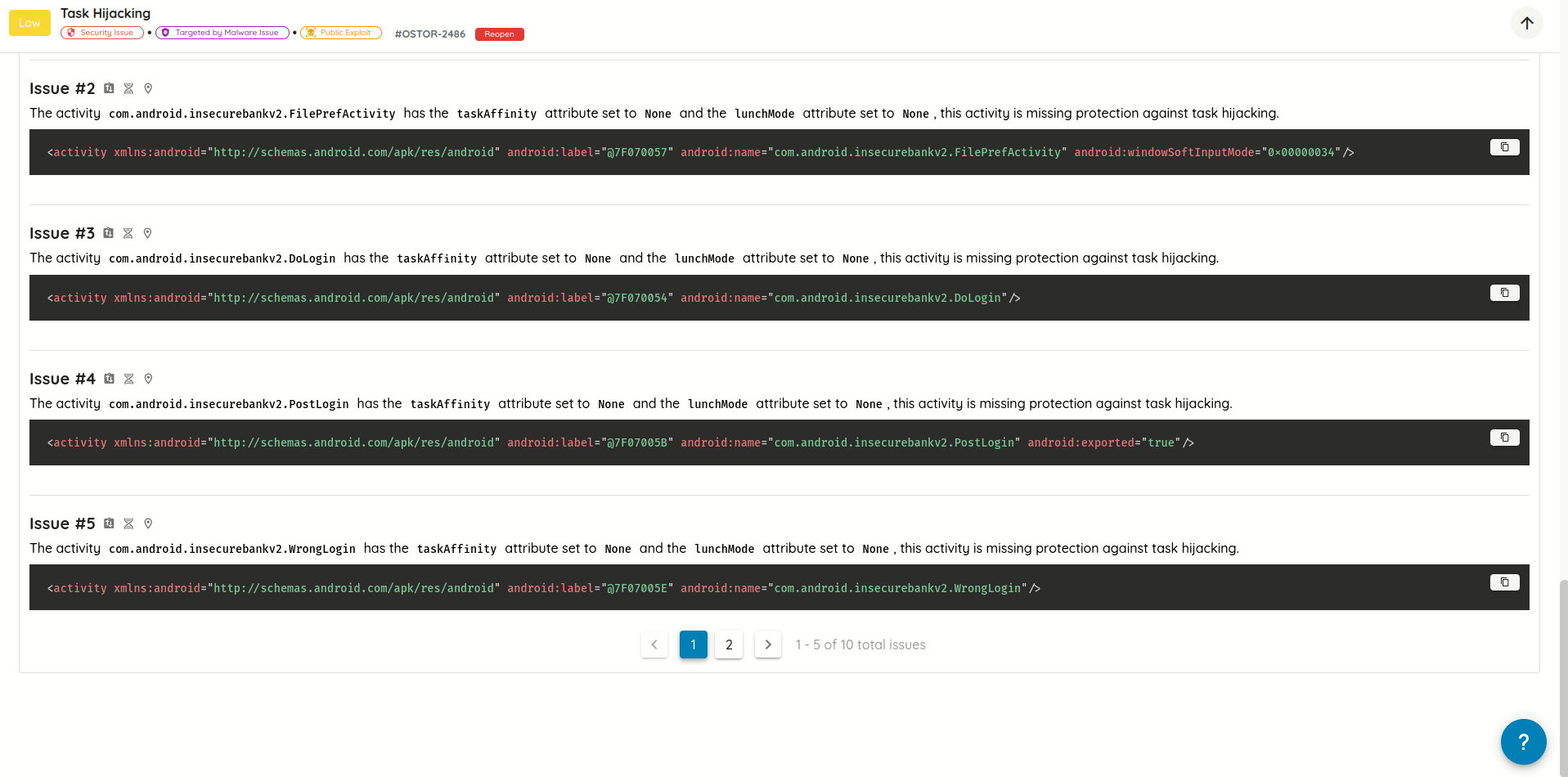
- Added support for searching vulnerability technical, exploit, and post-exploit details using plain text and/or
regular expressions, with text highlighting for text matching search queries.
