Tue 27 May 2025
The Privacy Policy Problem Every Mobile Dev Faces
Your privacy policy says you collect "basic user data." Your app requests location, contacts, and camera permissions. See the problem?
This disconnect isn't malicious—it's the reality of shipping features faster than legal can update policies. But regulators don't care about your development velocity when they're writing $4.3 million fines.
A Real-World Example - Policy vs. Reality
Here's what we found analyzing a popular social network app:
📜 Privacy Policy Said: "We collect basic account information to provide our services."
🔍 App Actually Did:
- ✅ UI text referencing account linking: "To connect your account, open the Facebook app…"
- ✅ Permissions requested: Contact access, precise location, camera
- ✅ API usage: Location services called every 30 seconds
- ✅ Code patterns: Accessing device contacts and call logs
⚠️ Result: 7 undisclosed data collection points that weren't explicitly mentioned in the privacy policy.
This wasn't malicious—it's the natural result of iterative development where features evolve faster than legal documentation. Our Privacy Analysis automatically catches these gaps before they become compliance issues.
Why Privacy Policies and Apps Get Out of Sync
The challenge lies in bridging the gap between four different representations of data collection:
- 📝 Privacy Policy Text - Often written in legal language that may be ambiguous or overly broad
- 🔒 App Permissions - Technical declarations that require interpretation to understand their privacy implications
- 💻 Application Code - The actual implementation that determines what data is accessed and how
- 📱 User Interface - What users see and interact with, creating expectations about data use
The reality: You ship code faster than legal updates policies, third-party SDKs add new data collection, and iOS/Android introduce new privacy requirements your policy doesn't cover yet.
How We Analyze Your App's Privacy Practices
Our Privacy Analysis tackles this through systematic verification of all four layers. We analyze over 30 distinct PII categories and typically identify 1-5 data collection practices that need review, plus a complete picture of what your app collects versus what your policy declares.
Step 1: What Your Policy Actually Promises
We automatically retrieve your privacy policy from app store metadata (or you can provide a custom URL) and use AI agents specialized in privacy compliance to parse the legal text.
For each of the 30+ data categories we track, we extract:
- ✅ Whether collection is explicitly stated
- 📝 The exact quote from the policy supporting this determination
- 🔗 Links to relevant policy sections
Example Finding:
Consider a navigation app that mentions "location services" in its policy but doesn't specify whether it's collecting current location only or also storing location history for analytics—a distinction that matters for GDPR compliance. Our analysis is able to detect these nuanced discrepancies automatically.
Step 2: What Permissions You Actually Request
This step reveals what data access your app declares at the OS level—often more than developers realize.
Android: We parse the AndroidManifest.xml file to extract all declared permissions, then map them to privacy implications. For instance, ACCESS_FINE_LOCATION clearly indicates location data collection.
iOS: We analyze the Info.plist file for permission usage strings like NSLocationWhenInUseUsageDescription or NSContactsUsageDescription.
These technical permissions get mapped to human-readable data categories and compared against your privacy policy declarations.
Common Discrepancy: An app requesting android.permission.READ_CONTACTS while its privacy policy makes no mention of contact access gets immediately flagged.
Step 3: What Your Code Actually Does
This is where we uncover the ground truth—what your app actually accesses versus what you think it accesses.
We perform static code analysis to identify actual data collection in your implementation:
Android: We examine compiled code to identify calls to privacy-sensitive APIs like:
TelephonyManager.getDeviceId()(device identifiers)ContactsContractqueries (contact access)LocationManagerusage (location tracking)
iOS: Through binary analysis tools, we identify calls to iOS framework APIs such as:
CLLocationManager(location services)CNContactStore(contacts access)HealthKitAPIs (health data)
Why This Matters: Your code might be accessing data through third-party SDKs or inherited functionality that you forgot about.
Step 4: What Your UI Suggests to Users
Finally, we examine what data collection users expect based on your interface text.
