Mon 21 February 2022
This is the most important announcement since Ostorlab was created and one that I am particularly excited to make.
Ostorlab is going open-source, releasing our scanning engine, vulnerability detectors, and analyzers.
At the core of Ostorlab is a highly modular engine that makes it fun to compose vulnerability detectors.
To empower this modularity we are releasing a market store that ships with popular open-source security tools, like Nmap, OpenVAS, Tsunami, Nuclei, and many others to come.
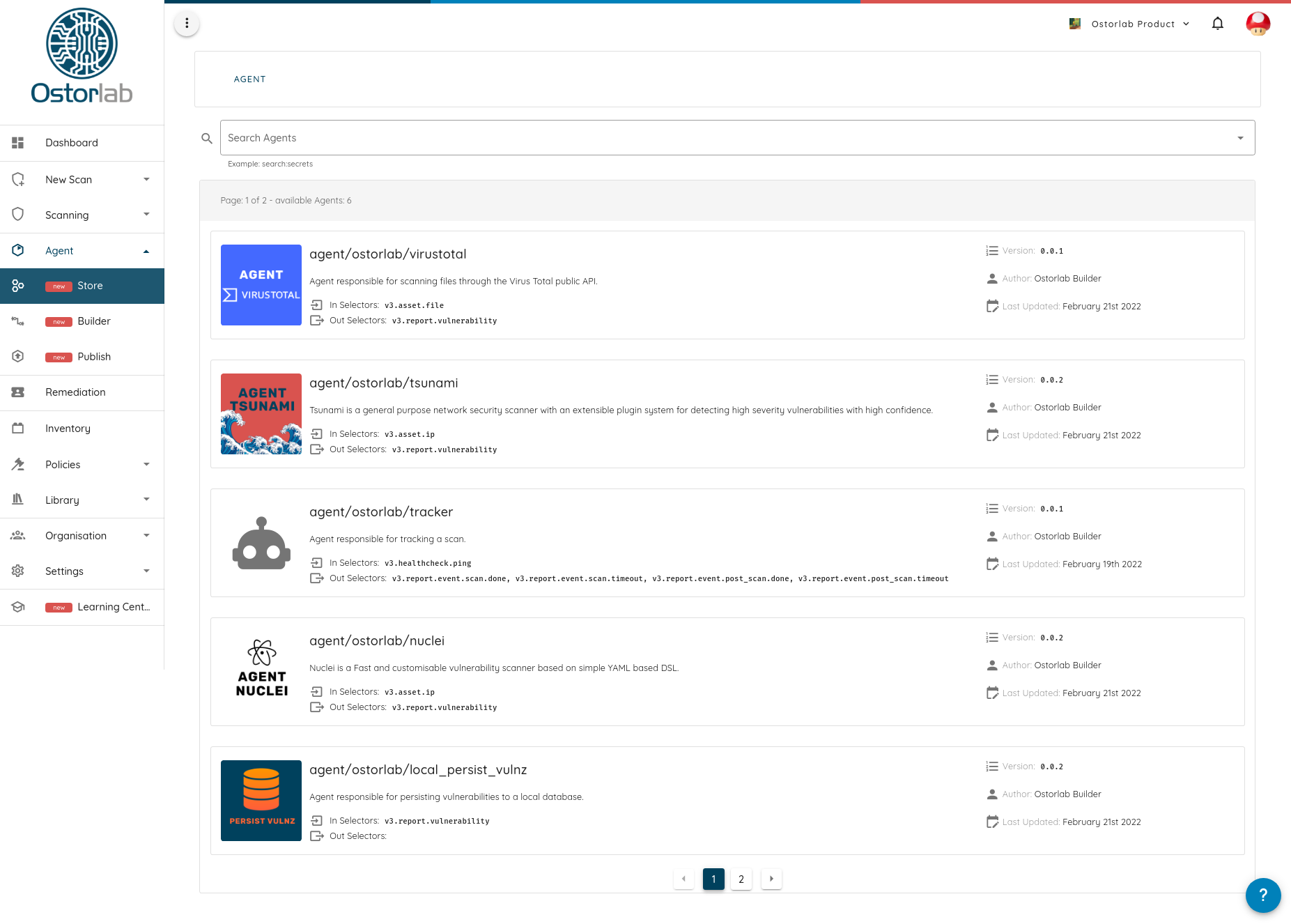
With the new release, we are adding support for scanning everything, from mobile applications, web applications, IP addresses to containers, and with that targeting the detection of almost everything, from finding simple configuration issues, crawling for secrets to running a full-blown dynamic analysis environment.
