Mon 01 July 2024
This update introduces bug fixes, detection improvements, and attack surface enhancements to provide a more seamless user experience.
🛡️ Scanning
- Show source code for the detected vulnerabilities in the vulnerability details page.
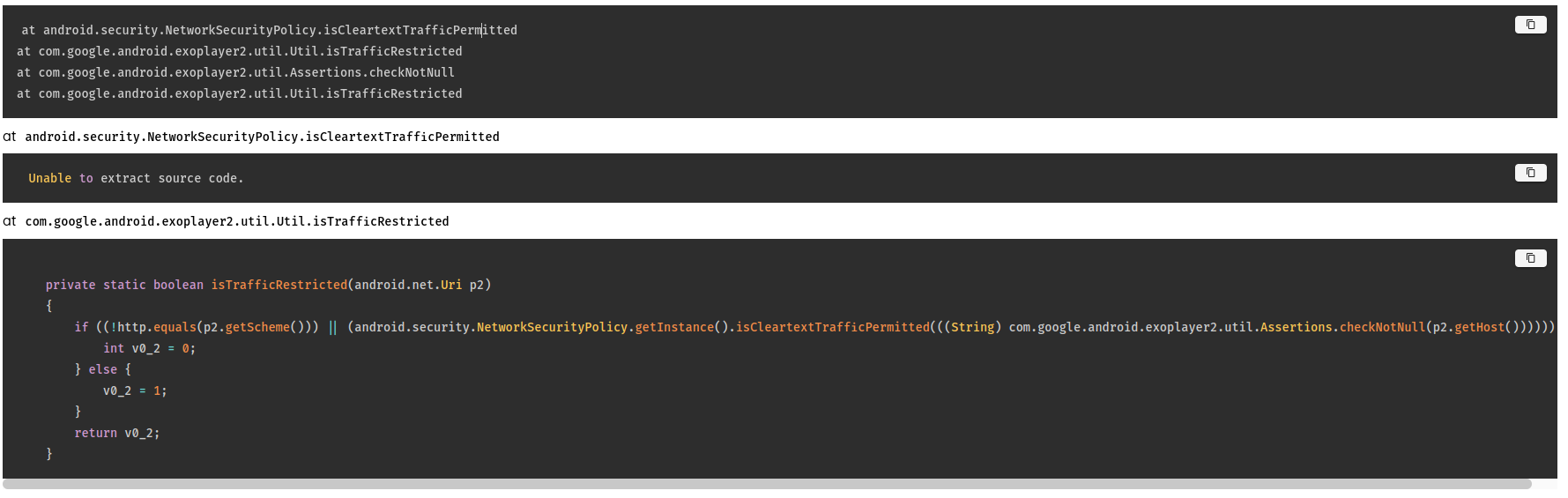
Source code for detected vulnerabilities
🛠️ Remediation
- Customized the weekly email for attack surface auditors to only contain their data.

The weekly email for attack surface auditors
🕸️ Attack Surface & Inventory
- Added autocomplete for tags in assets.
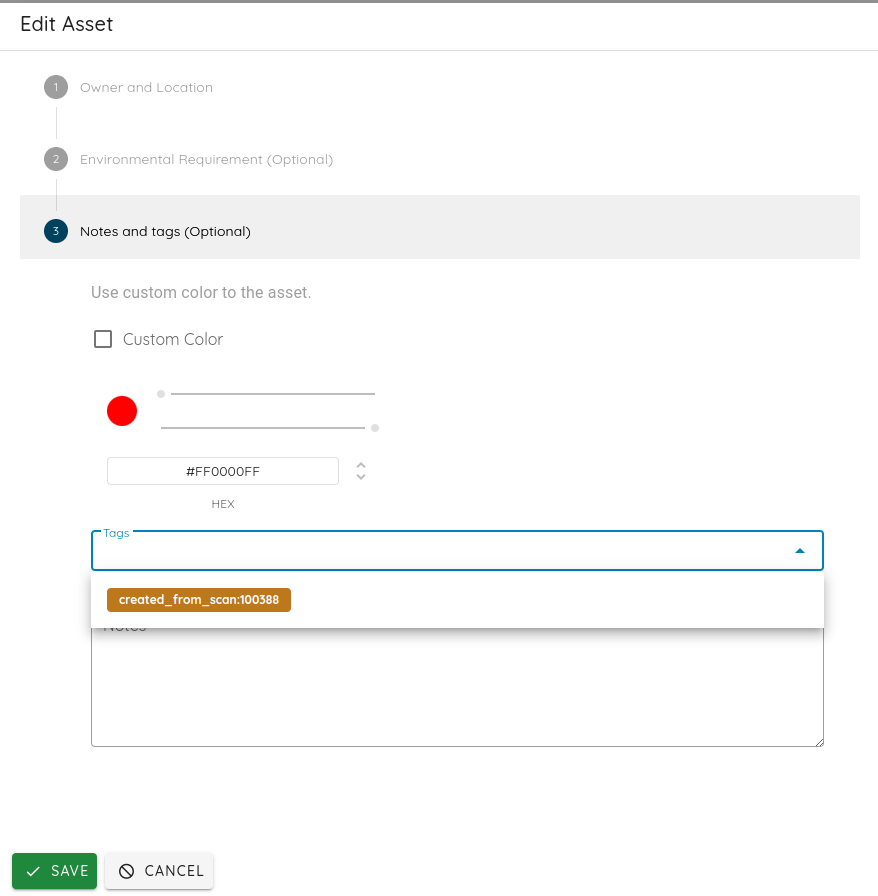
Autocomplete for tags in asset - Enabled filtering of assets by ownership type.
