Tue 22 October 2024
Search 🎨
- Revamped Search: Reworked the search UI to make searching very seamless, without the hassle of having to remember search keywords.
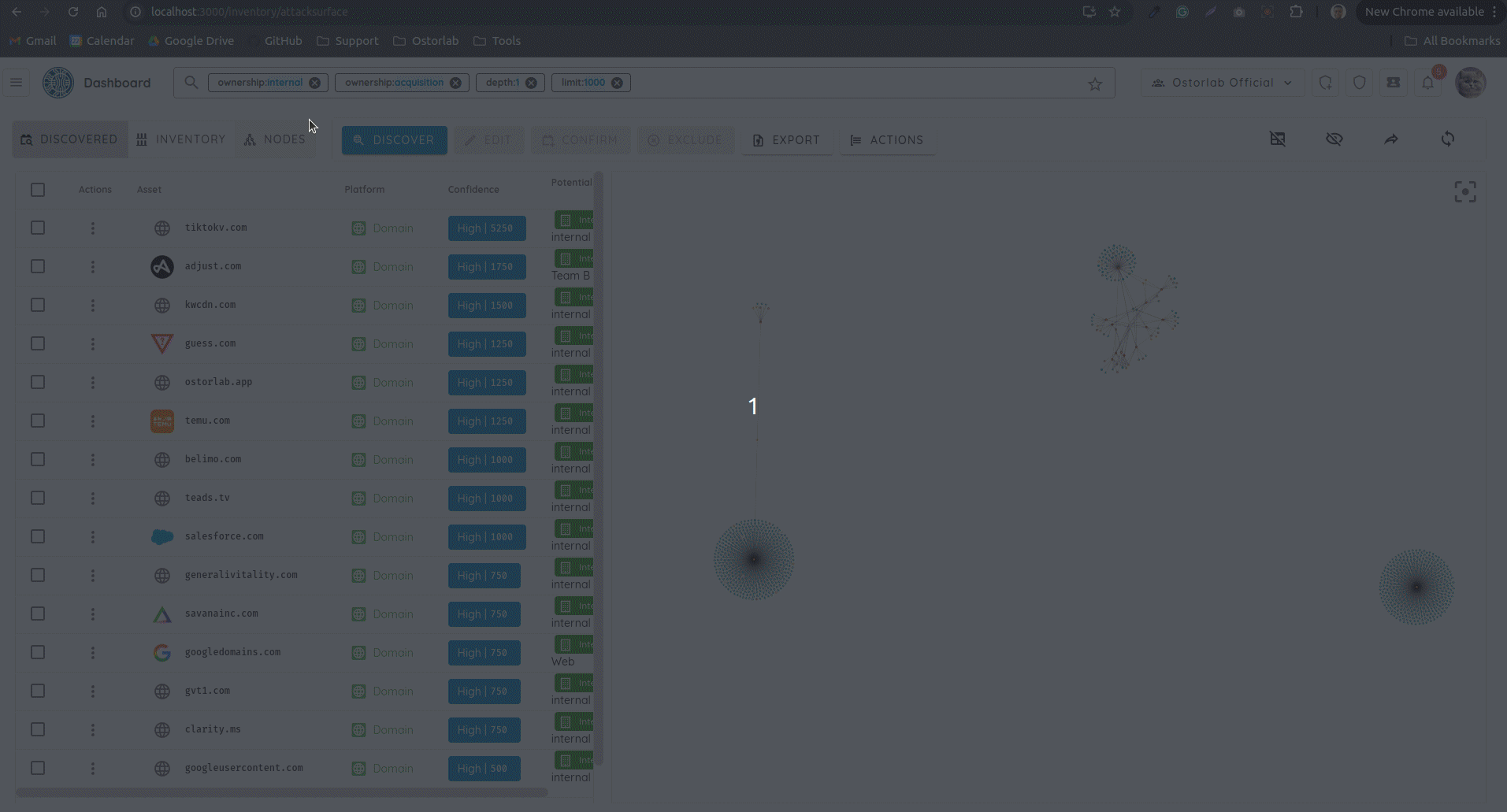