Getting started is as easy as one command to install, and one command to run:
pip install -U ostorlab
oxo scan run --install \
--agent agent/ostorlab/nmap --agent agent/ostorlab/openvas --agent agent/ostorlab/tsunami --agent agent/ostorlab/nuclei \
ip 8.8.8.8

But before I dig into the new platform and the features it provides, let me start by what led us to make the platform open-source.
The story behind it?
Ostorlab has been a community-focused platform since its inception. It was created as a free online platform that allowed scanning mobile applications with no limit. Just upload your app or select it from the store and that’s it.
This decision has been driven by a strong belief that security shouldn’t be restricted to large corporations with the means to pay for expensive tools.
Making the platform open-source is a natural extension that we have delayed because we wanted to share something that others can easily use, adopt, play with and contribute to.
The second reason we are open-sourcing the platform is a general disappointment with the direction the security industry has been taking. Legacy security scanners and even the newer platforms are all enterprise-focused and with an increasing tendency toward hyper-specialization.
If you are managing a vulnerability scanning program today, even at a very small scale, you need a plethora of tools to have sufficient coverage. From a tool for the web apps, network infrastructures, Web APIs, Cloud Projects, IAM policies, Containers, Source Code, Dependencies, Secrets, and the list goes on and on.
The issue is that these tools are not interoperable, come with different concepts, terminology and use different risk ratings.
On the other hand, the open-source security scene is a lively one, with several great projects. Its serious shortcoming is how short-lived these tools tend to be, often built for a round of conference presentations before going into decay. There are of course notable exceptions like the venerable Nmap or the amazing sqlmap, but those are the exception, not the rule.
What does it entail?
So how does Ostorlab play a role in this reality and how is it trying to help?
First, Ostorlab makes tools seamlessly work together by providing a single common language, no matter what programming language they are built-in, no matter what platform they are running on, all speak one lingo to collaboratively serve a single goal, finding vulnerabilities.
In practical terms, Ostorlab wraps tools into agents that communicate asynchronously over distributed messages. These messages represent a shared security taxonomy that tools can agree on. The messages are strongly typed, compact, binary and follow a hierarchical structure.
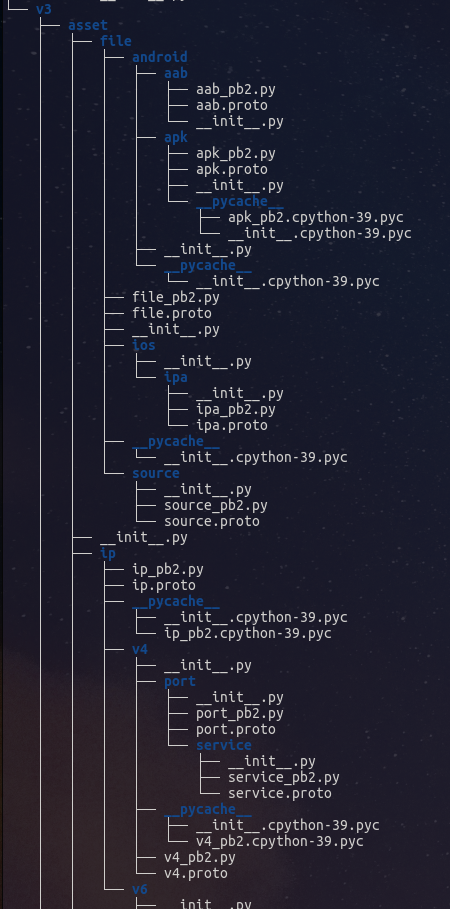
For instance, to scan a web application, the shared taxonomy would include:
URL:for crawling and brute-forcing URLs;Request/Response: to extract fingerprints, search in responses for patterns, like hardcoded secrets;Fingerprint: to list libraries, services, tech stacks and match them against known vulnerabilities;Injection Endpoint: to fuzz for vulnerabilities like XSS, SQL injection, XXE …
This approach makes:
- Chaining tools automated;
- Swapping tools or even using multiple is effortless;
- Extending them is standardized.

