Mon 11 January 2021
We are excited to announce the release of the Android and iOS application analysis environment. The goal of the environment is to ease manual assessment and offer the power to write custom checks on top of all the analyses done by Ostorlab, from taint analysis, dynamic call traces, intercepted traffic, and scanned API requests.
The current release focuses on static analysis and comes with the following features:
- APK and IPA file listing with content access
- Code highlighting for HTML, Javascript, XML, Java, C++
- Binary plist extraction
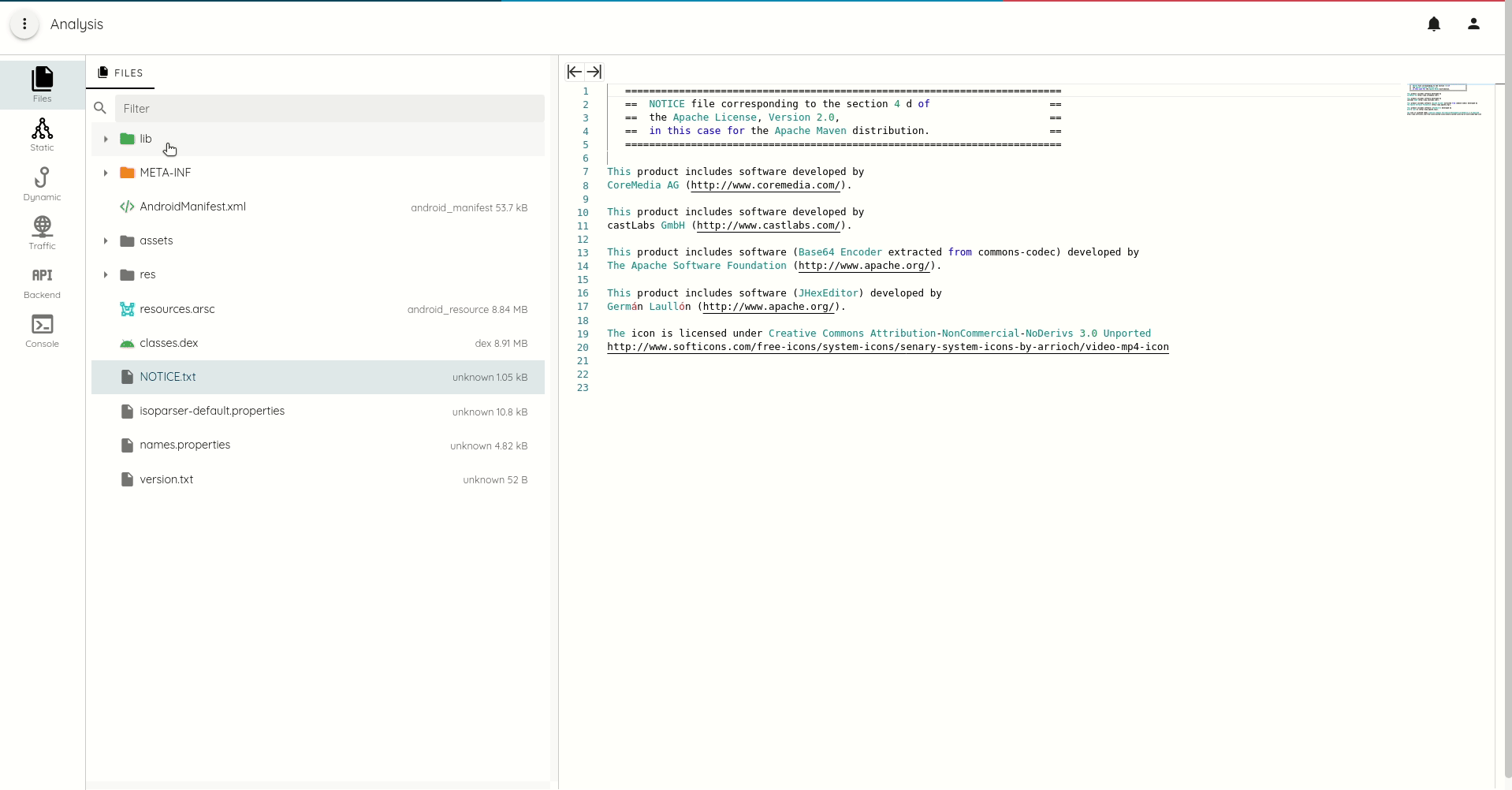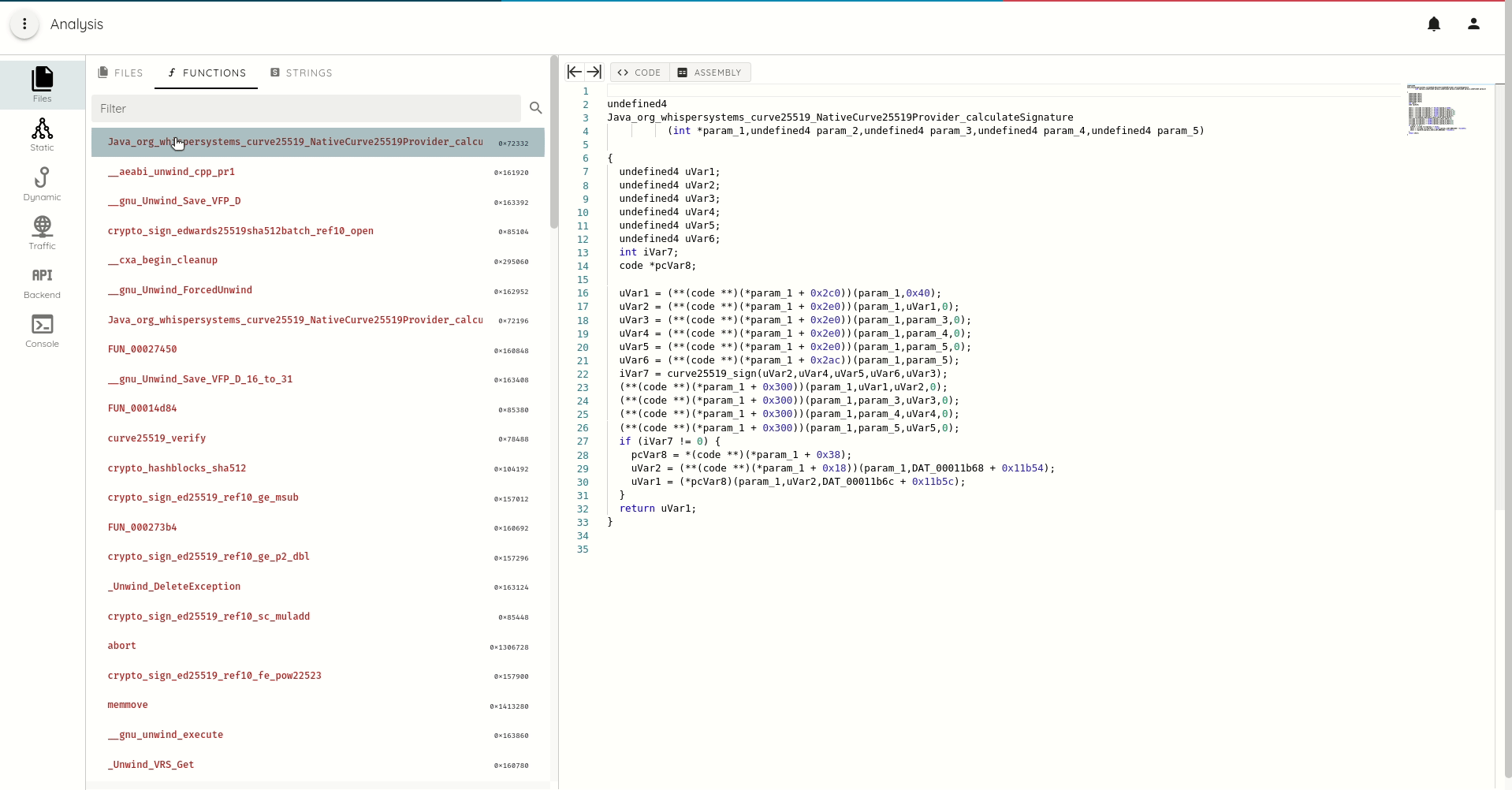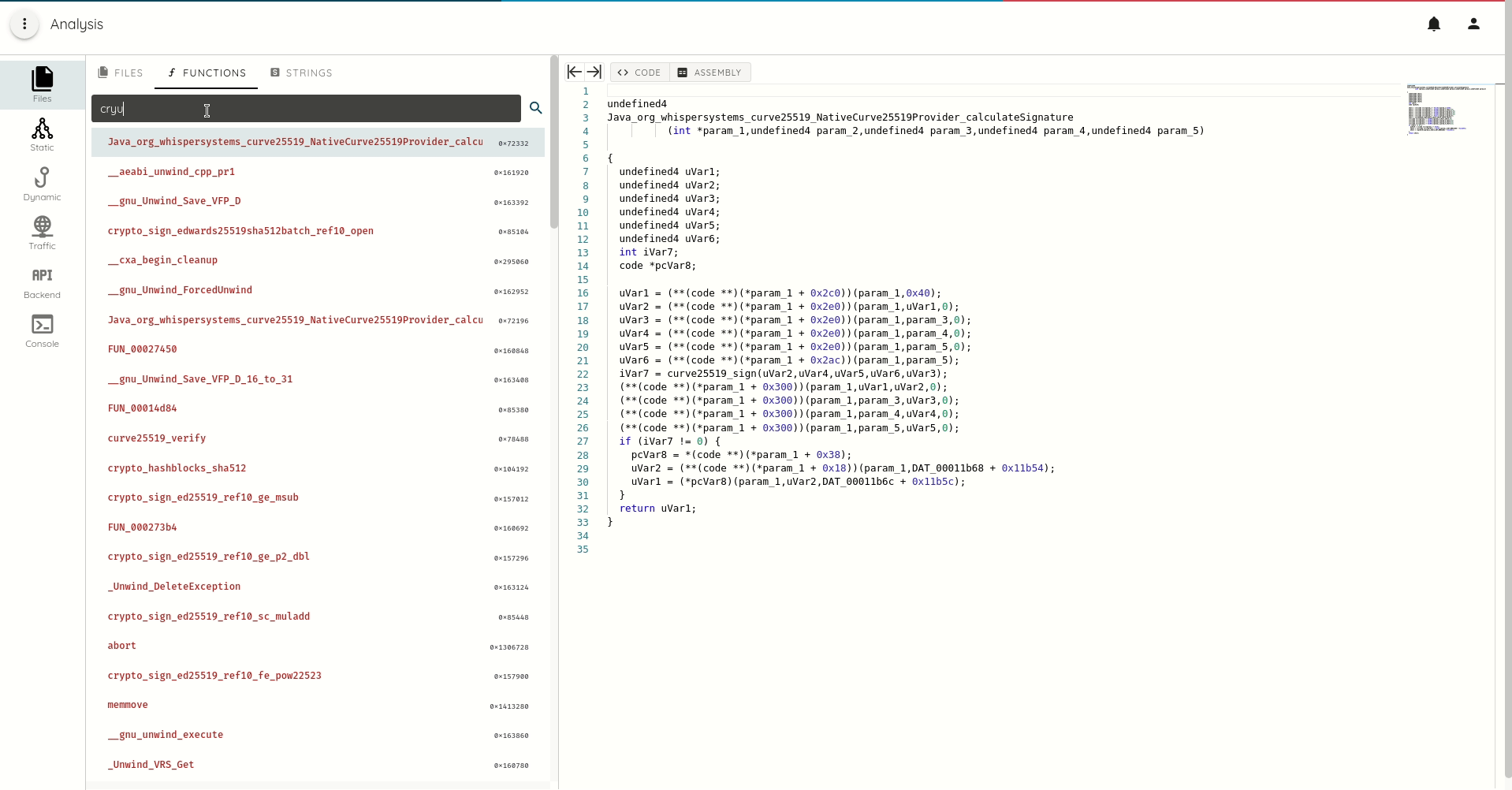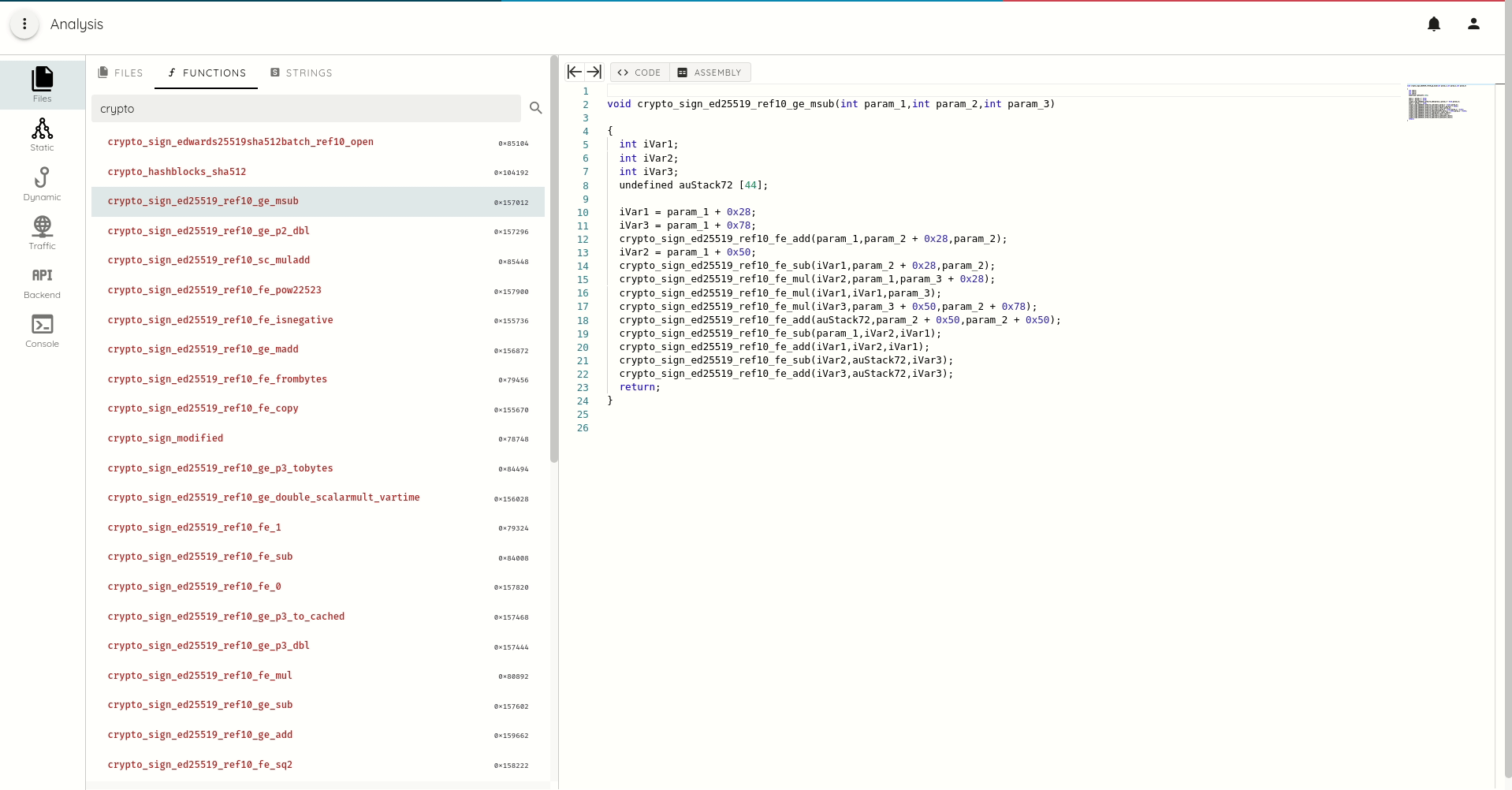