Android: We extract text from layout files, analyzing user-visible elements like form labels, button text, and input field hints.
iOS: We parse interface files and string resources to identify text that suggests data collection.
Our AI agents analyze this UI text (processing 1000+ strings per analysis) to identify phrases that imply data collection:
- "Enter your email address" → Email collection
- "Allow location access" → Location data
- "Connect your Facebook account" → External account access
Example UI Elements Analysis Finding:
Found 3 layout elements suggesting collection of gender identity:
Text: 'Display my identity preferences'
Reason: 'The text indicates collection and display of gender identity information.'
Text: 'Choose your identity'
Reason: 'This prompt explicitly requests gender identity data from users.'
Text: 'This setting controls identity visibility on your profile'
Reason: 'References collection and processing of gender identity for profile display.'
⚠️ This collection is NOT declared in the privacy policy.
Comprehensive Cross-Analysis That Actually Matters
After analyzing all four layers, we perform cross-referencing to identify discrepancies:
- Policy vs. Permissions: Does your app request permissions for data types not mentioned in your policy?
- Policy vs. Code: Does your code access data that isn't declared in your privacy policy?
- Policy vs. UI: Do your interface elements suggest data collection that isn't transparently documented?
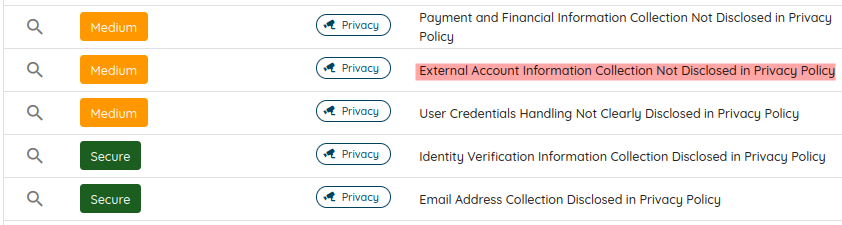
Each discrepancy gets flagged with specific evidence and actionable recommendations.
Common Privacy Patterns We Catch
Based on analyzing thousands of apps, these scenarios frequently lead to privacy discrepancies:
🔄 The Forgotten Feature: When developers add new functionality (like biometric authentication or social login) but forget to update privacy policies accordingly.
📈 Permission Creep: Apps that accumulate permissions over time without corresponding policy updates—requesting location for delivery tracking while only mentioning "general location services" in policies.
🎯 UI Expectations Gap: Interface elements that create user expectations about data use ("Enter your email," "Connect with Facebook") without clear policy backing.
⚡ API Evolution: When third-party SDKs introduce new data collection capabilities that aren't reflected in app privacy documentation.
Real Example: One app we analyzed requested calendar permissions but their privacy policy made no mention of calendar data collection:
android.permission.READ_CALENDAR
android.permission.WRITE_CALENDAR
The app was accessing calendar events to suggest meeting locations, but users had no idea their calendar data was being processed.
What You Get: Detailed Analysis Results
When Privacy Analysis completes, you receive comprehensive findings broken down by category:
Individual Vulnerability Reports
Each potential privacy issue gets detailed documentation with Technical Details like:
Found 1 layout elements suggesting collection of external account:
Text: "To connect your account, open the Facebook app on your mobile device and check for notifications."
Reason: The text indicates a connection to an external account (Facebook), which implies the collection or interaction with personal data associated with that account.
⚠️ This collection is NOT declared in the privacy policy.