This approach has also the benefit of making scanning scalable, tools can be run on multiple machines without any changes.

In addition to providing the platform to make tools work together, Ostorlab ships with a new store to easily access security tools packaged to seamlessly work with each other.
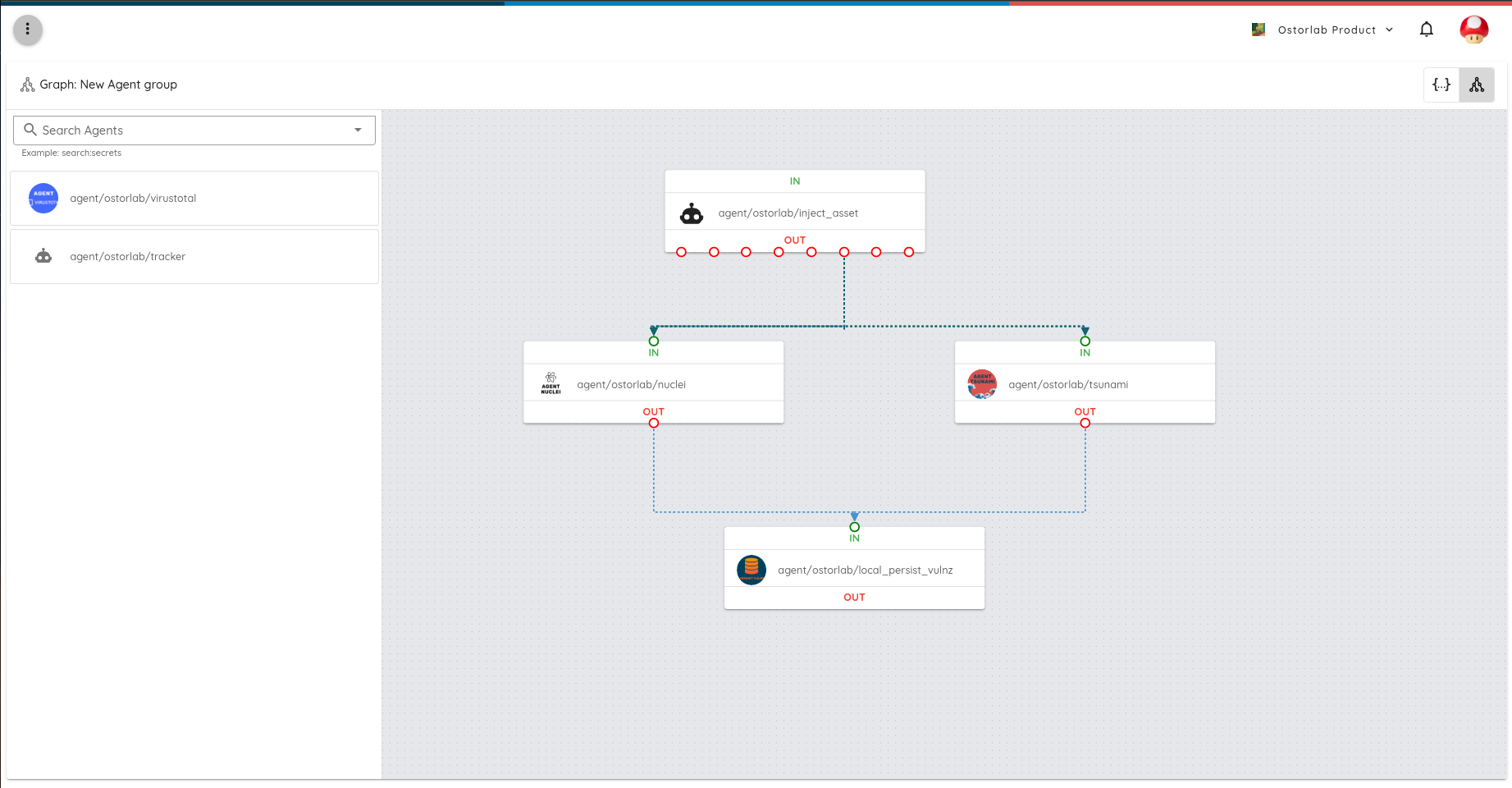
Behind the scenes, tools are nothing but containers, which enables supporting complex setups while remaining industry standard.