- Macho and ELF file disassembly and decompilation for ARM and ARM64
- Macho and ELF string listing
- DEX classes listing
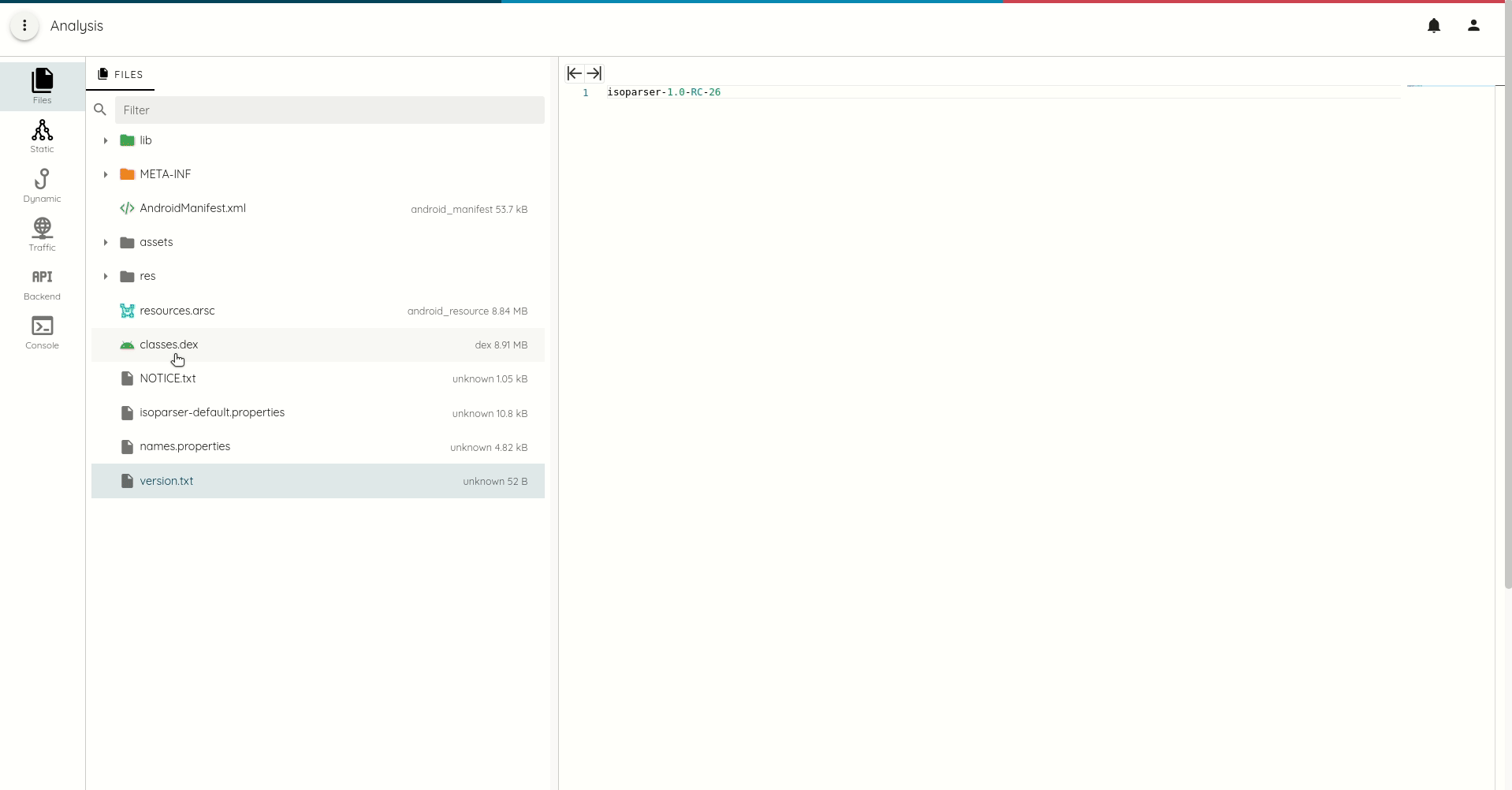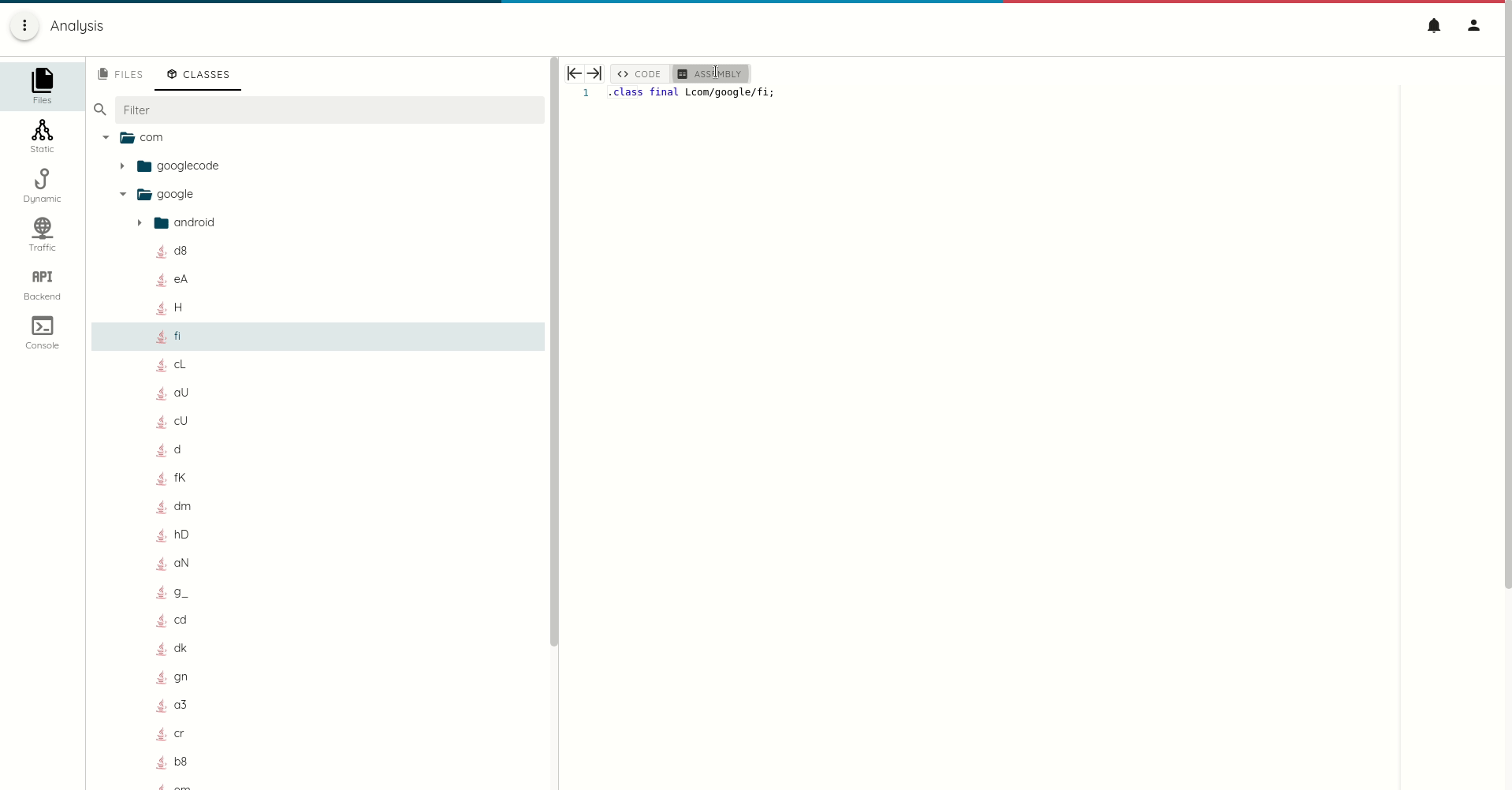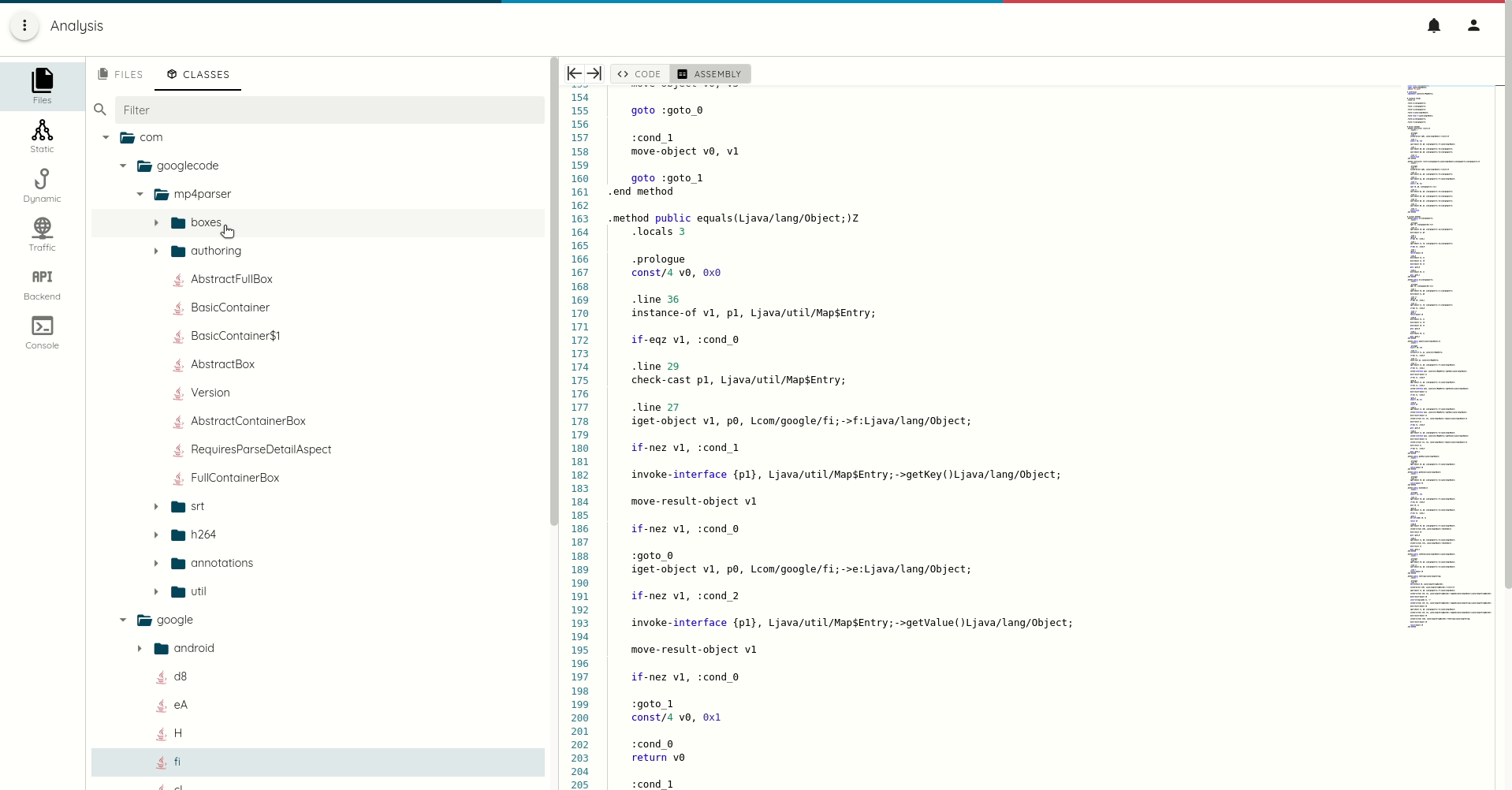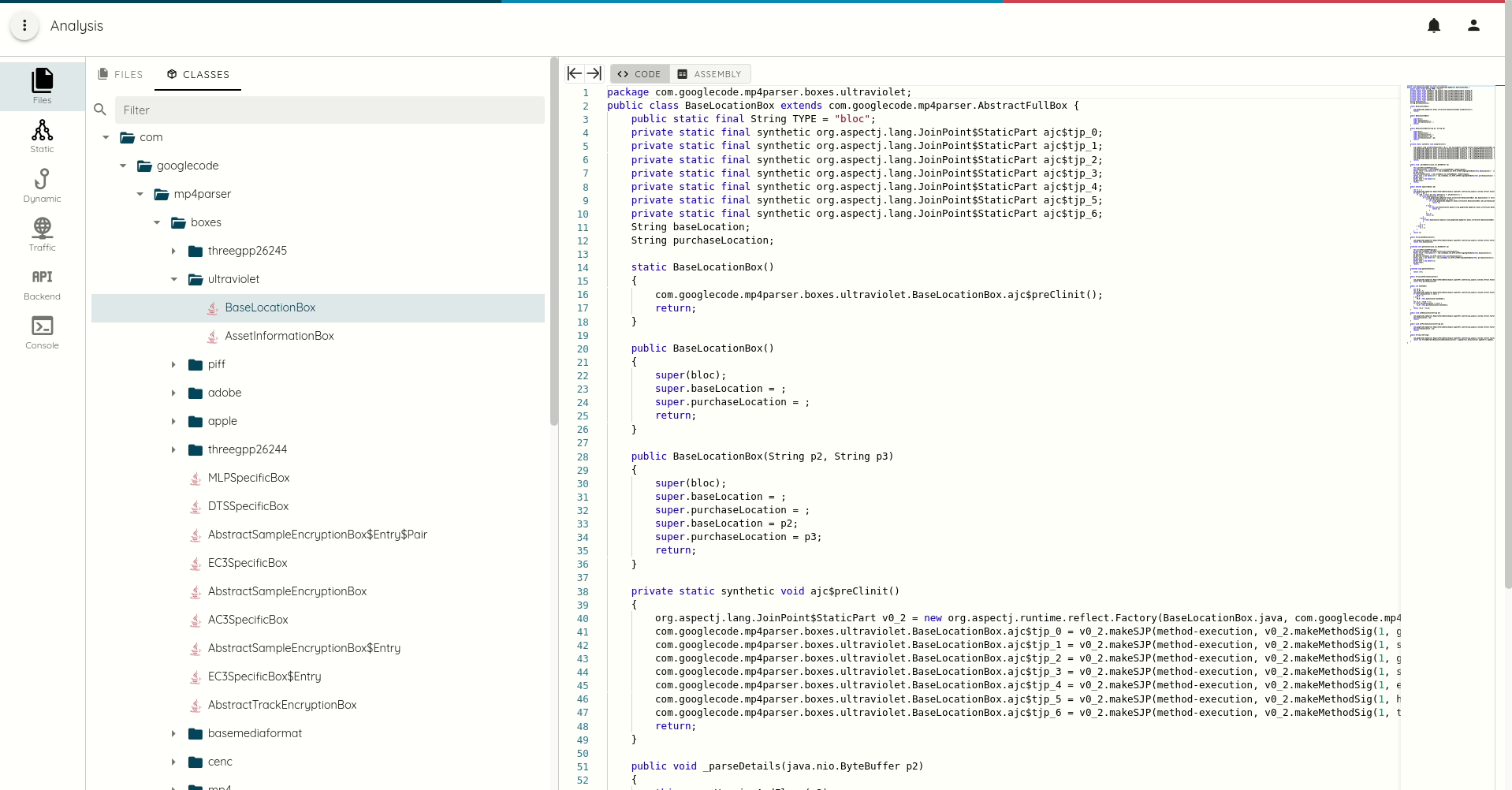
- DEX smali listing and java decompilation
- Android resource extraction