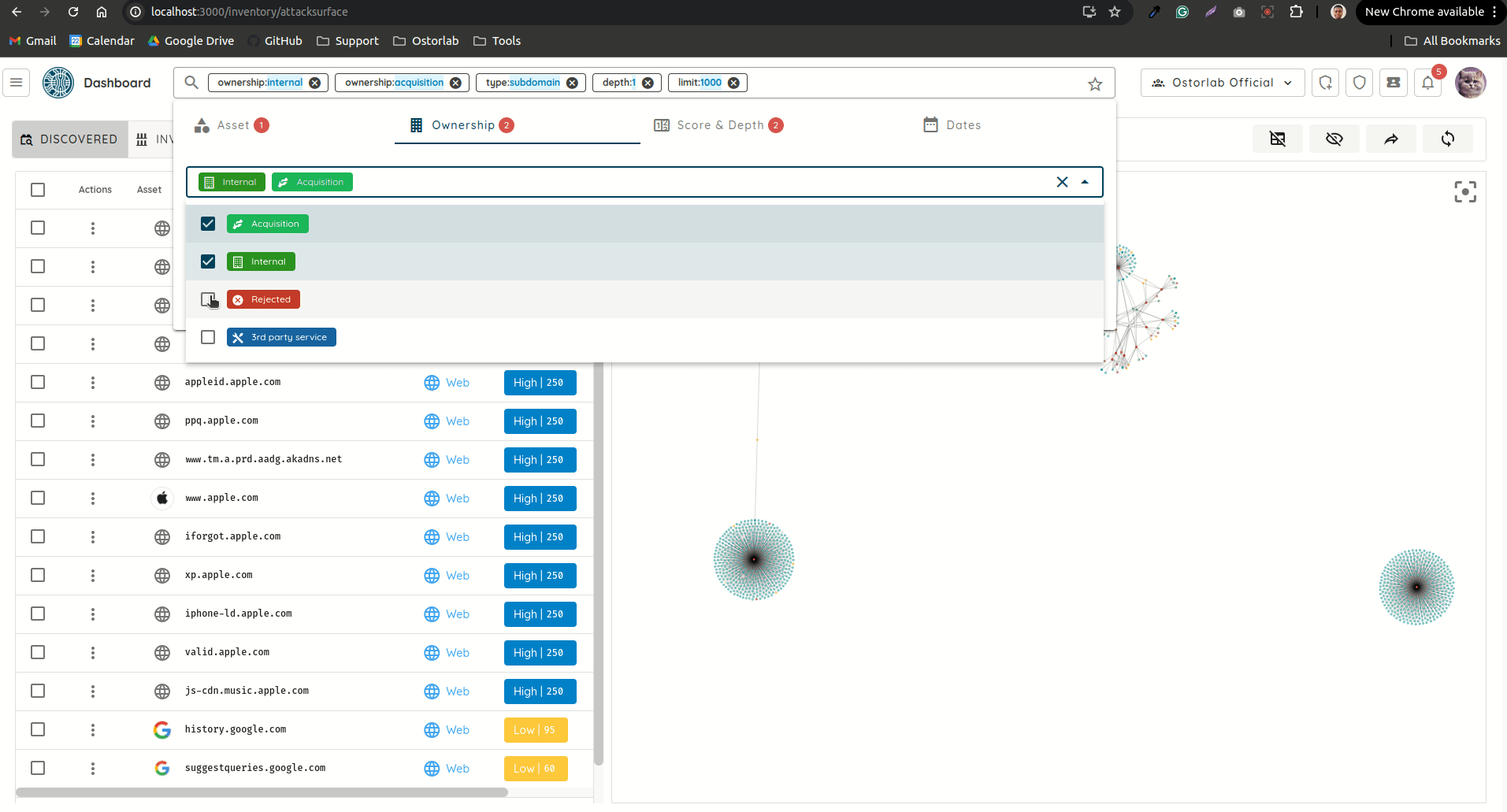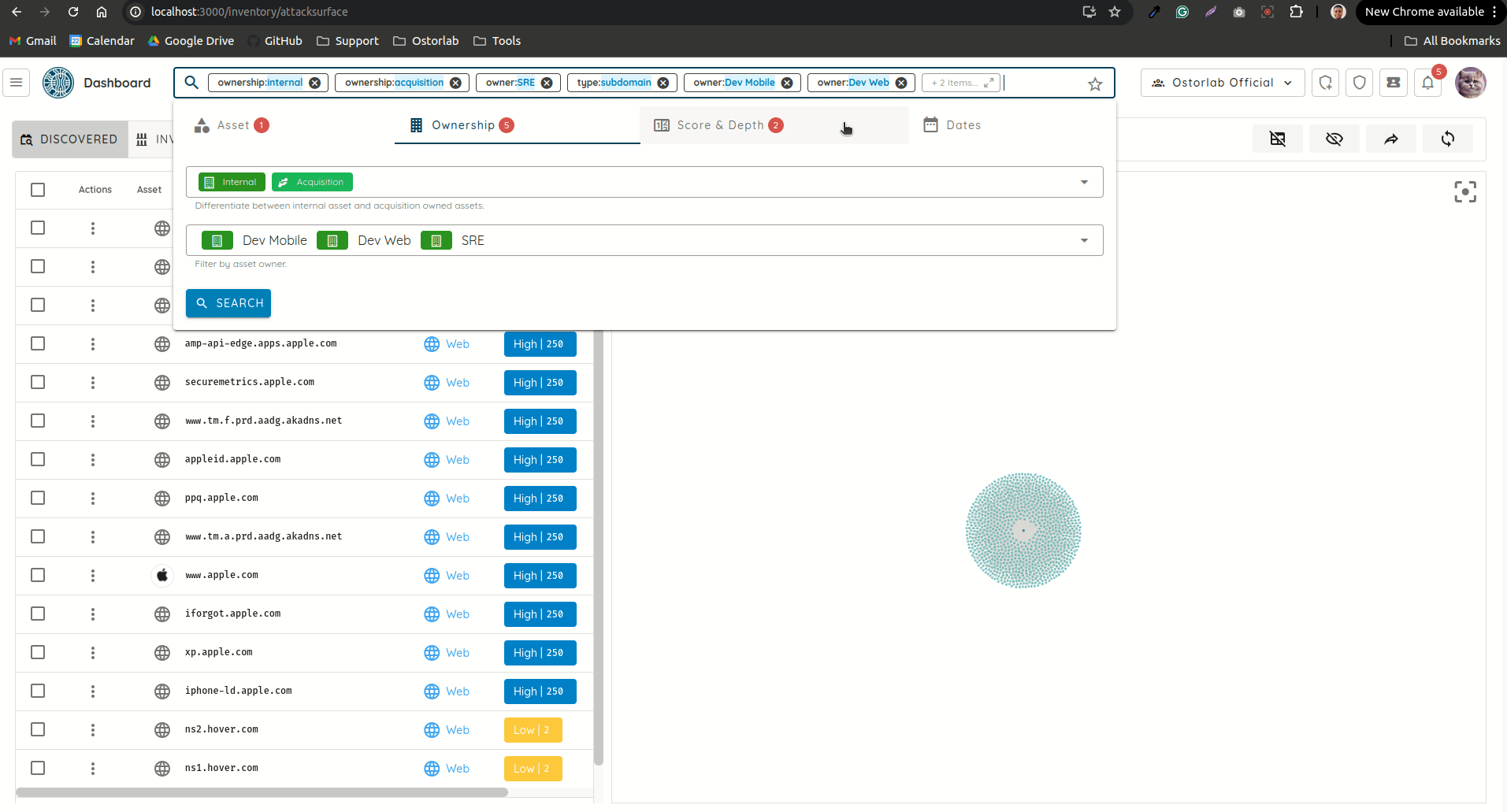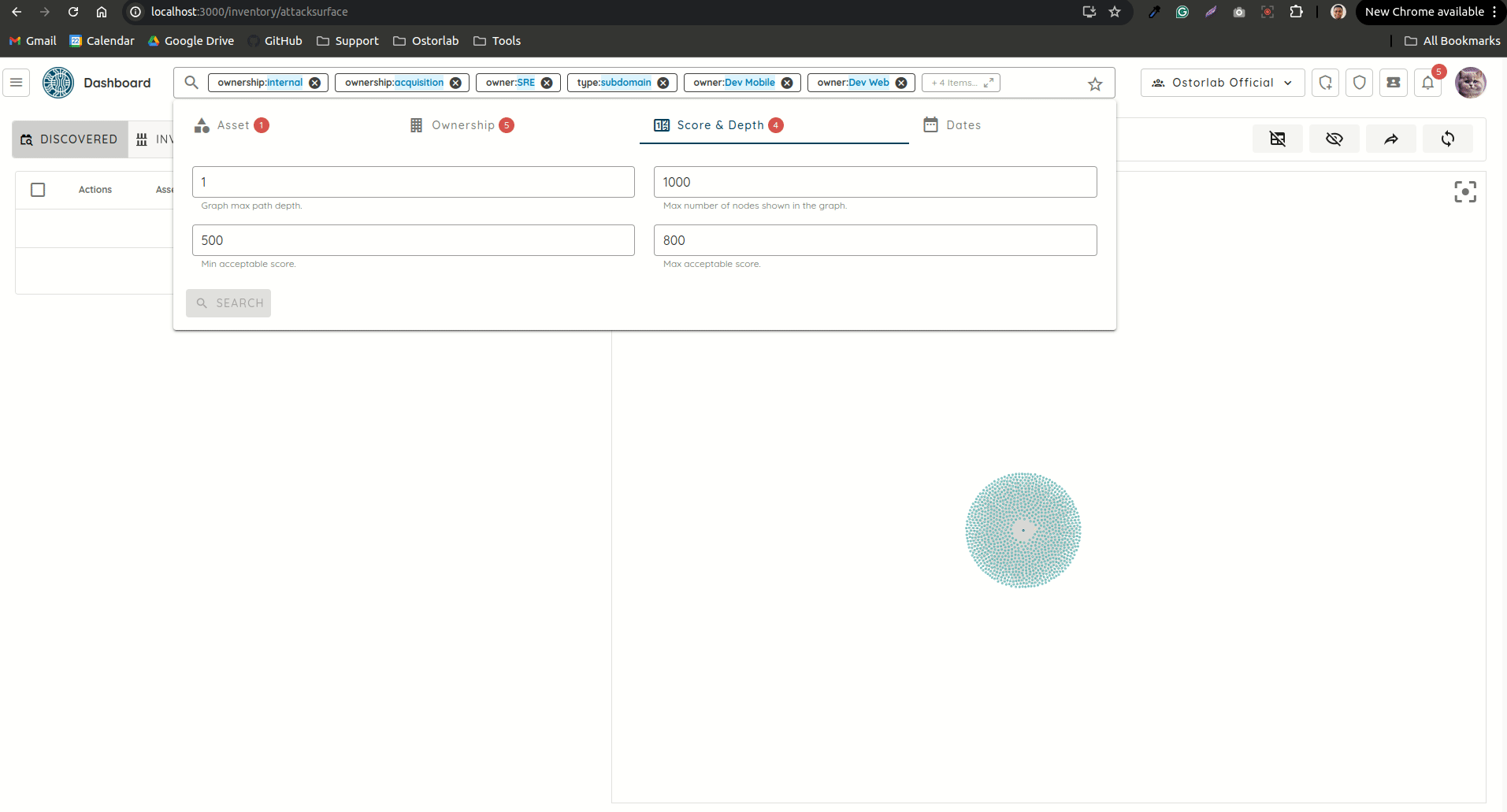
New Search UI - Added support for applying search filters even if Ticket Grouping is used.