The store also provides a visualization tool to compose agents together to perform complex analysis tasks, from brute-forcing domains up to taking screenshots of pages or extracting secrets. The visualization can then generate a YAML definition file that can be run on your target asset with a single command.
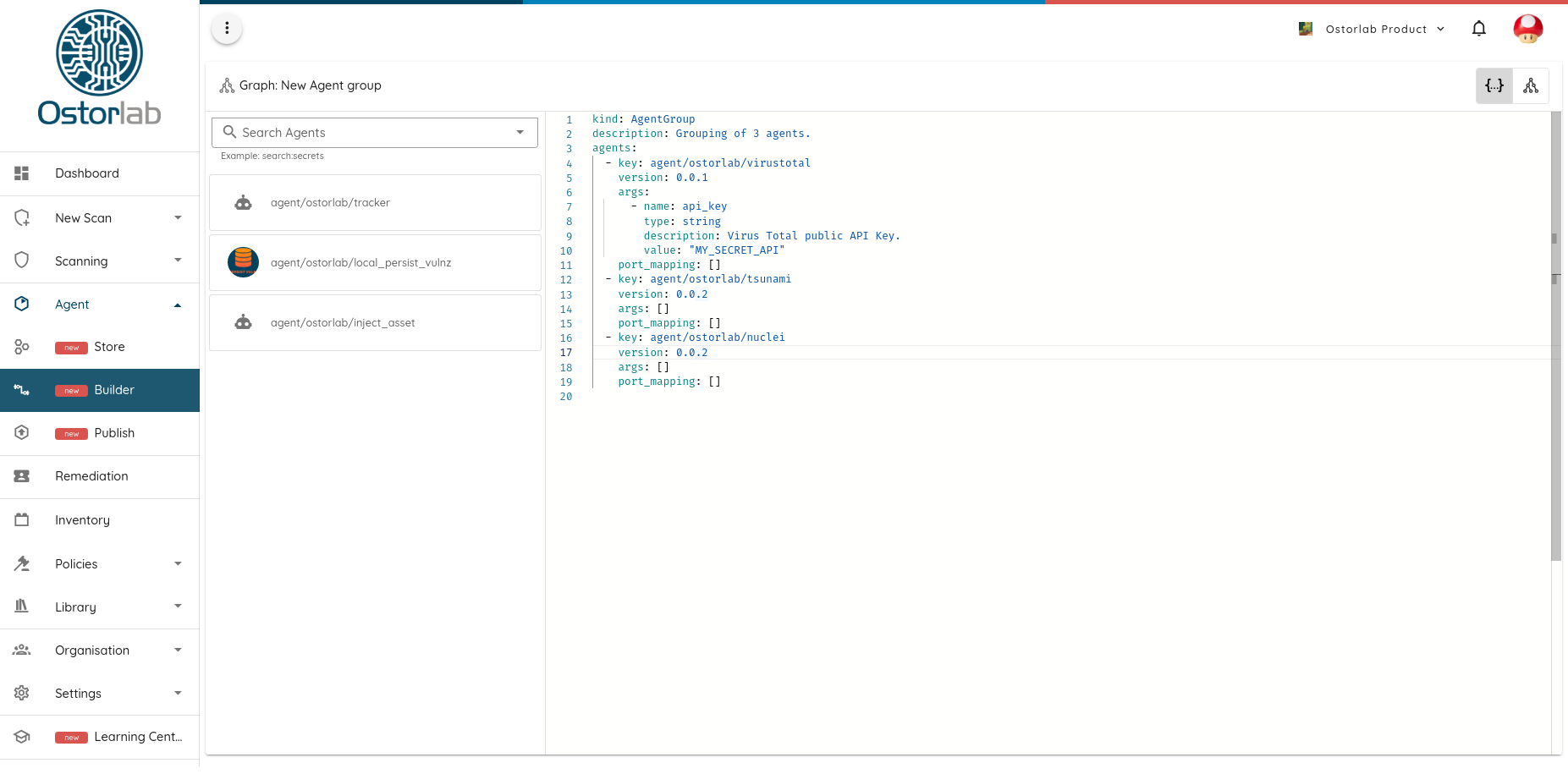
In addition to using the CLI to run scans, Ostorlab ships with an SDK to build your own agents. The SDK supports the standard use-cases with little code while also providing powerful APIs to build complex agents that can support