Mon 07 October 2024
Network Interception 🚦
- Add HTTP2 Support: Implemented support for HTTP2 traffic extraction. HTTP2 is more powerful than HTTP1 but comes with increased complexity to reconstruct traffic.
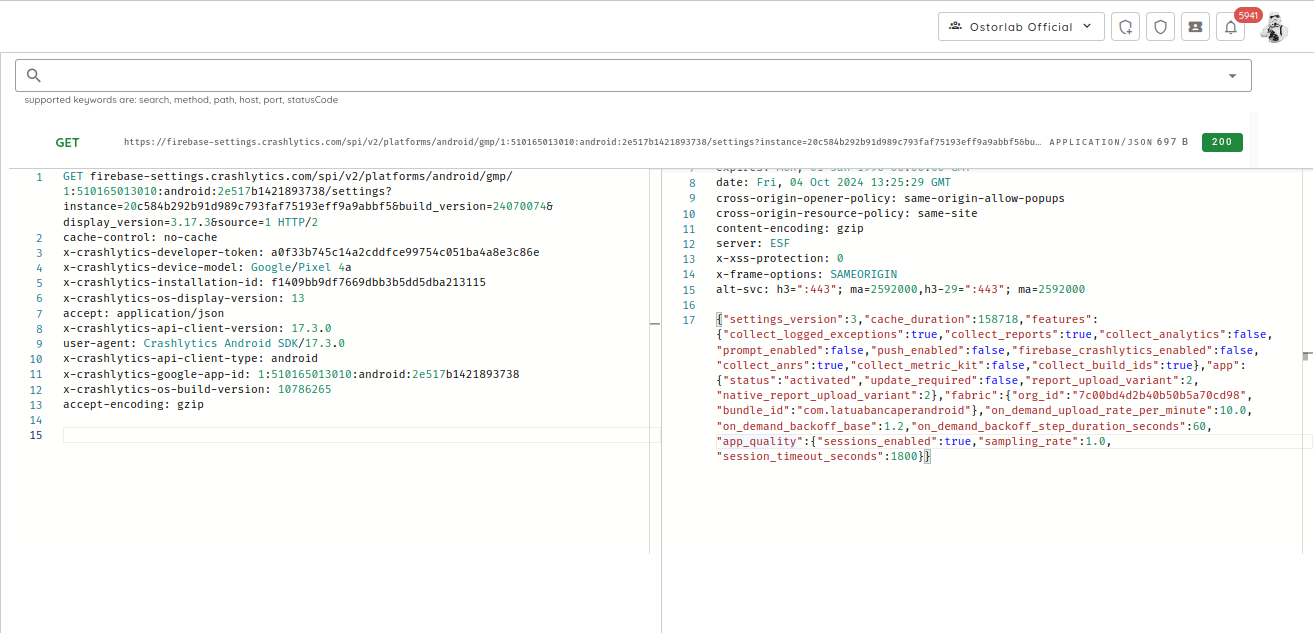
- Fix HTTP1 Handling: Resolved issues with handling requests under the HTTP1 protocol to maintain compatibility.
UI 🎨
-
Improve Reporting of Outdated Dependencies: Enhanced reporting of vulnerabilities due to outdated dependencies to offer a clearer understanding of the issue and where it is.
-
Improve Privacy Issues Detection: Upgraded detection mechanisms to better identify and manage privacy-related issues.
-
Fix to Oxotitan UI: Addressed UI glitches and improved overall user interface consistency for a smoother user experience.
-
Add Sorting of Findings by Risk: Introduced sorting capabilities for findings based on risk, making prioritization more efficient.
-
Improvement to Tags Listing and Autocomplete: Enhanced tags listing and autocomplete features to improve usability and user interaction.
Detection 🔍
-
Add Support for More Scalar Types in API Autodiscovery: Extended support for additional scalar types, enhancing compatibility with diverse API schemas.
-
Add Detection and Fingerprinting of Several CVEs: Implemented mechanisms for detecting and fingerprinting multiple CVEs, strengthening security posture, specifically:
-
CVE-2024-47176 - This vulnerability involves the CUPS (Common UNIX Printing System), allowing potential remote execution of arbitrary code by exploiting improper input validation and binding to an unrestricted IP address [1][2].
