Fri 14 February 2025
AI-Automated Attack Surface Management: The Future of Cybersecurity Discovery
Imagine typing a simple command: "Please find all the ways to compromise Microsoft or any of its acquisitions" and instantly receiving a comprehensive map of every potential vulnerability across an entire network infrastructure.
This isn't science fiction - it's the reality of AI-powered attack surface management, and it's revolutionizing how organizations discover and protect their digital assets.
Key Achievements
- Discovered all the acquisitions, domains, networks, and other assets belonging to large organizations like Airbnb, Tesla, and Microsoft, all without human intervention.
- Reduced discovery time from weeks to hours.
The Current Challenge
Modern organizations face an overwhelming task: managing and securing thousands, sometimes millions, of digital assets. These assets include:
- Domains and subdomains
- Cloud instances
- Mobile applications
- IP ranges
- Autonomous System Numbers (ASNs)
- Third-party integrations
Traditional methods of discovering and monitoring these assets involve manual input, CSV file uploads, and constant human supervision. With the rapid pace of digital transformation, new assets are continuously added, old ones deprecated, and configurations modified - making manual tracking nearly impossible.
The AI-Powered Solution
At Ostorlab, we've developed an AI-driven platform that automates the entire attack surface discovery and management process. Here's how it works:
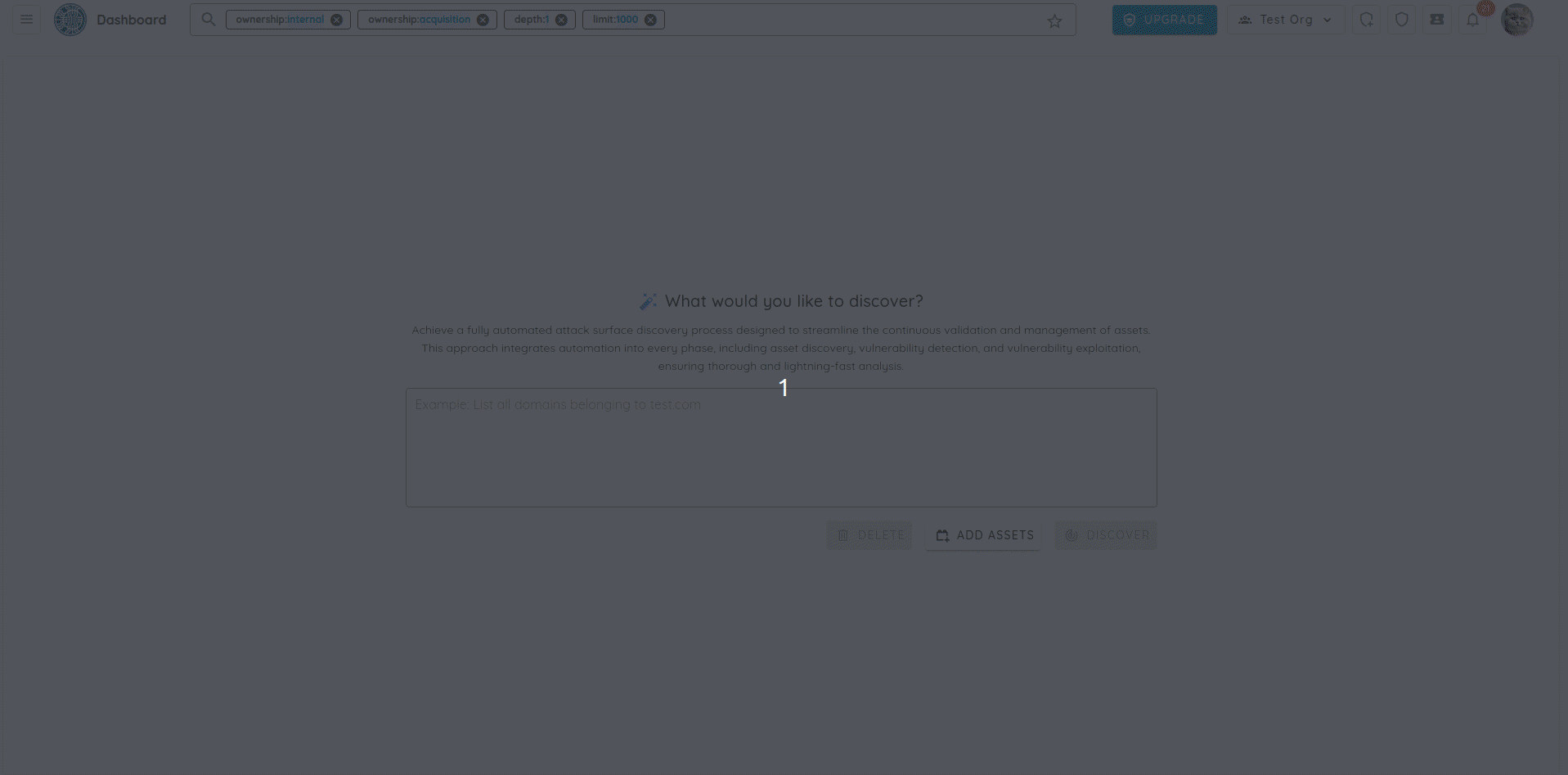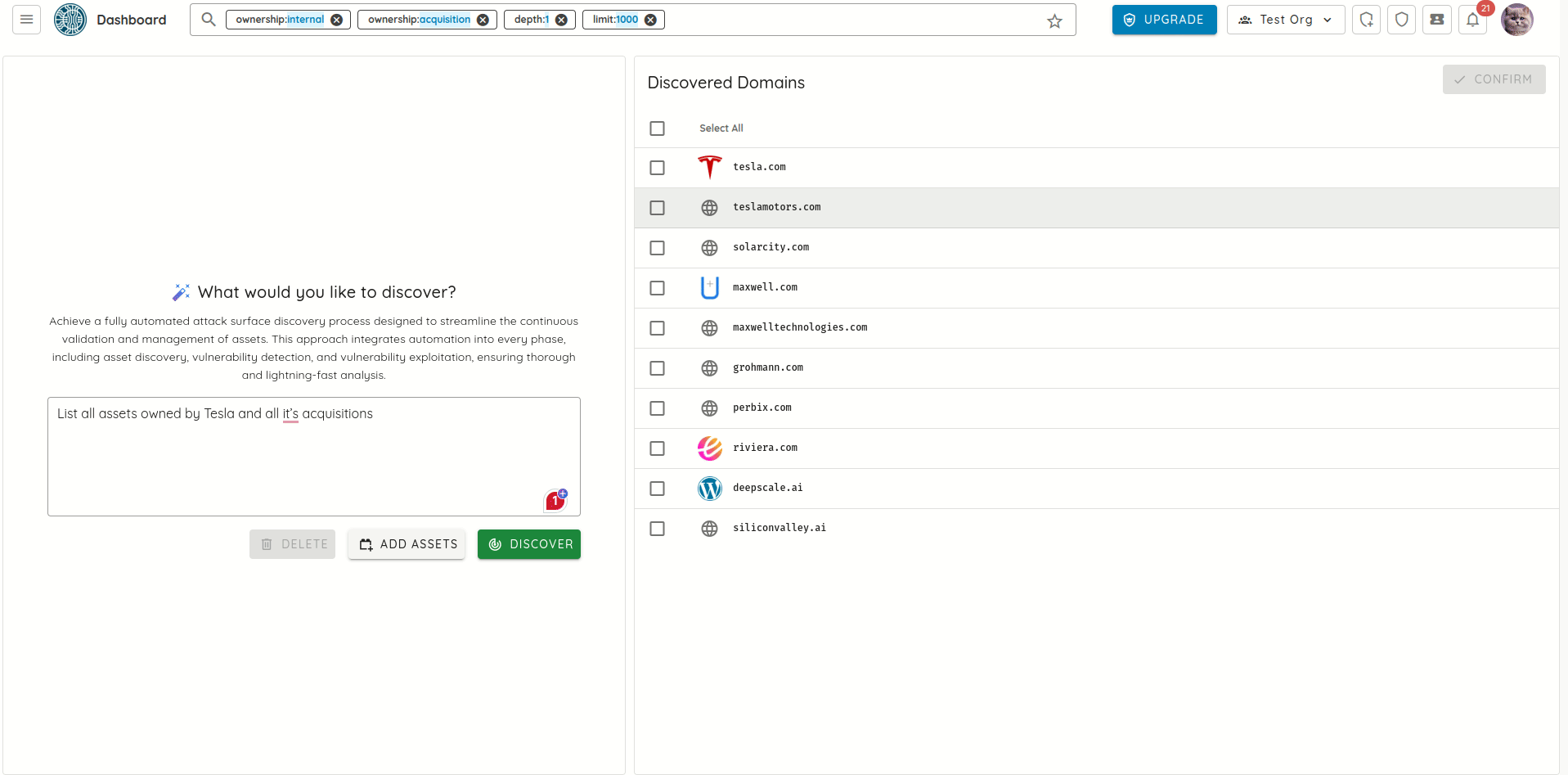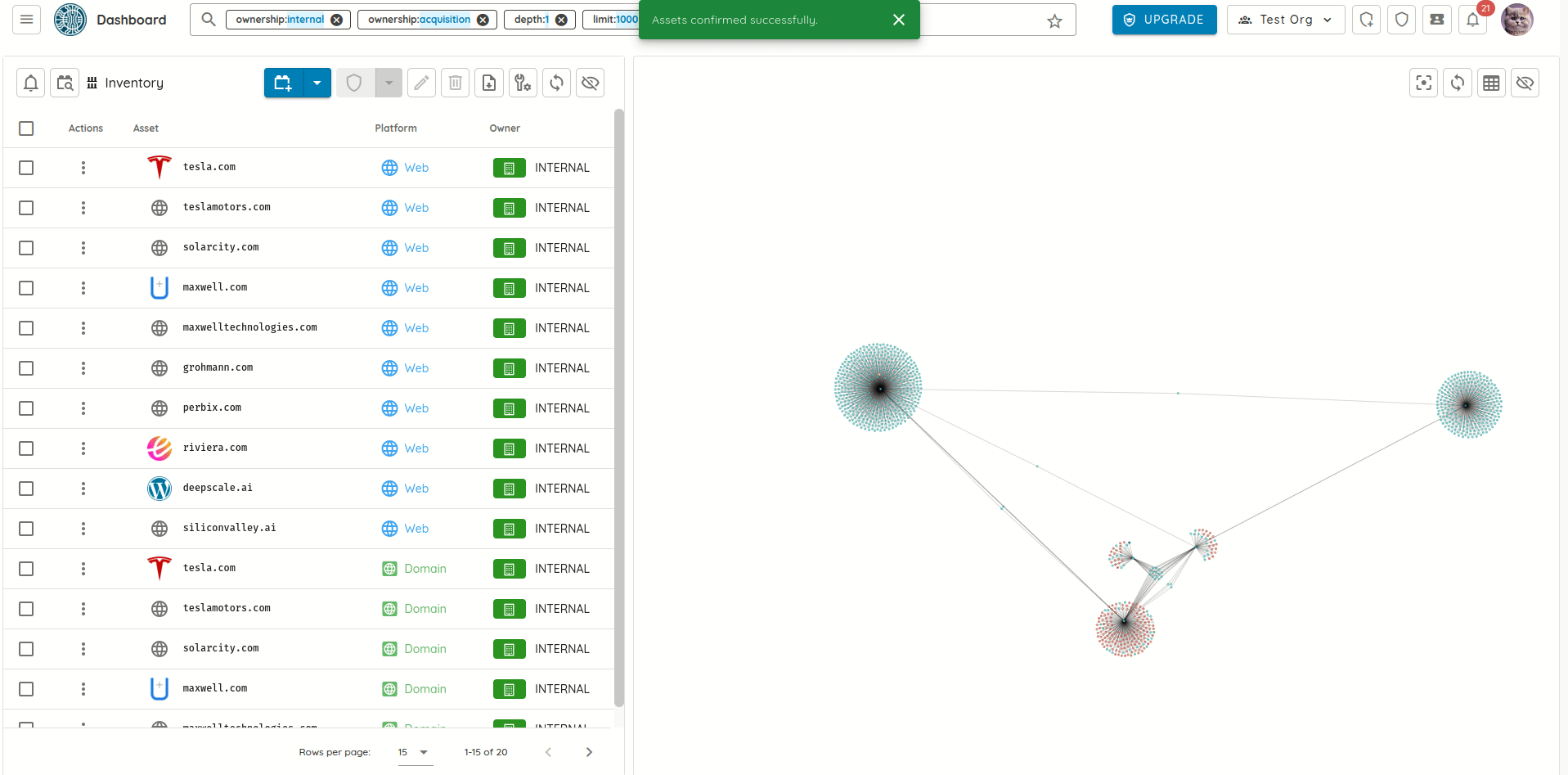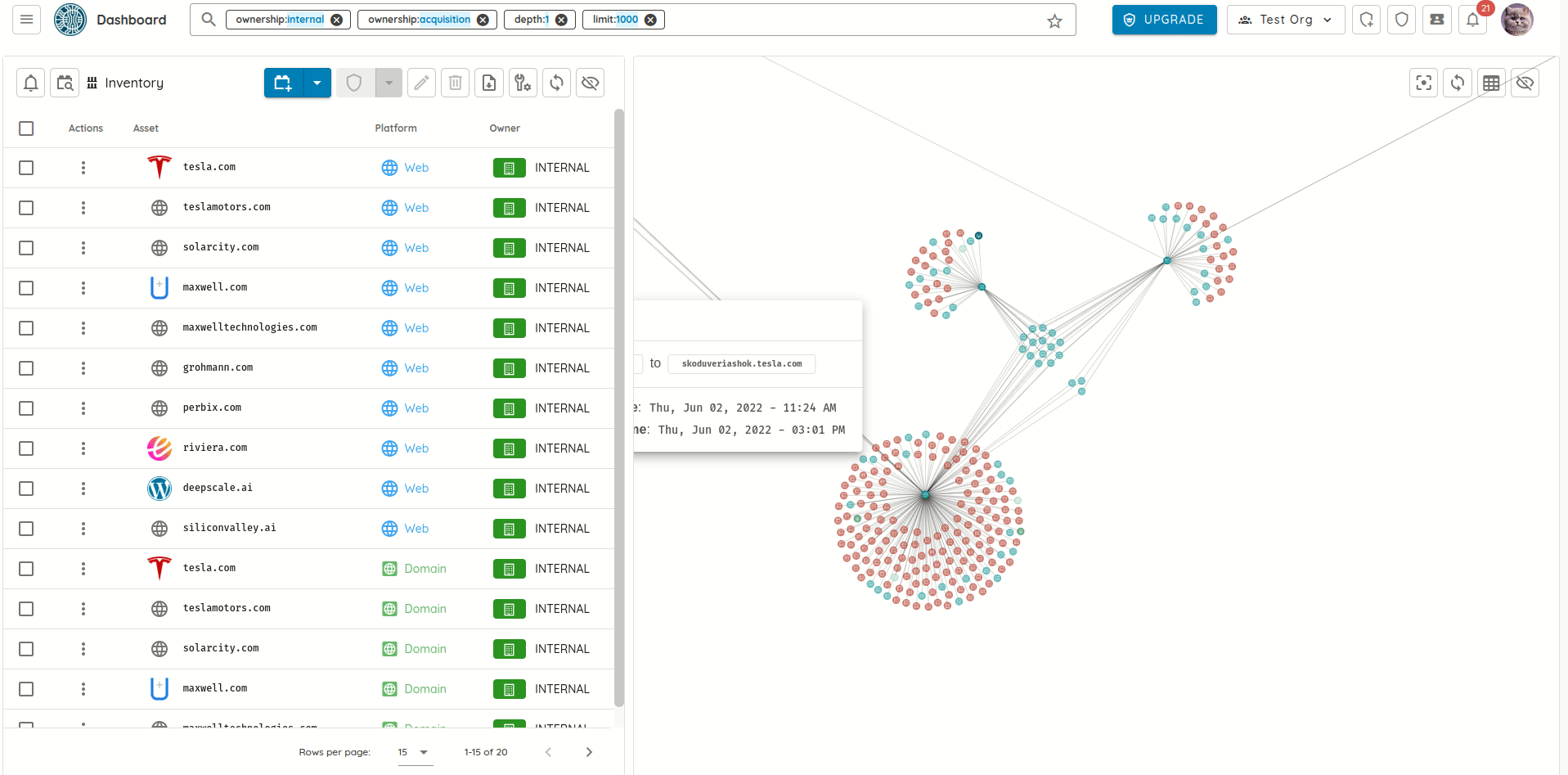
Initial Seeding
- Users provide a simple prompt (e.g., "List all assets owned by Tesla and its acquisitions").