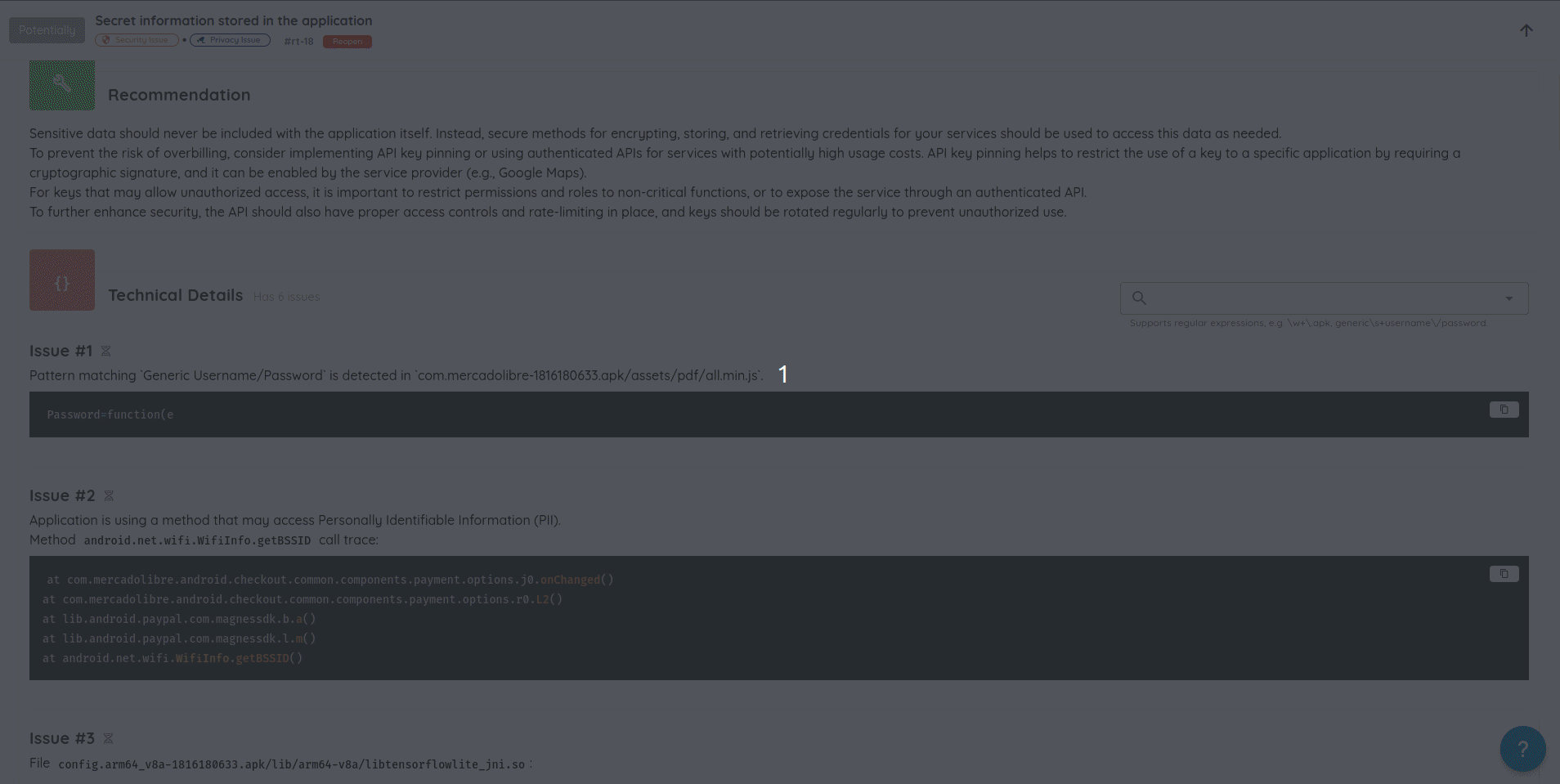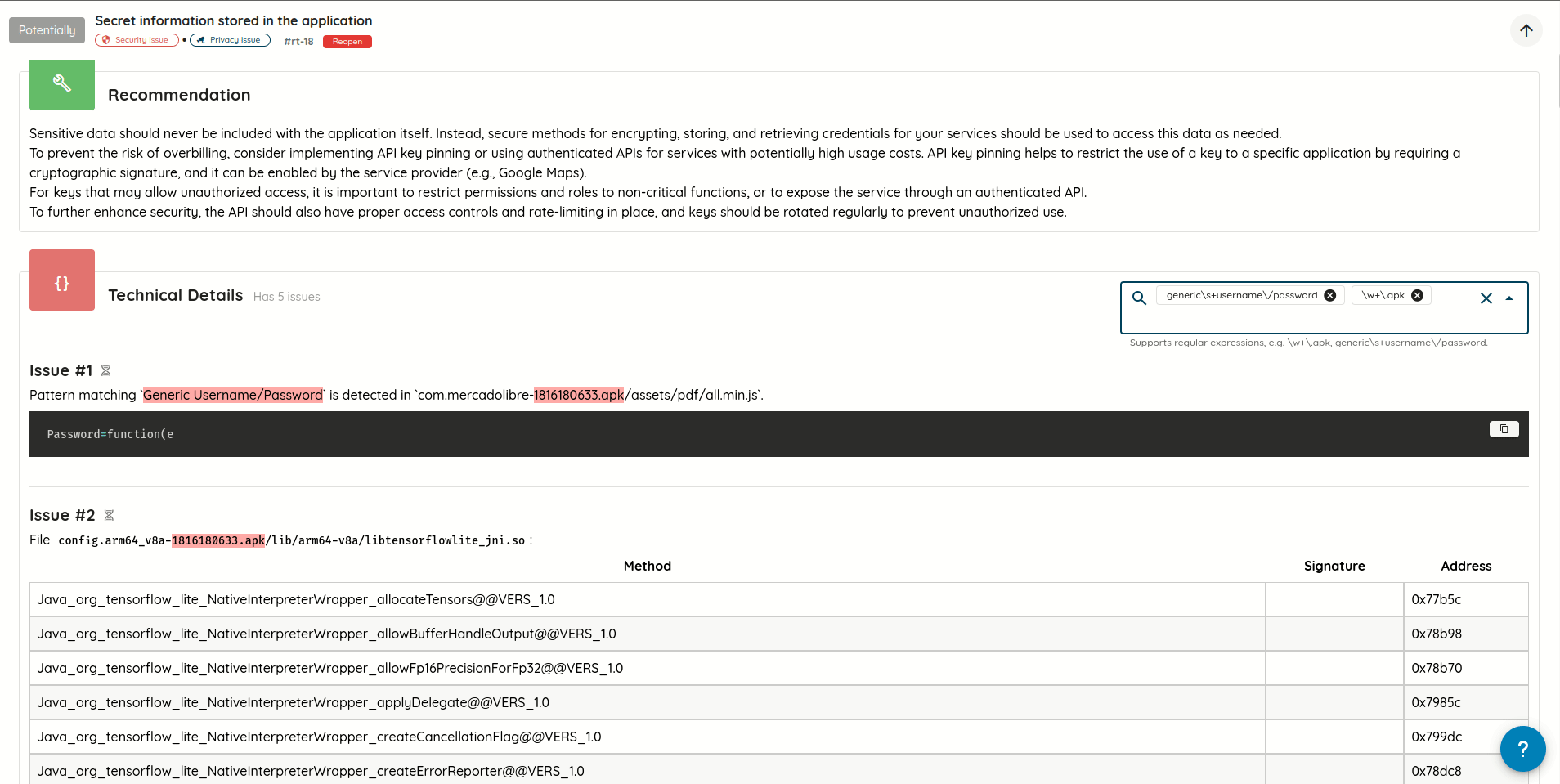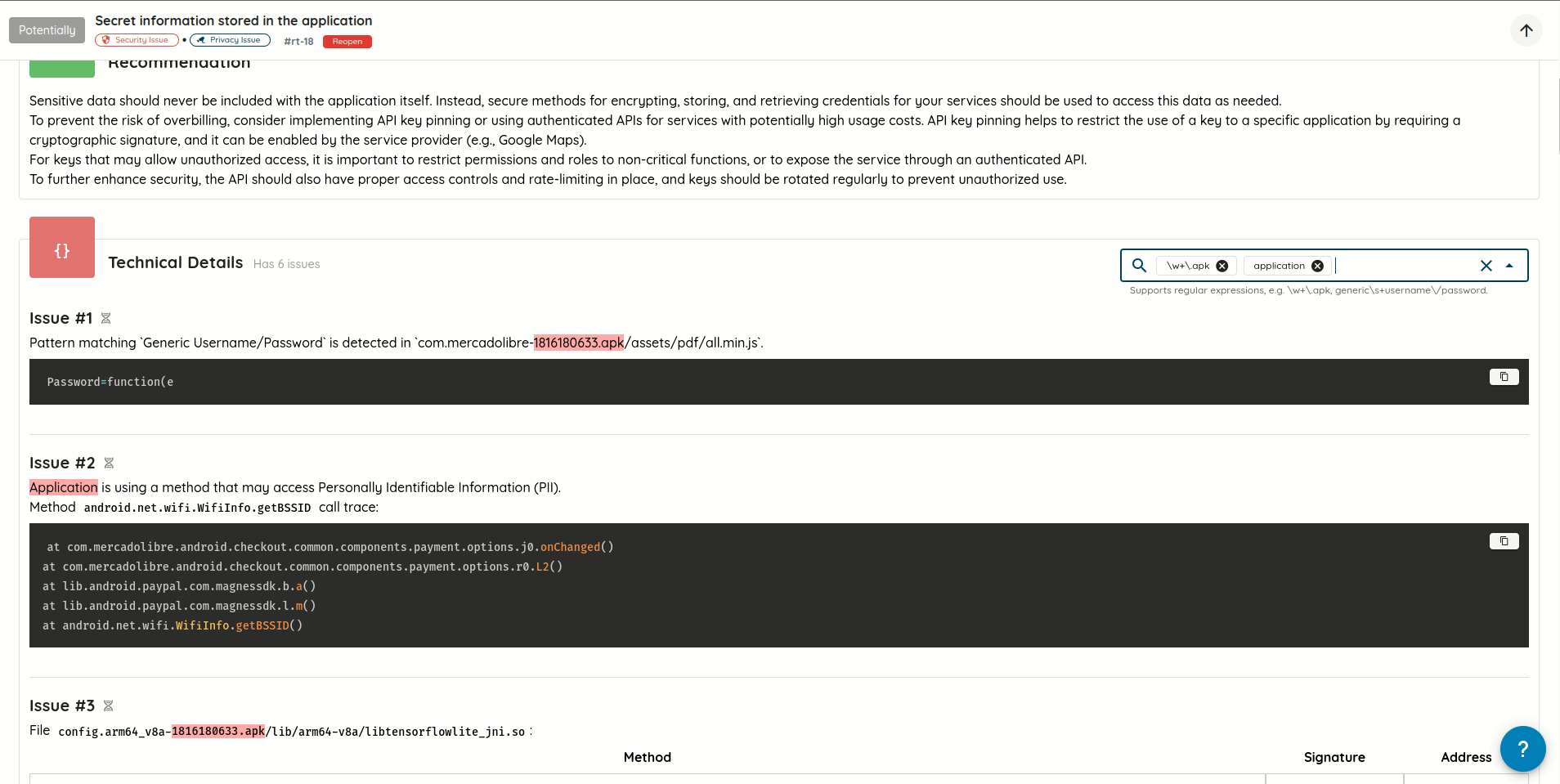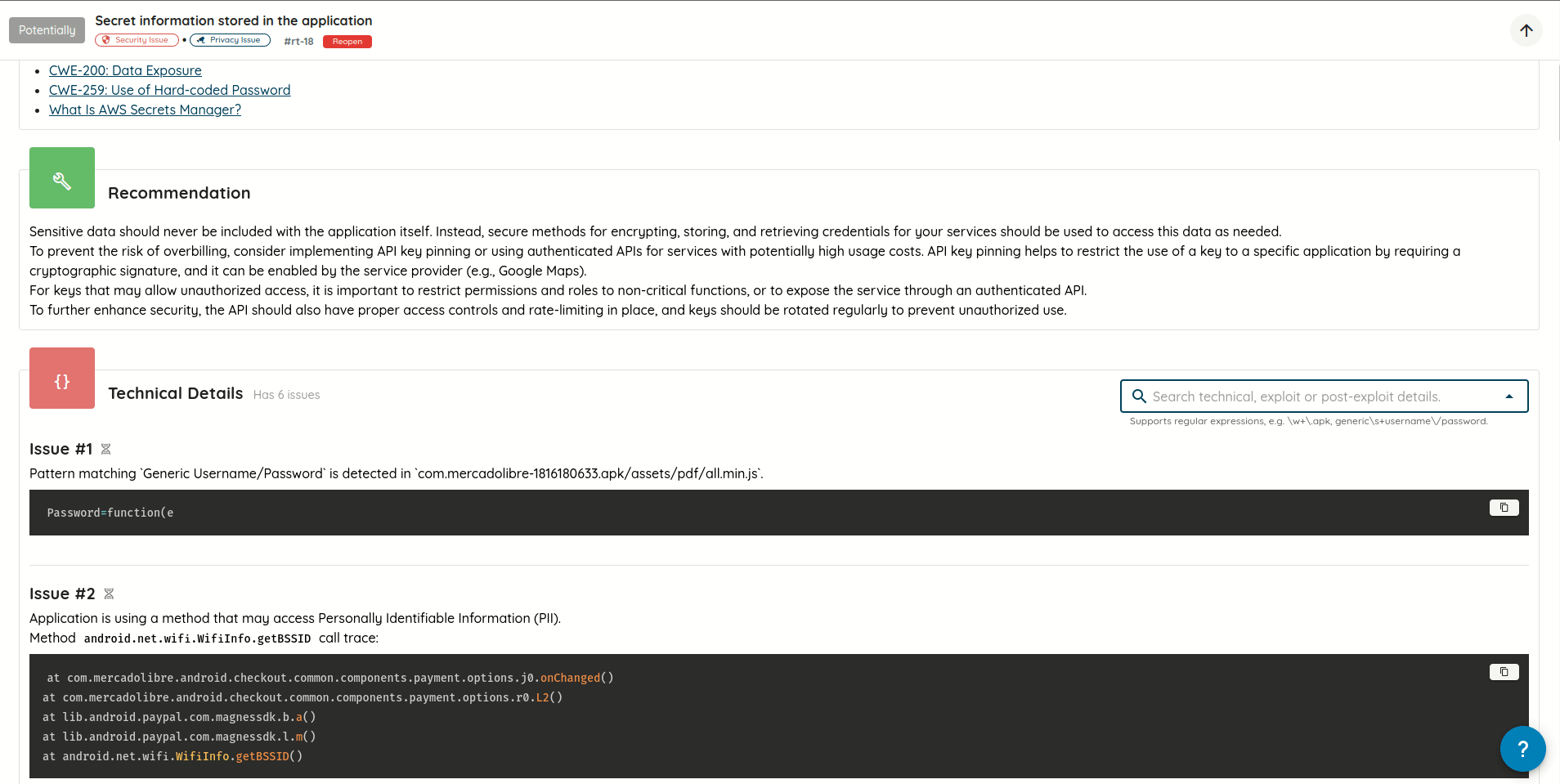
Search in vulnerability technical, exploit, and post-exploit details - Replaced scroll pagination with manual pagination: Improves control and performance when navigating through a lot
of vulnerability details.
🎫 Remediation
- Filter tickets by scan profile, allowing faster triage and resolution by narrowing down tickets to specific scan
context.
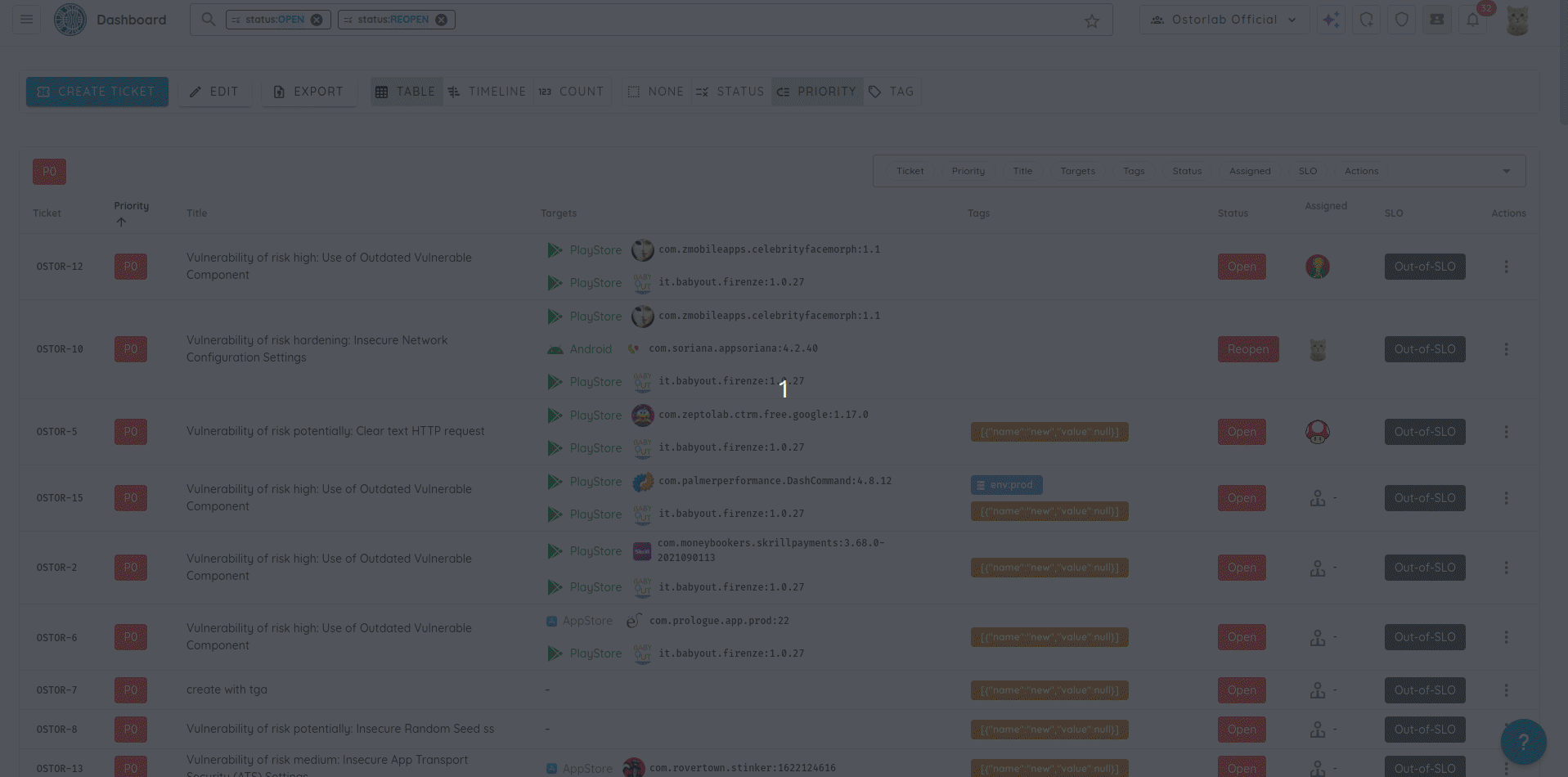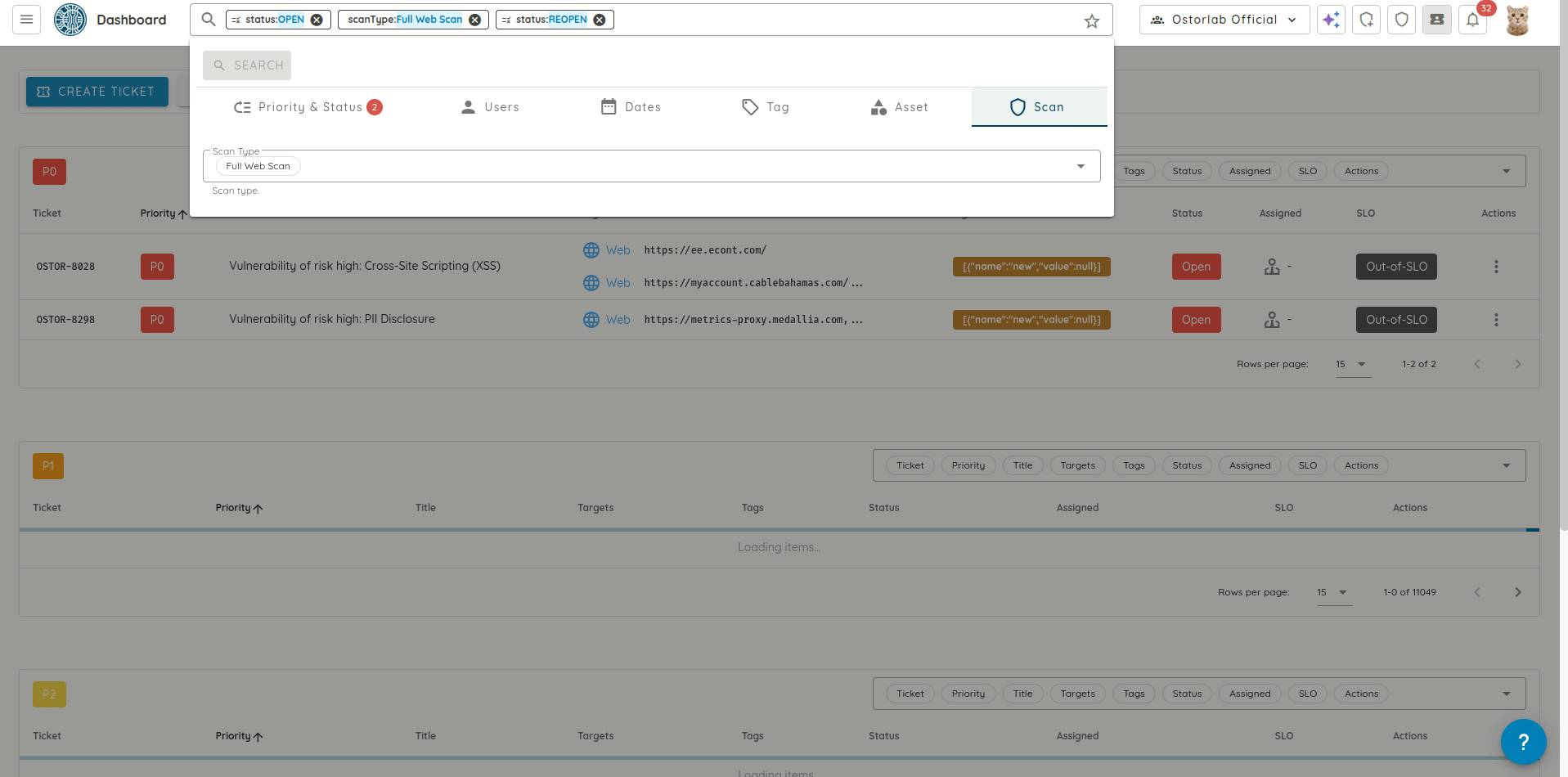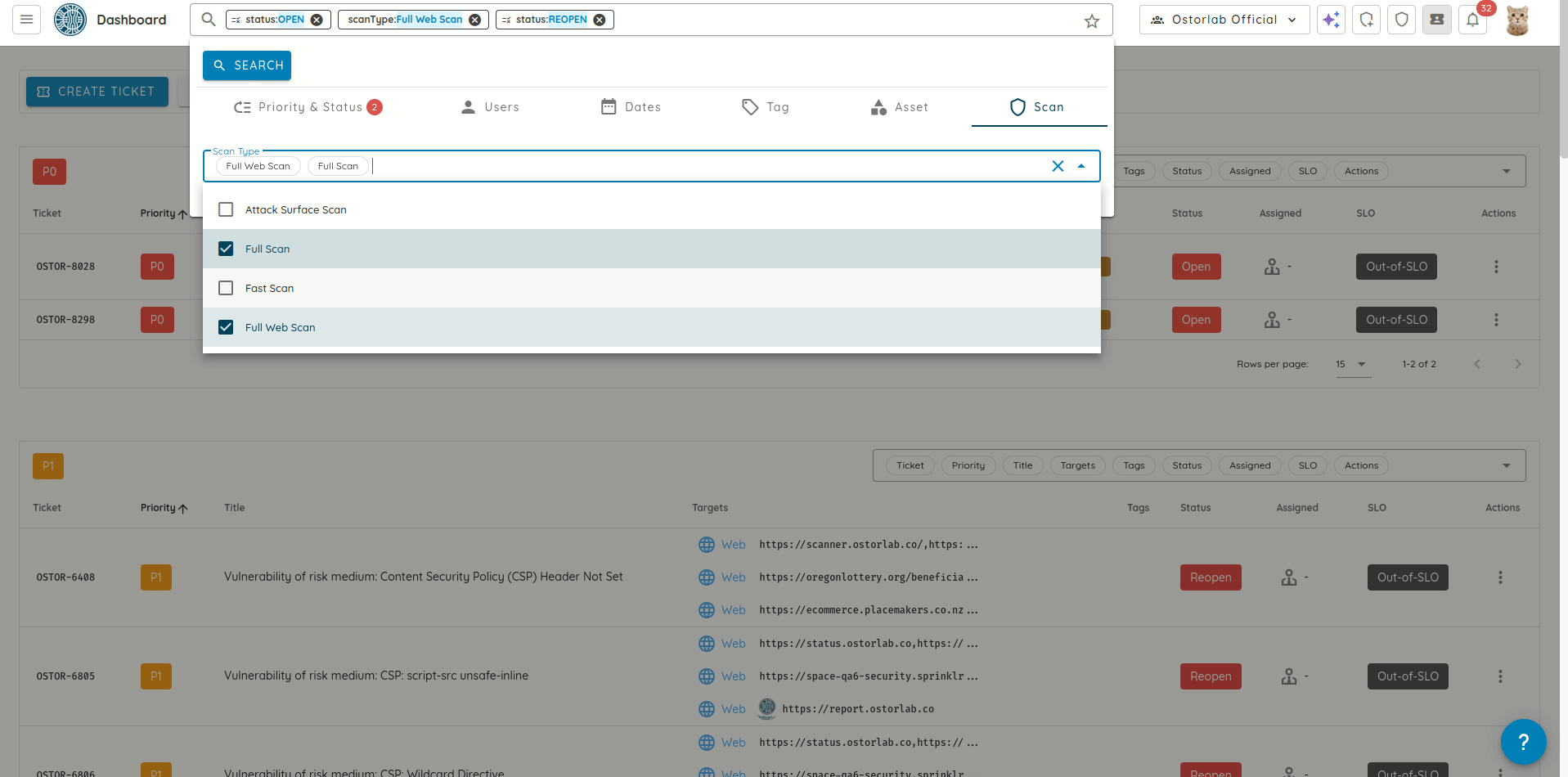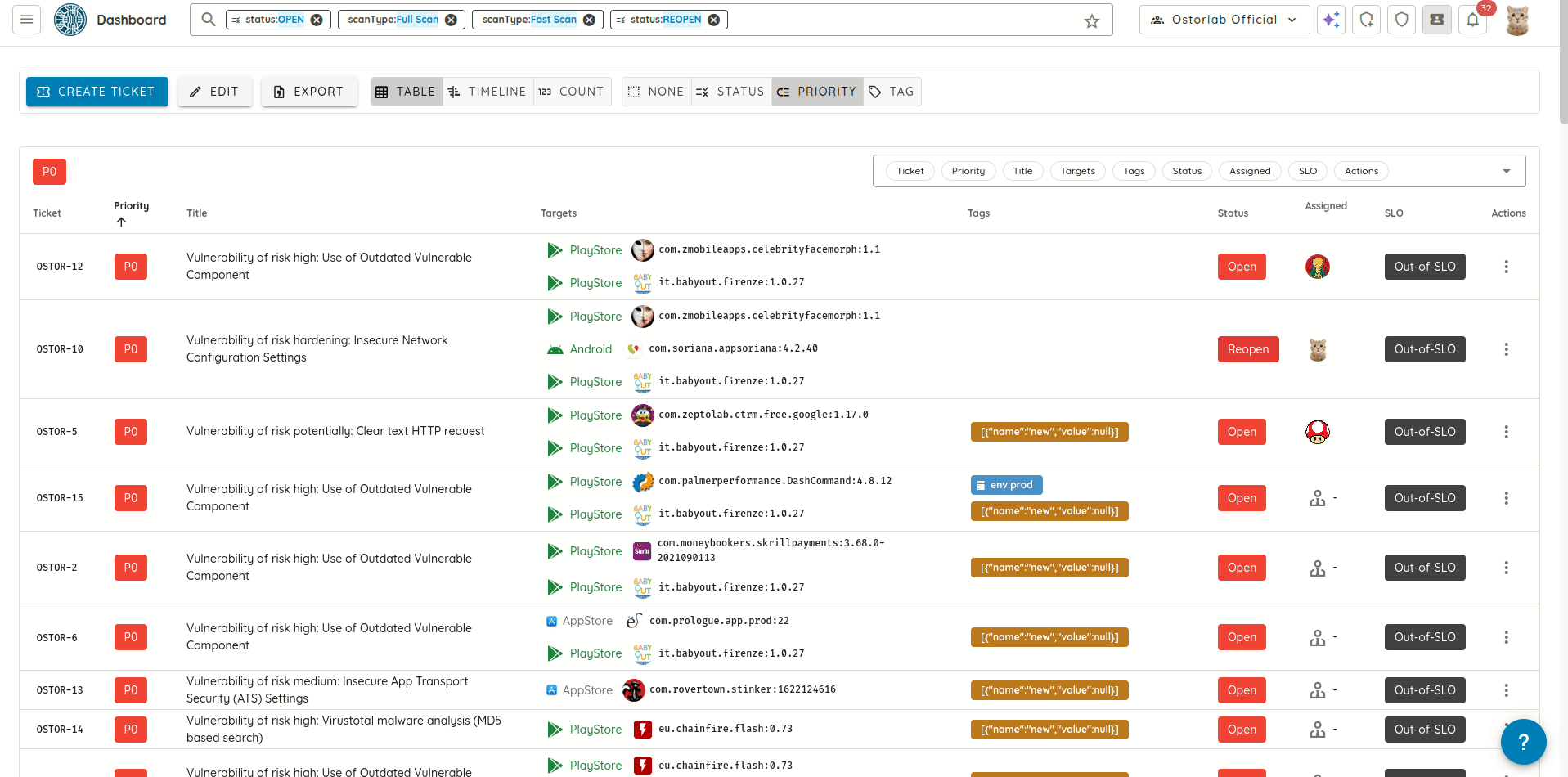
- Replaced Jira basic authentication with Personal Access Tokens (PATs) to ensure more secure and robust interactions with the Jira integration.
🛡️ Scanning
- Updated vulnerability reporting to include exploitation and post exploitation details. The details can be viewed using