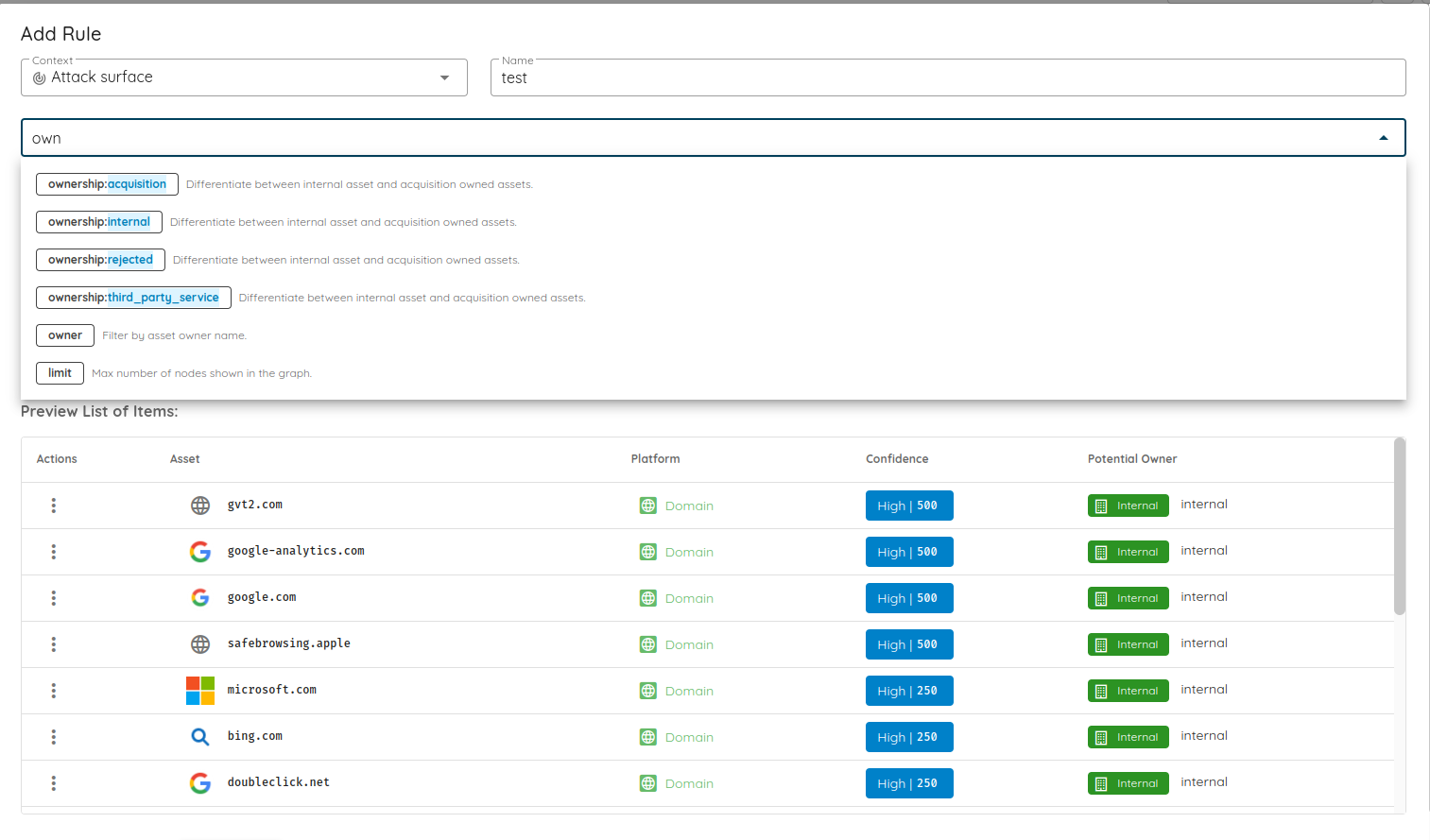
Filter the assets by the ownership type
📦 Detection
- Added detection for
CVE-2022-24816: A remote code execution vulnerability in the JT-JIFFLE extension of Geoserver allows remote attackers to execute arbitrary code. - Added detection for
CVE-2024-34470: An issue was discovered in HSC Mailinspector 5.2.17-3 through v.5.2.18. An Unauthenticated Path Traversal vulnerability exists in the /public/loader.php file. The path parameter does not properly filter whether the file and directory passed are part of the webroot, allowing an attacker to read arbitrary files on the server.
🐞 Bug Fixes
- Fixed the search function with inputs that included a schema.
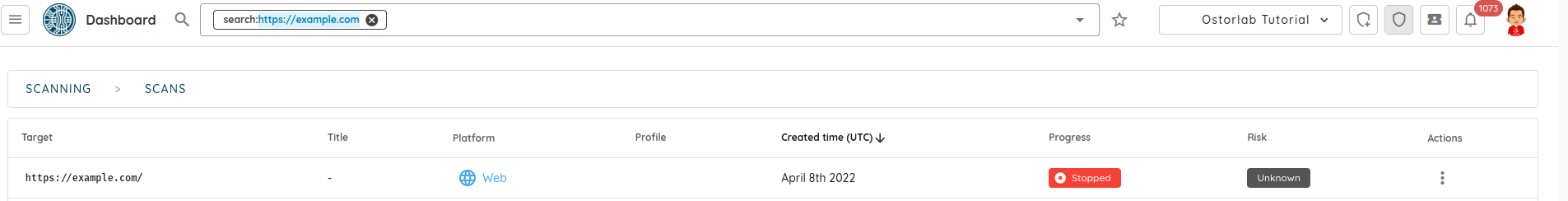
Searching scans using a specific schema - Fixed the iOS search issue when searching for common apps like Facebook.
Searching for common apps like Facebook - Fixed the issue where excluded values were still appearing in the graph during PDF generation.