- AI agent scours the internet for confirmed assets.
- Users can refine results through interactive prompts.
- Selected assets are visualized in a relationship graph.
Ownership Verification
- AI automatically validates asset ownership.
- Confirms or rejects assets based on multiple verification methods.
- Builds organizational context through prompt analysis.
- Maintains continuous monitoring for new assets.
AI-Powered Attack Surface 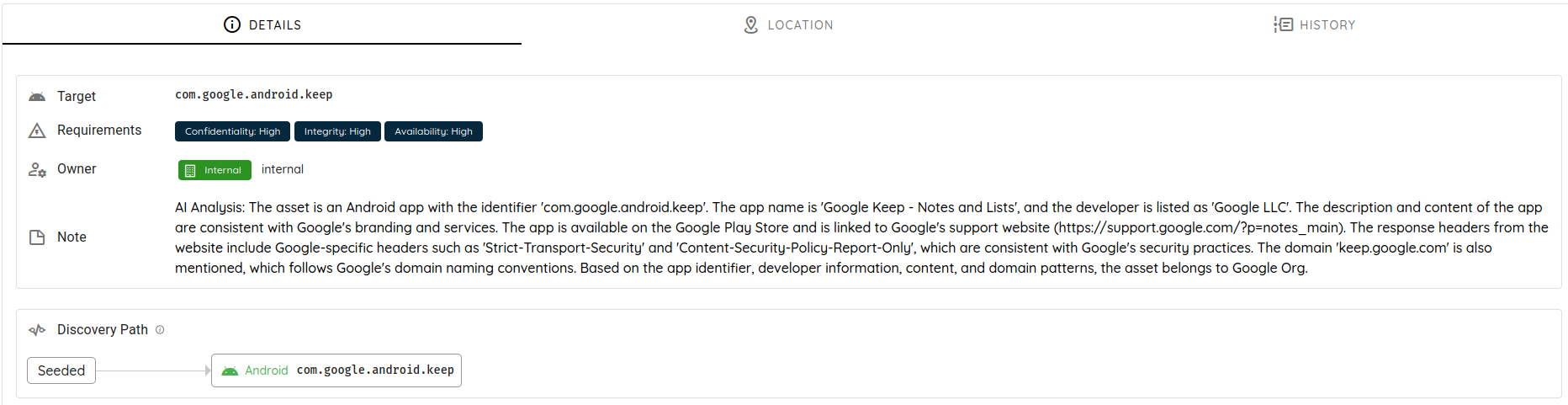