- CVE-2024-8963 - A path traversal vulnerability in Ivanti Cloud Services Appliance versions before 4.6 Patch 519, allowing unauthorized remote access to restricted functionality [1].
- CVE-2024-8522 - A SQL Injection vulnerability in the LearnPress WordPress plugin allows unauthenticated attackers to execute arbitrary SQL queries via the '/wp-json/learnpress/v1/courses' API endpoint, potentially extracting sensitive data.
- CVE-2024-45409 - A vulnerability in the Ruby SAML library improperly verifies the signature of SAML responses, allowing unauthenticated attackers to forge SAML assertions and potentially log in as arbitrary users [1][2].
- CVE-2024-40711 - An out-of-bounds write vulnerability in the ImageMagick software suite allows attackers to trigger the issue via specially crafted image files, potentially leading to arbitrary code execution.
Custom Checks ✔️
- Add Support for Private Repos: Enabled functionality to work with private repositories securely.
-
Use Deploy SSH Keys: Introduced use of deploy SSH keys for secure operations in private environments.
-
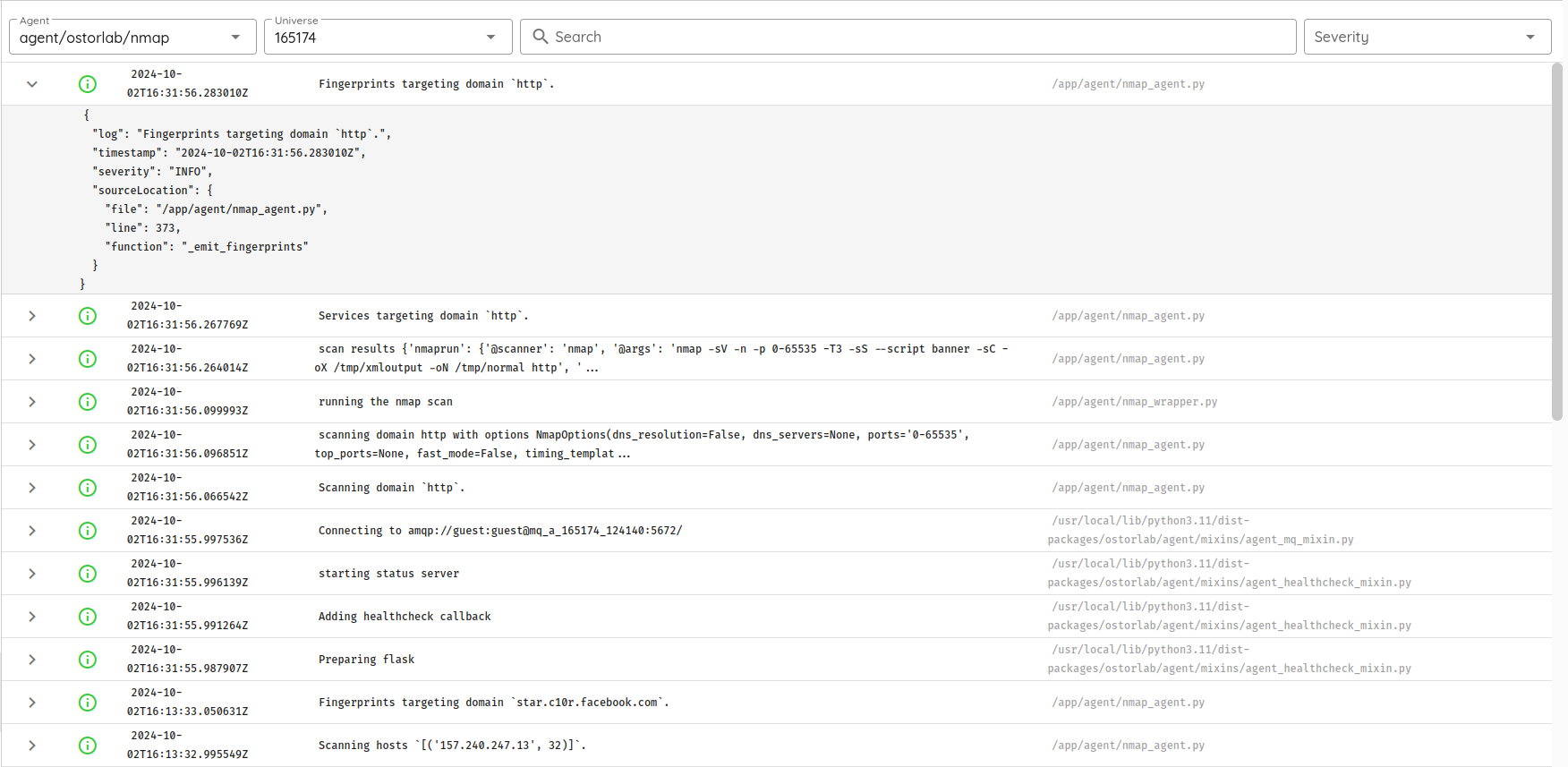
Add Support for Custom Agent Logs: Facilitated the generation and management of custom logs for monitoring agent activities.