Comprehensive Summary Table
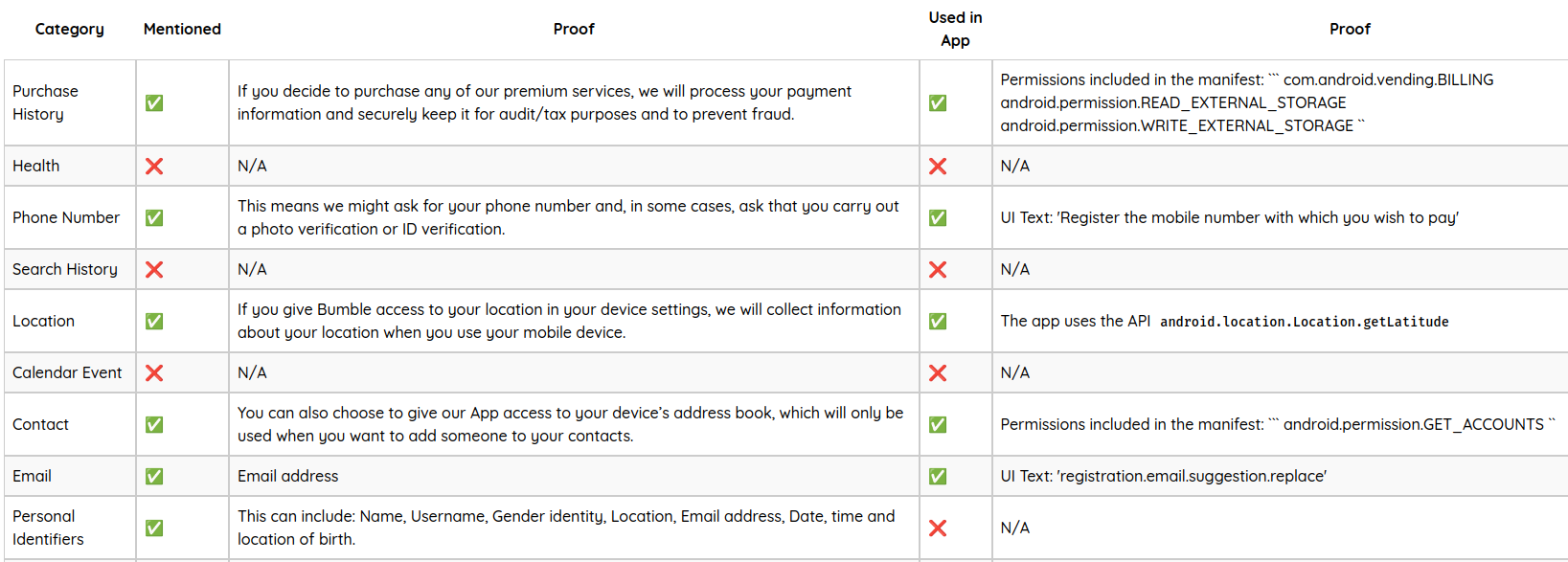
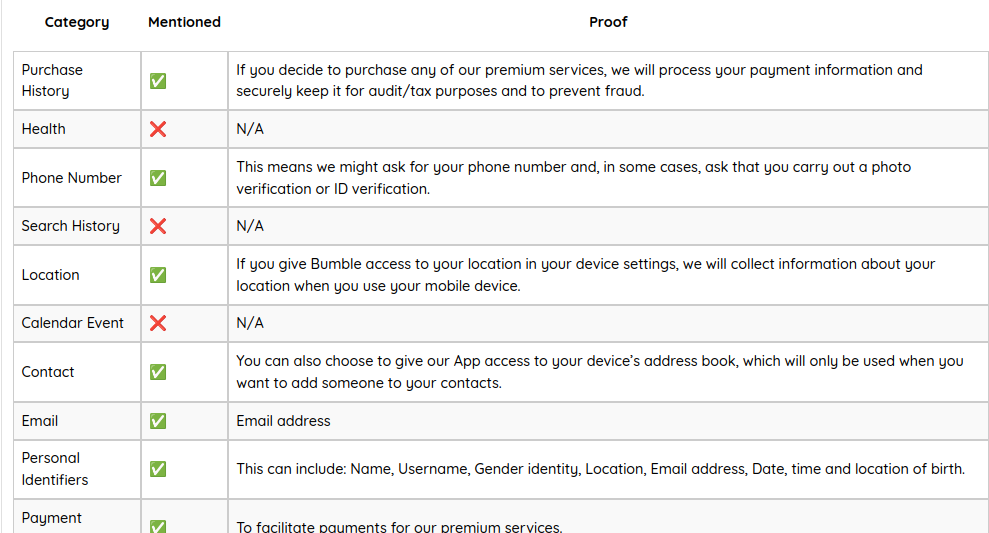
A master table shows policy declarations vs. actual app behavior across all data categories:
Privacy Policy Analysis:
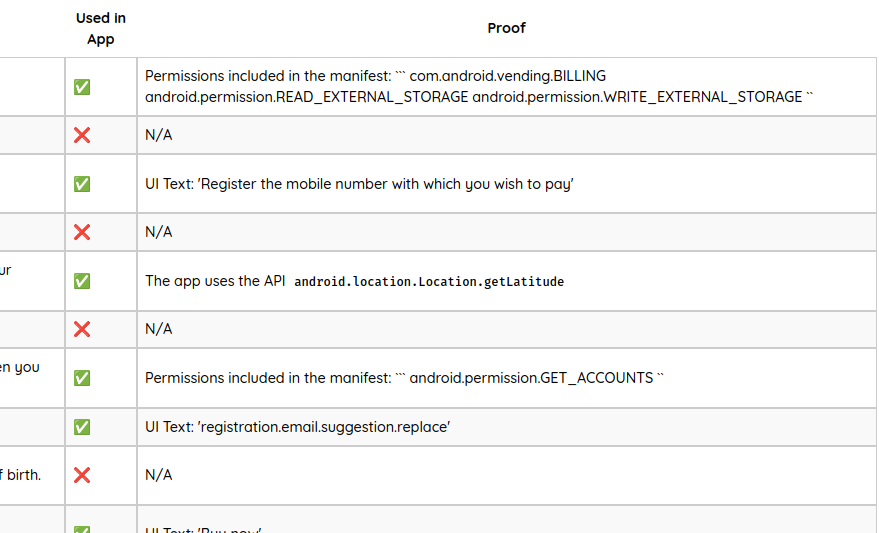
App Collection Behaviors:
Value for Development Teams
🚀 Proactive Compliance: Identify privacy discrepancies during development rather than after release, when fixes are more costly and damaging.
📊 Evidence-Based Documentation: Generate detailed reports showing exactly where privacy policy statements align or conflict with app behavior, useful for legal reviews and compliance audits.
⚖️ Reduced Legal Risk: Minimize exposure to GDPR, CCPA, and other privacy regulation violations by ensuring policy accuracy.
🤝 User Trust: Build stronger user relationships through transparent and accurate privacy practices.
👥 Developer Awareness: Help your development team understand the privacy implications of code changes and feature additions.
Multi-Platform Coverage
Our analysis works across both major mobile platforms, accounting for their different approaches to privacy:
📱 Android:
- Manifest permissions analysis
- Layout XML text extraction
- Dalvik bytecode examination
- Resource string analysis
🍎 iOS:
- Info.plist declarations parsing
- Interface file text extraction
- Binary analysis of iOS frameworks
- String resource examination
This comprehensive coverage ensures consistent privacy compliance regardless of your app's target platform.