Asset confirmed by AI with reason / note 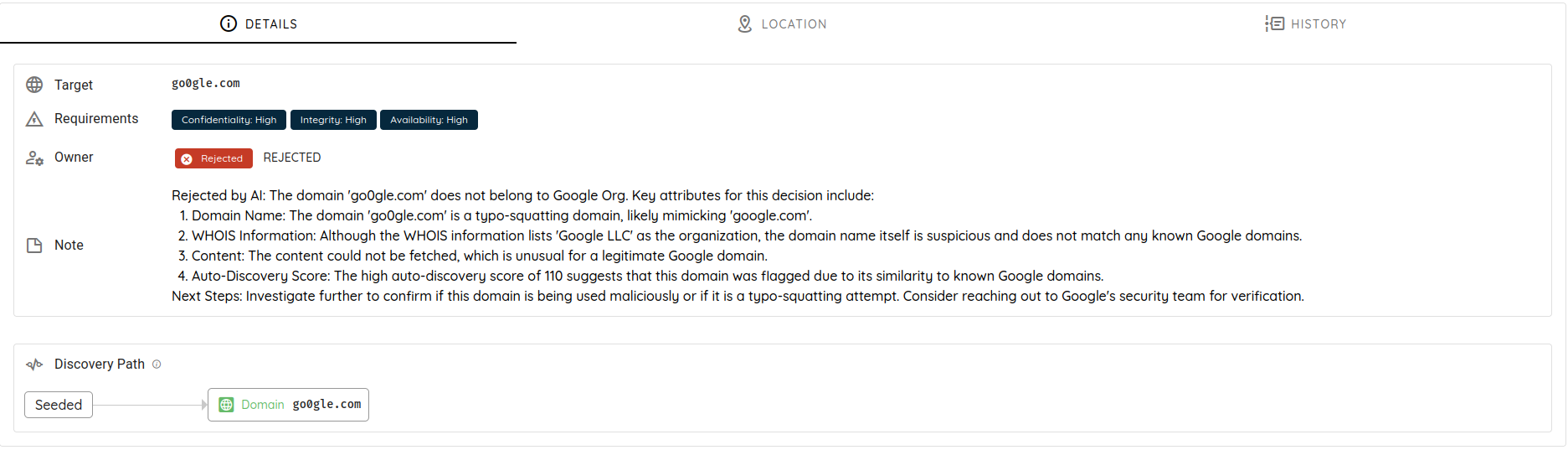
Asset rejected by AI with reason / note
Real-World Impact
In testing, our platform has demonstrated remarkable capabilities:
- Discovered numerous domain takeover vulnerabilities in major corporate networks.
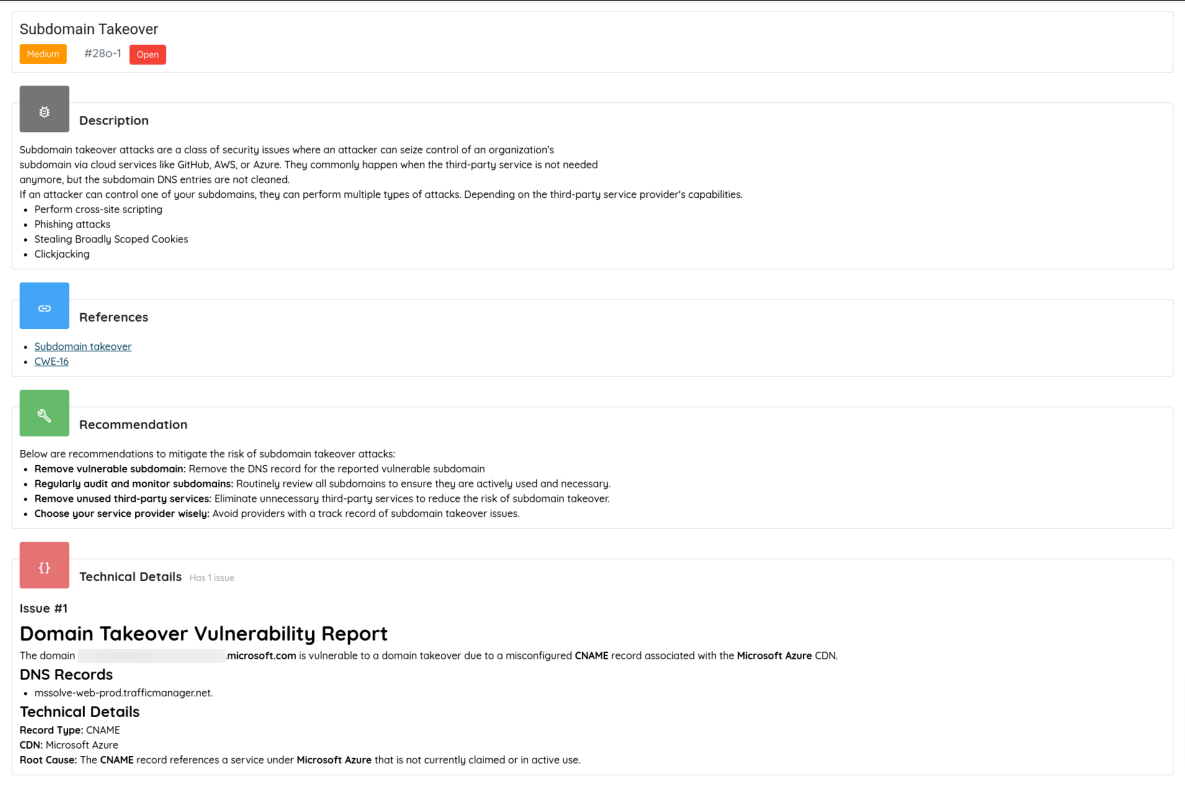
Domain Takeover Vulnerability - Identified remote code execution flaws in cloud infrastructure.