oxo vulnz describe -s <scan_id>.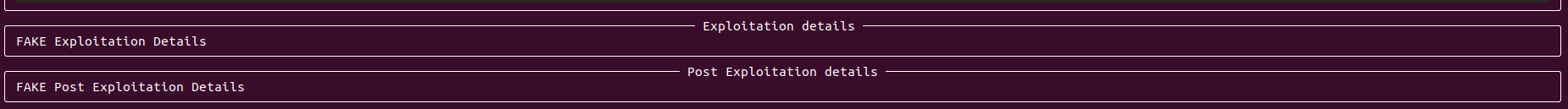
- Added persistence of session storage authentication in web scans, improving stability and results of web scans throughout the scanning process.
- Fixed a bug that prevented adding script test credentials when using Firefox, thereby improving browser compatibility and ensuring consistent behavior across environments.
- Fixed a bug that caused Smali and formatted source to not show in the scan analysis environment, restoring access to
important reverse-engineered code, aiding in deep technical analysis.
🐵 Monkey Tester
- Enhanced AI logic to handle complex application flows, therefore increasing scan coverage.
- Improved captcha handling to support more advanced testing strategies.
🕸️ Attack Surface
- Confirmed and discovered assets tables not refreshing when assets are confirmed or excluded, ensuring asset state