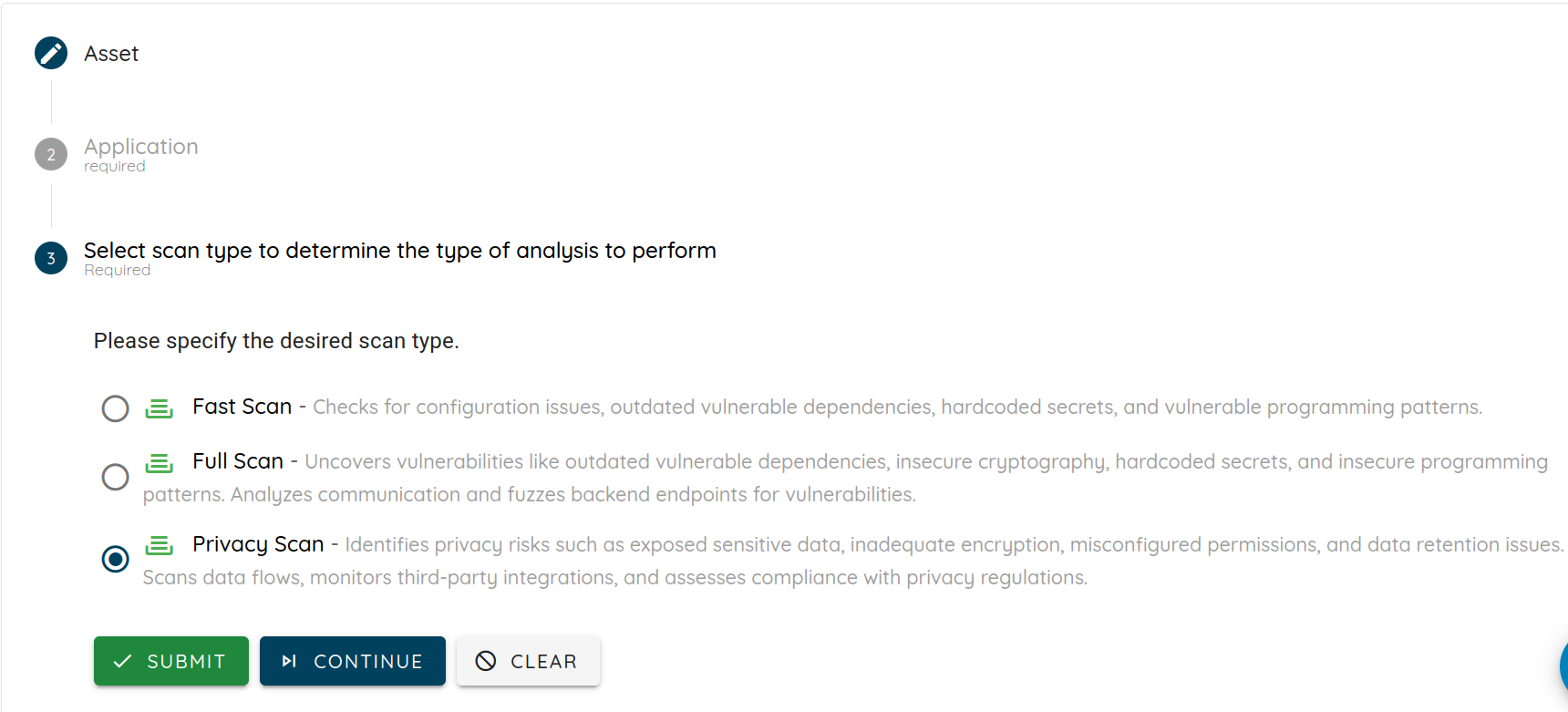
Running Ostorlab's Privacy Scan
Using Privacy Scan is straightforward:
- Upload your app file (Android APK/AAB or iOS IPA) to the Ostorlab platform
- Select Privacy Scan from available scan types
- Provide your privacy policy URL (or we'll grab it from app store metadata)
- Review detailed findings and recommendations
Conclusion
Privacy compliance isn't just about avoiding regulatory penalties—it's about building trust with your users through transparency and accuracy.
Our Privacy Analysis feature provides the systematic verification needed to ensure your privacy practices match your promises. By examining privacy policies, permissions, code, and user interfaces together, we offer unprecedented visibility into your app's actual data collection behavior.
The bottom line: Catch privacy discrepancies before they impact your users, your app store ratings, or your legal budget.
Table of Contents
- The Privacy Policy Problem Every Mobile Dev Faces
- A Real-World Example - Policy vs. Reality
- Why Privacy Policies and Apps Get Out of Sync
- How We Analyze Your App's Privacy Practices
- Comprehensive Cross-Analysis That Actually Matters
- Common Privacy Patterns We Catch
- What You Get: Detailed Analysis Results
- Value for Development Teams
- Multi-Platform Coverage
- Running Ostorlab's Privacy Scan
- Conclusion

