Tue 01 November 2016
For an Android developer, it has become standard practice to use external libraries to easily extend the functionalities of the mobile application . Thanks to Gradle easy dependency integration, features like HTTP frameworks, database ORM, fancy scrolling, efficient image loading, caching, social network integration and many others can be added easily.
dependencies {
compile 'com.android.support:appcompat-v7:22.0.0'
}
External libraries makes development much easier and more efficient and it is even considered a best practice.
External libraries present however a security risk, ranging from new vulnerabilities, dangerous hidden features or even an uncanny backdoor.
Scanning the top 150 apps for external dependencies, we identified the following most used ones:
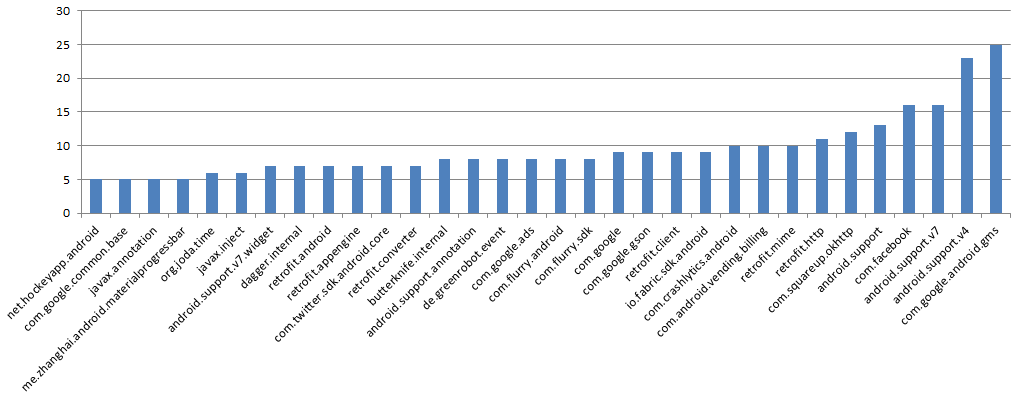
Most of these libraries are backed by companies like Twitter, Facebook or Square, but some are supported by a single developer, take ButterKnife for instance, the project lists 45 contributors, the first with 251 commit, the second with 13 commits and most of the rest with only 1 commit.
The compromise of this lib could lead to the compromise of million of users once the backdoored version is pushed to production. Others come as a blackbox and you can't even check the source code, like Flurry for instance.
The security of external libs is not an easy subject, but here are some recommendations to apply:
- Check the security notices of the library regularly and update the library accordingly
- Audit each external library before including it to your application.
- Control the interactions between external libraries and your application
- Before updating any library, check the content of the new submits
- Code sharing sites are regularly target to malicious attacks (Large Scale DDoS Attack on github.com). Check their blog, tweets to get informed.