changes are immediately reflected.
- Fixed the network search filter not showing all IP addresses, improving visibility of your network assets.
🤖 Copilot
Made some changes to enhance user experience:
-
Added support for performing write actions in Copilot, empowering users to not just analyze but also act directly from Copilot, automating workflows and saving time.
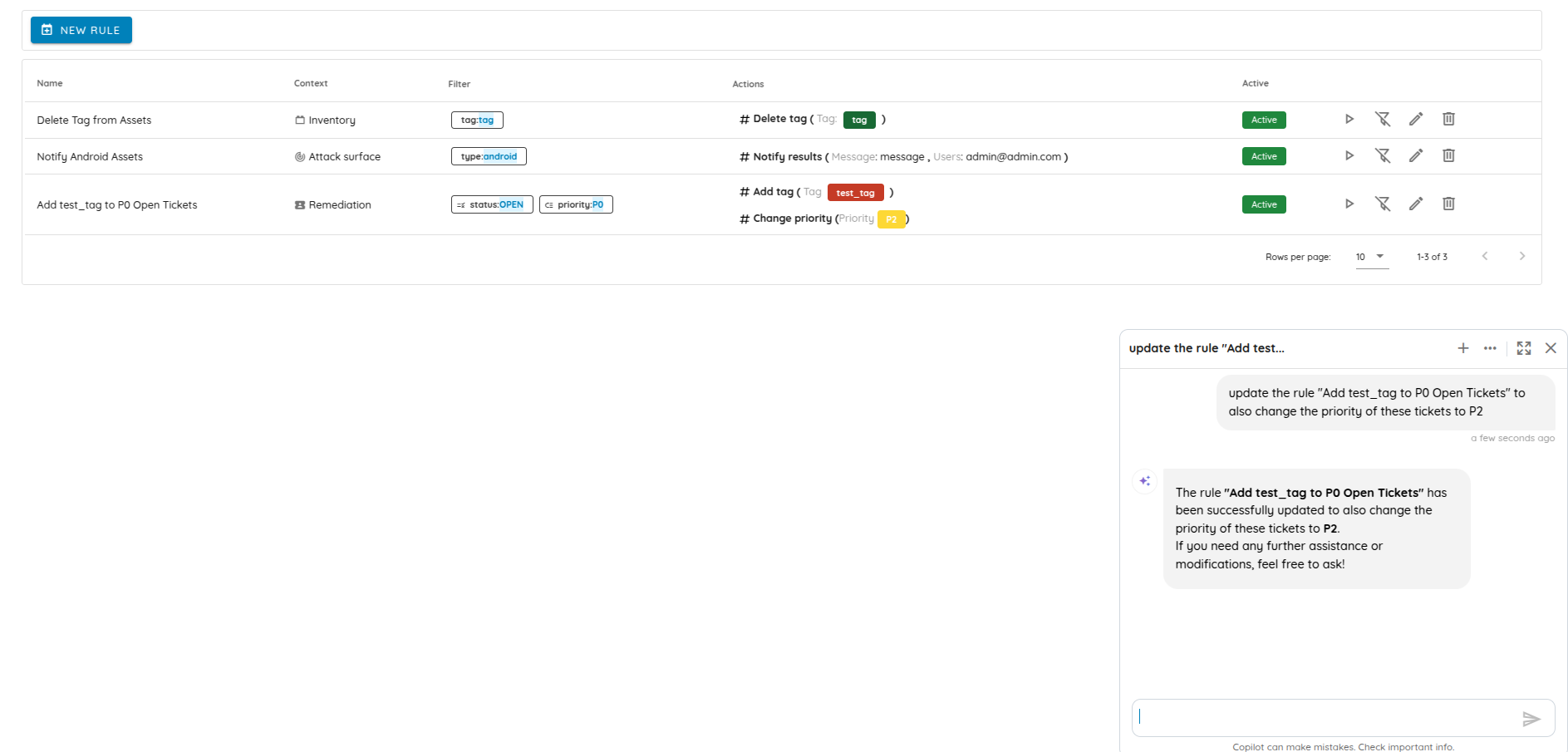
Updating an automation rule in Copilot -
Enhanced Copilot context and conversation suggestions, improving relevance and usefulness of recommendations, making Copilot more intuitive and helpful.
-
Updated Copilot to go to a new Copilot conversation when the active conversation is deleted, preventing confusion and ensuring smooth user navigation when managing multiple threads.
-
Fixed a bug that caused Copilot to not open in the Attack Surface page, ensuring full Copilot functionality across all pages.