- Fixed saved rules appearing to the all organisation users. Now, saved rules appear only to the user who saved them.
Remediation
- Allow the selection of any issue type available in the JIRA project scope.
Inventory & Attack Surface 🎯
- Search Assets using Regular Expressions (RegEx): Added support for advanced search patterns using regular expressions.
- Fixed slow loading of impacted assets in the threat center.
- Added support to limit assets to the asset owner when exporting potential nodes.
- Fixed a bug where in search with multiple fingerprints.
Detection 🔍
New Vulnerabilities
- Bleichenbacher vulnerability - Added detection for potential exposure to the Bleichenbacher attack (PKCS#1 v1.5 padding oracle) in SSL/TLS connections. The Bleichenbacher attack allows attackers to exploit weaknesses in RSA-encrypted communications, potentially decrypting sensitive data such as session keys.
- Weak Cipher Suites - Added detection for identifying whether a server supports weak cipher suites in its SSL/TLS connections.
- Raccoon Attack Implementation - Added detection for Raccoon Attack vulnerabilities in SSL certificates.
- ALPACA Attack - Added detection for ALPACA (Application Layer Protocol Confusion) attack vulnerabilities in SSL/TLS certificates.
- Backdoored Cryptographic Algorithms - Detection for backdoored cryptographic algorithms in SSL certificates, specifically targeting RC4 and Dual_EC_DRBG.
- Lucky Thirteen - The Lucky Thirteen attack targets the TLS (Transport Layer Security) protocol, specifically its handling of padding in encrypted messages. This attack exploits vulnerabilities in certain TLS implementations with block ciphers like AES.
- SSL/TLS Protocol - Added detection to identify outdated and potentially vulnerable SSL/TLS protocols such as SSLv3, TLSv1, and TLSv1.1, which are known to have security vulnerabilities.
- SSL Certificate - This check assesses the security and validity of SSL/TLS certificates by analyzing the certificate's attributes and ensuring compliance with modern best practices. Additionally, the check supports both domain names and IP addresses as targets for validation.
- Forward Secrecy in SSL/TLS connections - Checks if the server does not support Forward Secrecy (FS), which is vital for protecting session keys.
CVEs & Fingerprinting
- Add Jetpack version based detection - This implementation introduces detection for vulnerable Jetpack plugin actively exploited in the wild.
- CVE-2024-9634 - Detection of the GiveWP – Donation Plugin and Fundraising Platform plugin for WordPress is vulnerable to PHP Object Injection in versions up to
3.16.3. - CVE-2024-9487 - Detection of a cryptographic signature verification flaw in GitHub Enterprise Server allowed bypassing SAML SSO authentication leading to unauthorized user access.
- CVE-2024-23113 - Detection of a critical format string vulnerability affecting various Fortinet devices, including
FortiOS,FortiProxy,FortiPAM, andFortiSwitchManage. - CVE-2024-47374 - LiteSpeed Cache plugin for WordPress is vulnerable to a stored cross-site scripting (XSS) vulnerability in versions up to and including
6.5.0.2. - CVE-2024-28987 - The SolarWinds Web Help Desk (WHD) software is affected by a hardcoded credential vulnerability, allowing remote unauthenticated user to access internal functionality and modify data.
- CVE-2024-9463 - An OS command injection vulnerability in Palo Alto Networks Expedition allows an unauthenticated attacker to run arbitrary OS commands as root in Expedition, resulting in the disclosure of usernames, clear-text passwords, device configurations, and device API keys of PAN-OS firewalls.
Authorization Bypass 🔐
- Fixes to 4xx Bypass Detection to Remediate False Positives: Improved detection accuracy to reduce false positives in 4xx bypass scenarios.