scaling across multiple machines, like QPS limiting, distributed locking, shared state persistence, and distributed tracing and metrics…
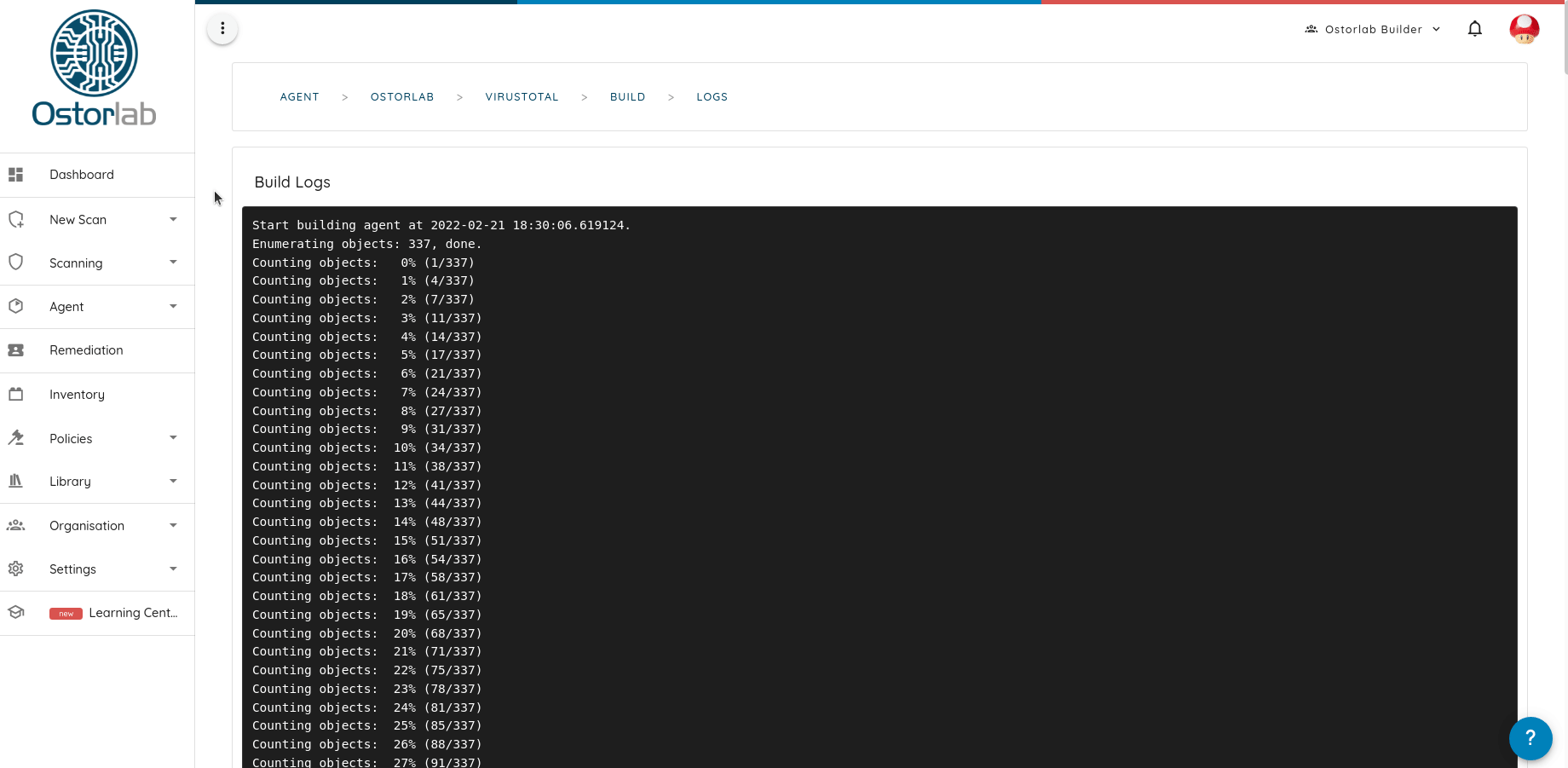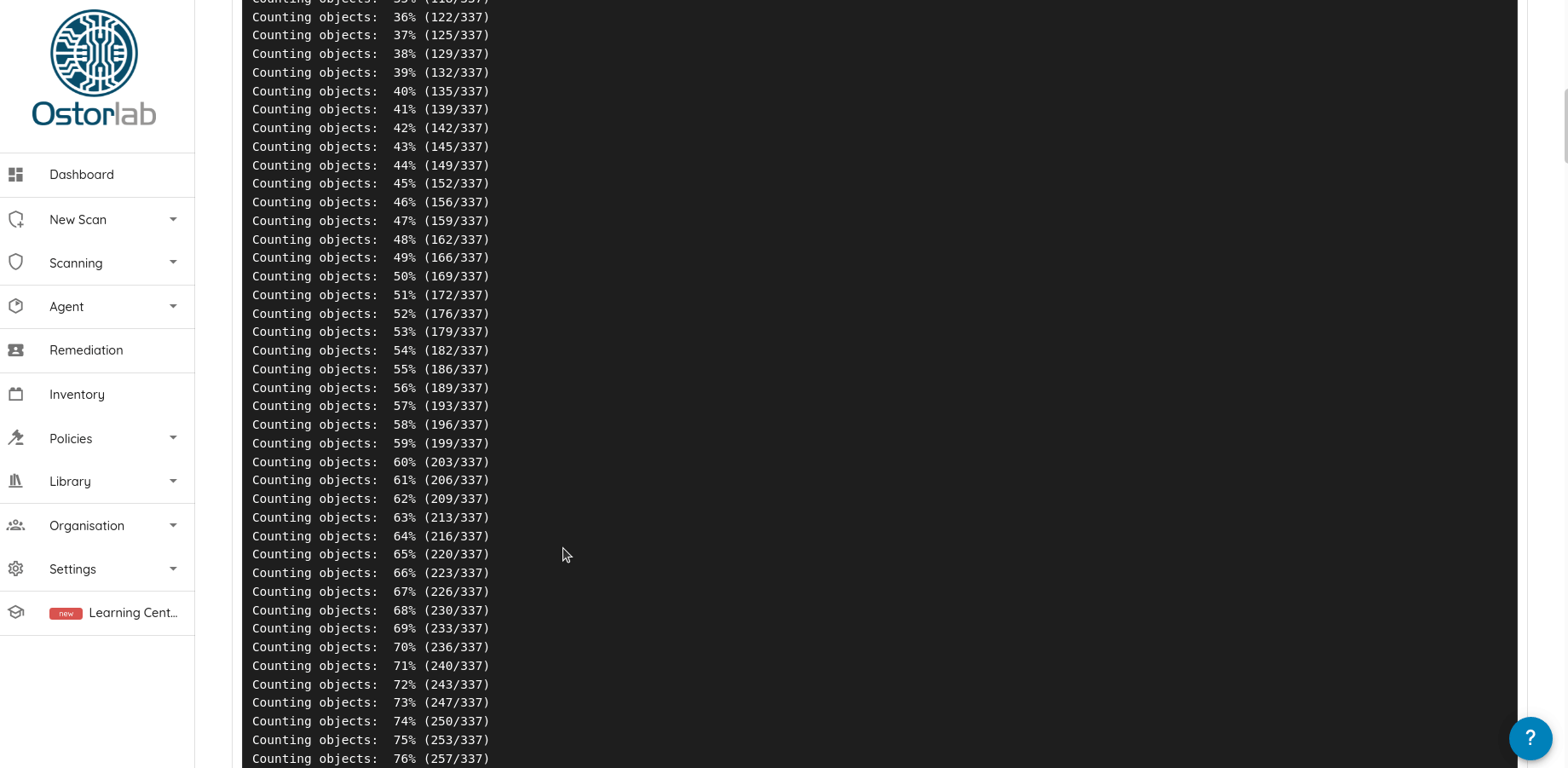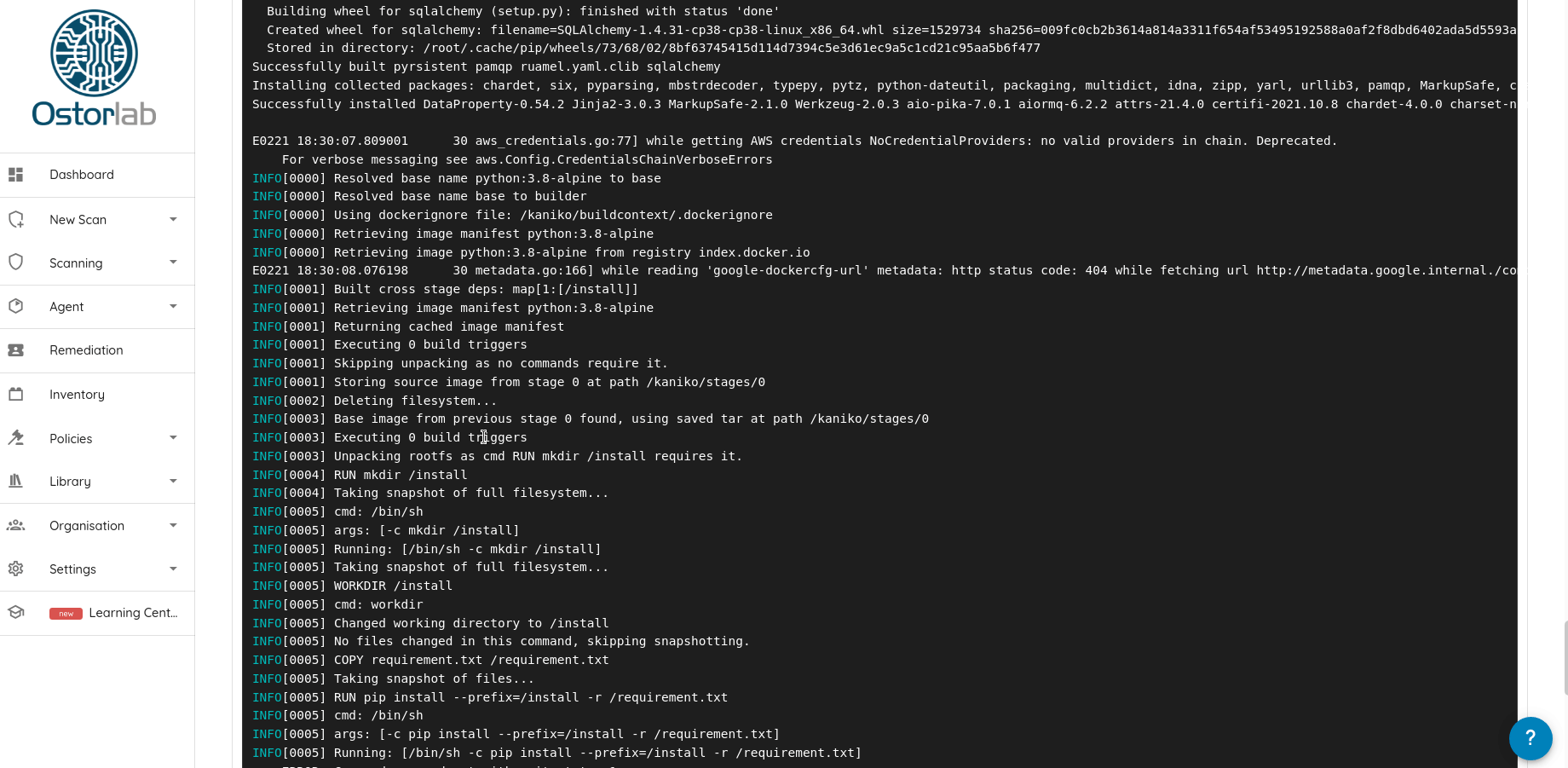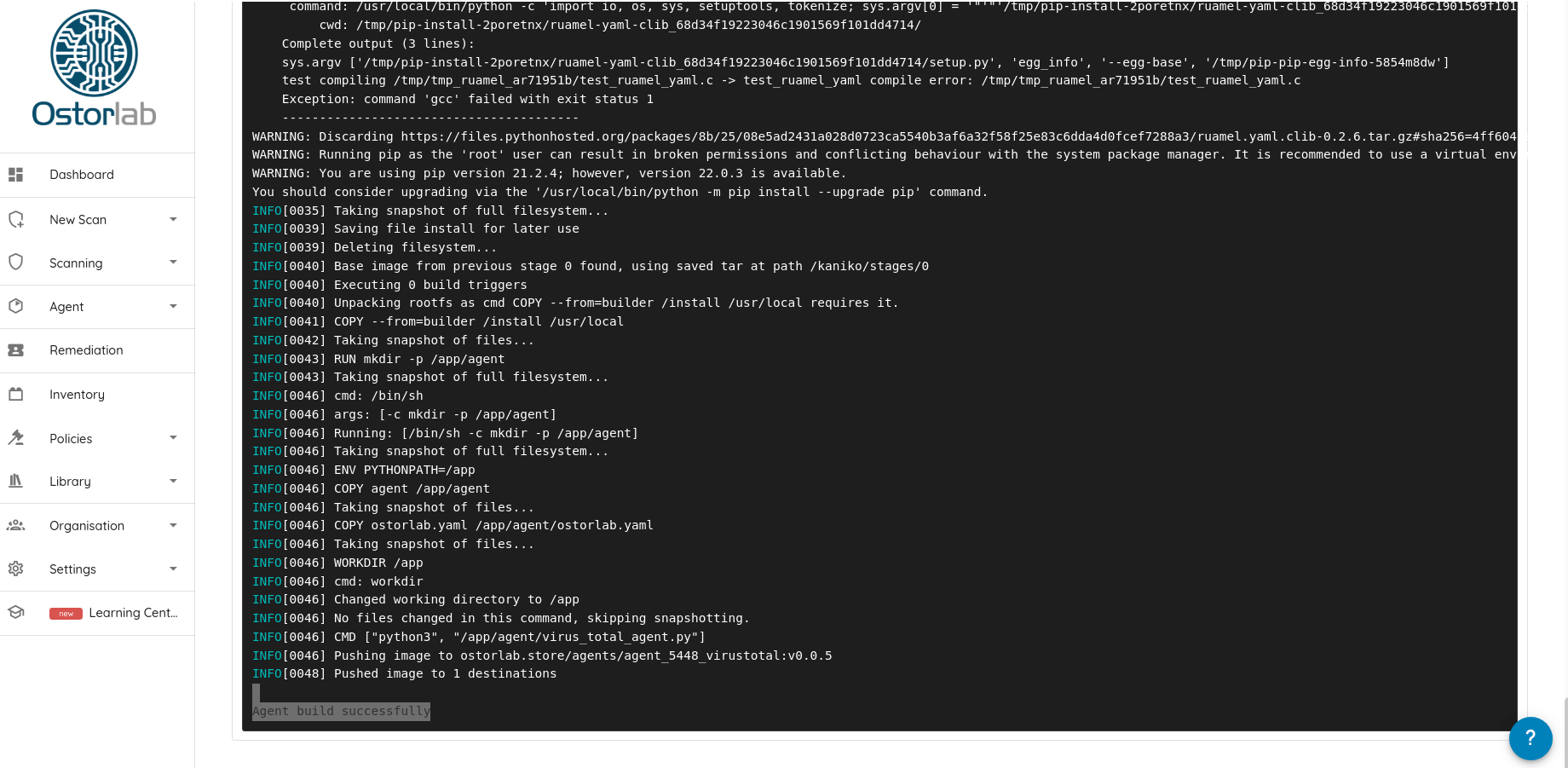
A critical part that makes adding and publishing new tools easy is the automated build and integration with Git repositories. Updates and changes are automatically picked up from the agent repo. New versions are built and shared the moment a new version tag is added and the store takes care of all the hassle of building and shipping new versions.
What can you do?
Take it for a ride and share your feedback. Report bug issues, suggestions, and comments. We would love to hear from you and learn more about how we can make the tool better.
The real power of the platform truly manifests as more agents are built and shared. Publish your favorite tool and share it in the store, or submit a feature request to have it added.
Next steps?
This release is only the start, as many other new features and updates are already on their way.
Notable upcoming updates are adding a managed version that enables running a scan on any asset in a managed environment. The managed environment uses Ostorlab's existing platform capabilities, like data persistence, scan history, automated scaling, ticketing system integration, multi-device support (iOS, macOS, …), and access to the analysis environment.
The upcoming releases will also focus on adding more specialized target assets and tools. These releases will include open-sourcing more of our cherished internal detectors, like our venerable crawler, XSS scanner, ostorlab taint engine, secret detector, and black box web fuzzer.
Finally, we are working on supporting open-source maintainers by sharing a significant portion of Ostorlab returns.
The returns will take into consideration key factors to help promote higher quality tools, these will include:
- Tool popularity;
- Tool contribution to vulnerability detection (true positives);
- Rate of false positives;
- Resource consumption (CPU, memory, disk size).
We hope by doing this that we will enable tool maintainers to have a meaningful way to continue supporting these tools and continue improving them.