- Android manifest extraction
- DEX, Macho, and ELF function call trace with full refs and xrefs generation
-
Dangerous functions tagging to identify security hotspots. The tagging differentiates between:
- Sink: over a dozen sink categories. Sinks are functions or method that can lead to vulnerabilities, like
execSQLthat can lead to SQL injection if the input is controlled by the user. - Source: Source function and methods return untrusted input that could come from the network, IPC, filesystem (external storage) ... Source function should be sanitized before use by sink methods.
- Privacy Source: Privacy source functions and methods return sensitive input, like user location, SMS, wifi endpoints that can affect the privacy of the user
- Input: Input methods are typically overridable methods that serve as callbacks and whose parameters are untrusted
and can be manipulated by an attacker. A typical example is content providers
query,update,insert,delete, etc methods. - Sanitizer: sanitizer function and methods are used to scrub untrusted input for particular API use.
- Persist Read and Write: Persist read and write are helpful to find 2nd order injection vulnerabilities. Read and Write operations are separate.
- Deprecated: simply deprecated functions and methods.
- Sink: over a dozen sink categories. Sinks are functions or method that can lead to vulnerabilities, like
-
Contextual call trace generation.
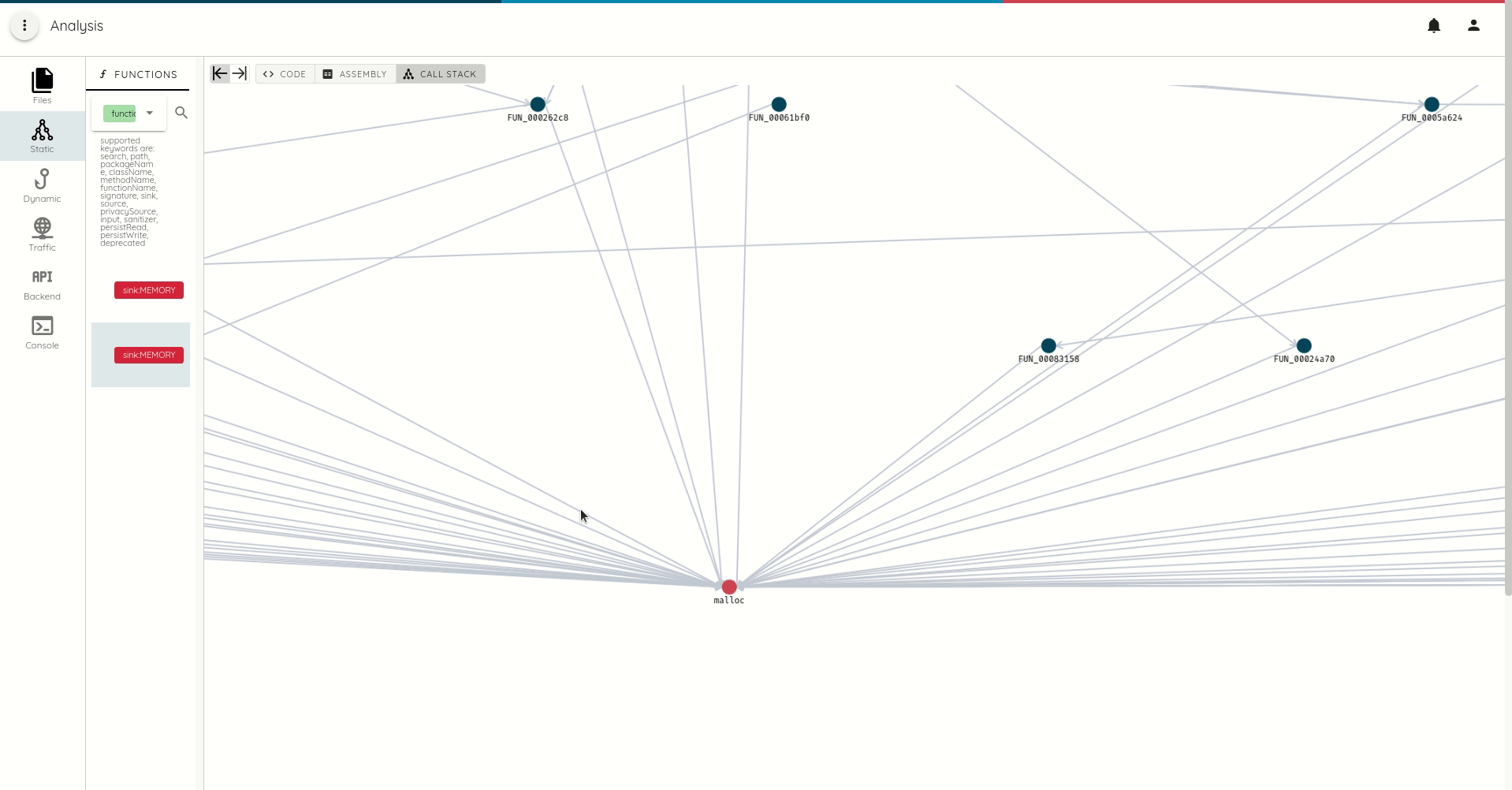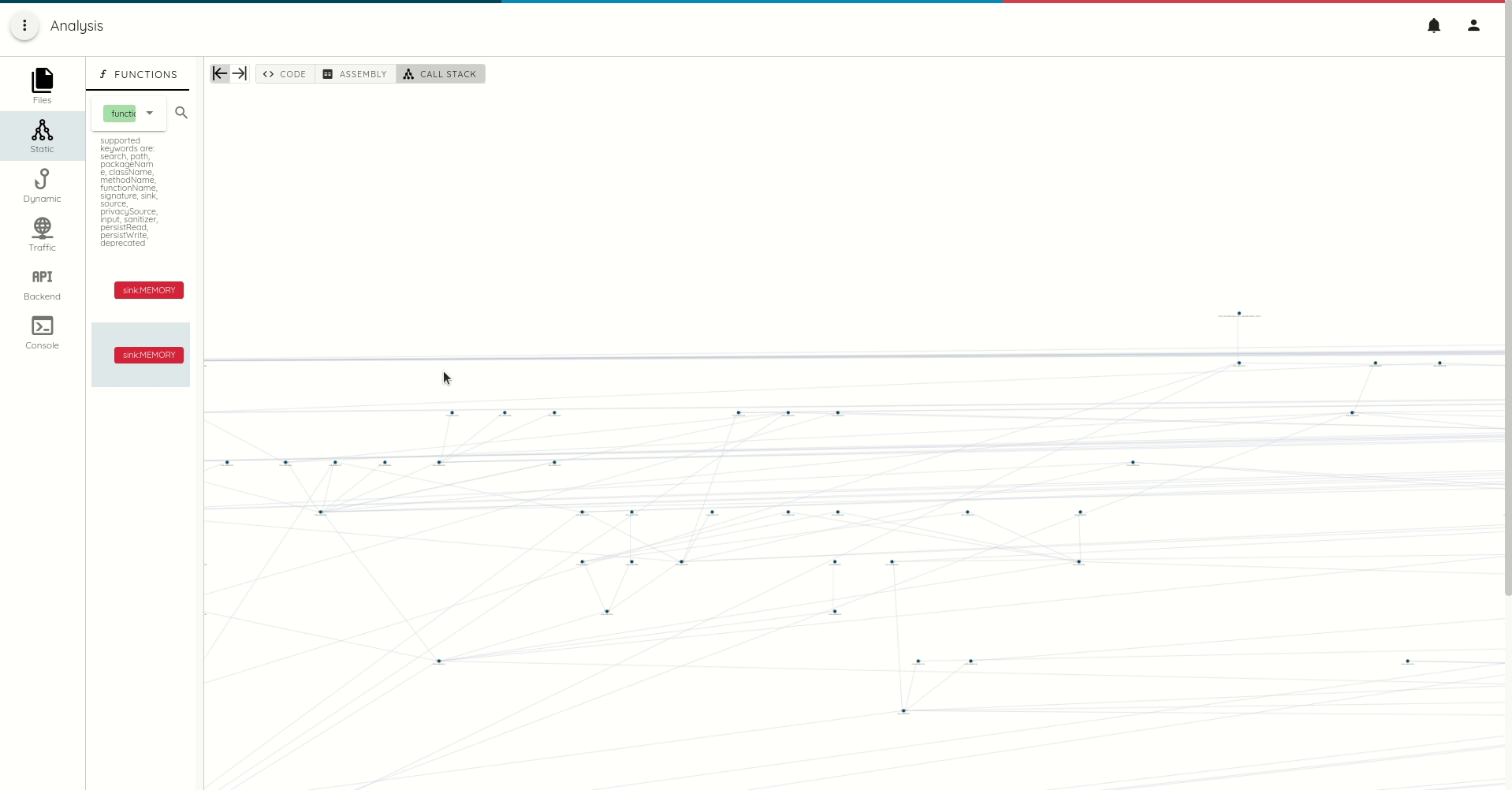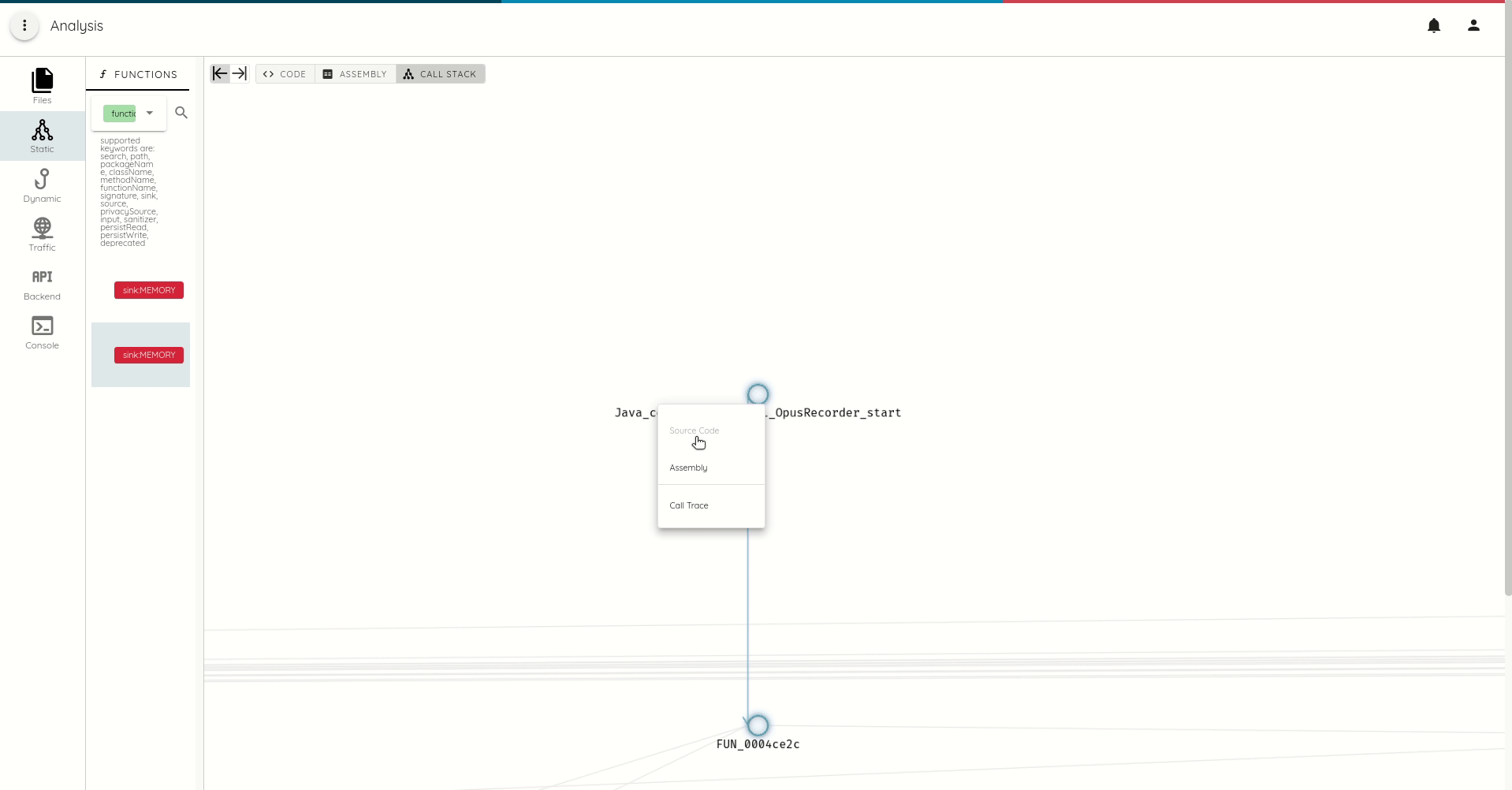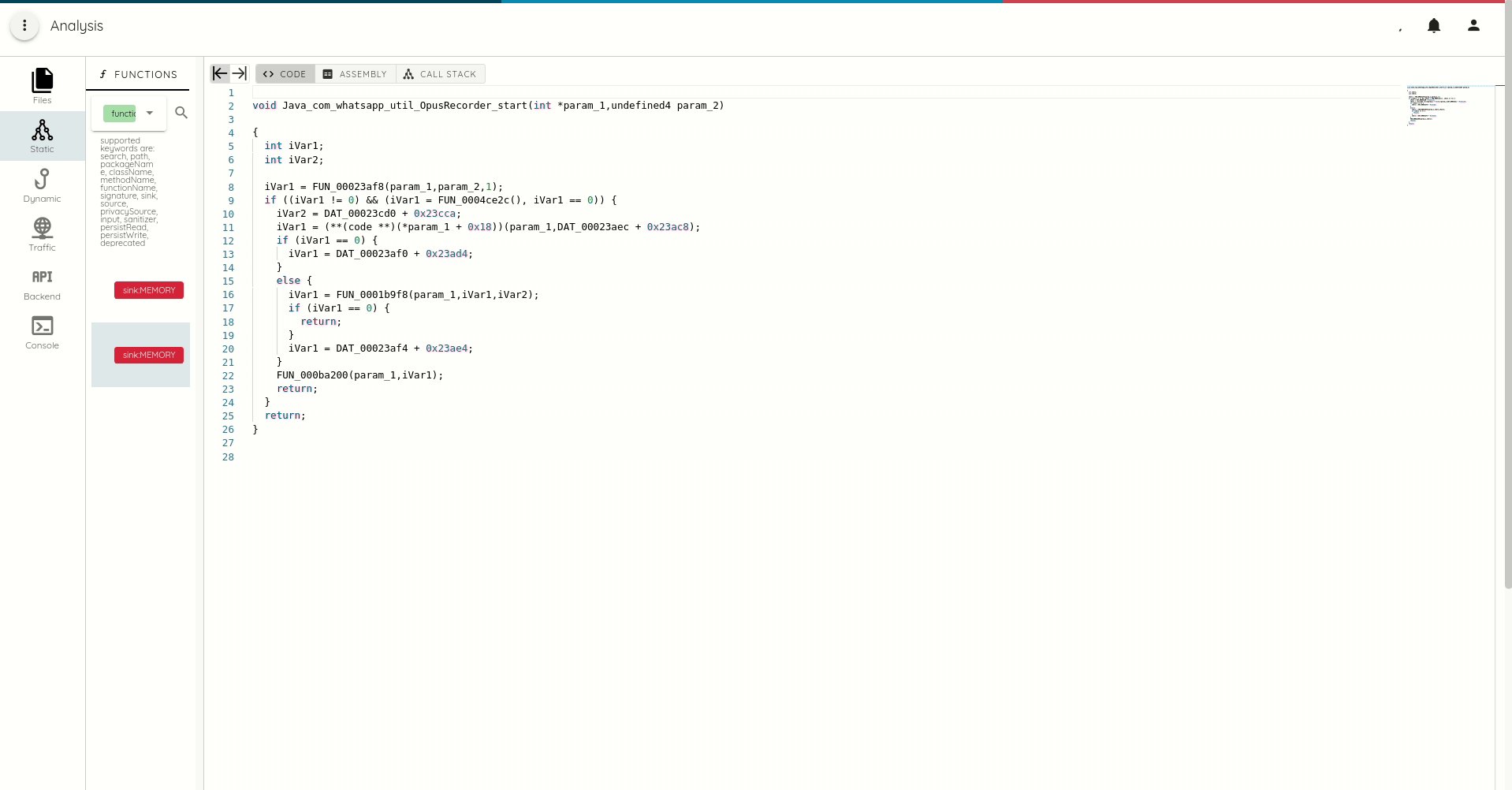
Expect a wealth of new features to be released in the upcoming months. The next release will focus on backend dynamic analysis.
All of these features are included with the community scan and are 100% free to use.