🔍 Detection
Threat Center
Added support for several CVEs:
-
CVE-2025-27364: MITRE Caldera Agent Dynamic Compilation RCE - This exploit targets the dynamic compilation functionality in Caldera to achieve remote code execution by manipulating Go linker flags.
-
CVE-2024-12084: Rsync Heap Buffer Overflow - A crafted rsync traffic sequence can trigger a heap buffer overflow vulnerability in rsync. This is achieved by sending a specially constructed sum_struct header with a manipulated s2length value.
-
CVE-2024-48248: NAKIVO Backup and Replication Solution - Unauthenticated Arbitrary File Read (NAKIVO Backup & Replication is a data protection solution used for backing up and restoring virtualized and physical environments. A vulnerability has been identified in certain versions of NAKIVO Backup & Replication that allows an unauthenticated attacker to read arbitrary files on the underlying system.
-
CVE-2025-1974: Ingress-Nginx Controller - Remote Code Execution - A security issue was discovered in ingress-nginx where the
auth-tls-match-cnIngress annotation can be used to inject configuration into nginx. This can lead to arbitrary code execution in the context of the ingress-nginx controller, and disclosure of Secrets accessible to the controller. -
CVE-2025-29927: Next.js Middleware Bypass - Next.js contains a critical middleware bypass vulnerability affecting versions
11.1.4through15.2.2. The vulnerability allows attackers to bypass middleware security controls by sending a specially crafted 'x-middleware-subrequest' header, which can lead to authorization bypass and other security control circumvention. -
CVE-2025-24813: Apache Tomcat Path Equivalence - Remote Code Execution - Path Equivalence –