Analysis Environment 🧩
-
Add API Endpoints to Scans Analysis Environment: Added new API endpoints to enhance scans analysis and improve investigation processes.
-
Improve Request-Response Research: Optimized methodologies for analyzing request-response interactions for better performance.
-
Add Mixing of Java and C Stack Traces: Enhanced debugging capabilities by enabling mixed Java and C stack trace analysis.
Attack Surface 🎯
- Fix Grouping of Fingerprints in Attack Surface by Adding OS: Improved fingerprint grouping to include OS data, optimizing analysis and identification.
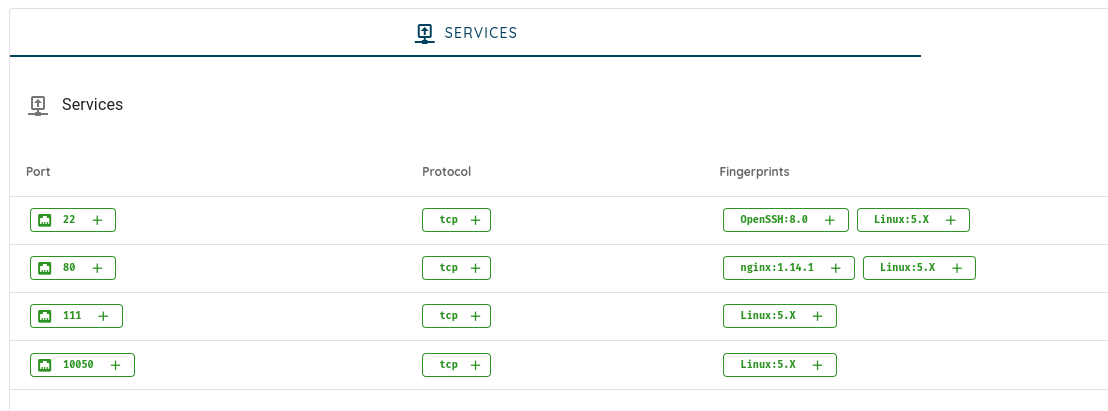
- Fix Fingerprint Collection for IP Assets: Enhanced processes for collecting fingerprints related to IP assets for more accurate assessments.
Instrumentation 📏
- Fix Parsing of Integer Arguments in Flutter/Dart Apps: Corrected parsing logic for integer arguments within Flutter/Dart applications to ensure accuracy.
Authorization Bypass 🔐
-
Fixes to 4xx Bypass Detection to Remediate False Positives: Improved detection accuracy to reduce false positives in 4xx bypass scenarios.
-
Support for Archived Pages Detection: Implemented support to identify and handle archived pages, aiding historical data analysis.
RSS Feed 📡
- Add RSS Feed: Introduced an RSS feed to keep users updated on the latest changes. Access it
https://blog.ostorlab.co/feed/rss.xmlorhttps://blog.ostorlab.co/feed/atom.xml
Tags:
http2, kev, oxo, oxotitan, api autodiscovery, attack surface, threat center, custom agent, 4xx bypass