- Mapped complex organizational hierarchies and their digital assets.
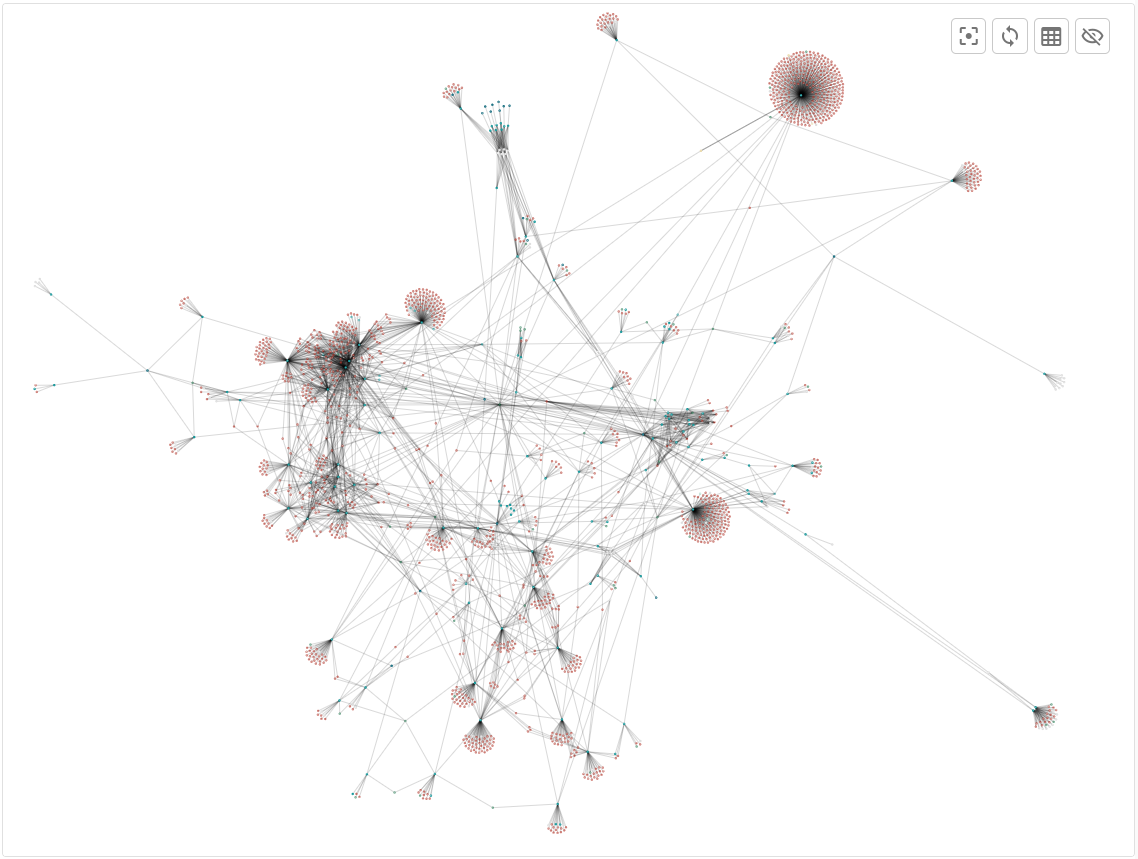
Organizational Hierarchies and their digital assets
Conclusion
The landscape of cybersecurity is evolving rapidly. AI-powered attack surface management isn't just an innovation - it's becoming a necessity. Organizations must adapt to this new reality where automated systems can rapidly discover and potentially exploit vulnerabilities. The choice isn't whether to embrace this technology, but how quickly you can implement it to stay ahead of potential threats.