file.Name(Internal Dot) vulnerability in Apache Tomcat which may lead to Remote Code Execution, information disclosure, or malicious content injection via writable session files. -
CVE-2024-13160: Ivanti EPM - Credential Coercion Vulnerability in GetHashForWildcard - A vulnerability in Ivanti Endpoint Manager (EPM) allows an unauthenticated attacker to coerce the EPM machine account credential via the GetHashForWildcard endpoint. The vulnerability exists due to improper input validation in the wildcard parameter, allowing an attacker to specify a remote UNC path that triggers NTLM authentication.
-
CVE-2025-27636 - CVE-2025-29891: Apache Camel Exec Component Command Injection & Internal Method Invocation - Bypass/Injection vulnerabilities in Apache Camel. These issues affect Apache Camel: from
4.10.0through <=4.10.1, from4.8.0through <=4.8.4, from3.10.0through <=3.22.3. CVE-2025-27636: Case-insensitive header filtering bypass allows overriding static commands. CVE-2025-29891: Query parameter manipulation enables arbitrary command execution. -
CVE-2022-43939: Hitachi Vantara Pentaho Business Analytics Server - Auth Bypass & RCE (Hitachi Vantara’s Pentaho Business Analytics Server versions prior to
9.4.0.1,9.3.0.2, and all8.3.xare vulnerable due to improper handling of non-canonical URL paths during authorization decisions. This flaw, which is actively exploited in the wild, allows attackers not only to bypass security restrictions but, when chained with CVE-2022-43769, to execute arbitrary commands (RCE) on the server. -
CVE-2022-47945: Thinkphp Lang - Local File Inclusion - ThinkPHP Framework before
6.0.14allows local file inclusion via the lang parameter when the language pack feature is enabled (lang_switch_on=true). An unauthenticated and remote attacker can exploit this to execute arbitrary operating system commands, as demonstrated by includingpearcmd.php.